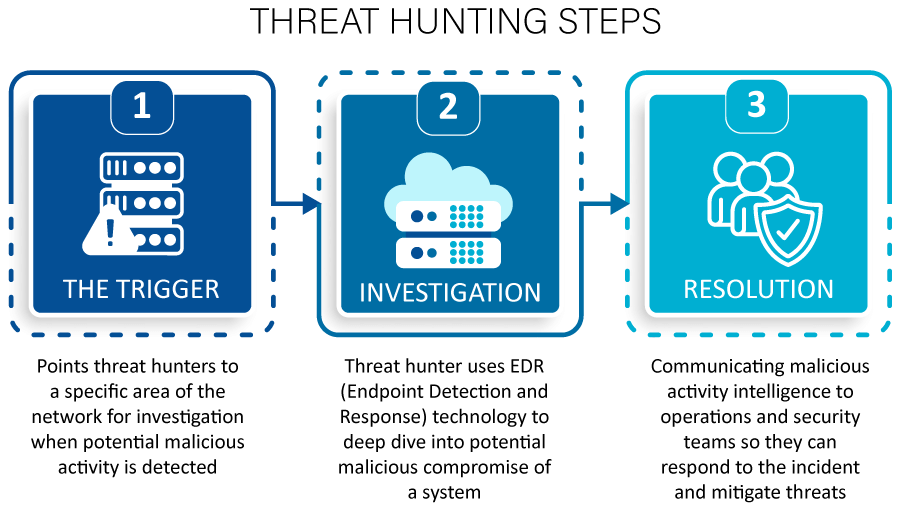
Threat Hunting Process Document . A trigger, an investigation and a resolution. It falls under the active defense category of. Threat hunting is a proactive and iterative approach to detecting threats. There are three phases in a proactive threat hunting process: Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. An initial trigger phase, followed by an investigation, and ending. The process of proactive cyber threat hunting typically involves three steps:
from proinf.com
Threat hunting is a proactive and iterative approach to detecting threats. An initial trigger phase, followed by an investigation, and ending. It falls under the active defense category of. A trigger, an investigation and a resolution. The process of proactive cyber threat hunting typically involves three steps: Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. There are three phases in a proactive threat hunting process:
Cyber Threat Hunting 101 Guide Methods, Tools, Techniques & Frameworks
Threat Hunting Process Document An initial trigger phase, followed by an investigation, and ending. It falls under the active defense category of. A trigger, an investigation and a resolution. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. Threat hunting is a proactive and iterative approach to detecting threats. An initial trigger phase, followed by an investigation, and ending. There are three phases in a proactive threat hunting process: The process of proactive cyber threat hunting typically involves three steps:
From www.atatus.com
Threat Hunting Definition, Process, Methodologies, and More Threat Hunting Process Document The process of proactive cyber threat hunting typically involves three steps: Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. An initial trigger phase, followed by an investigation, and ending. It falls under the active defense category of. A trigger, an investigation and a resolution. There are. Threat Hunting Process Document.
From thecyphere.com
Threat Hunting Process, Methodologies, Tools And Tips Threat Hunting Process Document An initial trigger phase, followed by an investigation, and ending. The process of proactive cyber threat hunting typically involves three steps: It falls under the active defense category of. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. A trigger, an investigation and a resolution. Threat hunting. Threat Hunting Process Document.
From www.govinfosecurity.com
An Inside Look at a Level 4 Threat Hunting Program Threat Hunting Process Document An initial trigger phase, followed by an investigation, and ending. A trigger, an investigation and a resolution. It falls under the active defense category of. There are three phases in a proactive threat hunting process: Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. The process of. Threat Hunting Process Document.
From www.researchgate.net
Threat Hunting Solution Steps Download Scientific Diagram Threat Hunting Process Document There are three phases in a proactive threat hunting process: The process of proactive cyber threat hunting typically involves three steps: A trigger, an investigation and a resolution. Threat hunting is a proactive and iterative approach to detecting threats. It falls under the active defense category of. An initial trigger phase, followed by an investigation, and ending. Threat hunting is. Threat Hunting Process Document.
From www.atatus.com
Threat Hunting Definition, Process, Methodologies, and More Threat Hunting Process Document Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. Threat hunting is a proactive and iterative approach to detecting threats. There are three phases in a proactive threat hunting process: An initial trigger phase, followed by an investigation, and ending. A trigger, an investigation and a resolution.. Threat Hunting Process Document.
From www.slideteam.net
Cyber Threat Hunting Program With Process And Tools Presentation Threat Hunting Process Document Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. An initial trigger phase, followed by an investigation, and ending. There are three phases in a proactive threat hunting process: The process of proactive cyber threat hunting typically involves three steps: Threat hunting is a proactive and iterative. Threat Hunting Process Document.
From blog.gigamon.com
How Threat Hunting Can Evolve Your Detection Capabilities Gigamon Blog Threat Hunting Process Document The process of proactive cyber threat hunting typically involves three steps: It falls under the active defense category of. An initial trigger phase, followed by an investigation, and ending. A trigger, an investigation and a resolution. There are three phases in a proactive threat hunting process: Threat hunting is a process usually followed by security analysts to search for such. Threat Hunting Process Document.
From expel.com
What is (cyber) threat hunting and where do you start? Expel Threat Hunting Process Document An initial trigger phase, followed by an investigation, and ending. A trigger, an investigation and a resolution. Threat hunting is a proactive and iterative approach to detecting threats. There are three phases in a proactive threat hunting process: Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber.. Threat Hunting Process Document.
From proinf.com
Threat Hunting Techniques, Checklist, Examples, Execution, Metrics Threat Hunting Process Document Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. A trigger, an investigation and a resolution. It falls under the active defense category of. Threat hunting is a proactive and iterative approach to detecting threats. An initial trigger phase, followed by an investigation, and ending. The process. Threat Hunting Process Document.
From old.sermitsiaq.ag
Threat Hunting Report Template Threat Hunting Process Document Threat hunting is a proactive and iterative approach to detecting threats. An initial trigger phase, followed by an investigation, and ending. It falls under the active defense category of. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. A trigger, an investigation and a resolution. The process. Threat Hunting Process Document.
From thecyphere.com
Threat Hunting Process, Methodologies, Tools And Tips Threat Hunting Process Document Threat hunting is a proactive and iterative approach to detecting threats. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. A trigger, an investigation and a resolution. There are three phases in a proactive threat hunting process: An initial trigger phase, followed by an investigation, and ending.. Threat Hunting Process Document.
From www.cyberproof.com
What is threat hunting? CyberProof Threat Hunting Process Document The process of proactive cyber threat hunting typically involves three steps: It falls under the active defense category of. Threat hunting is a proactive and iterative approach to detecting threats. An initial trigger phase, followed by an investigation, and ending. A trigger, an investigation and a resolution. Threat hunting is a process usually followed by security analysts to search for. Threat Hunting Process Document.
From heimdalsecurity.com
Managed Threat Hunting The Next Step from Traditional Cybersecurity Threat Hunting Process Document The process of proactive cyber threat hunting typically involves three steps: Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. It falls under the active defense category of. A trigger, an investigation and a resolution. An initial trigger phase, followed by an investigation, and ending. There are. Threat Hunting Process Document.
From threatcop.com
Threat Hunting What is it and How is it Done? ThreatCop Threat Hunting Process Document An initial trigger phase, followed by an investigation, and ending. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. A trigger, an investigation and a resolution. The process of proactive cyber threat hunting typically involves three steps: Threat hunting is a proactive and iterative approach to detecting. Threat Hunting Process Document.
From www.slideteam.net
Five Step Process Of Cyber Threat Hunting Threat Hunting Process Document There are three phases in a proactive threat hunting process: The process of proactive cyber threat hunting typically involves three steps: An initial trigger phase, followed by an investigation, and ending. Threat hunting is a proactive and iterative approach to detecting threats. A trigger, an investigation and a resolution. It falls under the active defense category of. Threat hunting is. Threat Hunting Process Document.
From www.researchgate.net
Threat Hunting Process from Scratch Download Scientific Diagram Threat Hunting Process Document Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. An initial trigger phase, followed by an investigation, and ending. Threat hunting is a proactive and iterative approach to detecting threats. A trigger, an investigation and a resolution. The process of proactive cyber threat hunting typically involves three. Threat Hunting Process Document.
From threatcop.com
Threat Hunting What is it and How is it Done? ThreatCop Threat Hunting Process Document There are three phases in a proactive threat hunting process: It falls under the active defense category of. A trigger, an investigation and a resolution. Threat hunting is a proactive and iterative approach to detecting threats. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. An initial. Threat Hunting Process Document.
From www.dts-solution.com
A Threat Hunt tale Threat Hunting Process Document An initial trigger phase, followed by an investigation, and ending. It falls under the active defense category of. There are three phases in a proactive threat hunting process: A trigger, an investigation and a resolution. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. The process of. Threat Hunting Process Document.
From www.researchgate.net
Threat Hunting Process from Scratch Download Scientific Diagram Threat Hunting Process Document The process of proactive cyber threat hunting typically involves three steps: An initial trigger phase, followed by an investigation, and ending. Threat hunting is a proactive and iterative approach to detecting threats. It falls under the active defense category of. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to. Threat Hunting Process Document.
From socradar.io
What are Threat Hunting Tools? SOCRadar® Cyber Intelligence Inc. Threat Hunting Process Document Threat hunting is a proactive and iterative approach to detecting threats. An initial trigger phase, followed by an investigation, and ending. There are three phases in a proactive threat hunting process: The process of proactive cyber threat hunting typically involves three steps: Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s. Threat Hunting Process Document.
From www.blusapphire.com
The Complete Guide To Threat Hunting Threat Hunting Process Document A trigger, an investigation and a resolution. It falls under the active defense category of. The process of proactive cyber threat hunting typically involves three steps: An initial trigger phase, followed by an investigation, and ending. Threat hunting is a proactive and iterative approach to detecting threats. There are three phases in a proactive threat hunting process: Threat hunting is. Threat Hunting Process Document.
From www.crowdstrike.com
What is Cyber Threat Hunting? [Proactive Guide] CrowdStrike Threat Hunting Process Document Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. A trigger, an investigation and a resolution. There are three phases in a proactive threat hunting process: An initial trigger phase, followed by an investigation, and ending. It falls under the active defense category of. The process of. Threat Hunting Process Document.
From innovatecybersecurity.com
A Threat Hunting Primer Innovate Cybersecurity Threat Advisory Threat Hunting Process Document A trigger, an investigation and a resolution. Threat hunting is a proactive and iterative approach to detecting threats. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. An initial trigger phase, followed by an investigation, and ending. There are three phases in a proactive threat hunting process:. Threat Hunting Process Document.
From www.splunk.com
Introducing the PEAK Threat Hunting Framework Splunk Threat Hunting Process Document The process of proactive cyber threat hunting typically involves three steps: Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. A trigger, an investigation and a resolution. It falls under the active defense category of. There are three phases in a proactive threat hunting process: Threat hunting. Threat Hunting Process Document.
From proinf.com
Cyber Threat Hunting 101 Guide Methods, Tools, Techniques & Frameworks Threat Hunting Process Document Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. There are three phases in a proactive threat hunting process: The process of proactive cyber threat hunting typically involves three steps: A trigger, an investigation and a resolution. Threat hunting is a proactive and iterative approach to detecting. Threat Hunting Process Document.
From socprime.com
Threat Hunting Maturity Model Explained With Examples SOC Prime Threat Hunting Process Document The process of proactive cyber threat hunting typically involves three steps: There are three phases in a proactive threat hunting process: Threat hunting is a proactive and iterative approach to detecting threats. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. An initial trigger phase, followed by. Threat Hunting Process Document.
From www.packtpub.com
The Foundations of Threat Hunting Packt Threat Hunting Process Document There are three phases in a proactive threat hunting process: A trigger, an investigation and a resolution. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. It falls under the active defense category of. An initial trigger phase, followed by an investigation, and ending. The process of. Threat Hunting Process Document.
From thecyphere.com
Threat Hunting Process, Methodologies, Tools And Tips Threat Hunting Process Document Threat hunting is a proactive and iterative approach to detecting threats. A trigger, an investigation and a resolution. An initial trigger phase, followed by an investigation, and ending. There are three phases in a proactive threat hunting process: It falls under the active defense category of. The process of proactive cyber threat hunting typically involves three steps: Threat hunting is. Threat Hunting Process Document.
From www.dts-solution.com
The Basics of Threat Hunting Threat Hunting Process Document Threat hunting is a proactive and iterative approach to detecting threats. An initial trigger phase, followed by an investigation, and ending. It falls under the active defense category of. A trigger, an investigation and a resolution. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. The process. Threat Hunting Process Document.
From threatcop.com
Threat Hunting What is it and How is it Done? ThreatCop Threat Hunting Process Document An initial trigger phase, followed by an investigation, and ending. There are three phases in a proactive threat hunting process: Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. It falls under the active defense category of. Threat hunting is a proactive and iterative approach to detecting. Threat Hunting Process Document.
From www.logpoint.com
What is Cyber Threat Hunting? A simple guide to Threat Hunting Threat Hunting Process Document Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. A trigger, an investigation and a resolution. There are three phases in a proactive threat hunting process: An initial trigger phase, followed by an investigation, and ending. Threat hunting is a proactive and iterative approach to detecting threats.. Threat Hunting Process Document.
From www.crowdstrike.com
Could you be a threat hunter? Humio and Corelight make it easy for Threat Hunting Process Document An initial trigger phase, followed by an investigation, and ending. It falls under the active defense category of. Threat hunting is a proactive and iterative approach to detecting threats. There are three phases in a proactive threat hunting process: Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify. Threat Hunting Process Document.
From www.zippyops.com
5Step Cyber Threat Hunting Process Threat Hunting Process Document An initial trigger phase, followed by an investigation, and ending. There are three phases in a proactive threat hunting process: A trigger, an investigation and a resolution. Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. The process of proactive cyber threat hunting typically involves three steps:. Threat Hunting Process Document.
From socradar.io
Step by Step Threat Hunting SOCRadar® Cyber Intelligence Inc. Threat Hunting Process Document A trigger, an investigation and a resolution. It falls under the active defense category of. The process of proactive cyber threat hunting typically involves three steps: Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. Threat hunting is a proactive and iterative approach to detecting threats. An. Threat Hunting Process Document.
From www.sangfor.com
Cyber Threat Hunting Definition, Techniques, and Solutions Threat Hunting Process Document An initial trigger phase, followed by an investigation, and ending. The process of proactive cyber threat hunting typically involves three steps: Threat hunting is a process usually followed by security analysts to search for such anomalies in an organization’s environment to identify cyber. Threat hunting is a proactive and iterative approach to detecting threats. There are three phases in a. Threat Hunting Process Document.