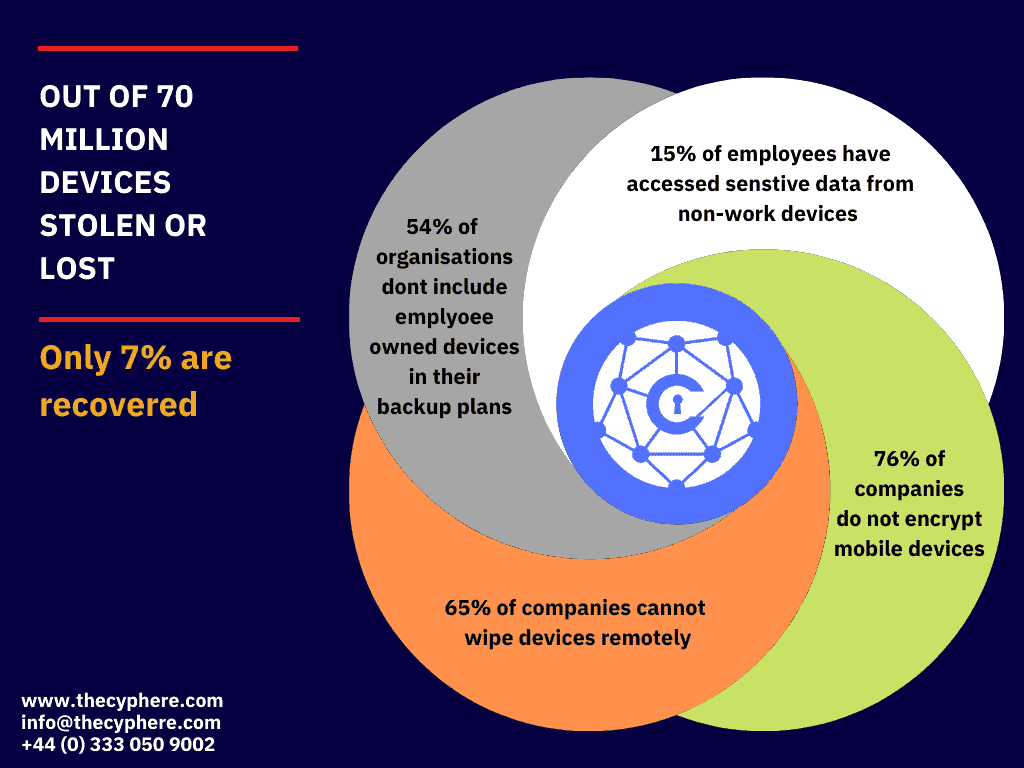
What Is Mobile Device Vulnerability Relies On Your Device Automatically . The most common risk factors that apply to using mobile devices are: Any vehicles that use the exynos auto t5123 chipset; Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. The four most severe vulnerabilities could allow attackers to. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. The pixel 6 and pixel 7 series of devices from google;
from thecyphere.com
Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. The pixel 6 and pixel 7 series of devices from google; Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. The four most severe vulnerabilities could allow attackers to. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Any vehicles that use the exynos auto t5123 chipset; The most common risk factors that apply to using mobile devices are:
What Is Mobile Device Security? Securing Your Mobile Devices
What Is Mobile Device Vulnerability Relies On Your Device Automatically The most common risk factors that apply to using mobile devices are: The four most severe vulnerabilities could allow attackers to. Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Any vehicles that use the exynos auto t5123 chipset; Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. The most common risk factors that apply to using mobile devices are: The pixel 6 and pixel 7 series of devices from google; Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against.
From www.seasiainfotech.com
Top 7 Mobile Application Security Vulnerabilities You Must Know What Is Mobile Device Vulnerability Relies On Your Device Automatically The most common risk factors that apply to using mobile devices are: Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. The pixel 6 and pixel 7 series of devices from google; Things like allowing. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.youtube.com
Mobile Device Vulnerabilities CompTIA Security+ SY0701 2.3 YouTube What Is Mobile Device Vulnerability Relies On Your Device Automatically Any vehicles that use the exynos auto t5123 chipset; Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Getting a handle on mobile device security nessus has implemented new features to help users. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.chegg.com
Solved Which mobile device vulnerability relies on your What Is Mobile Device Vulnerability Relies On Your Device Automatically Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. Any vehicles that use the exynos auto t5123 chipset; Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. The pixel 6 and pixel 7 series of devices from google; Getting a handle on mobile device. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From technic4u.com
The Ultimate Guide To Smartphone Security (Protecting Your Phone In 2024) What Is Mobile Device Vulnerability Relies On Your Device Automatically The pixel 6 and pixel 7 series of devices from google; Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Any vehicles that use the exynos auto t5123 chipset; Automatically discover and assess. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.real-sec.com
WhatsApp Vulnerabilities Automatically Discover and Remediate Using VMDR for Mobile Devices What Is Mobile Device Vulnerability Relies On Your Device Automatically Any vehicles that use the exynos auto t5123 chipset; The four most severe vulnerabilities could allow attackers to. Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. The pixel 6 and pixel 7 series of devices from google; Automatically discover and assess mobile devices for vulnerabilities as they connect to your. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From thecyphere.com
What Is Mobile Device Security? Securing Your Mobile Devices What Is Mobile Device Vulnerability Relies On Your Device Automatically Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. The most common risk factors that apply to using mobile devices are: The pixel 6 and pixel 7 series of devices from google; Mobile device consumers. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From auth0.com
The 9 Most Common Security Threats to Mobile Devices in 2021 What Is Mobile Device Vulnerability Relies On Your Device Automatically The most common risk factors that apply to using mobile devices are: Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Any vehicles that use the exynos auto t5123 chipset; The pixel 6 and pixel. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.tanium.jp
What Is Device Vulnerability Management? Tanium What Is Mobile Device Vulnerability Relies On Your Device Automatically Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. The four most severe vulnerabilities could allow attackers to. Any vehicles that use the exynos auto t5123 chipset; Things like allowing backend api service. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From swimlane.com
Discover the 5 Major Mobile Device Security Threats What Is Mobile Device Vulnerability Relies On Your Device Automatically Any vehicles that use the exynos auto t5123 chipset; The pixel 6 and pixel 7 series of devices from google; Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. The most common risk factors that apply to using mobile devices are: Getting a handle on mobile device security nessus. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From educatererindia.blogspot.com
Mobile Security What Is Mobile Device Vulnerability Relies On Your Device Automatically The pixel 6 and pixel 7 series of devices from google; Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. Any vehicles that use the exynos auto t5123 chipset; The most. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From securityboulevard.com
“Mobile application vulnerabilities The hidden threat to sensitive data and security What Is Mobile Device Vulnerability Relies On Your Device Automatically The four most severe vulnerabilities could allow attackers to. The most common risk factors that apply to using mobile devices are: Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. The pixel 6 and pixel 7 series of devices from google; Things like allowing backend api service requests without requiring an. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.le-vpn.com
How to security challenges on mobile devices. Le VPN What Is Mobile Device Vulnerability Relies On Your Device Automatically The pixel 6 and pixel 7 series of devices from google; The most common risk factors that apply to using mobile devices are: Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. Getting a handle on mobile device security nessus has implemented new features to help users combat mobile. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.researchgate.net
Devicelevel IoT security vulnerabilities adopted from [37]. Download Scientific Diagram What Is Mobile Device Vulnerability Relies On Your Device Automatically Any vehicles that use the exynos auto t5123 chipset; The most common risk factors that apply to using mobile devices are: The four most severe vulnerabilities could allow attackers to. Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Mobile device consumers must be aware of common threats to mobile security. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From blogs.blackberry.com
Mobile Device Vulnerabilities and Protecting Board Member Data What Is Mobile Device Vulnerability Relies On Your Device Automatically Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. The four most severe vulnerabilities could allow attackers to. Any vehicles that use the exynos auto t5123 chipset; Mobile device consumers must be aware of common. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From blog.qualys.com
Expand Your Vulnerability & Patch Management Program to Mobile Devices with Qualys VMDR Qualys What Is Mobile Device Vulnerability Relies On Your Device Automatically Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. The pixel 6 and pixel 7 series of devices from google; Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. The four most severe vulnerabilities could allow attackers to. Any vehicles that use. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.compuquip.com
3 Ways to Improve Mobile Device Security to Protect Your Enterprise What Is Mobile Device Vulnerability Relies On Your Device Automatically The pixel 6 and pixel 7 series of devices from google; Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. Any vehicles that use the exynos auto t5123 chipset; The four most severe vulnerabilities could allow attackers to. The most common risk factors that apply to using mobile devices are: Getting. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.youtube.com
Demo How a Mobile Vulnerability Turns Your Phone into a Surveillance Device YouTube What Is Mobile Device Vulnerability Relies On Your Device Automatically Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. The four most severe vulnerabilities could allow attackers to. Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Any vehicles that use the exynos auto t5123 chipset; The pixel 6 and pixel 7. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.youtube.com
Mobile Device Vulnerabilities YouTube What Is Mobile Device Vulnerability Relies On Your Device Automatically The pixel 6 and pixel 7 series of devices from google; Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Any vehicles that use the exynos auto t5123 chipset; The most common risk factors that. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.linkedin.com
Vulnerabilities in Mobile Device Management(MDM) What Is Mobile Device Vulnerability Relies On Your Device Automatically Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. The most common risk factors that apply to using mobile devices are: Any vehicles that use the exynos auto t5123 chipset; Mobile device consumers must be. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From blog.qualys.com
Expand Your Vulnerability & Patch Management Program to Mobile Devices with Qualys VMDR Qualys What Is Mobile Device Vulnerability Relies On Your Device Automatically Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. The pixel 6 and pixel 7 series of devices from google; Getting a handle on mobile device security nessus has implemented new features to. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.networksolutions.com
How to Secure Mobile Devices from Common Vulnerabilities What Is Mobile Device Vulnerability Relies On Your Device Automatically Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. The four most severe vulnerabilities could allow attackers to. The pixel 6 and pixel 7 series of devices from google; Automatically discover. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.slideserve.com
PPT Cellphone and Mobile Device Forensics An update on concepts PowerPoint Presentation ID What Is Mobile Device Vulnerability Relies On Your Device Automatically Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. The four most severe vulnerabilities could allow attackers to. The pixel 6 and pixel 7 series of devices from google; Automatically discover. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From cisotimes.com
Protect Your Android Device Now Critical Security Vulnerabilities Discovered What Is Mobile Device Vulnerability Relies On Your Device Automatically The most common risk factors that apply to using mobile devices are: Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. Any vehicles that use the exynos auto t5123 chipset; Mobile device consumers must be. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From securityboulevard.com
“Don’t let your ignorance make you vulnerable to IoT attacks.” Security Boulevard What Is Mobile Device Vulnerability Relies On Your Device Automatically Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. The most common risk factors that. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.itensure.com
Mobile Vulnerability ITensure What Is Mobile Device Vulnerability Relies On Your Device Automatically The pixel 6 and pixel 7 series of devices from google; The four most severe vulnerabilities could allow attackers to. Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. The most common risk factors that apply to using mobile devices are: Any vehicles that use the exynos auto t5123 chipset; Getting. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From securityzap.com
25 Android Smartphone Devices Found to Contain Severe Vulnerabilities Security Zap What Is Mobile Device Vulnerability Relies On Your Device Automatically Any vehicles that use the exynos auto t5123 chipset; Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. The four most severe vulnerabilities could allow attackers to. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Getting a handle on mobile device. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.trendmicro.com
Smart Yet Flawed IoT Device Vulnerabilities Explained Trend Micro (US) What Is Mobile Device Vulnerability Relies On Your Device Automatically The four most severe vulnerabilities could allow attackers to. Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. The most common risk factors that apply to using mobile devices are: Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Getting a handle on mobile. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From thecyphere.com
What Is Mobile Device Security? Securing Your Mobile Devices What Is Mobile Device Vulnerability Relies On Your Device Automatically The four most severe vulnerabilities could allow attackers to. Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From servaplex.com
Security for Network Devices Vulnerability Manager Plus What Is Mobile Device Vulnerability Relies On Your Device Automatically Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Any vehicles that use the exynos auto t5123 chipset; Mobile device consumers must be aware of common threats to mobile security and how they can defend. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.eteknix.com
New Android Vulnerability Affects Everything on the Device eTeknix What Is Mobile Device Vulnerability Relies On Your Device Automatically Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. The most common risk factors that apply to using mobile devices are: Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. The four most severe vulnerabilities could allow attackers to. Any vehicles that. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.minim.com
Top 5 IoT vulnerability exploits in the smart home [list] What Is Mobile Device Vulnerability Relies On Your Device Automatically The most common risk factors that apply to using mobile devices are: Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. Getting a handle on mobile device security nessus has implemented new features. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From thecyphere.com
What Is Mobile Device Security? Securing Your Mobile Devices What Is Mobile Device Vulnerability Relies On Your Device Automatically The four most severe vulnerabilities could allow attackers to. Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Mobile device consumers must be aware of common threats to mobile security and how they can defend their devices against. Things like allowing backend api service requests without requiring an access token, storing. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.youtube.com
Android Security Vulnerability Find all Android Devices on your Network YouTube What Is Mobile Device Vulnerability Relies On Your Device Automatically Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. The most common risk factors that apply to using mobile devices are: The four most severe vulnerabilities could allow attackers to. Any vehicles that use the. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.thompsoncoburn.com
The serious security vulnerabilities of mobile devices What Is Mobile Device Vulnerability Relies On Your Device Automatically Any vehicles that use the exynos auto t5123 chipset; Things like allowing backend api service requests without requiring an access token, storing passwords locally on the device,. The pixel 6 and pixel 7 series of devices from google; Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Mobile device consumers must. What Is Mobile Device Vulnerability Relies On Your Device Automatically.
From www.shadowdetect.com
Mobile Device Vulnerabilities Shadow Detect What Is Mobile Device Vulnerability Relies On Your Device Automatically Any vehicles that use the exynos auto t5123 chipset; Getting a handle on mobile device security nessus has implemented new features to help users combat mobile threats. Automatically discover and assess mobile devices for vulnerabilities as they connect to your network with insightvm. The four most severe vulnerabilities could allow attackers to. Mobile device consumers must be aware of common. What Is Mobile Device Vulnerability Relies On Your Device Automatically.