Flask Upload Vulnerability . The os module was imported into the script. One malicious file can compromise the whole server. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). However, with the right precautions in place, you can mitigate these risks and secure your flask application against such vulnerabilities. Flask is a lightweight wsgi web application framework. More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. Keeping this in mind, i knew flask file write to rce was a possibility, in certain circumstances. The full path of the application was disclosed on line 19. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. The best way to discover this vulnerability is by doing thorough recon. When all of the following conditions are met, a response containing data intended.
from github.com
However, with the right precautions in place, you can mitigate these risks and secure your flask application against such vulnerabilities. When all of the following conditions are met, a response containing data intended. Flask is a lightweight wsgi web application framework. The os module was imported into the script. The best way to discover this vulnerability is by doing thorough recon. The full path of the application was disclosed on line 19. Keeping this in mind, i knew flask file write to rce was a possibility, in certain circumstances. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. One malicious file can compromise the whole server. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses.
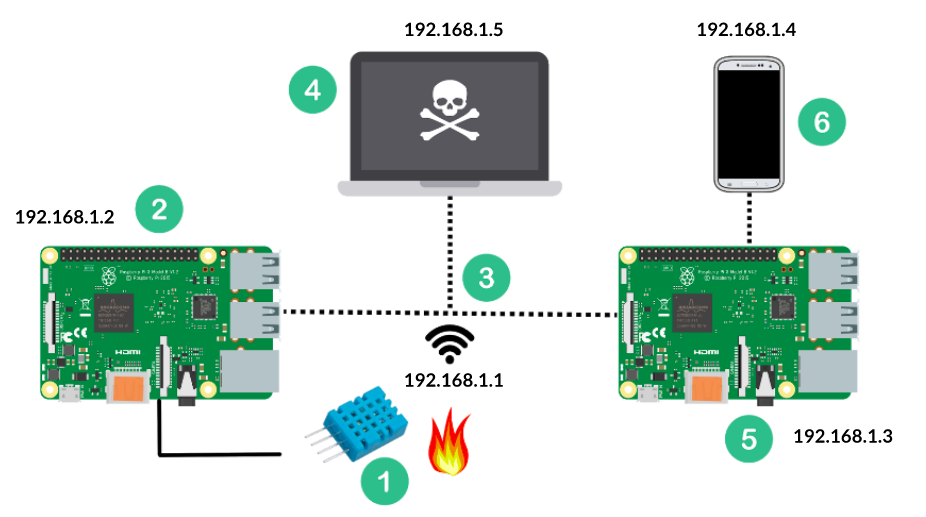
GitHub davikawasaki/iotsecurityvulnerability Raspberry PI Vulnerability Study using Flask
Flask Upload Vulnerability Flask is a lightweight wsgi web application framework. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. Keeping this in mind, i knew flask file write to rce was a possibility, in certain circumstances. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). The best way to discover this vulnerability is by doing thorough recon. When all of the following conditions are met, a response containing data intended. The full path of the application was disclosed on line 19. More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. The os module was imported into the script. One malicious file can compromise the whole server. However, with the right precautions in place, you can mitigate these risks and secure your flask application against such vulnerabilities. Flask is a lightweight wsgi web application framework. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal.
From appcheck-ng.com
File Upload Vulnerabilities AppCheck Flask Upload Vulnerability However, with the right precautions in place, you can mitigate these risks and secure your flask application against such vulnerabilities. More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). When all of the following conditions are met,. Flask Upload Vulnerability.
From github.com
GitHub arzuozkan/BasicLoginPage Login page development with Flask and pentesting for the Flask Upload Vulnerability More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. However, with the right precautions in place, you can mitigate these risks and secure your flask application against such vulnerabilities. Additionally, it can. Flask Upload Vulnerability.
From www.youtube.com
File Upload Vulnerability ContentType Manipulation YouTube Flask Upload Vulnerability There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. Flask is a lightweight wsgi web application framework. One malicious file can compromise the whole server. When all of the following conditions are met, a response containing data intended. Using. Flask Upload Vulnerability.
From tutorial101.blogspot.com
Uploading Files with Python FlaskUploads Tutorial101 Flask Upload Vulnerability Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). The best way to discover this vulnerability is by doing thorough recon. More severe the more the remote (logically and physically) an attacker can be in order to exploit. Flask Upload Vulnerability.
From github.com
Python Flask Path Traversal Vulnerability · Issue 669 · github/securitylab · GitHub Flask Upload Vulnerability There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). Flask is a lightweight wsgi web application framework. Keeping this in mind, i knew flask file write to rce was a possibility, in certain circumstances. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. Using shodan or by carefully. Flask Upload Vulnerability.
From simpleopec.weebly.com
Flask file upload example simpleopec Flask Upload Vulnerability There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). However, with the right precautions in place, you can mitigate these risks and secure your flask application against such vulnerabilities. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. Keeping this in mind, i knew flask file write to. Flask Upload Vulnerability.
From utopia-insights.dev
Uploading Files to Flask using FlaskUploads A Beginner's Guide Flask Upload Vulnerability Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. The os module was imported into the script. The best way to discover this vulnerability is by doing thorough recon. Keeping this in mind, i knew flask file write to rce was a possibility, in certain circumstances. However, with the right precautions in. Flask Upload Vulnerability.
From www.we45.com
How to Exploit File Upload Vulnerabilities (and How to Fix Them!) we45 Blogs Flask Upload Vulnerability The os module was imported into the script. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. The full path of the application was disclosed on line 19. Keeping this in mind, i knew flask file write to rce was a possibility, in certain circumstances. However, with the right precautions in place,. Flask Upload Vulnerability.
From www.twilio.com
Build a Site with Flask and Twilio Verify for Users to Upload a File Flask Upload Vulnerability Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. The best way to discover this vulnerability is by doing thorough recon. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. The full path of the application was disclosed on line 19. Flask is. Flask Upload Vulnerability.
From www.bogotobogo.com
Flask blog app tutorial 5 Uploading an image 2020 Flask Upload Vulnerability The best way to discover this vulnerability is by doing thorough recon. The os module was imported into the script. The full path of the application was disclosed on line 19. One malicious file can compromise the whole server. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. Flask is a. Flask Upload Vulnerability.
From www.youtube.com
Learn File Upload Vulnerability Basics In 5 Minutes! (for beginners) YouTube Flask Upload Vulnerability Keeping this in mind, i knew flask file write to rce was a possibility, in certain circumstances. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). More severe the more the remote (logically and physically) an attacker can be. Flask Upload Vulnerability.
From www.geeksforgeeks.org
Uploading and Downloading Files in Flask Flask Upload Vulnerability When all of the following conditions are met, a response containing data intended. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. The best way to discover this vulnerability is by doing thorough recon. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal.. Flask Upload Vulnerability.
From data-flair.training
File Uploading in Flask DataFlair Flask Upload Vulnerability The full path of the application was disclosed on line 19. The best way to discover this vulnerability is by doing thorough recon. However, with the right precautions in place, you can mitigate these risks and secure your flask application against such vulnerabilities. Flask is a lightweight wsgi web application framework. Additionally, it can result in cyber attacks on website. Flask Upload Vulnerability.
From github.com
GitHub Jieyab89/Jinja2pythonorflaskSSTIvulnerabilitypayload cheat sheet Jinja2 python Flask Upload Vulnerability The best way to discover this vulnerability is by doing thorough recon. Flask is a lightweight wsgi web application framework. When all of the following conditions are met, a response containing data intended. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). However, with the right precautions in place, you can mitigate these risks and secure. Flask Upload Vulnerability.
From medium.com
How to Exploit File Upload Vulnerability with Bypass Double Extension Security System by Ahmad Flask Upload Vulnerability Keeping this in mind, i knew flask file write to rce was a possibility, in certain circumstances. Flask is a lightweight wsgi web application framework. One malicious file can compromise the whole server. More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. The os module was imported into the script.. Flask Upload Vulnerability.
From www.stackhawk.com
Finding & Fixing SQL Injection Vulns in Flask (Python) Flask Upload Vulnerability More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). The os module was imported into the script. Flask is. Flask Upload Vulnerability.
From www.youtube.com
Uploading and Returning Files With a Database in Flask YouTube Flask Upload Vulnerability More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. One malicious file can compromise the whole server. Keeping this in mind, i knew flask file write to rce was a possibility, in certain. Flask Upload Vulnerability.
From fabianlee.org
Python Using Flask to upload files Fabian Lee Software Engineer Flask Upload Vulnerability One malicious file can compromise the whole server. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. The os module was imported into the script. More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. The best way to discover this vulnerability. Flask Upload Vulnerability.
From www.youtube.com
How to hack MySQL mysql injection vulnerability Python and Flask app is used in this example Flask Upload Vulnerability One malicious file can compromise the whole server. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. The best way to discover this vulnerability is by doing thorough recon. More severe the more the remote (logically and physically) an. Flask Upload Vulnerability.
From akash-venky091.medium.com
Interesting Test Cases of File uploading vulnerabilities by Akash Venky Medium Flask Upload Vulnerability The best way to discover this vulnerability is by doing thorough recon. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). However, with the right precautions in place, you can mitigate these risks and secure your flask application. Flask Upload Vulnerability.
From appsecure.security
Exploiting File Upload Vulnerabilities Prevention Strategies Appsecure Security Flask Upload Vulnerability Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. The best way to discover this vulnerability is by doing thorough recon. However, with the right precautions in place, you can mitigate these. Flask Upload Vulnerability.
From github.com
GitHub whippinmywrist/Flasktemplateinjection The simplest example of a template injection Flask Upload Vulnerability The os module was imported into the script. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. However, with the right precautions in place, you can mitigate these risks and secure your flask application against such vulnerabilities. The full. Flask Upload Vulnerability.
From github.com
GitHub keholmbeck/angularjsflaskuploadfileexample Flask Upload Vulnerability More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. When all of the following conditions are met, a response containing data intended. The os module was imported into the script. The full. Flask Upload Vulnerability.
From medium.com
Methods For Exploiting File Upload Vulnerabilities by Ömer Faruk PurpleBox Security Medium Flask Upload Vulnerability One malicious file can compromise the whole server. The best way to discover this vulnerability is by doing thorough recon. The full path of the application was disclosed on line 19. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. There was a clear zip slip (path traversal) vulnerability (lines 24 &. Flask Upload Vulnerability.
From www.bogotobogo.com
Flask blog app tutorial 5 Uploading an image 2020 Flask Upload Vulnerability The full path of the application was disclosed on line 19. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). One malicious file can compromise the whole server. When all of the following conditions are met, a response containing data intended. The os module was imported into the script. More severe the more the remote (logically. Flask Upload Vulnerability.
From www.wati.com
File Upload Vulnerability West Advanced Technologies, Inc. Flask Upload Vulnerability Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. The full path of the application was disclosed on line 19. Keeping this in mind, i knew flask file write to rce was a possibility,. Flask Upload Vulnerability.
From www.stackhawk.com
Finding & Fixing SQL Injection Vulns in Flask (Python) Flask Upload Vulnerability Keeping this in mind, i knew flask file write to rce was a possibility, in certain circumstances. The full path of the application was disclosed on line 19. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. Flask. Flask Upload Vulnerability.
From www.we45.com
How to Exploit File Upload Vulnerabilities (and How to Fix Them!) we45 Blogs Flask Upload Vulnerability However, with the right precautions in place, you can mitigate these risks and secure your flask application against such vulnerabilities. One malicious file can compromise the whole server. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. The full path of the application was disclosed on line 19. More severe the. Flask Upload Vulnerability.
From www.youtube.com
Python Flask Upload File and validate before save to Database using Flask SQLAlchemy YouTube Flask Upload Vulnerability When all of the following conditions are met, a response containing data intended. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of. Flask Upload Vulnerability.
From github.com
GitHub davikawasaki/iotsecurityvulnerability Raspberry PI Vulnerability Study using Flask Flask Upload Vulnerability There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. The os module was imported into the script. However, with the. Flask Upload Vulnerability.
From www.stackhawk.com
Finding & Fixing SQL Injection Vulns in Flask (Python) Flask Upload Vulnerability When all of the following conditions are met, a response containing data intended. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. There was a clear zip slip (path traversal) vulnerability (lines 24 &. Flask Upload Vulnerability.
From sec.ud64.com
Understanding File Upload Vulnerabilities in App Testing Security Alert Flask Upload Vulnerability The full path of the application was disclosed on line 19. The os module was imported into the script. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). The best way to discover this vulnerability is by doing thorough recon. However, with the right precautions in place, you can mitigate these risks and secure your flask. Flask Upload Vulnerability.
From tutorial101.blogspot.com
Python Flask Upload multiple images and display with Progress Bar Jquery Ajax Tutorial101 Flask Upload Vulnerability More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. When all of the following conditions are met, a response containing data intended. Flask is a lightweight wsgi web application framework. There was a clear zip slip (path traversal) vulnerability (lines 24 & 25). However, with the right precautions in place,. Flask Upload Vulnerability.
From tutorial101.blogspot.com
Python Flask Upload File and validate before save to Database using SQLAlchemy Tutorial101 Flask Upload Vulnerability However, with the right precautions in place, you can mitigate these risks and secure your flask application against such vulnerabilities. The best way to discover this vulnerability is by doing thorough recon. The os module was imported into the script. Using shodan or by carefully examining the server’s response headers, you can find out whether the application uses. One malicious. Flask Upload Vulnerability.
From www.youtube.com
DANGEROUS Python Flask Debug Mode Vulnerabilities YouTube Flask Upload Vulnerability The best way to discover this vulnerability is by doing thorough recon. Additionally, it can result in cyber attacks on website visitors, unauthorized server access, the hosting of illegal. More severe the more the remote (logically and physically) an attacker can be in order to exploit the vulnerability. Using shodan or by carefully examining the server’s response headers, you can. Flask Upload Vulnerability.