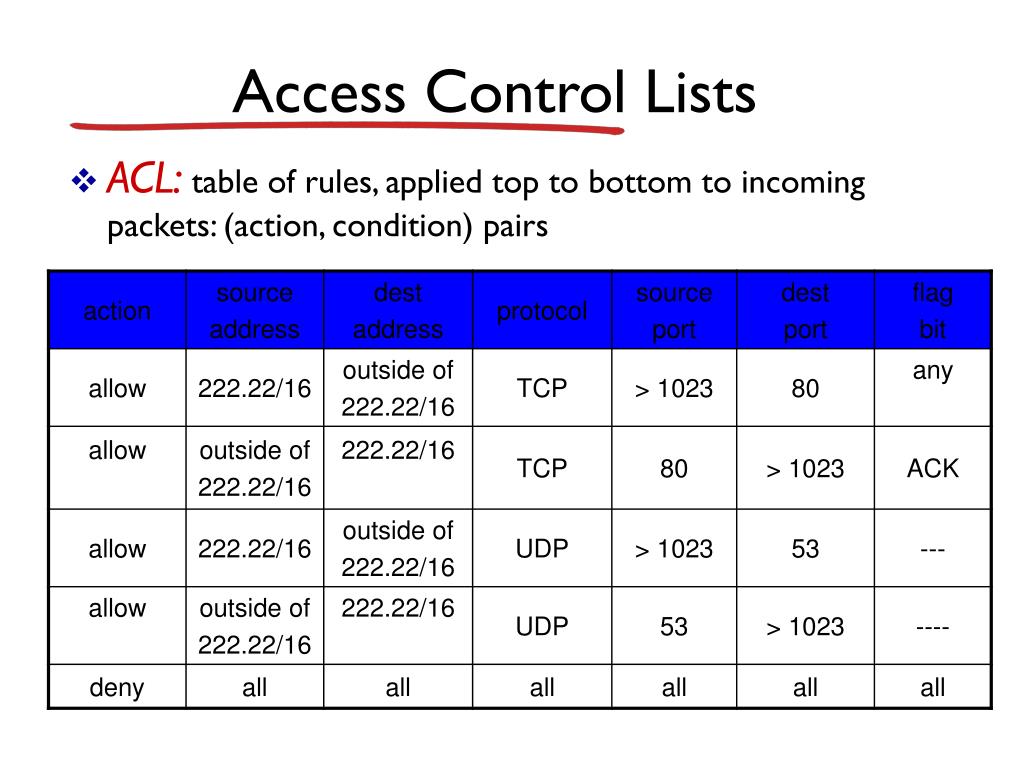
Network Access Control List Azure . Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. What is an ip based access control list (acl)? The criteria define the pattern to be matched such as an ip address. Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. Role assignments are the way you control access to azure back end and infrastructure resources. Azure service tags were introduced in 2018 to simplify network security management in. Access lists are a statement of criteria and actions. You can use the following network access controls to selectively allow access to a database via the public endpoint: For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups.
from www.slideserve.com
Access lists are a statement of criteria and actions. Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. Role assignments are the way you control access to azure back end and infrastructure resources. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. You can use the following network access controls to selectively allow access to a database via the public endpoint: Azure service tags were introduced in 2018 to simplify network security management in. What is an ip based access control list (acl)? Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. The criteria define the pattern to be matched such as an ip address.
PPT Computer Security Network + Link Layer Security + Network Management PowerPoint
Network Access Control List Azure Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. You can use the following network access controls to selectively allow access to a database via the public endpoint: Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. Access lists are a statement of criteria and actions. Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. Role assignments are the way you control access to azure back end and infrastructure resources. Azure service tags were introduced in 2018 to simplify network security management in. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. What is an ip based access control list (acl)? The criteria define the pattern to be matched such as an ip address.
From azure.jkr.co.il
כיצד מגדירים ACL Access Control List על Microsoft Azure endpoint Microsoft Azure Network Access Control List Azure You can use the following network access controls to selectively allow access to a database via the public endpoint: Azure service tags were introduced in 2018 to simplify network security management in. Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. Access lists are. Network Access Control List Azure.
From www.vcloudnotes.com
vCloudNotes Let's Learn Together Azure Resource Hierarchy and how to manage them effectively Network Access Control List Azure Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. Role assignments are the way you control access to azure back end and infrastructure resources. What. Network Access Control List Azure.
From www.vrogue.co
Azure Rbac Tutorial Manage Azure Role Based Access Co vrogue.co Network Access Control List Azure The criteria define the pattern to be matched such as an ip address. Access lists are a statement of criteria and actions. You can use the following network access controls to selectively allow access to a database via the public endpoint: Azure service tags were introduced in 2018 to simplify network security management in. What is an ip based access. Network Access Control List Azure.
From www.slideserve.com
PPT Computer Security Network + Link Layer Security + Network Management PowerPoint Network Access Control List Azure Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. You can use the following network access controls to selectively allow access to a database via the public endpoint: Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according. Network Access Control List Azure.
From learn.microsoft.com
アカウント コンソールの IP アクセス リスト Azure Databricks Microsoft Learn Network Access Control List Azure Role assignments are the way you control access to azure back end and infrastructure resources. You can use the following network access controls to selectively allow access to a database via the public endpoint: For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. The criteria define the pattern. Network Access Control List Azure.
From learn.microsoft.com
List Azure role assignments using the Azure portal Azure RBAC Microsoft Learn Network Access Control List Azure Access lists are a statement of criteria and actions. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. What is an ip based access control list (acl)? The criteria define the pattern to be matched such as an ip address. Azure service tags were introduced in 2018 to. Network Access Control List Azure.
From www.networkeducator.com
What Is Access Control List (ACL) & How It Works Network Educator Network Access Control List Azure Azure service tags were introduced in 2018 to simplify network security management in. What is an ip based access control list (acl)? Access lists are a statement of criteria and actions. You can use the following network access controls to selectively allow access to a database via the public endpoint: For example, in microsoft azure, we have what is called. Network Access Control List Azure.
From learnwithaniket.com
Security Groups vs Network Access Control Lists — Learn with Aniket Network Access Control List Azure Role assignments are the way you control access to azure back end and infrastructure resources. Azure service tags were introduced in 2018 to simplify network security management in. Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. For example, in microsoft azure, we have. Network Access Control List Azure.
From www.vrogue.co
What Is Azure Role Based Access Control Rbac Rijwan Satya S Blog www.vrogue.co Network Access Control List Azure Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. Role assignments are the way you control access to azure back end and infrastructure resources. What is an ip based access control list (acl)? Azure service tags were introduced in 2018 to simplify network security. Network Access Control List Azure.
From learn.microsoft.com
Secure your resources with Conditional Access policy templates Microsoft Entra Microsoft Learn Network Access Control List Azure Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. What is an ip based access control list (acl)? The criteria define the pattern. Network Access Control List Azure.
From viettuans.vn
Network Access Control là gì? Ứng dụng thực tiễn của Network Access Co Network Access Control List Azure What is an ip based access control list (acl)? Access lists are a statement of criteria and actions. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. You can. Network Access Control List Azure.
From www.youtube.com
Managing Azure RoleBased Access Control (RBAC) Azure Training YouTube Network Access Control List Azure Role assignments are the way you control access to azure back end and infrastructure resources. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. You can use the following network access controls to selectively allow access to a database via the public endpoint: Access lists are a statement. Network Access Control List Azure.
From www.thenetworkdna.com
Introduction to Azure Network Security Group (NSG) The Network DNA Network Access Control List Azure Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. Access lists are a statement of criteria and actions. You can use the following network access. Network Access Control List Azure.
From learn.microsoft.com
Manage network access control to an endpoint Microsoft Learn Network Access Control List Azure You can use the following network access controls to selectively allow access to a database via the public endpoint: Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. Role. Network Access Control List Azure.
From andrewmatveychuk.com
Design the access management process for Azure resources Network Access Control List Azure Role assignments are the way you control access to azure back end and infrastructure resources. Azure service tags were introduced in 2018 to simplify network security management in. You can use the following network access controls to selectively allow access to a database via the public endpoint: The criteria define the pattern to be matched such as an ip address.. Network Access Control List Azure.
From docs.microsoft.com
Azure Network Security Microsoft Docs Network Access Control List Azure Role assignments are the way you control access to azure back end and infrastructure resources. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. You can use the following network access controls to selectively allow access to a database via the public endpoint: The criteria define the pattern. Network Access Control List Azure.
From aviatrix.com
Azure Network Virtual Appliance (NVA) Aviatrix Network Access Control List Azure Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. Access lists are a statement of criteria and actions. The criteria define the pattern to be matched such as an. Network Access Control List Azure.
From www.softwaredesignpartners.com
Azure Application Gateway Network Access Control List Azure Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. Role assignments are the way you control access to azure back end and infrastructure resources. Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. You. Network Access Control List Azure.
From www.wallarm.com
What is ACL? Examples and Types of Access Control List Network Access Control List Azure Role assignments are the way you control access to azure back end and infrastructure resources. Azure service tags were introduced in 2018 to simplify network security management in. Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. For example, in microsoft azure, we have what is called network security groups. Network Access Control List Azure.
From www.youtube.com
Azure Role Based Access Control Azure RBAC Overview YouTube Network Access Control List Azure The criteria define the pattern to be matched such as an ip address. Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. Azure service tags were introduced in 2018 to simplify network security management in. You can use the following network access controls to. Network Access Control List Azure.
From www.databricks.com
How to protect Data Exfiltration with Azure Databricks to help ensure Cloud Security Network Access Control List Azure The criteria define the pattern to be matched such as an ip address. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. Role assignments are the way you control. Network Access Control List Azure.
From jaycemeowcunningham.blogspot.com
What Function Describe the Uses of an Access Control List Network Access Control List Azure The criteria define the pattern to be matched such as an ip address. Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. Access lists are. Network Access Control List Azure.
From subscription.packtpub.com
Azure RoleBased Access Control Architecting Microsoft Azure Solutions Exam Guide 70535 Network Access Control List Azure What is an ip based access control list (acl)? Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. Role assignments are the way you control access to azure back. Network Access Control List Azure.
From learn.microsoft.com
IP アクセス リスト Azure Databricks Microsoft Learn Network Access Control List Azure Role assignments are the way you control access to azure back end and infrastructure resources. The criteria define the pattern to be matched such as an ip address. Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. What is an ip based access control list (acl)? Azure service tags were. Network Access Control List Azure.
From www.conceptdraw.com
Azure Management Network Access Control List Azure Access lists are a statement of criteria and actions. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. Role assignments are the way you control access to azure back end and infrastructure resources. Gaining network access should be based on ip and device restrictions, firewall policies, network ports. Network Access Control List Azure.
From docs.microsoft.com
Manage app & resource access using groups Azure AD Microsoft Entra Microsoft Docs Network Access Control List Azure What is an ip based access control list (acl)? Azure service tags were introduced in 2018 to simplify network security management in. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. Role assignments are the way you control access to azure back end and infrastructure resources. The criteria. Network Access Control List Azure.
From msandbu.org
Customizing Role Based Access Control in Azure Marius Sandbu Network Access Control List Azure Access lists are a statement of criteria and actions. The criteria define the pattern to be matched such as an ip address. Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have. Network Access Control List Azure.
From www.thenetworkdna.com
Azure NSG Vs Azure Firewall The Network DNA Network Access Control List Azure What is an ip based access control list (acl)? Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. Access lists are a statement. Network Access Control List Azure.
From learn.microsoft.com
Azure portal を使用して Azure でのロールの割り当てを一覧表示する Azure RBAC Microsoft Learn Network Access Control List Azure Azure service tags were introduced in 2018 to simplify network security management in. Access lists are a statement of criteria and actions. Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. Role assignments are the way you control access to azure back end and infrastructure resources. For example, in microsoft. Network Access Control List Azure.
From www.vrogue.co
Azure Role Based Access Control Rbac Tutorials Dojo M vrogue.co Network Access Control List Azure What is an ip based access control list (acl)? The criteria define the pattern to be matched such as an ip address. Role assignments are the way you control access to azure back end and infrastructure resources. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. Azure service. Network Access Control List Azure.
From learn.microsoft.com
Manage virtual networks Azure Databricks Microsoft Learn Network Access Control List Azure The criteria define the pattern to be matched such as an ip address. Access control lists (acls) are a set of rules that regulate inbound and outbound packet flow within a network. For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. What is an ip based access control. Network Access Control List Azure.
From learn.microsoft.com
Azure roles, Microsoft Entra roles, and classic subscription administrator roles Microsoft Learn Network Access Control List Azure Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. You can use the following network access controls to selectively allow access to a database via the public endpoint: Azure service tags were introduced in 2018 to simplify network security management in. Role assignments are. Network Access Control List Azure.
From www.freecodecamp.org
What is An ACL? Access Control Lists Explained Network Access Control List Azure For example, in microsoft azure, we have what is called network security groups (nsg) and in aws, we have security groups. Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. The criteria define the pattern to be matched such as an ip address. Access. Network Access Control List Azure.
From secops.one
Azure virtual network service endpoints Amal Mammadov Network Access Control List Azure Role assignments are the way you control access to azure back end and infrastructure resources. What is an ip based access control list (acl)? The criteria define the pattern to be matched such as an ip address. Access lists are a statement of criteria and actions. Gaining network access should be based on ip and device restrictions, firewall policies, network. Network Access Control List Azure.
From www.vrogue.co
What Is Azure Role Based Access Control Rbac And How vrogue.co Network Access Control List Azure The criteria define the pattern to be matched such as an ip address. Gaining network access should be based on ip and device restrictions, firewall policies, network ports control, network security rules and more according to your business’s. Azure service tags were introduced in 2018 to simplify network security management in. For example, in microsoft azure, we have what is. Network Access Control List Azure.