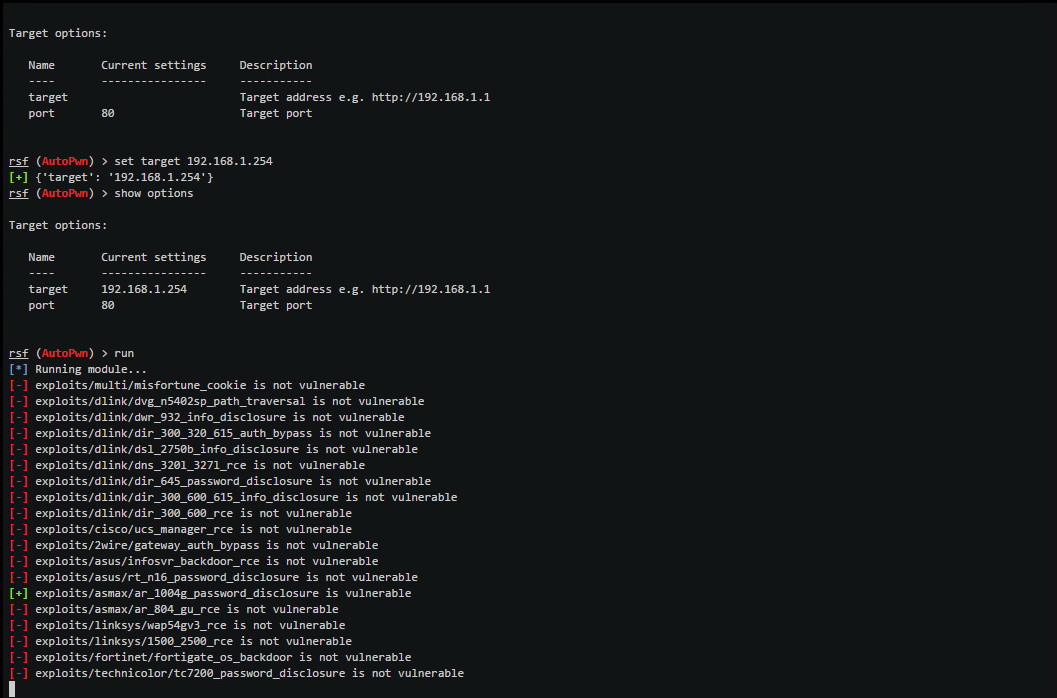
Routersploit Wordlist . Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before. Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path to. If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. While / may work in some cases, you may have to look at the requests your browser sends during login to determine the path (e.g. Exploitation framework for embedded devices. It consists of various modules that aids penetration testing operations:. It consists of various modules that aid penetration testing operations:. Contribute to threat9/routersploit development by creating an account on github.
from xakep.ru
It consists of various modules that aid penetration testing operations:. It consists of various modules that aids penetration testing operations:. Contribute to threat9/routersploit development by creating an account on github. Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path to. Exploitation framework for embedded devices. If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. While / may work in some cases, you may have to look at the requests your browser sends during login to determine the path (e.g. Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before.
Исследователи опубликовали на GitHub аналог Metasploit для роутеров — Хакер
Routersploit Wordlist Exploitation framework for embedded devices. If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. Exploitation framework for embedded devices. Contribute to threat9/routersploit development by creating an account on github. It consists of various modules that aids penetration testing operations:. Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. It consists of various modules that aid penetration testing operations:. While / may work in some cases, you may have to look at the requests your browser sends during login to determine the path (e.g. As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path to. Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before.
From www.hackers-arise.com
Routersploit Hacking the of Things (IoT) Routersploit Wordlist Exploitation framework for embedded devices. It consists of various modules that aid penetration testing operations:. Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path to. It consists of various modules that aids penetration testing operations:. If you want to evaluate the. Routersploit Wordlist.
From null-byte.wonderhowto.com
How to Seize Control of a Router with RouterSploit « Null Byte Routersploit Wordlist While / may work in some cases, you may have to look at the requests your browser sends during login to determine the path (e.g. As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. Routersploit has a number of exploits for different router models. Routersploit Wordlist.
From www.pinterest.com
How to Exploit Routers on an Unrooted Android Phone Android phone Routersploit Wordlist If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. While / may work in some cases, you may have to look at the requests your browser sends during login to determine the path (e.g. Exploitation framework for embedded devices. Find file blame history permalink new upstream version. Routersploit Wordlist.
From www.youtube.com
Exploit a Router Using RouterSploit [Tutorial] YouTube Routersploit Wordlist Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before. It consists of various modules that aid penetration testing operations:. While / may work in some cases, you may have to look at the requests your browser sends during login to determine the path (e.g. Find. Routersploit Wordlist.
From cyberpointsolution.com
Router and Switches Testing Tools Routersploit Framework Routersploit Wordlist Exploitation framework for embedded devices. Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before. Contribute to threat9/routersploit development by creating an account on github. It consists of various modules that aid penetration testing. Routersploit Wordlist.
From miloserdov.org
RouterSploit User Manual Ethical hacking and testing Routersploit Wordlist Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path to. It consists of various modules that aid penetration testing operations:. Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target. Routersploit Wordlist.
From bbs.kanxue.com
[原创]使用 RouterSploit Routersploit Wordlist Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. It consists of various modules that aid penetration testing operations:. As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. Contribute to threat9/routersploit development by creating an account on github. Exploitation framework for. Routersploit Wordlist.
From xakep.ru
Исследователи опубликовали на GitHub аналог Metasploit для роутеров — Хакер Routersploit Wordlist Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path to. While / may work in some cases, you may have to look at the requests your browser sends during login to determine the path (e.g. As you can see, this module. Routersploit Wordlist.
From null-byte.wonderhowto.com
How to Seize Control of a Router with RouterSploit « Null Byte Routersploit Wordlist It consists of various modules that aid penetration testing operations:. While / may work in some cases, you may have to look at the requests your browser sends during login to determine the path (e.g. As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist.. Routersploit Wordlist.
From techglobal7894.blogspot.com
how to hack wifi using routersploit in termux (without root) 2021. Best Routersploit Wordlist As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. It consists of various modules that aids penetration testing operations:. Let's leave that default setting, but we could use any wordlist from kali. Routersploit Wordlist.
From miloserdov.org
RouterSploit User Manual Ethical hacking and testing Routersploit Wordlist Exploitation framework for embedded devices. While / may work in some cases, you may have to look at the requests your browser sends during login to determine the path (e.g. Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before. As you can see, this module. Routersploit Wordlist.
From techglobal7894.blogspot.com
how to hack wifi using routersploit in termux (without root) 2021. Best Routersploit Wordlist As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before. It consists of various modules that aid penetration testing operations:. Let's. Routersploit Wordlist.
From www.freebuf.com
RouterSploit:一款功能强大的嵌入式设备渗透测试框架 FreeBuf网络安全行业门户 Routersploit Wordlist Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. Exploitation framework for embedded devices. If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you. Routersploit Wordlist.
From justaskittotheask.blogspot.com
Hacking WiFi using Termux on Android PART 1 Routersploit Wordlist If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. It consists of various modules that aids penetration testing operations:. Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path. Routersploit Wordlist.
From gbhackers.com
Exploitation Framework for Embedded devices RouterSploit Routersploit Wordlist It consists of various modules that aid penetration testing operations:. It consists of various modules that aids penetration testing operations:. Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. Routersploit has a number of exploits. Routersploit Wordlist.
From albadarcyber.blogspot.com
Cara Install Routersploit Di Android No Root (Termux) Albadar Cyber Routersploit Wordlist If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. While / may work in some cases, you may have to look at the requests your browser sends during login to determine the path (e.g. Contribute to threat9/routersploit development by creating an account on github. Find file blame. Routersploit Wordlist.
From null-byte.wonderhowto.com
How to Exploit Routers on an Unrooted Android Phone « Null Byte Routersploit Wordlist While / may work in some cases, you may have to look at the requests your browser sends during login to determine the path (e.g. It consists of various modules that aid penetration testing operations:. Contribute to threat9/routersploit development by creating an account on github. Routersploit has a number of exploits for different router models and they have the ability. Routersploit Wordlist.
From www.pinterest.com
How to Exploit Routers on an Unrooted Android Phone Router, Android Routersploit Wordlist As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. While / may work in some cases, you may have to look at the requests your browser sends during login to determine the path (e.g. Contribute to threat9/routersploit development by creating an account on github.. Routersploit Wordlist.
From www.bilibili.com
安卓手机通过termux免Root运行Routersploit对路由器进行渗透【渗透工具】 哔哩哔哩 Routersploit Wordlist Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path to. As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. It consists of various modules that. Routersploit Wordlist.
From iemlabs.com
RouterSploit Cybersecurity Tool IEMLabs Blog Knowledge Base Routersploit Wordlist If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. Contribute. Routersploit Wordlist.
From miloserdov.org
RouterSploit User Manual Ethical hacking and testing Routersploit Wordlist It consists of various modules that aids penetration testing operations:. It consists of various modules that aid penetration testing operations:. Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before. If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen. Routersploit Wordlist.
From blog.eldernode.com
Introducing And Install RouterSploit On Kali Linux Eldernode Blog Routersploit Wordlist Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. Contribute to threat9/routersploit development by creating an account on github. It consists of various modules that aid penetration testing operations:. Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before. If you want to. Routersploit Wordlist.
From hackwaretutorial.blogspot.com
Hack a router from an android phone Routersploit Wordlist It consists of various modules that aid penetration testing operations:. Exploitation framework for embedded devices. Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. Contribute to threat9/routersploit development by creating an account on github. If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. It. Routersploit Wordlist.
From www.cyberpunk.rs
Router Exploitation Framework RouterSploit CYBERPUNK Routersploit Wordlist Exploitation framework for embedded devices. It consists of various modules that aids penetration testing operations:. If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. Contribute to threat9/routersploit development by creating an account on github. Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. Routersploit. Routersploit Wordlist.
From github.com
GitHub threat9/routersploit Exploitation Framework for Embedded Devices Routersploit Wordlist If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. Contribute to threat9/routersploit development by creating an account on github. Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path. Routersploit Wordlist.
From www.prodefence.org
routersploit v3.2.0 released Router Exploitation Framework Routersploit Wordlist It consists of various modules that aids penetration testing operations:. Exploitation framework for embedded devices. Contribute to threat9/routersploit development by creating an account on github. If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. As. Routersploit Wordlist.
From www.pinterest.com
How to Exploit Routers on an Unrooted Android Phone Android phone Routersploit Wordlist Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before. As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. Let's leave that default setting, but we could use any wordlist. Routersploit Wordlist.
From securitytwins.com
RouterSploit Framework para la auditoría de routers Security Twins Routersploit Wordlist If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path to. It consists of various modules that aid penetration testing. Routersploit Wordlist.
From linuxsecurityblog.com
Exploiting Routers With Routersploit ls /blog Routersploit Wordlist It consists of various modules that aids penetration testing operations:. Contribute to threat9/routersploit development by creating an account on github. Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path to. While / may work in some cases, you may have to. Routersploit Wordlist.
From simplypsychology.org
Beismerni ó, drágám Susteen technicolor router feltörés mozi Esemény Routersploit Wordlist Exploitation framework for embedded devices. If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. As you can see, this module simply requires that we enter the target ip address and it has a built in password list at /root/routersploit/routersploit/resources/wordlist. Routersploit has a number of exploits for different. Routersploit Wordlist.
From pentesttools.net
RouterSploit v3.4.0 Exploitation Framework For Embedded Devices Routersploit Wordlist It consists of various modules that aid penetration testing operations:. If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before. While / may work. Routersploit Wordlist.
From www.youtube.com
RouterSploit Exploitation Framework for Embedded Devices Latest Routersploit Wordlist Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. It consists of various modules that aids penetration testing operations:. If you want to evaluate the security of some devices (routers, cameras, etc.) and perform pen test, you can use routersploit framework. Let's leave that default setting, but we could use any wordlist from kali or one we. Routersploit Wordlist.
From pentestcore.com
آموزش ابزار RouterSploit در تست نفوذ پن تست کور Routersploit Wordlist Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path to. It consists of various modules that aid penetration testing operations:. While / may work in some cases, you may. Routersploit Wordlist.
From github.com
GitHub Ha3MrX/routersploit A router Sploit is the core of anyone's Routersploit Wordlist Let's leave that default setting, but we could use any wordlist from kali or one we have downloaded by simply setting the passwords variable to the absolute path to. Exploitation framework for embedded devices. It consists of various modules that aids penetration testing operations:. Routersploit has a number of exploits for different router models and they have the ability to. Routersploit Wordlist.
From www.youtube.com
RouterSploit Complete Tutorial YouTube Routersploit Wordlist It consists of various modules that aids penetration testing operations:. Find file blame history permalink new upstream version 3.4.0 · 792f5891 sophie. Routersploit has a number of exploits for different router models and they have the ability to check whether the remote target is vulnerable before. As you can see, this module simply requires that we enter the target ip. Routersploit Wordlist.