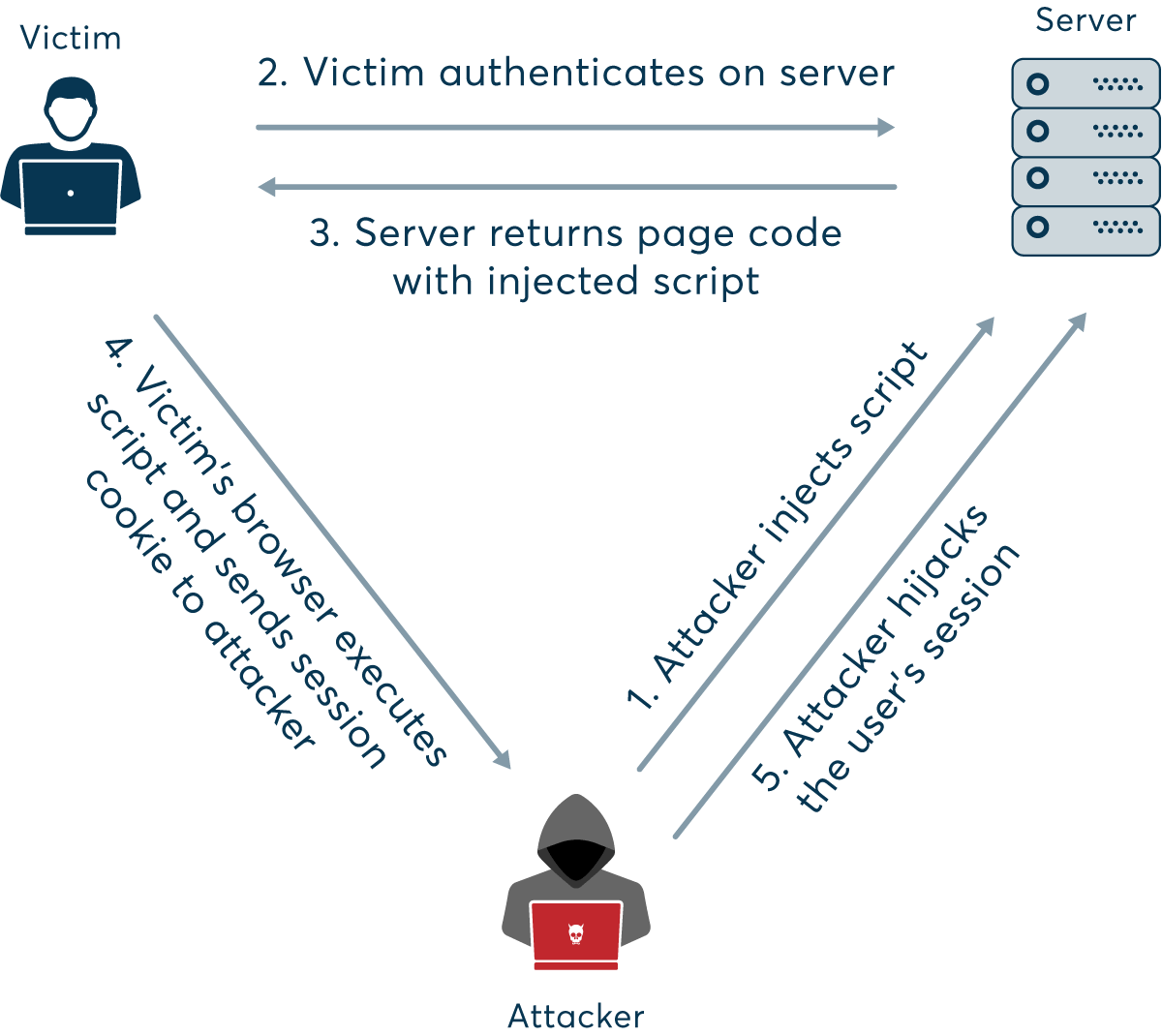
Cookie Attack Example . Examples of cookie theft can be found in various cyberattack scenarios. A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data. Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in. One notable instance involves phishing attacks, where attackers. The server then creates a session that is stored in a. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. Prevention against ‘pass the cookie’ attack.
from www.invicti.com
Prevention against ‘pass the cookie’ attack. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. The server then creates a session that is stored in a. Examples of cookie theft can be found in various cyberattack scenarios. A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data. Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in. One notable instance involves phishing attacks, where attackers.
What Is Session Hijacking? Invicti
Cookie Attack Example A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data. Prevention against ‘pass the cookie’ attack. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. Examples of cookie theft can be found in various cyberattack scenarios. The server then creates a session that is stored in a. One notable instance involves phishing attacks, where attackers. Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in.
From clerk.com
How HttpOnly cookies help mitigate XSS attacks Clerk Blog Cookie Attack Example Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in. One notable instance involves phishing attacks, where attackers. A typical example of a cookie use begins with a user entering their login credentials, which the server verifies. Cookie Attack Example.
From computersecuritypgp.blogspot.com
Computer Security and PGP What is Session Fixation Attack Cookie Attack Example The server then creates a session that is stored in a. Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks,. Cookie Attack Example.
From www.onelogin.com
Defending Against Session Cookie Replay Attacks OneLogin Cookie Attack Example The server then creates a session that is stored in a. One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data. Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to. Cookie Attack Example.
From www.slideserve.com
PPT Authentication and Session Management PowerPoint Presentation Cookie Attack Example A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. The server then creates a session that is stored in a. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. Prevention. Cookie Attack Example.
From www.slideserve.com
PPT Cookie Attack PowerPoint Presentation, free download ID12640877 Cookie Attack Example Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. Examples of cookie theft can be found in various cyberattack scenarios. One notable instance involves phishing attacks, where attackers. One specific attack method is cookie poisoning, also referred to as session hijacking, which. Cookie Attack Example.
From github.com
GitHub 1UC1F3R616/CookieAnalyzerandSessionHijack A tool to find Cookie Attack Example Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a.. Cookie Attack Example.
From www.vaadata.com
XSS Principles, Attacks and Security Best Practices Cookie Attack Example A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in. The server then creates a session. Cookie Attack Example.
From www.slideshare.net
𝐏𝐚𝐬𝐬𝐓𝐡𝐞𝐂𝐨𝐨𝐤𝐢𝐞 𝐀𝐭𝐭𝐚𝐜𝐤 PDF Cookie Attack Example Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in. Examples of cookie theft can be found in various cyberattack scenarios. The server then creates a session that is stored in a. One notable instance involves phishing. Cookie Attack Example.
From www.youtube.com
Does Storing JWT's In HTTP Only Cookies Stop XSS Attacks YouTube Cookie Attack Example Prevention against ‘pass the cookie’ attack. A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data. One notable instance involves phishing. Cookie Attack Example.
From debugpointer.com
Pass the Cookie Attack Types, Examples & Preventing it Cookie Attack Example One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. Cookie poisoning is a type. Cookie Attack Example.
From limevpn.com
Top 10 Most Common Types of Hacking Attacks LimeVPN Cookie Attack Example The server then creates a session that is stored in a. A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. Prevention against ‘pass the cookie’ attack. Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain. Cookie Attack Example.
From www.untitledblog.co.uk
How Dangerous Are Tracking Cookies? Cookie Attack Example Prevention against ‘pass the cookie’ attack. Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in. A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct.. Cookie Attack Example.
From www.cookieyes.com
How to Conduct a Cookie Audit for Cookie Compliance? Cookie Attack Example Examples of cookie theft can be found in various cyberattack scenarios. Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in. One notable instance involves phishing attacks, where attackers. One specific attack method is cookie poisoning, also. Cookie Attack Example.
From sulimanalruz.com
Ultimate Guide to HTTP Cookie Security, Attacks Prevention and Best Cookie Attack Example A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. Examples of cookie theft can be found in various cyberattack scenarios. One. Cookie Attack Example.
From emtmeta.com
What Is Cookie Poisoning? Best Cybersecurity and IT Technologies Cookie Attack Example A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. The server then creates a session that is stored in a. Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account,. Cookie Attack Example.
From www.makeuseof.com
What Is a PasstheCookie Attack? How to Stay Logged In to sites Safely Cookie Attack Example A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. Examples of cookie theft can be found in various cyberattack scenarios. One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data.. Cookie Attack Example.
From www.codecademy.com
Defending Node Applications from SQL Injection, XSS, & CSRF Attacks Cookie Attack Example One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data. Prevention against ‘pass the cookie’ attack. The server then creates a session that is stored in a. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges,. Cookie Attack Example.
From emtmeta.com
Understanding Cookie Poisoning Attacks Cookie Attack Example A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. Prevention against ‘pass the cookie’ attack. One specific attack method is cookie. Cookie Attack Example.
From www.acunetix.com
What Is Cookie Poisoning Cookie Attack Example One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data. Examples of cookie theft can be found in various cyberattack scenarios. Prevention against ‘pass the cookie’ attack. A typical example of a cookie use begins with a user entering their login credentials,. Cookie Attack Example.
From news.sophos.com
Cookie stealing the new perimeter bypass Sophos News Cookie Attack Example A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. Examples of cookie theft can be found in various cyberattack scenarios. One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data.. Cookie Attack Example.
From www.malcare.com
What is cookie stealing attack and how to prevent it? Cookie Attack Example One notable instance involves phishing attacks, where attackers. Prevention against ‘pass the cookie’ attack. A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back. Cookie Attack Example.
From hacker-hub8.blogspot.com
Hacker Hub 8 Cookie Attack Example Examples of cookie theft can be found in various cyberattack scenarios. Prevention against ‘pass the cookie’ attack. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. A typical example of a cookie use begins with a user entering their login credentials, which. Cookie Attack Example.
From www.invicti.com
What Is Session Hijacking? Invicti Cookie Attack Example Examples of cookie theft can be found in various cyberattack scenarios. Prevention against ‘pass the cookie’ attack. One notable instance involves phishing attacks, where attackers. The server then creates a session that is stored in a. One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server. Cookie Attack Example.
From www.invicti.com
What Is Session Hijacking? Invicti Cookie Attack Example One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data. Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account. Cookie Attack Example.
From www.youtube.com
Cookie Theft Ethical Hacking Cyber Security Explained in 15 Cookie Attack Example Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in. The server then creates a session that is stored in a. One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating. Cookie Attack Example.
From www.deviantart.com
Cookie attack! by shadowdragon975 on DeviantArt Cookie Attack Example One notable instance involves phishing attacks, where attackers. The server then creates a session that is stored in a. A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. Examples of cookie theft can be found in various cyberattack scenarios. One specific attack method is cookie poisoning, also referred. Cookie Attack Example.
From securityonline.info
Steal victim's cookie using Cross Site Scripting (XSS) Cookie Attack Example The server then creates a session that is stored in a. One notable instance involves phishing attacks, where attackers. Prevention against ‘pass the cookie’ attack. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. Cookie poisoning is a type of cyber attack. Cookie Attack Example.
From www.slideserve.com
PPT Cookie Attack PowerPoint Presentation, free download ID12640877 Cookie Attack Example One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data. The server then creates a session that is stored in a. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise. Cookie Attack Example.
From www.behance.net
Cookie Attack on Behance Cookie Attack Example One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data. Examples of cookie theft can be found in various cyberattack scenarios. One notable instance involves phishing attacks, where attackers. Cookie poisoning is a type of cyber attack in which a bad actor. Cookie Attack Example.
From www.geeksforgeeks.org
Cookie Tampering Techniques Cookie Attack Example A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. One specific attack method is cookie poisoning, also referred to as session. Cookie Attack Example.
From www.cyberghostvpn.com
How to Stop Replay Attacks Forever Cookie Attack Example The server then creates a session that is stored in a. Examples of cookie theft can be found in various cyberattack scenarios. Prevention against ‘pass the cookie’ attack. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. One notable instance involves phishing. Cookie Attack Example.
From docs.citrix.com
Cookie hijacking protection App Firewall Cookie Attack Example A typical example of a cookie use begins with a user entering their login credentials, which the server verifies are correct. One notable instance involves phishing attacks, where attackers. The server then creates a session that is stored in a. One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized. Cookie Attack Example.
From adhikariarjun.com.np
State based Attacks EAD Notes Cookie Attack Example Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. One specific attack method is cookie poisoning, also referred to as session hijacking, which entails manipulating cookies to gain unauthorized entry to a server and pilfer valuable data. Cookie poisoning is a type. Cookie Attack Example.
From www.youtube.com
Cookie attack YouTube Cookie Attack Example Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in.. Cookie Attack Example.
From www.loginworks.com
How to stop Cross Site Scripting(XSS) Attack Loginworks Cookie Attack Example One notable instance involves phishing attacks, where attackers. Cookie poisoning—also known as session hijacking—is an attack strategy in which the attacker alters, forges, hijacks, or otherwise poisons an otherwise valid cookie sent back to a. The server then creates a session that is stored in a. Cookie poisoning is a type of cyber attack in which a bad actor hijacks,. Cookie Attack Example.