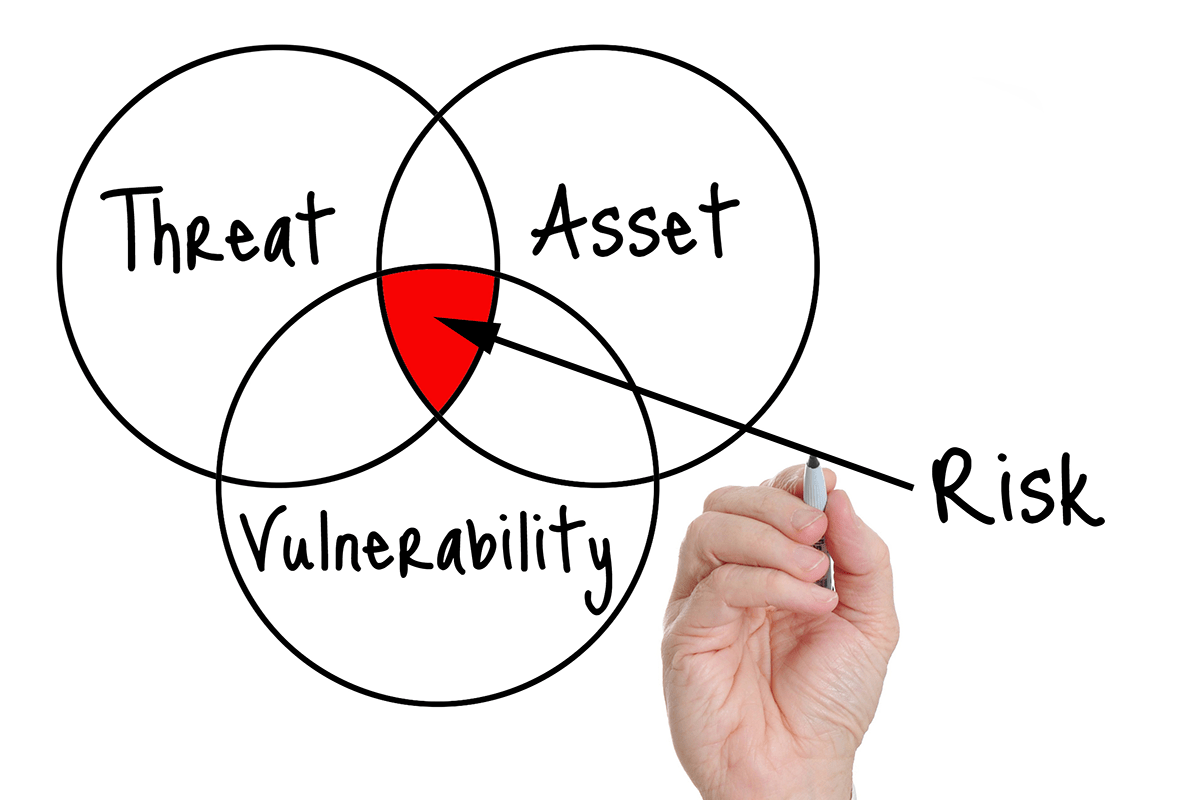
How To Do A Vulnerability Assessment . Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Find out what tools and strategies you need to conduct effective vulnerability. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Follow the steps of asset discovery,. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. This assessment focuses on identifying vulnerabilities within an.
from cognussys.com
Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. This assessment focuses on identifying vulnerabilities within an. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Find out what tools and strategies you need to conduct effective vulnerability. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Follow the steps of asset discovery,.
Vulnerability and Risk assessments Cognus Systems Inc
How To Do A Vulnerability Assessment This assessment focuses on identifying vulnerabilities within an. Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Find out what tools and strategies you need to conduct effective vulnerability. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. This assessment focuses on identifying vulnerabilities within an. Follow the steps of asset discovery,.
From spectralops.io
How to Perform a Comprehensive Network Vulnerability Assessment Spectral How To Do A Vulnerability Assessment Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Learn how to perform a vulnerability assessment using any automated or manual tool, from. How To Do A Vulnerability Assessment.
From eschoolsafety.org
Vulnerability Assessment — The Educator's School Safety Network How To Do A Vulnerability Assessment Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Learn how to plan, scan, analyze, prioritize,. How To Do A Vulnerability Assessment.
From www.businesstechweekly.com
Vulnerability Assessments 4 Crucial Steps for Identifying How To Do A Vulnerability Assessment Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Learn how to plan, scan,. How To Do A Vulnerability Assessment.
From www.manageengine.com
Vulnerability Assessment Process How to conduct a Vulnerability How To Do A Vulnerability Assessment Follow the steps of asset discovery,. Find out what tools and strategies you need to conduct effective vulnerability. Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. This assessment focuses on identifying vulnerabilities within an. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits. How To Do A Vulnerability Assessment.
From williamson-ga.us
Threat Vulnerability Risk assessment Template williamsonga.us How To Do A Vulnerability Assessment Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Follow the steps of asset discovery,. Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Find out what. How To Do A Vulnerability Assessment.
From www.pnas.org
A framework for vulnerability analysis in sustainability science PNAS How To Do A Vulnerability Assessment Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Follow the steps of asset discovery,. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Find out what tools and strategies you need to conduct effective vulnerability. This assessment focuses on identifying vulnerabilities within an. Learn. How To Do A Vulnerability Assessment.
From www.intruder.io
How To Perform A Vulnerability Assessment StepbyStep How To Do A Vulnerability Assessment Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Vulnerability. How To Do A Vulnerability Assessment.
From www.manageengine.com
Vulnerability Assessment Process How to conduct a Vulnerability How To Do A Vulnerability Assessment Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Find out what tools and strategies you need to conduct effective vulnerability. Learn how to perform a vulnerability assessment using any automated or manual tool,. How To Do A Vulnerability Assessment.
From www.pandasecurity.com
What is a Vulnerability Assessment? Panda Security How To Do A Vulnerability Assessment Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Find out what tools and strategies you need to conduct effective vulnerability. This assessment focuses on identifying vulnerabilities within an. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Learn the six steps to find and prioritize. How To Do A Vulnerability Assessment.
From www.future-processing.com
Vulnerability Assessment 101 What Every IT Expert Should Know How To Do A Vulnerability Assessment Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Follow the steps of asset discovery,. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the. How To Do A Vulnerability Assessment.
From purplesec.us
How To Conduct A Vulnerability Assessment In 8 Steps How To Do A Vulnerability Assessment Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Follow the steps of asset discovery,. This assessment focuses on identifying vulnerabilities within an. Find out what tools and strategies you need to conduct effective vulnerability.. How To Do A Vulnerability Assessment.
From businesspara.com
Vulnerability Assessments Explained How To Do A Vulnerability Assessment Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. This assessment focuses on identifying vulnerabilities within an. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Follow the steps of asset discovery,. Learn what a vulnerability assessment is, why it's important, and how to conduct one. How To Do A Vulnerability Assessment.
From threatshieldsecurity.com
Tampa Vulnerability Assessment threatSHIELD Security How To Do A Vulnerability Assessment Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Find out what tools and strategies you need to conduct effective vulnerability. Follow the steps of asset discovery,. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Vulnerability assessment enhances an organization’s. How To Do A Vulnerability Assessment.
From www.esecforte.com
Vulnerability Assessment Scanning Tools List 2018 eSecForte How To Do A Vulnerability Assessment This assessment focuses on identifying vulnerabilities within an. Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Find out what tools and strategies you need to conduct effective vulnerability. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Follow the steps of asset discovery,. Learn what. How To Do A Vulnerability Assessment.
From www.lanworks.com
Vulnerability Assessment Lanworks How To Do A Vulnerability Assessment Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Learn the six steps to. How To Do A Vulnerability Assessment.
From www.rootshellsecurity.net
Vulnerability Management Process Flow Chart Rootshell How To Do A Vulnerability Assessment Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Find out what tools and strategies you need to conduct effective vulnerability. Learn what a vulnerability assessment is, why it's important, and how to. How To Do A Vulnerability Assessment.
From zsecurity.org
Creating a Vulnerability Management Strategy zSecurity How To Do A Vulnerability Assessment This assessment focuses on identifying vulnerabilities within an. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Find out what tools and strategies you need to conduct effective vulnerability. Learn how to perform a vulnerability. How To Do A Vulnerability Assessment.
From phoenixnap.com
What Is Vulnerability Assessment? {Vulnerability Testing Guide} How To Do A Vulnerability Assessment Follow the steps of asset discovery,. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report.. How To Do A Vulnerability Assessment.
From www.slideteam.net
Crisis Vulnerability Assessment Matrix For Management Strategy How To Do A Vulnerability Assessment Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. This assessment focuses on identifying vulnerabilities within an. Find out what tools. How To Do A Vulnerability Assessment.
From www.businesstechweekly.com
Vulnerability Assessments 4 Crucial Steps for Identifying How To Do A Vulnerability Assessment Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Find out. How To Do A Vulnerability Assessment.
From cognussys.com
Vulnerability and Risk assessments Cognus Systems Inc How To Do A Vulnerability Assessment Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Learn what a vulnerability assessment is, why it's important,. How To Do A Vulnerability Assessment.
From www.manageengine.com
Vulnerability Assessment Tools & Checklists ManageEngine How To Do A Vulnerability Assessment This assessment focuses on identifying vulnerabilities within an. Follow the steps of asset discovery,. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Find out what tools and strategies you need to conduct effective vulnerability. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Learn how. How To Do A Vulnerability Assessment.
From www.educba.com
Vulnerability Assessment Tools Tool to Maintain Systems & Security How To Do A Vulnerability Assessment Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Learn how to perform a vulnerability. How To Do A Vulnerability Assessment.
From www.securehyperloop.com
Secure Hyperloop Securing Cyber World From Threats & Attacks How To Do A Vulnerability Assessment Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Learn how to perform a vulnerability assessment using any automated or. How To Do A Vulnerability Assessment.
From sysdig.com
Top vulnerability assessment and management best practices Sysdig How To Do A Vulnerability Assessment Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. This assessment focuses on identifying vulnerabilities within an. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Learn the six steps to find. How To Do A Vulnerability Assessment.
From purplesec.us
What Is A Vulnerability Assessment? (A Complete Guide For 2023) How To Do A Vulnerability Assessment Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Find out what tools and strategies you need to. How To Do A Vulnerability Assessment.
From brightsec.com
Vulnerability Management Lifecycle, Tools, and Best Practices How To Do A Vulnerability Assessment Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Follow the steps of asset discovery,. Learn what a vulnerability assessment is, why it's important, and how to conduct one with. How To Do A Vulnerability Assessment.
From purplesec.us
How To Perform A Network Vulnerability Assessment (With Examples How To Do A Vulnerability Assessment Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. This assessment focuses on identifying vulnerabilities within an. Learn how to. How To Do A Vulnerability Assessment.
From academy.hackthebox.com
Vulnerability Assessment Course HTB Academy How To Do A Vulnerability Assessment Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating a report. Follow the steps of asset discovery,. Find out what tools and strategies you need to conduct effective vulnerability. This assessment focuses on identifying vulnerabilities within an. Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities. How To Do A Vulnerability Assessment.
From sigmaearth.com
Risk Assessment and Vulnerability Analysis Sigma Earth How To Do A Vulnerability Assessment Learn how to plan, scan, analyze, prioritize, report, and remediate network vulnerabilities with this guide. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Vulnerability assessment enhances an organization’s security posture and offers. How To Do A Vulnerability Assessment.
From www.securitynewspaper.com
How to do security vulnerability testing? How To Do A Vulnerability Assessment This assessment focuses on identifying vulnerabilities within an. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Find out what tools and strategies you need to conduct effective vulnerability. Vulnerability assessment is. How To Do A Vulnerability Assessment.
From www.boardish.io
Vulnerability Assessment Best Practices How To Be One Step Ahead of How To Do A Vulnerability Assessment This assessment focuses on identifying vulnerabilities within an. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Learn how to perform a vulnerability assessment using any automated or manual tool, from identifying assets and risk to creating. How To Do A Vulnerability Assessment.
From www.businesstechweekly.com
Vulnerability Assessments 4 Crucial Steps for Identifying How To Do A Vulnerability Assessment Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Follow the steps of asset discovery,. Find out what. How To Do A Vulnerability Assessment.
From www.crowdstrike.com
What is Vulnerability Management? CrowdStrike How To Do A Vulnerability Assessment Find out what tools and strategies you need to conduct effective vulnerability. Follow the steps of asset discovery,. Learn what a vulnerability assessment is, why it's important, and how to conduct one with the right tools. Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. Learn how to plan, scan, analyze, prioritize,. How To Do A Vulnerability Assessment.
From blog.teamascend.com
The Five Stages of Vulnerability Management How To Do A Vulnerability Assessment Vulnerability assessment is the process of identifying, quantifying, and prioritizing (or ranking) the vulnerabilities in a system. This assessment focuses on identifying vulnerabilities within an. Vulnerability assessment enhances an organization’s security posture and offers numerous other benefits as follows. Learn the six steps to find and prioritize security weaknesses in your environment using a vulnerability scanner and a. Follow the. How To Do A Vulnerability Assessment.