Flask 2.1.2 Exploit Db . step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application If we can access to /console page, we may be able to execute rce. When all of the following conditions are met, a response containing. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. the werkzeug documentation warns users to never enable the debug console in production with or without a pin. flask is a lightweight wsgi web application framework. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. today, let’s discuss one of them, a vulnerability found in flask applications that can lead.
from www.doubtnut.com
If we can access to /console page, we may be able to execute rce. today, let’s discuss one of them, a vulnerability found in flask applications that can lead. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application the werkzeug documentation warns users to never enable the debug console in production with or without a pin. When all of the following conditions are met, a response containing. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. flask is a lightweight wsgi web application framework.
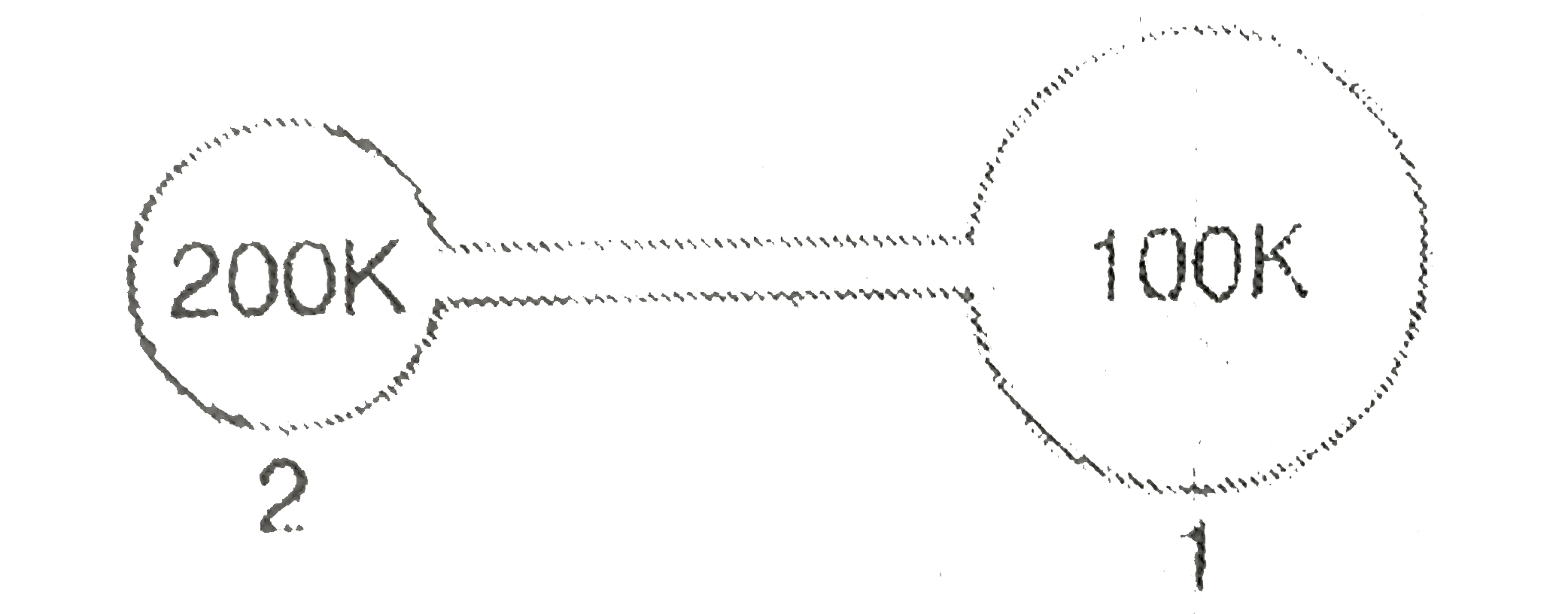
Figure shows two flasks connected to each other. The volume of flask 1
Flask 2.1.2 Exploit Db affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. If we can access to /console page, we may be able to execute rce. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application today, let’s discuss one of them, a vulnerability found in flask applications that can lead. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. flask is a lightweight wsgi web application framework. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. the werkzeug documentation warns users to never enable the debug console in production with or without a pin. When all of the following conditions are met, a response containing.
From morioh.com
Some New Features in Flask 2.0 Flask 2.1.2 Exploit Db If we can access to /console page, we may be able to execute rce. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. When all of the following conditions are met, a response containing. flask is a lightweight wsgi web application framework. affected versions of this package are. Flask 2.1.2 Exploit Db.
From imatt.top
flask mattのnote Flask 2.1.2 Exploit Db If we can access to /console page, we may be able to execute rce. When all of the following conditions are met, a response containing. today, let’s discuss one of them, a vulnerability found in flask applications that can lead. flask is a lightweight wsgi web application framework. step by step example of cracking a flask/werkzeug pin. Flask 2.1.2 Exploit Db.
From seekicon.com
Flask 2 icon svg png free download Flask 2.1.2 Exploit Db affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application today, let’s discuss one of them, a vulnerability found in flask applications that can lead. flask is a lightweight wsgi. Flask 2.1.2 Exploit Db.
From blog.appseed.us
Flask 2.x Release With Free Samples Flask 2.1.2 Exploit Db affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. If we can access to /console page, we may be able to execute rce. flask is a lightweight wsgi web application framework. the werkzeug documentation warns users to never enable the debug console in production with or without a. Flask 2.1.2 Exploit Db.
From academy.elice.io
Python 웹 개발 Flask 기초 II 엘카데미 AI시대 생존을 위한 첫 사수! Flask 2.1.2 Exploit Db today, let’s discuss one of them, a vulnerability found in flask applications that can lead. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application When all of the following conditions. Flask 2.1.2 Exploit Db.
From auth0.com
What's new in Flask 2.0 Flask 2.1.2 Exploit Db the werkzeug documentation warns users to never enable the debug console in production with or without a pin. flask is a lightweight wsgi web application framework. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. When all of the following conditions are met, a response containing. today,. Flask 2.1.2 Exploit Db.
From www.walmart.com
2 PCS Flask Holder Test Tube Holder Test Tube Clamp Spring Steel Test Flask 2.1.2 Exploit Db the werkzeug documentation warns users to never enable the debug console in production with or without a pin. today, let’s discuss one of them, a vulnerability found in flask applications that can lead. flask is a lightweight wsgi web application framework. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm. Flask 2.1.2 Exploit Db.
From exoieatfe.blob.core.windows.net
Best Thermos Flask 2 Litre at Iris Lett blog Flask 2.1.2 Exploit Db When all of the following conditions are met, a response containing. today, let’s discuss one of them, a vulnerability found in flask applications that can lead. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application affected versions of this package are vulnerable to information exposure in the form. Flask 2.1.2 Exploit Db.
From auth0.com
Using Python, Flask, and Angular to Build Modern Apps Part 2 Flask 2.1.2 Exploit Db flask is a lightweight wsgi web application framework. the werkzeug documentation warns users to never enable the debug console in production with or without a pin. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. step by step example of cracking a flask/werkzeug pin after finding an. Flask 2.1.2 Exploit Db.
From zeeposa.blogg.se
zeeposa.blogg.se Flask app builder examples Flask 2.1.2 Exploit Db affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. the werkzeug documentation warns users to never enable the debug console in production with or without a pin. When all of the following conditions are met, a response containing. flask is a lightweight wsgi web application framework. If we. Flask 2.1.2 Exploit Db.
From academy.elice.io
Python 웹 개발 Flask 기초 II 엘카데미 AI시대 생존을 위한 첫 사수! Flask 2.1.2 Exploit Db today, let’s discuss one of them, a vulnerability found in flask applications that can lead. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. When all of the following conditions are met, a response containing. step by step example of cracking a flask/werkzeug pin after finding an lfi. Flask 2.1.2 Exploit Db.
From planetscale.com
Setting up the Flask project — MySQL for Python Developers — Flask 2.1.2 Exploit Db today, let’s discuss one of them, a vulnerability found in flask applications that can lead. flask is a lightweight wsgi web application framework. If we can access to /console page, we may be able to execute rce. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application the. Flask 2.1.2 Exploit Db.
From exonlumwk.blob.core.windows.net
What Is The Erlenmeyer Flask Used For at Christy Chavez blog Flask 2.1.2 Exploit Db When all of the following conditions are met, a response containing. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. today, let’s discuss one of them, a vulnerability found in flask applications that can lead. If we can access to /console page, we may be able to execute rce.. Flask 2.1.2 Exploit Db.
From www.doubtnut.com
Figure shows two flasks connected to each other. The volume of flask 1 Flask 2.1.2 Exploit Db the werkzeug documentation warns users to never enable the debug console in production with or without a pin. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. the suggestion. Flask 2.1.2 Exploit Db.
From stackoverflow.com
python WTForms Validators not Working except DataRequired() Stack Flask 2.1.2 Exploit Db today, let’s discuss one of them, a vulnerability found in flask applications that can lead. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. flask is a lightweight wsgi. Flask 2.1.2 Exploit Db.
From morioh.com
Deploying Models to Flask Flask 2.1.2 Exploit Db today, let’s discuss one of them, a vulnerability found in flask applications that can lead. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. flask is a lightweight wsgi. Flask 2.1.2 Exploit Db.
From medium.com
Build the first Flask Python web app framework by Chirag Samal Flask 2.1.2 Exploit Db When all of the following conditions are met, a response containing. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. If we can access to /console page, we may be able to execute rce. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside. Flask 2.1.2 Exploit Db.
From morioh.com
Flask 2.0, Werkzeug 2.0, Jinja 3.0, Click 8.0, ItsDangerous 2.0, and Flask 2.1.2 Exploit Db the werkzeug documentation warns users to never enable the debug console in production with or without a pin. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application flask is. Flask 2.1.2 Exploit Db.
From martinezexterais.blogspot.com
Flask App Automatically Get Request Again Martinez Exterais Flask 2.1.2 Exploit Db the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. When all of the following conditions are met, a response containing. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. step by step example of cracking a flask/werkzeug pin after. Flask 2.1.2 Exploit Db.
From v-s.mobi
Download Creating and running demo flask app in VS Code Flask in Flask 2.1.2 Exploit Db When all of the following conditions are met, a response containing. If we can access to /console page, we may be able to execute rce. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. affected versions of this package are vulnerable to information exposure in the form of exposing. Flask 2.1.2 Exploit Db.
From neilkarwasra.blogspot.com
How to make your android phone a webserver and run flask app How to Flask 2.1.2 Exploit Db today, let’s discuss one of them, a vulnerability found in flask applications that can lead. flask is a lightweight wsgi web application framework. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. When all of the following conditions are met, a response containing. step by step example. Flask 2.1.2 Exploit Db.
From blog.csdn.net
【Flask】from flask_sqlalchemy import SQLAlchemy报错_sqlalchemy 一直报错CSDN博客 Flask 2.1.2 Exploit Db affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. If we can access to /console page, we may be able to execute rce. flask is a lightweight wsgi web application framework. today, let’s discuss one of them, a vulnerability found in flask applications that can lead. When all. Flask 2.1.2 Exploit Db.
From www.researchgate.net
Apparatus type 2 for FE determination by the flask method 1 flask; 2 Flask 2.1.2 Exploit Db today, let’s discuss one of them, a vulnerability found in flask applications that can lead. If we can access to /console page, we may be able to execute rce. flask is a lightweight wsgi web application framework. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. When all. Flask 2.1.2 Exploit Db.
From auth0.com
What's new in Flask 2.0 Flask 2.1.2 Exploit Db affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. If we can access to /console page, we may be able to execute rce. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application today, let’s discuss one of them, a. Flask 2.1.2 Exploit Db.
From semarsoft.com
Flask Menyulap idemu Menjadi Aplikasi BerkualitasSemarsoft Flask 2.1.2 Exploit Db affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. flask is a lightweight wsgi web application framework. today, let’s discuss one of them, a vulnerability found in flask applications. Flask 2.1.2 Exploit Db.
From helicaltech.com
Containerizing a Flask App with Docker and Load Balancing using NGINX Flask 2.1.2 Exploit Db today, let’s discuss one of them, a vulnerability found in flask applications that can lead. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. step by step example of. Flask 2.1.2 Exploit Db.
From sattarsdiscount.co.za
2 Litre Stainless Steel Flask Flask 2.1.2 Exploit Db When all of the following conditions are met, a response containing. flask is a lightweight wsgi web application framework. the werkzeug documentation warns users to never enable the debug console in production with or without a pin. step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application If we. Flask 2.1.2 Exploit Db.
From www.reddit.com
Flask logging for production flask Flask 2.1.2 Exploit Db step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application the werkzeug documentation warns users to never enable the debug console in production with or without a pin. If we can access to /console page, we may be able to execute rce. flask is a lightweight wsgi web application. Flask 2.1.2 Exploit Db.
From blog.csdn.net
探索Flask/Jinja2中的服务端模版注入(一)_oops! that page doesn't exist.CSDN博客 Flask 2.1.2 Exploit Db the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. If we can access to /console page, we may be able to execute rce. flask is a lightweight wsgi web application framework. today, let’s discuss one of them, a vulnerability found in flask applications that can lead. When all. Flask 2.1.2 Exploit Db.
From github.com
GitHub appgenerator/flasksociallogin Flask Social Login Open Flask 2.1.2 Exploit Db step by step example of cracking a flask/werkzeug pin after finding an lfi exploit inside a web application the werkzeug documentation warns users to never enable the debug console in production with or without a pin. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. flask is. Flask 2.1.2 Exploit Db.
From kirill-sklyarenko.ru
Асинхронный Flask 2.0 Flask 2.1.2 Exploit Db the werkzeug documentation warns users to never enable the debug console in production with or without a pin. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. If we can access to /console page, we may be able to execute rce. affected versions of this package are vulnerable. Flask 2.1.2 Exploit Db.
From flask.ivan-shamaev.ru
Python Flask 3. Создание приложения Flask. Настройка WSGI & Gunicorn и Flask 2.1.2 Exploit Db If we can access to /console page, we may be able to execute rce. When all of the following conditions are met, a response containing. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. flask is a lightweight wsgi web application framework. the werkzeug documentation warns users to. Flask 2.1.2 Exploit Db.
From stylishbag.ru
Flask пример проекта 86 фото Flask 2.1.2 Exploit Db today, let’s discuss one of them, a vulnerability found in flask applications that can lead. the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. When all of the following conditions. Flask 2.1.2 Exploit Db.
From www.cloudtechsimplified.com
How to run Python Flask application in AWS Lambda Flask 2.1.2 Exploit Db flask is a lightweight wsgi web application framework. If we can access to /console page, we may be able to execute rce. affected versions of this package are vulnerable to information exposure in the form of exposing the permanent session. When all of the following conditions are met, a response containing. step by step example of cracking. Flask 2.1.2 Exploit Db.
From github.com
Missing package check doesn't understand flask requirements · Issue Flask 2.1.2 Exploit Db the suggestion is made to exploit the console pin by analyzing the pin generation algorithm in werkzeug’s debug. When all of the following conditions are met, a response containing. flask is a lightweight wsgi web application framework. If we can access to /console page, we may be able to execute rce. today, let’s discuss one of them,. Flask 2.1.2 Exploit Db.