Application Access Controls . access control is an essential element of security that determines who is allowed to access certain data, apps, and. access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. mandatory access control (mac) is a security model that enforces tight security and access control through a. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. These limit access to the application system to authorized users, ip addresses, or applications.
from learn.microsoft.com
access control is an essential element of security that determines who is allowed to access certain data, apps, and. access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. These limit access to the application system to authorized users, ip addresses, or applications. mandatory access control (mac) is a security model that enforces tight security and access control through a. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access.
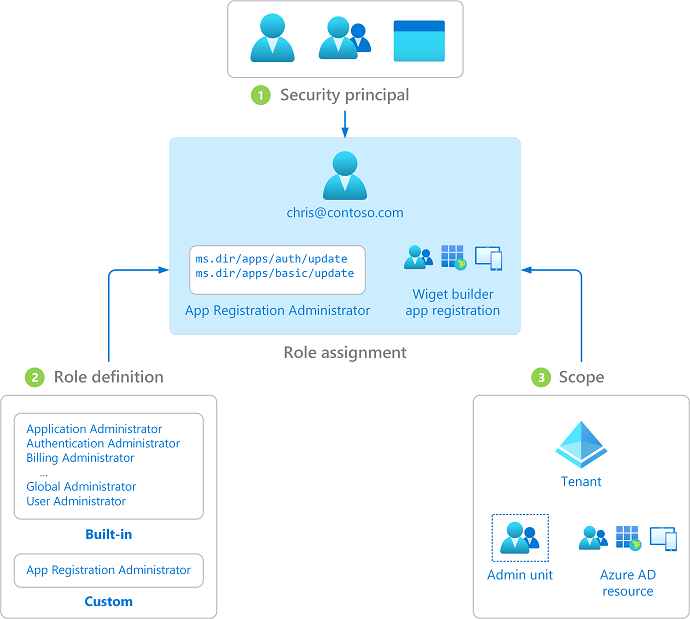
Overview of Microsoft Entra rolebased access control (RBAC
Application Access Controls access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. access control is an essential element of security that determines who is allowed to access certain data, apps, and. mandatory access control (mac) is a security model that enforces tight security and access control through a. These limit access to the application system to authorized users, ip addresses, or applications. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy.
From budibase.com
RoleBased Access Control Ultimate Guide Application Access Controls access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. mandatory access control (mac). Application Access Controls.
From www.spectra-vision.com
Why Access Control And Attendance Management Via Mobile App Is Application Access Controls These limit access to the application system to authorized users, ip addresses, or applications. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. access control is an essential element of security that determines who is allowed to access certain data, apps, and. access control design. Application Access Controls.
From www.scribd.com
Application Access Controls Governor Implementation Guide 8.2.0 PDF Application Access Controls access control is an essential element of security that determines who is allowed to access certain data, apps, and. mandatory access control (mac) is a security model that enforces tight security and access control through a. access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control, also known. Application Access Controls.
From www.visual-guard.com
Identity and Access Management Best Practices for Application Security Application Access Controls access control is an essential element of security that determines who is allowed to access certain data, apps, and. access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. These limit. Application Access Controls.
From www.slideteam.net
Role Based Access Control RBAC Flow Chart PPT Example Application Access Controls These limit access to the application system to authorized users, ip addresses, or applications. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. access control design patterns provide. Application Access Controls.
From jaycemeowcunningham.blogspot.com
What Function Describe the Uses of an Access Control List Application Access Controls mandatory access control (mac) is a security model that enforces tight security and access control through a. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. access control design patterns provide developers with guidelines and best practices for implementing effective access control. These limit access to the application system. Application Access Controls.
From digestley.com
Understanding Access Control And How To Implement It Application Access Controls These limit access to the application system to authorized users, ip addresses, or applications. access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. mandatory access control (mac) is a security. Application Access Controls.
From searchcloudcomputing.techtarget.com
Secure data in the cloud with encryption and access controls Application Access Controls mandatory access control (mac) is a security model that enforces tight security and access control through a. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. access. Application Access Controls.
From www.microsemi.com
Applications Access Control Microsemi Application Access Controls access control design patterns provide developers with guidelines and best practices for implementing effective access control. These limit access to the application system to authorized users, ip addresses, or applications. access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. mandatory access control (mac) is a security model. Application Access Controls.
From www.researchgate.net
A typical architecture of an access control system. Download Application Access Controls mandatory access control (mac) is a security model that enforces tight security and access control through a. These limit access to the application system to authorized users, ip addresses, or applications. access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control, also known as authorization — is mediating access. Application Access Controls.
From www.slideserve.com
PPT Auditing Application Controls PowerPoint Presentation, free Application Access Controls access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. mandatory access. Application Access Controls.
From dxolovigi.blob.core.windows.net
Logical Access Control Definition at Ron Vang blog Application Access Controls access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. mandatory access control (mac) is a security model that enforces tight security and access control through a. access control is an. Application Access Controls.
From www.digitalid.co.uk
The Complete Guide to Mobile Access Control Digital ID Application Access Controls access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. These limit access to the application system to authorized users, ip addresses, or applications. access control is an essential element of security that determines who is allowed to access certain data, apps, and. access control, also known as authorization —. Application Access Controls.
From www.youtube.com
Types of access control lists explained Standard, Extended, Numbered Application Access Controls mandatory access control (mac) is a security model that enforces tight security and access control through a. access control is an essential element of security that determines who is allowed to access certain data, apps, and. access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control is a. Application Access Controls.
From www.visual-guard.com
Identity and Access Management Best Practices for Application Security Application Access Controls access control is an essential element of security that determines who is allowed to access certain data, apps, and. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy.. Application Access Controls.
From www.pinterest.co.uk
ISO 27001 Annex A.9.4 System and Application Access Control Application Access Controls access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. mandatory access control (mac) is a security model that enforces tight security and access control through a. These limit access to the application system to authorized users, ip addresses, or applications. access control is an essential element of security that. Application Access Controls.
From duo.com
Application Access Policies Duo Security Application Access Controls mandatory access control (mac) is a security model that enforces tight security and access control through a. access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. These limit access to the application system to authorized users, ip addresses, or applications. access control, also known as authorization —. Application Access Controls.
From www.vrogue.co
Types Of Access Control System Infographics Access Control System Vrogue Application Access Controls access control is an essential element of security that determines who is allowed to access certain data, apps, and. access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. access control acts as. Application Access Controls.
From blog.soliditech.com
Five Best Practices for Access Control Application Access Controls mandatory access control (mac) is a security model that enforces tight security and access control through a. access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. access control, also known. Application Access Controls.
From atuldewangan.medium.com
RoleBased Access Control (RBAC). RoleBased Access Control (RBAC) by Application Access Controls access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. mandatory access control (mac) is a security model that enforces tight security and access control through a. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. access control is. Application Access Controls.
From www.nedapsecurity.com
The Ultimate Guide to Physical Access Control Systems in 2023 Application Access Controls access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital.. Application Access Controls.
From subscription.packtpub.com
User and groupbased application access management Mastering Identity Application Access Controls mandatory access control (mac) is a security model that enforces tight security and access control through a. access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control is a. Application Access Controls.
From efficientip.com
DNS Foundation of Application Access Control EfficientIP Application Access Controls access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. access control is an essential element of security that determines who is allowed to access certain data, apps, and. access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control,. Application Access Controls.
From identitymanagementinstitute.org
Access Control Matrix and Capability List Identity Management Institute® Application Access Controls access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. access control is an essential element of security that determines who is allowed to access certain data, apps, and. access control acts as a resolute layer of security that protects assets, applications, data and networks from. Application Access Controls.
From www.cctvminneapolis.com
Benefits of Access Control Application Access Controls mandatory access control (mac) is a security model that enforces tight security and access control through a. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. These limit access to the application system to authorized users, ip addresses, or applications. access control is an essential. Application Access Controls.
From www.360connect.com
5 Things You Need to Know About Access Control Software 360Connect Application Access Controls access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. These limit access to the application system to authorized users, ip addresses, or applications. access control is an essential element of security that determines. Application Access Controls.
From exogefltu.blob.core.windows.net
Access Control Policy Microsoft at Mary Thornton blog Application Access Controls access control is an essential element of security that determines who is allowed to access certain data, apps, and. These limit access to the application system to authorized users, ip addresses, or applications. mandatory access control (mac) is a security model that enforces tight security and access control through a. access control acts as a resolute layer. Application Access Controls.
From www.chiyu-tech.com
Application for Mobile Access Control Chiyu Professional Door Application Access Controls access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. These limit access to the application system to authorized users, ip addresses, or applications. access control acts as a resolute layer of security that. Application Access Controls.
From study.com
Access Control Types & Implementation Lesson Application Access Controls access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. mandatory access control (mac) is a security model that enforces tight security and access control through a. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. These limit access to. Application Access Controls.
From www.techtarget.com
What is Access Control? Application Access Controls mandatory access control (mac) is a security model that enforces tight security and access control through a. access control design patterns provide developers with guidelines and best practices for implementing effective access control. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. access control. Application Access Controls.
From learn.microsoft.com
Overview of Microsoft Entra rolebased access control (RBAC Application Access Controls access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. mandatory access control (mac) is a security model that enforces tight security and access control through a.. Application Access Controls.
From biznis-plus.com
What Is RoleBased Access Control? Here’s A Quick Guide For Every Application Access Controls access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. access control design patterns provide developers with guidelines and best practices for implementing effective access control. These. Application Access Controls.
From www.cdvi.co.uk
What is access control? Access control explained CDVI UK Application Access Controls access control acts as a resolute layer of security that protects assets, applications, data and networks from unauthorized access. These limit access to the application system to authorized users, ip addresses, or applications. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. mandatory access control (mac) is a security. Application Access Controls.
From cie-group.com
How to design an Access Control system Application Access Controls access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. access control is an essential element of security that determines who is allowed to access certain data, apps, and. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy.. Application Access Controls.
From howtomanagedevices.com
How To Change User Access Control (UAC) Settings In Windows 10 Device Application Access Controls mandatory access control (mac) is a security model that enforces tight security and access control through a. access control, also known as authorization — is mediating access to resources on the basis of identity and is generally policy. access control is a comprehensive data security mechanism that determines who is permitted to access specific digital. These limit. Application Access Controls.