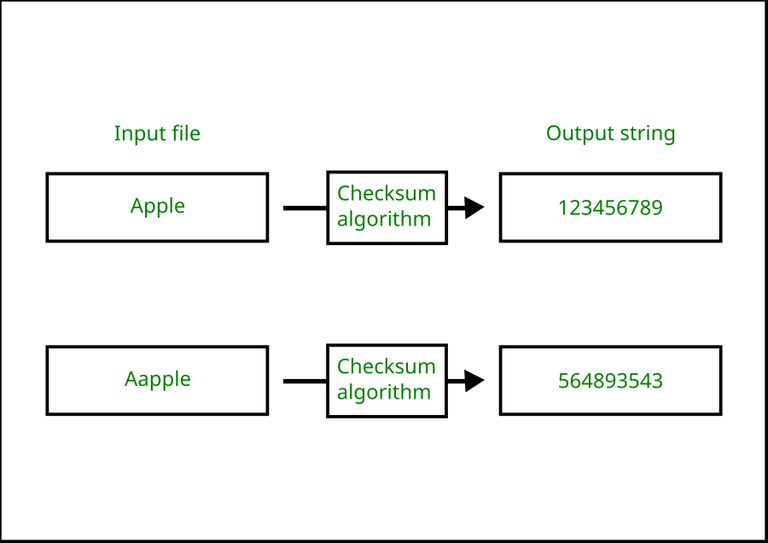
Standard Checksum Algorithm . Checksum is the error detection method used by upper layer protocols and is considered to be more reliable than lrc, vrc and crc. Overview of checksum algorithms and their purpose in detecting errors in data. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. Explanation of how checksum algorithms generate unique checksum values. To produce a checksum, you run a program that puts that file through an algorithm. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. This method makes the use of. Checksum programs work by running a file through an algorithm that uses. A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity.
from www.geeksforgeeks.org
This method makes the use of. Checksum programs work by running a file through an algorithm that uses. A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. Checksum is the error detection method used by upper layer protocols and is considered to be more reliable than lrc, vrc and crc. Overview of checksum algorithms and their purpose in detecting errors in data. To produce a checksum, you run a program that puts that file through an algorithm. Explanation of how checksum algorithms generate unique checksum values. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans.
How to Check a File Checksum in Linux
Standard Checksum Algorithm The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. This method makes the use of. To produce a checksum, you run a program that puts that file through an algorithm. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. Checksum programs work by running a file through an algorithm that uses. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. Explanation of how checksum algorithms generate unique checksum values. Checksum is the error detection method used by upper layer protocols and is considered to be more reliable than lrc, vrc and crc. Overview of checksum algorithms and their purpose in detecting errors in data.
From www.slideserve.com
PPT Search Algorithms Winter Semester 2004/2005 11 Oct 2004 1st Standard Checksum Algorithm Checksum programs work by running a file through an algorithm that uses. To produce a checksum, you run a program that puts that file through an algorithm. A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. This method makes the use of. Explanation of how checksum algorithms generate unique checksum. Standard Checksum Algorithm.
From linubezyx.weebly.com
Ip header checksum calculator linubezyX Standard Checksum Algorithm This method makes the use of. Explanation of how checksum algorithms generate unique checksum values. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans.. Standard Checksum Algorithm.
From www.youtube.com
Checksums The Luhn Algorithm for Verifying Credit Card Numbers YouTube Standard Checksum Algorithm A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. Checksum programs work by running a file through an algorithm that uses. A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. Overview of checksum algorithms and their purpose. Standard Checksum Algorithm.
From www.youtube.com
Checksum YouTube Standard Checksum Algorithm Overview of checksum algorithms and their purpose in detecting errors in data. A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. This method makes the use of. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. The. Standard Checksum Algorithm.
From freeloadsforme.weebly.com
freeloadsforme Blog Standard Checksum Algorithm Overview of checksum algorithms and their purpose in detecting errors in data. Checksum programs work by running a file through an algorithm that uses. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. The luhn algorithm or luhn formula, also known as the modulus 10 or mod. Standard Checksum Algorithm.
From www.slideserve.com
PPT Search Algorithms Winter Semester 2004/2005 11 Oct 2004 1st Standard Checksum Algorithm A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. Explanation of how checksum algorithms generate unique checksum values. To produce a checksum, you run a program that. Standard Checksum Algorithm.
From www.geeksforgeeks.org
How to Check a File Checksum in Linux Standard Checksum Algorithm Explanation of how checksum algorithms generate unique checksum values. Checksum programs work by running a file through an algorithm that uses. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. Checksum is the error detection method used by upper layer protocols and is considered to be more. Standard Checksum Algorithm.
From 9to5answer.com
[Solved] Robust and fast checksum algorithm? 9to5Answer Standard Checksum Algorithm The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. To produce a checksum, you run a program that puts that file through an algorithm. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file.. Standard Checksum Algorithm.
From ploraright.weebly.com
Checksum algorithm ploraright Standard Checksum Algorithm A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. Checksum is the error detection method used by upper layer protocols and is considered to be more reliable than lrc, vrc and crc. Overview of checksum algorithms and their purpose in detecting errors in data. A checksum is. Standard Checksum Algorithm.
From www.alpharithms.com
Checksum Simplified StepbyStep Calculation Guide αlphαrithms Standard Checksum Algorithm To produce a checksum, you run a program that puts that file through an algorithm. Overview of checksum algorithms and their purpose in detecting errors in data. Checksum programs work by running a file through an algorithm that uses. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm. Standard Checksum Algorithm.
From www.youtube.com
Checksum Algorithms and Majority Voting YouTube Standard Checksum Algorithm Explanation of how checksum algorithms generate unique checksum values. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. To produce a checksum, you run a program that. Standard Checksum Algorithm.
From www.youtube.com
Validating Credit Cards with Luhn Check Algorithm YouTube Standard Checksum Algorithm Explanation of how checksum algorithms generate unique checksum values. Checksum programs work by running a file through an algorithm that uses. This method makes the use of. Overview of checksum algorithms and their purpose in detecting errors in data. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm. Standard Checksum Algorithm.
From www.youtube.com
Code Review Custom checksum algorithm in Python (4 Solutions!!) YouTube Standard Checksum Algorithm Overview of checksum algorithms and their purpose in detecting errors in data. Checksum is the error detection method used by upper layer protocols and is considered to be more reliable than lrc, vrc and crc. This method makes the use of. A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity.. Standard Checksum Algorithm.
From www.alpharithms.com
Checksum Simplified StepbyStep Calculation Guide αlphαrithms Standard Checksum Algorithm A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. Checksum programs work by running a file through an algorithm that uses. Overview of checksum algorithms and their purpose. Standard Checksum Algorithm.
From instantgulu.weebly.com
instantgulu Blog Standard Checksum Algorithm To produce a checksum, you run a program that puts that file through an algorithm. Overview of checksum algorithms and their purpose in detecting errors in data. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. Checksum programs work by running a file through an algorithm that. Standard Checksum Algorithm.
From www.youtube.com
C++ Can this checksum algorithm be improved? YouTube Standard Checksum Algorithm Explanation of how checksum algorithms generate unique checksum values. To produce a checksum, you run a program that puts that file through an algorithm. A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named. Standard Checksum Algorithm.
From www.scaler.com
Error Detection and Correction in Computer Networks Scaler Topics Standard Checksum Algorithm Overview of checksum algorithms and their purpose in detecting errors in data. Checksum is the error detection method used by upper layer protocols and is considered to be more reliable than lrc, vrc and crc. Checksum programs work by running a file through an algorithm that uses. The luhn algorithm or luhn formula, also known as the modulus 10 or. Standard Checksum Algorithm.
From slideplayer.com
CIPHER SUITE Each name has an algorithm divided into four parts Standard Checksum Algorithm A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. Checksum is the error detection method used by upper layer protocols and is considered to be more reliable than lrc, vrc and crc. Explanation of how checksum algorithms generate unique checksum values. A checksum is a sequence of. Standard Checksum Algorithm.
From www.slideserve.com
PPT Oppenheimer Technologies PowerPoint Presentation, free download Standard Checksum Algorithm The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. To produce a checksum, you run a program that puts that file through an algorithm. This method makes the use of. Checksum is the error detection method used by upper layer protocols and is considered to be. Standard Checksum Algorithm.
From www.chegg.com
Solved Write a program to implement the checksum method. The Standard Checksum Algorithm Explanation of how checksum algorithms generate unique checksum values. This method makes the use of. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file.. Standard Checksum Algorithm.
From www.jcchouinard.com
What is Hashing (and how it works). Checksums, hash functions and more Standard Checksum Algorithm The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. Checksum programs work by running a file through an algorithm that uses. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. Explanation of how. Standard Checksum Algorithm.
From slideplayer.com
Reliability and Channel Coding ppt download Standard Checksum Algorithm This method makes the use of. Explanation of how checksum algorithms generate unique checksum values. Overview of checksum algorithms and their purpose in detecting errors in data. To produce a checksum, you run a program that puts that file through an algorithm. A checksum is a sequence of letters and numbers that you use to check a file’s validity and. Standard Checksum Algorithm.
From www.broadcastbeat.com
Using Checksum to Ensure the Integrity of Data Files Broadcast Beat Standard Checksum Algorithm Checksum is the error detection method used by upper layer protocols and is considered to be more reliable than lrc, vrc and crc. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. This method makes the use of. Checksum programs work by running a file through an. Standard Checksum Algorithm.
From www.numerade.com
SOLVED Question 3 IP Checksum The IP checksum only covers the header Standard Checksum Algorithm Checksum programs work by running a file through an algorithm that uses. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. Explanation of how checksum algorithms generate unique checksum values. Checksum is the error detection method used by upper layer protocols and is considered to be more. Standard Checksum Algorithm.
From www.slideserve.com
PPT CS433/533 Computer Networks PowerPoint Presentation, free Standard Checksum Algorithm The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. This method makes the use of. Overview of checksum algorithms and their purpose in detecting errors in data. Checksum is the error detection method used by upper layer protocols and is considered to be more reliable than. Standard Checksum Algorithm.
From www.scaler.com
What is Checksum? Scaler Topics Standard Checksum Algorithm To produce a checksum, you run a program that puts that file through an algorithm. Explanation of how checksum algorithms generate unique checksum values. Checksum programs work by running a file through an algorithm that uses. A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. This method makes the use. Standard Checksum Algorithm.
From medium.com
What is Checksum?. Visit systemdesign.us for System Design… by PB Standard Checksum Algorithm A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. To produce a checksum, you run a program that puts that file through an algorithm. Explanation of how checksum algorithms generate unique checksum values. Checksum is the error detection method used by upper layer protocols and is considered. Standard Checksum Algorithm.
From www.slideserve.com
PPT Computer Networks A Systems Approach, 5e Larry L. Peterson and Standard Checksum Algorithm The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. Checksum programs work by running a file through an algorithm that uses. A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. Overview of checksum algorithms and their. Standard Checksum Algorithm.
From www.slideserve.com
PPT Outline Encoding Framing Error Detection Sliding Window Algorithm Standard Checksum Algorithm A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. Explanation of how checksum algorithms generate unique checksum values. Checksum programs work by running a file through an algorithm that uses. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually. Standard Checksum Algorithm.
From www.aimodels.fyi
An Improved Modular Addition Checksum Algorithm AI Research Paper Details Standard Checksum Algorithm To produce a checksum, you run a program that puts that file through an algorithm. A checksum is a sequence of letters and numbers that you use to check a file’s validity and integrity. Overview of checksum algorithms and their purpose in detecting errors in data. This method makes the use of. Checksum programs work by running a file through. Standard Checksum Algorithm.
From m2pfintech.com
Validate Aadhaar numbers using the Verhoeff Algorithm in FlutterM2P Standard Checksum Algorithm A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. Overview of checksum algorithms and their purpose in detecting errors in data. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. Explanation of how. Standard Checksum Algorithm.
From www.qtuningtools.co.uk
SPECIFIC CHECKSUM ALGORITHM ECU Remapping and Chip Tuning Tools Standard Checksum Algorithm This method makes the use of. Checksum is the error detection method used by upper layer protocols and is considered to be more reliable than lrc, vrc and crc. To produce a checksum, you run a program that puts that file through an algorithm. Checksum programs work by running a file through an algorithm that uses. The luhn algorithm or. Standard Checksum Algorithm.
From www.slideserve.com
PPT Computer Networks Chapter 2 Getting Connected PowerPoint Standard Checksum Algorithm This method makes the use of. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. Checksum is the error detection method used by upper layer protocols and is considered to be more reliable than lrc, vrc and crc. A checksum is the result of running an. Standard Checksum Algorithm.
From www.upgrad.com
What is Checksum & How it Works? upGrad blog Standard Checksum Algorithm To produce a checksum, you run a program that puts that file through an algorithm. A checksum is the result of running an algorithm, called a cryptographic hash function, on a piece of data, usually a file. Checksum programs work by running a file through an algorithm that uses. The luhn algorithm or luhn formula, also known as the modulus. Standard Checksum Algorithm.
From www.geeksforgeeks.org
Understanding Checksum Algorithm for Data Integrity Standard Checksum Algorithm Checksum is the error detection method used by upper layer protocols and is considered to be more reliable than lrc, vrc and crc. The luhn algorithm or luhn formula, also known as the modulus 10 or mod 10 algorithm, named after its creator, ibm scientist hans. Overview of checksum algorithms and their purpose in detecting errors in data. This method. Standard Checksum Algorithm.