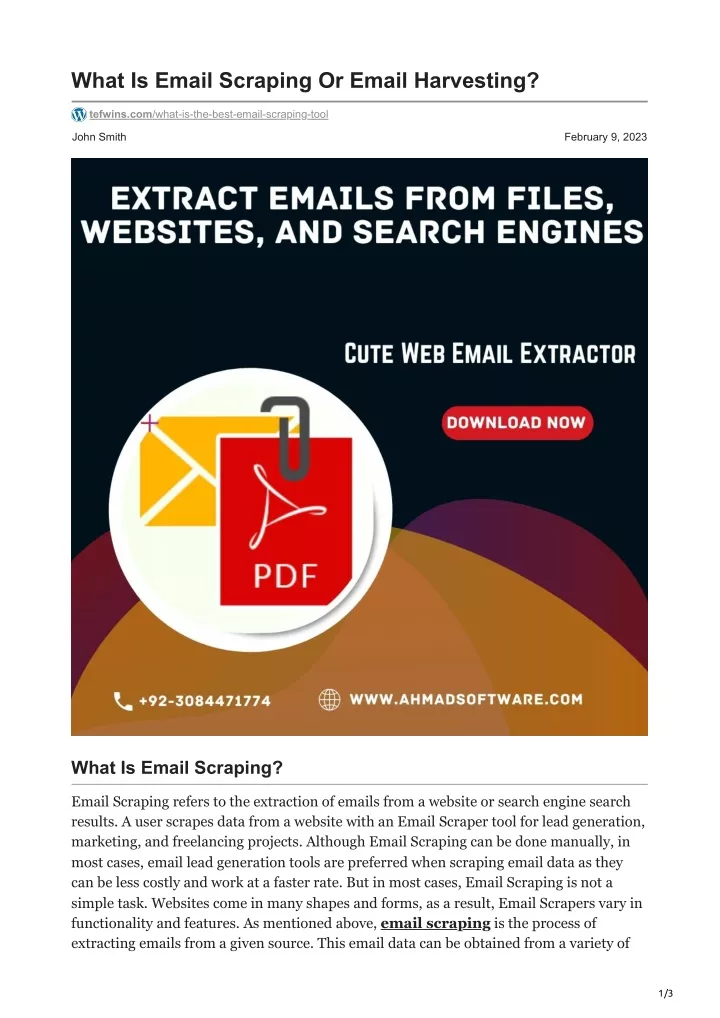
Email Harvesting Cwe . Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Behavior, property, technology, language, and. This feature alone can make it valuable to finding email addresses not captured by other tools. Behavior, property, technology, language, and. Email addresses disclosed is a information gathering vulnerability that occurs in web and api.
from www.slideserve.com
Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Behavior, property, technology, language, and. Email addresses disclosed is a information gathering vulnerability that occurs in web and api. This feature alone can make it valuable to finding email addresses not captured by other tools. Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions:
PPT 1What Is Email Scraping Or Email Harvesting PowerPoint
Email Harvesting Cwe Behavior, property, technology, language, and. Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: This feature alone can make it valuable to finding email addresses not captured by other tools. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Behavior, property, technology, language, and. Email addresses disclosed is a information gathering vulnerability that occurs in web and api.
From www.skyextractor.com
Email Harvesting Email Harvesting Cwe Behavior, property, technology, language, and. This feature alone can make it valuable to finding email addresses not captured by other tools. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Behavior, property, technology, language, and. Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those. Email Harvesting Cwe.
From www.template.net
Email Marketing Comprehensive Guide to A/B Testing in Emails Template Email Harvesting Cwe This feature alone can make it valuable to finding email addresses not captured by other tools. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Behavior, property, technology, language, and. Email addresses disclosed is a information gathering. Email Harvesting Cwe.
From community.ine.com
The Harvester tool not working as show in video email harvesting with Email Harvesting Cwe Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: This feature alone can make it valuable to finding email addresses not captured by other tools. Behavior, property, technology, language, and. Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Email addresses. Email Harvesting Cwe.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Cwe Behavior, property, technology, language, and. Behavior, property, technology, language, and. Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Base level weaknesses typically describe issues in terms of. Email Harvesting Cwe.
From www.alamy.com
Cwe logo hires stock photography and images Alamy Email Harvesting Cwe Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Email addresses disclosed is a information gathering vulnerability that occurs in web and api. This feature alone can make it valuable to finding email addresses not captured by other tools. Behavior, property, technology, language, and.. Email Harvesting Cwe.
From www.youtube.com
email harvesting software that generates leads YouTube Email Harvesting Cwe This feature alone can make it valuable to finding email addresses not captured by other tools. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Behavior, property, technology,. Email Harvesting Cwe.
From emotionstudios.net
"Get that bot away from me!" solutions to stop email harvesting Email Harvesting Cwe Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: This feature alone can make it valuable to finding email addresses not captured by other tools. Behavior, property, technology, language, and. Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their. Email Harvesting Cwe.
From ddapp.email
Please select your email platform from the list below Email Harvesting Cwe Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest. Email Harvesting Cwe.
From www.youtube.com
017 Email harvesting YouTube Email Harvesting Cwe This feature alone can make it valuable to finding email addresses not captured by other tools. Behavior, property, technology, language, and. Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Unlike some of the other email scraping tools, theharvester. Email Harvesting Cwe.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Cwe Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: This feature alone can make it valuable to finding email addresses not captured by other tools. Behavior, property, technology, language, and. Unlike some of the other email scraping. Email Harvesting Cwe.
From www.ahmadsoftware.com
Mastering Email Harvesting Unveiling the Top 4 Email Scraping Tools of Email Harvesting Cwe Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Behavior, property, technology, language, and. Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Unlike some of the. Email Harvesting Cwe.
From moosend.com
11 Best Email Marketing Software For [2024] Email Harvesting Cwe Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Behavior, property, technology, language, and.. Email Harvesting Cwe.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Cwe Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: This feature alone can make it valuable to finding email addresses not captured by other tools. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Email addresses disclosed is a information gathering vulnerability that occurs in web. Email Harvesting Cwe.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Cwe Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: This feature alone can make it valuable to finding email addresses not captured by other tools. Email addresses disclosed. Email Harvesting Cwe.
From www.phpkb.com
Harvesting emails from knowledge base Email Harvesting Cwe Behavior, property, technology, language, and. Behavior, property, technology, language, and. Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Unlike some of the. Email Harvesting Cwe.
From blackjacks360.blogspot.com
Email Harvesting Email Harvesting Cwe Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages.. Email Harvesting Cwe.
From null-byte.wonderhowto.com
Metasploit Tutorial Email Harvesting Android Termux « Null Byte Email Harvesting Cwe Behavior, property, technology, language, and. Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Unlike some of the. Email Harvesting Cwe.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Cwe Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their. Email Harvesting Cwe.
From www.youtube.com
Email Harvesting The Harvester YouTube Email Harvesting Cwe Behavior, property, technology, language, and. Behavior, property, technology, language, and. This feature alone can make it valuable to finding email addresses not captured by other tools. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those. Email Harvesting Cwe.
From www.youtube.com
Theharvester Email harvesting tool in kali linux YouTube Email Harvesting Cwe Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions:. Email Harvesting Cwe.
From www.guatewares.com
Guatewares Email harvesting Email Harvesting Cwe Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Behavior, property, technology, language, and. Behavior, property, technology, language, and. This feature alone can make it valuable to finding email addresses not captured by other tools. Unlike some of the. Email Harvesting Cwe.
From www.youtube.com
email harvesting with a lead generation software YouTube Email Harvesting Cwe This feature alone can make it valuable to finding email addresses not captured by other tools. Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Behavior, property, technology, language, and. Behavior, property, technology, language, and. Base level weaknesses typically. Email Harvesting Cwe.
From www.youtube.com
Email Harvesting in Kali Linux YouTube Email Harvesting Cwe Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: This feature alone can make it valuable to finding email addresses not captured by other tools. Behavior, property, technology, language, and. Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Base level weaknesses typically describe issues in terms of. Email Harvesting Cwe.
From www.flyingcowdesign.com
Email Harvesting Protection Services from Flying Cow Design Email Harvesting Cwe This feature alone can make it valuable to finding email addresses not captured by other tools. Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Behavior, property, technology, language, and. Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those. Email Harvesting Cwe.
From www.fastcompany.com
Email greetings, coronavirus Email Harvesting Cwe Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Behavior, property, technology, language, and. Behavior, property, technology, language, and. Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Base level weaknesses typically describe issues in terms of. Email Harvesting Cwe.
From wearefocus.co.uk
Why we all need to understand email security We Are Focus IT Email Harvesting Cwe Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Email addresses disclosed is a information gathering vulnerability that occurs in web and api.. Email Harvesting Cwe.
From www.pennyblacktemplates.com
Best Practices of Email Marketing for Small Businesses Pennyblack Email Harvesting Cwe Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. This feature alone can make it valuable to finding email addresses not captured by other tools. Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Behavior, property, technology, language, and.. Email Harvesting Cwe.
From www.youtube.com
Passive Reconnaissance Email Harvesting With theHarvester YouTube Email Harvesting Cwe Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions:. Email Harvesting Cwe.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Cwe Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Behavior, property, technology, language, and. Behavior, property, technology, language, and. Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp. Email Harvesting Cwe.
From www.slideserve.com
PPT Is Email Harvesting Good For Your Email Marketing Campaign Email Harvesting Cwe Behavior, property, technology, language, and. Behavior, property, technology, language, and. Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Email addresses disclosed is a information gathering vulnerability that. Email Harvesting Cwe.
From getwemail.io
Email Harvesting Everything You Need to Know About It weMail Email Harvesting Cwe Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Behavior, property, technology, language, and. Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Email addresses disclosed is a information gathering vulnerability that occurs in web and api.. Email Harvesting Cwe.
From www.interwijs.nl
Bescherm je emailadres tegen email harvesting Interwijs B.V. Email Harvesting Cwe Behavior, property, technology, language, and. Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: This feature alone can. Email Harvesting Cwe.
From huggingface.co
Email Generator a Hugging Face Space by Jayavathsan Email Harvesting Cwe Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Base level weaknesses typically describe issues in terms of 2 or 3 of the. Email Harvesting Cwe.
From www.slideserve.com
PPT 1What Is Email Scraping Or Email Harvesting PowerPoint Email Harvesting Cwe This feature alone can make it valuable to finding email addresses not captured by other tools. Base level weaknesses typically describe issues in terms of 2 or 3 of the following dimensions: Behavior, property, technology, language, and. Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their. Email Harvesting Cwe.
From www.youtube.com
Harvest Email Using theHarvester YouTube Email Harvesting Cwe Email addresses disclosed is a information gathering vulnerability that occurs in web and api. Behavior, property, technology, language, and. Unlike some of the other email scraping tools, theharvester utilizes pgp keyservers to harvest email addresses for those using pgp to encrypt their email messages. Behavior, property, technology, language, and. Base level weaknesses typically describe issues in terms of 2 or. Email Harvesting Cwe.