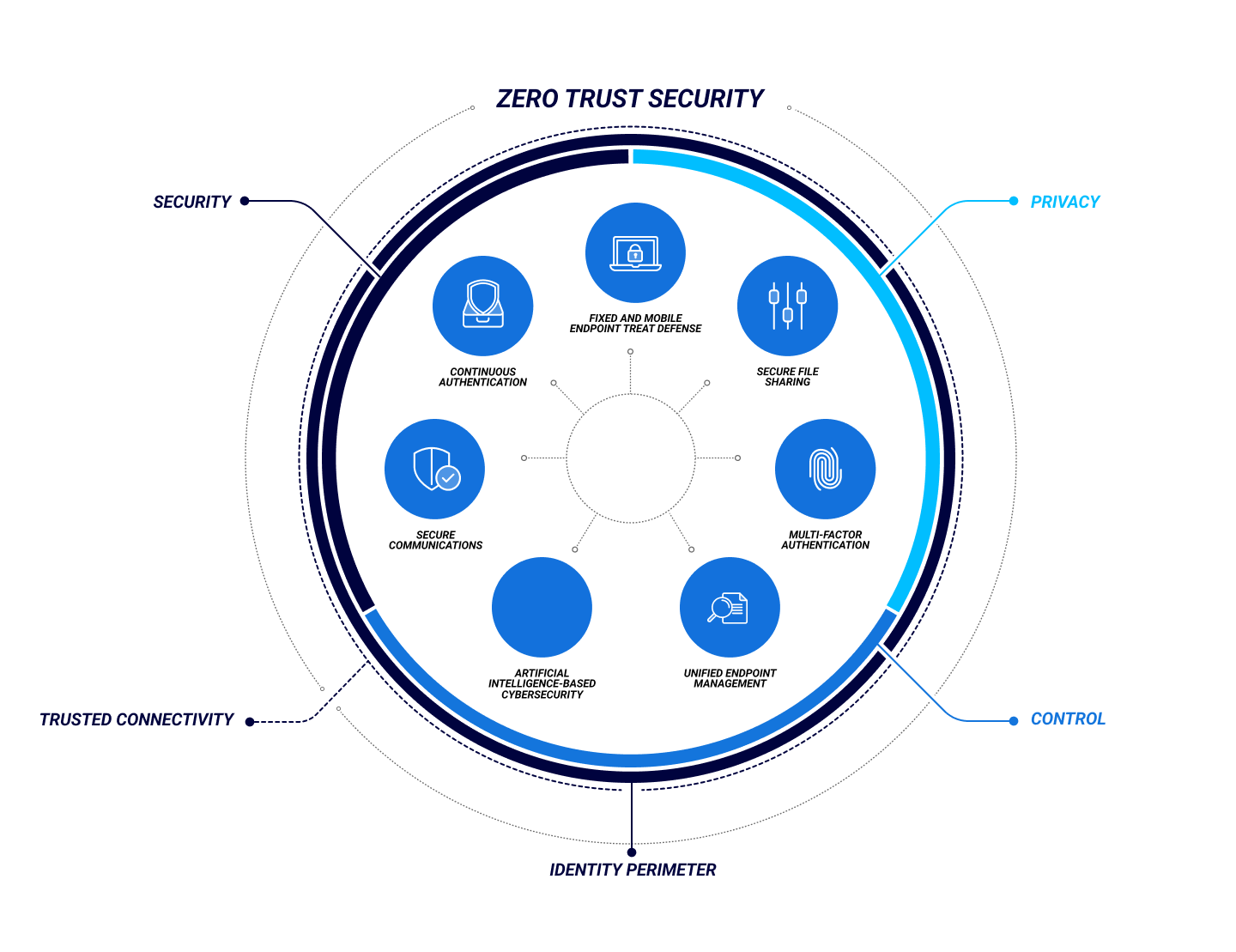
Endpoint Security Zero Trust . a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. Endpoint 向け microsoft defender は、エン. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. The conduits for users to access your data, network, and. Zero trust security policies are centrally enforced. zero trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and. zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. see how you can apply zero trust principles and policies to your endpoints and apps; there are a few key rules for securing devices and endpoints in a zero trust model:
from www.blackberry.com
there are a few key rules for securing devices and endpoints in a zero trust model: Endpoint 向け microsoft defender は、エン. see how you can apply zero trust principles and policies to your endpoints and apps; The conduits for users to access your data, network, and. Zero trust security policies are centrally enforced. zero trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and. a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security.
What Is Zero Trust Security?
Endpoint Security Zero Trust zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. see how you can apply zero trust principles and policies to your endpoints and apps; zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. Zero trust security policies are centrally enforced. Endpoint 向け microsoft defender は、エン. The conduits for users to access your data, network, and. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. there are a few key rules for securing devices and endpoints in a zero trust model: zero trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and.
From www.bankinfosecurity.com
2020 Endpoint and IoT Zero Trust Security Report Endpoint Security Zero Trust Zero trust security policies are centrally enforced. see how you can apply zero trust principles and policies to your endpoints and apps; The conduits for users to access your data, network, and. there are a few key rules for securing devices and endpoints in a zero trust model: this rigorous process is focused on clearly defining the. Endpoint Security Zero Trust.
From www.stealthlabs.com
Zero Trust Security All You Need To Know! Endpoint Security Zero Trust Zero trust security policies are centrally enforced. a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. The conduits for users to access your data, network, and. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust. Endpoint Security Zero Trust.
From www.femmehub.com
Introducing Identity & Endpoint Protection with Microsoft Zero Trust Endpoint Security Zero Trust zero trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and. see how you can apply zero trust principles and policies to your endpoints and apps; there are a few key rules for securing devices and endpoints in a zero trust model: a holistic approach to. Endpoint Security Zero Trust.
From edgile.com
Zero Trust Edgile Endpoint Security Zero Trust zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. Endpoint 向け microsoft defender は、エン. Zero trust security policies are centrally enforced. The conduits for users to access your data, network, and. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how. Endpoint Security Zero Trust.
From logrhythm.com
Embracing a Zero Trust Security Model LogRhythm Endpoint Security Zero Trust zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. there are a few key rules for securing devices and endpoints in a zero trust model: zero trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and. this rigorous process is. Endpoint Security Zero Trust.
From hiswai.com
Science & Tech Spotlight Zero Trust Architecture U.S. GAO Hiswai Endpoint Security Zero Trust a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. The conduits for users to access your data, network, and. zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. Endpoint 向け microsoft defender は、エン. see how you can apply zero trust principles and policies to. Endpoint Security Zero Trust.
From www.arpsolutions.nl
Een gelaagde beveiliging met Zero Trust Endpoint Protection Endpoint Security Zero Trust see how you can apply zero trust principles and policies to your endpoints and apps; Endpoint 向け microsoft defender は、エン. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. zero trust is a security framework requiring all users,. Endpoint Security Zero Trust.
From www.usclaro.com
Zero Trust Endpoint Security Solution Endpoint Security Zero Trust The conduits for users to access your data, network, and. there are a few key rules for securing devices and endpoints in a zero trust model: this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. zero trust principles. Endpoint Security Zero Trust.
From info.teledynamics.com
Zero trust security model a paradigm shift in network security Endpoint Security Zero Trust The conduits for users to access your data, network, and. zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. Zero trust security policies are centrally enforced. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and. Endpoint Security Zero Trust.
From www.microsoft.com
4 best practices to implement a comprehensive Zero Trust security Endpoint Security Zero Trust this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. see how you can apply zero trust principles and policies to your endpoints and apps; Zero trust security policies are centrally enforced. there are a few key rules for. Endpoint Security Zero Trust.
From www.samsungknox.com
The role of the endpoint in Zero Trust Endpoint Security Zero Trust this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. The conduits for users to access your data, network, and. zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. a holistic approach to. Endpoint Security Zero Trust.
From docs.microsoft.com
Microsoft 365 Zero Trust deployment plan Microsoft Docs Endpoint Security Zero Trust zero trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and. The conduits for users to access your data, network, and. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security). Endpoint Security Zero Trust.
From www.kuppingercole.com
Credentialingenabled Zero Trust Architecture for API EndpointSecurity Endpoint Security Zero Trust a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. there are a few key rules for securing devices and endpoints in a zero trust model: zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. this rigorous process is focused on clearly defining the. Endpoint Security Zero Trust.
From www.cloud-kinetics.com
Rise of Zero Trust Security Adoption, Benefits and Core Principles Endpoint Security Zero Trust this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. Endpoint 向け microsoft defender は、エン. zero trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and. there are a. Endpoint Security Zero Trust.
From www.f5.com
How to Implement a Zero Trust Security Model F5 Endpoint Security Zero Trust there are a few key rules for securing devices and endpoints in a zero trust model: zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. Zero trust security policies are centrally enforced. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t,. Endpoint Security Zero Trust.
From nordlayer.com
Extending Zero Trust to the endpoint NordLayer Learn Endpoint Security Zero Trust Zero trust security policies are centrally enforced. there are a few key rules for securing devices and endpoints in a zero trust model: a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. The conduits for users to access your data, network, and. Endpoint 向け microsoft defender は、エン. zero trust is. Endpoint Security Zero Trust.
From smallbizepp.com
Unlock Zero Trust Endpoint Security The Future of Protection? Endpoint Security Zero Trust see how you can apply zero trust principles and policies to your endpoints and apps; The conduits for users to access your data, network, and. a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. there are a few key rules for securing devices and endpoints in a zero trust model:. Endpoint Security Zero Trust.
From technology.gov.capital
How does Zero Trust architecture improve endpoint access control Endpoint Security Zero Trust zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. zero trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how. Endpoint Security Zero Trust.
From www.techcity.cloud
Zero Trust security model Techcity Company Limited Endpoint Security Zero Trust Zero trust security policies are centrally enforced. The conduits for users to access your data, network, and. there are a few key rules for securing devices and endpoints in a zero trust model: zero trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and. a holistic approach. Endpoint Security Zero Trust.
From resources.aithority.com
Endpoint security is an essential element of your Zero Trust journey Endpoint Security Zero Trust zero trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and. The conduits for users to access your data, network, and. Endpoint 向け microsoft defender は、エン. Zero trust security policies are centrally enforced. see how you can apply zero trust principles and policies to your endpoints and apps;. Endpoint Security Zero Trust.
From technology.gov.capital
Why should organizations prioritize endpoint security within a Zero Endpoint Security Zero Trust zero trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and. see how you can apply zero trust principles and policies to your endpoints and apps; Zero trust security policies are centrally enforced. zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical. Endpoint Security Zero Trust.
From www.orbit.de
EndpointSecurity Sicherheit für Endgeräte nach ZeroTrust ORBIT IT Endpoint Security Zero Trust see how you can apply zero trust principles and policies to your endpoints and apps; Endpoint 向け microsoft defender は、エン. Zero trust security policies are centrally enforced. a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. there are a few key rules for securing devices and endpoints in a zero. Endpoint Security Zero Trust.
From www.propelex.com
Endpoint Security Rooted in Zero Trust Propelex Endpoint Security Zero Trust see how you can apply zero trust principles and policies to your endpoints and apps; zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. Zero trust security policies are centrally enforced. a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. zero trust is. Endpoint Security Zero Trust.
From www.blackberry.com
What Is Zero Trust Security? Endpoint Security Zero Trust Endpoint 向け microsoft defender は、エン. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. there are a few key rules for securing devices and endpoints in a zero trust model: a holistic approach to zero trust should extend. Endpoint Security Zero Trust.
From smallbizepp.com
Unlock Zero Trust Endpoint Security The Future of Protection? Endpoint Security Zero Trust this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. zero trust is a security framework requiring all users, whether in or outside the organization’s network, to be authenticated, authorized, and. see how you can apply zero trust principles. Endpoint Security Zero Trust.
From nordlayer.com
Extending Zero Trust to the endpoint NordLayer Learn Endpoint Security Zero Trust Endpoint 向け microsoft defender は、エン. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. see how you can apply zero trust principles and policies to your endpoints and apps; The conduits for users to access your data, network, and.. Endpoint Security Zero Trust.
From www.ciowatercooler.co.uk
Mapping apps, data and users for zero trust endpoint security Endpoint Security Zero Trust see how you can apply zero trust principles and policies to your endpoints and apps; a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. The conduits for users to access your data, network, and. this rigorous process is focused on clearly defining the scope of zero trust, what it is,. Endpoint Security Zero Trust.
From www.microsoft.com
Using Zero Trust principles to protect against sophisticated attacks Endpoint Security Zero Trust see how you can apply zero trust principles and policies to your endpoints and apps; Zero trust security policies are centrally enforced. The conduits for users to access your data, network, and. zero trust principles include assuming compromise (assuming breach) to drive a holistic and practical security. Endpoint 向け microsoft defender は、エン. there are a few key. Endpoint Security Zero Trust.
From ardalyst.com
AllThreat™ (Zero Trust) Architecture Ardalyst Endpoint Security Zero Trust The conduits for users to access your data, network, and. see how you can apply zero trust principles and policies to your endpoints and apps; this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. zero trust is a. Endpoint Security Zero Trust.
From www.usclaro.com
Zero Trust Endpoint Security Solution Endpoint Security Zero Trust a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. The conduits for users to access your data, network, and. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. see how you. Endpoint Security Zero Trust.
From www.paloaltonetworks.ca
Build Endpoint Security into Your Zero Trust Strategy Palo Alto Endpoint Security Zero Trust this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. The conduits for users to access your data, network, and. see how you can apply zero trust principles and policies to your endpoints and apps; a holistic approach to. Endpoint Security Zero Trust.
From technology.gov.capital
How can Zero Trust Security Frameworks enhance endpoint security Endpoint Security Zero Trust Zero trust security policies are centrally enforced. a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. see how you can apply zero. Endpoint Security Zero Trust.
From smallbizepp.com
Unlock Zero Trust Endpoint Security The Future of Protection? Endpoint Security Zero Trust there are a few key rules for securing devices and endpoints in a zero trust model: a holistic approach to zero trust should extend to your entire digital estate—inclusive of identities, endpoints,. Zero trust security policies are centrally enforced. this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it. Endpoint Security Zero Trust.
From www.geeksforgeeks.org
Zero Security Model Endpoint Security Zero Trust there are a few key rules for securing devices and endpoints in a zero trust model: this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. zero trust principles include assuming compromise (assuming breach) to drive a holistic and. Endpoint Security Zero Trust.
From pubs.opengroup.org
Zero Trust Core Principles Endpoint Security Zero Trust this rigorous process is focused on clearly defining the scope of zero trust, what it is, what it isn’t, and how to link zero trust (and security) to. there are a few key rules for securing devices and endpoints in a zero trust model: The conduits for users to access your data, network, and. see how you. Endpoint Security Zero Trust.