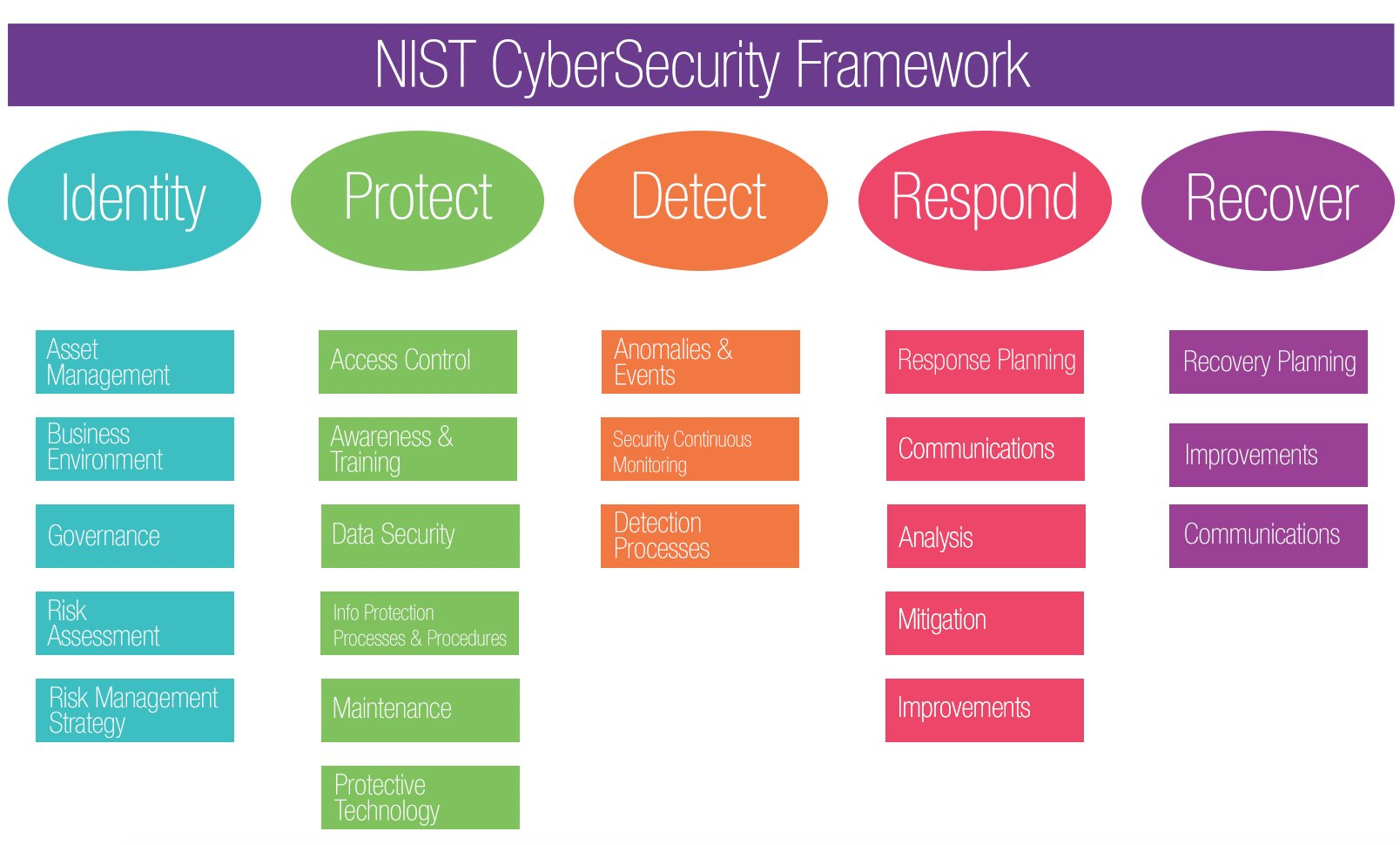
Nist Access Control Plan . Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Access control solution with abac architecture; Leads in the development of national and international identity and access management standards, guidance, best practices,. To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. Abac is a logical access control methodology where authorization to perform a set. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. This document provides federal agencies with a definition of attribute based access control (abac).
from www.aiophotoz.com
Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Access control solution with abac architecture; This document provides federal agencies with a definition of attribute based access control (abac). Abac is a logical access control methodology where authorization to perform a set. To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Leads in the development of national and international identity and access management standards, guidance, best practices,. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki.
The Cyber Security Hub On Twitter Nist Cybersecurity Framework Images
Nist Access Control Plan To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. This document provides federal agencies with a definition of attribute based access control (abac). Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. Leads in the development of national and international identity and access management standards, guidance, best practices,. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Abac is a logical access control methodology where authorization to perform a set. Access control solution with abac architecture; To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms.
From securityboulevard.com
Leveraging the NIST Cybersecurity Framework For Business Security Nist Access Control Plan Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. Access control solution with abac architecture; To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. This document provides federal agencies with a definition of attribute based access control (abac). Leads in the development of. Nist Access Control Plan.
From www.getastra.com
ISO 27001 vs NIST Standards All You Need To Know Nist Access Control Plan Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. Access control solution with abac architecture; To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. This publication provides. Nist Access Control Plan.
From www.zenarmor.com
What is NIST Cybersecurity Framework? Nist Access Control Plan Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Access control solution with abac architecture; This document provides federal agencies with a definition of attribute based access control (abac). Abac is a logical access control. Nist Access Control Plan.
From sprinto.com
An Ultimate Guide to NIST Access Controls Requirements Sprinto Nist Access Control Plan This document provides federal agencies with a definition of attribute based access control (abac). Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Leads in the development of national and international identity and access management standards, guidance, best practices,. Abac is a logical access control methodology where authorization to perform a set. To. Nist Access Control Plan.
From db-excel.com
Nist Sp 800 53 Rev 4 Spreadsheet — Nist Access Control Plan Access control solution with abac architecture; Leads in the development of national and international identity and access management standards, guidance, best practices,. Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Control (8) revocaon. Nist Access Control Plan.
From old.sermitsiaq.ag
Nist 800 171 Policy Templates Nist Access Control Plan Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Access control solution with abac architecture; Abac is a logical access control methodology where authorization to perform a set. This publication provides a catalog of security. Nist Access Control Plan.
From www.micoope.com.gt
The NIST Cybersecurity Framework Core (Part Of 3), 50 OFF Nist Access Control Plan Access control solution with abac architecture; To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Abac is a logical. Nist Access Control Plan.
From www.securityscientist.net
Don't be a sitting duck 7 steps to contingency planning from NIST Nist Access Control Plan To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. This publication provides a catalog of security and privacy. Nist Access Control Plan.
From www.nist.gov
NIST Risk Management Framework Aims to Improve Trustworthiness of Nist Access Control Plan Access control solution with abac architecture; Leads in the development of national and international identity and access management standards, guidance, best practices,. Abac is a logical access control methodology where authorization to perform a set. To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Control (8) revocaon of access authorizaons (9) controlled. Nist Access Control Plan.
From www.securityscientist.net
20 NIST Control Families Nist Access Control Plan Leads in the development of national and international identity and access management standards, guidance, best practices,. This document provides federal agencies with a definition of attribute based access control (abac). Abac is a logical access control methodology where authorization to perform a set. To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a.. Nist Access Control Plan.
From ikase.us
Free 30 Nist Security Assessment Plan Template In 2020 Security Nist Access Control Plan Abac is a logical access control methodology where authorization to perform a set. Access control solution with abac architecture; Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Leads in the development of national and. Nist Access Control Plan.
From flamlabelthema.netlify.app
Role Based Access Control Matrix Template Nist Access Control Plan Abac is a logical access control methodology where authorization to perform a set. Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Control (8) revocaon of access authorizaons (9) controlled release (10) audited override. Nist Access Control Plan.
From www.comparitech.com
NIST Cybersecurity Framework Guide 2024 Core, Implementation & Profile Nist Access Control Plan Leads in the development of national and international identity and access management standards, guidance, best practices,. This document provides federal agencies with a definition of attribute based access control (abac). Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Abac is a logical access control methodology where authorization to perform a set. This. Nist Access Control Plan.
From cybriant.com
NIST Cybersecurity Framework Cybriant Nist Access Control Plan Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. This document provides federal agencies with a definition of attribute based access control (abac). Abac is a logical access control methodology where authorization to perform. Nist Access Control Plan.
From delinea.com
NIST 80053 Privileged Access Management, Security and Privacy Nist Access Control Plan Leads in the development of national and international identity and access management standards, guidance, best practices,. Abac is a logical access control methodology where authorization to perform a set. Access control solution with abac architecture; This publication provides a catalog of security and privacy controls for information systems and organizations to protect. To solve the interoperability and policy enforcement problems. Nist Access Control Plan.
From sprinto.com
An Ultimate Guide to NIST Access Controls Requirements Sprinto Nist Access Control Plan To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. This publication provides a catalog of security and privacy. Nist Access Control Plan.
From consultdts.com
NIST SP 8001717 and CMMC DTS Nist Access Control Plan This document provides federal agencies with a definition of attribute based access control (abac). Access control solution with abac architecture; Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Leads in the development of national and international identity and access management standards, guidance, best practices,. Abac is a logical access control methodology where. Nist Access Control Plan.
From delinea.com
NIST 80053 Privileged Access Management, Security and Privacy Nist Access Control Plan Access control solution with abac architecture; Abac is a logical access control methodology where authorization to perform a set. Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. This publication provides a catalog of security. Nist Access Control Plan.
From www.tenable.com
NIST 80053 Configuration Auditing SC Report Template Tenable® Nist Access Control Plan This document provides federal agencies with a definition of attribute based access control (abac). Leads in the development of national and international identity and access management standards, guidance, best practices,. Abac is a logical access control methodology where authorization to perform a set. To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a.. Nist Access Control Plan.
From www.securityscientist.net
20 NIST Control Families Nist Access Control Plan Leads in the development of national and international identity and access management standards, guidance, best practices,. Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. This document provides federal agencies with a definition of attribute based access control (abac). Access control solution with abac architecture; This publication provides a catalog of. Nist Access Control Plan.
From www.aiophotoz.com
The Cyber Security Hub On Twitter Nist Cybersecurity Framework Images Nist Access Control Plan Abac is a logical access control methodology where authorization to perform a set. Access control solution with abac architecture; This document provides federal agencies with a definition of attribute based access control (abac). Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Leads in the development of national and international identity and access. Nist Access Control Plan.
From studylib.net
RMF Access Control Plan Nist Access Control Plan This document provides federal agencies with a definition of attribute based access control (abac). To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. Access control solution with abac architecture; Control (8) revocaon of access. Nist Access Control Plan.
From www.template.net
Access Plans Templates Format, Free, Download Nist Access Control Plan Access control solution with abac architecture; Abac is a logical access control methodology where authorization to perform a set. Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Leads in the development of national and international identity and access management standards, guidance, best practices,. This document provides federal agencies with a definition of. Nist Access Control Plan.
From youattest.com
NIST SP 80053 PR.AC1, User Access Reviews and Identity Security Nist Access Control Plan This document provides federal agencies with a definition of attribute based access control (abac). Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Leads in the development of national and international identity and access management standards, guidance, best practices,. Abac is a logical access control methodology where authorization to perform a set. Provides. Nist Access Control Plan.
From www.nist800171.com
NIST 800171 & CMMC Policies & Procedures Templates Nist Access Control Plan This document provides federal agencies with a definition of attribute based access control (abac). Abac is a logical access control methodology where authorization to perform a set. Access control solution with abac architecture; Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Provides increased assurance by signing attributes with private key infrastructure (pki). Nist Access Control Plan.
From templates.esad.edu.br
Nist 800171 Access Control Policy Template Nist Access Control Plan Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. This document provides federal agencies with a definition of attribute based access control (abac). Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. Abac is a logical access control methodology where authorization to perform a. Nist Access Control Plan.
From www.slideshare.net
NIST SP 800 30 Flow Chart Nist Access Control Plan Access control solution with abac architecture; This document provides federal agencies with a definition of attribute based access control (abac). This publication provides a catalog of security and privacy controls for information systems and organizations to protect. To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Control (8) revocaon of access authorizaons. Nist Access Control Plan.
From techzone.vmware.com
Workspace ONE Cloud Services Alignment with NIST SP 800171 VMware Nist Access Control Plan Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. This document provides federal agencies with a definition of attribute based access control (abac). Leads in the development of national and international identity and access management standards,. Nist Access Control Plan.
From www.contrapositionmagazine.com
Nist 800 171 Access Control Policy Template Template 1 Resume Nist Access Control Plan To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Leads in the development of national and international identity and access management standards, guidance, best practices,. This publication provides a catalog of security and privacy controls for information systems and organizations to protect. This document provides federal agencies with a definition of attribute. Nist Access Control Plan.
From www.enzoic.com
NIST Password Guidelines Best Practices Revealed Enzoic Nist Access Control Plan Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. This document provides federal agencies with a definition of attribute based access control (abac). This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Leads in the development of national and international identity and access management standards,. Nist Access Control Plan.
From sprinto.com
A Detailed Guide to NIST 80053 Standard Sprinto Nist Access Control Plan This document provides federal agencies with a definition of attribute based access control (abac). To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Access control solution with abac architecture; Leads in the development of national and international identity and access management standards, guidance, best practices,. Abac is a logical access control methodology. Nist Access Control Plan.
From templates.esad.edu.br
Nist 800171 Access Control Policy Template Nist Access Control Plan Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. Leads in the development of national and international identity and access management standards, guidance, best practices,. To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. This publication provides a catalog of security and privacy. Nist Access Control Plan.
From tutore.org
Nist System Security Plan Template Master of Documents Nist Access Control Plan Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Access control solution with abac architecture; This publication provides a catalog of security and privacy controls for information systems and organizations to protect. This document provides federal agencies with a definition of attribute based access control (abac). Abac is a logical access control methodology. Nist Access Control Plan.
From wesecureapp.com
Leveraging NIST Cybersecurity Framework For Business WeSecureApp Nist Access Control Plan Access control solution with abac architecture; Control (8) revocaon of access authorizaons (9) controlled release (10) audited override of access control mechanisms. Abac is a logical access control methodology where authorization to perform a set. To solve the interoperability and policy enforcement problems of today’s access control approaches, nist has developed a. Leads in the development of national and international. Nist Access Control Plan.
From cashier.mijndomein.nl
Access Control Policy Template Nist Nist Access Control Plan This publication provides a catalog of security and privacy controls for information systems and organizations to protect. Provides increased assurance by signing attributes with private key infrastructure (pki) and requiring users to authenticate with pki. Abac is a logical access control methodology where authorization to perform a set. Leads in the development of national and international identity and access management. Nist Access Control Plan.