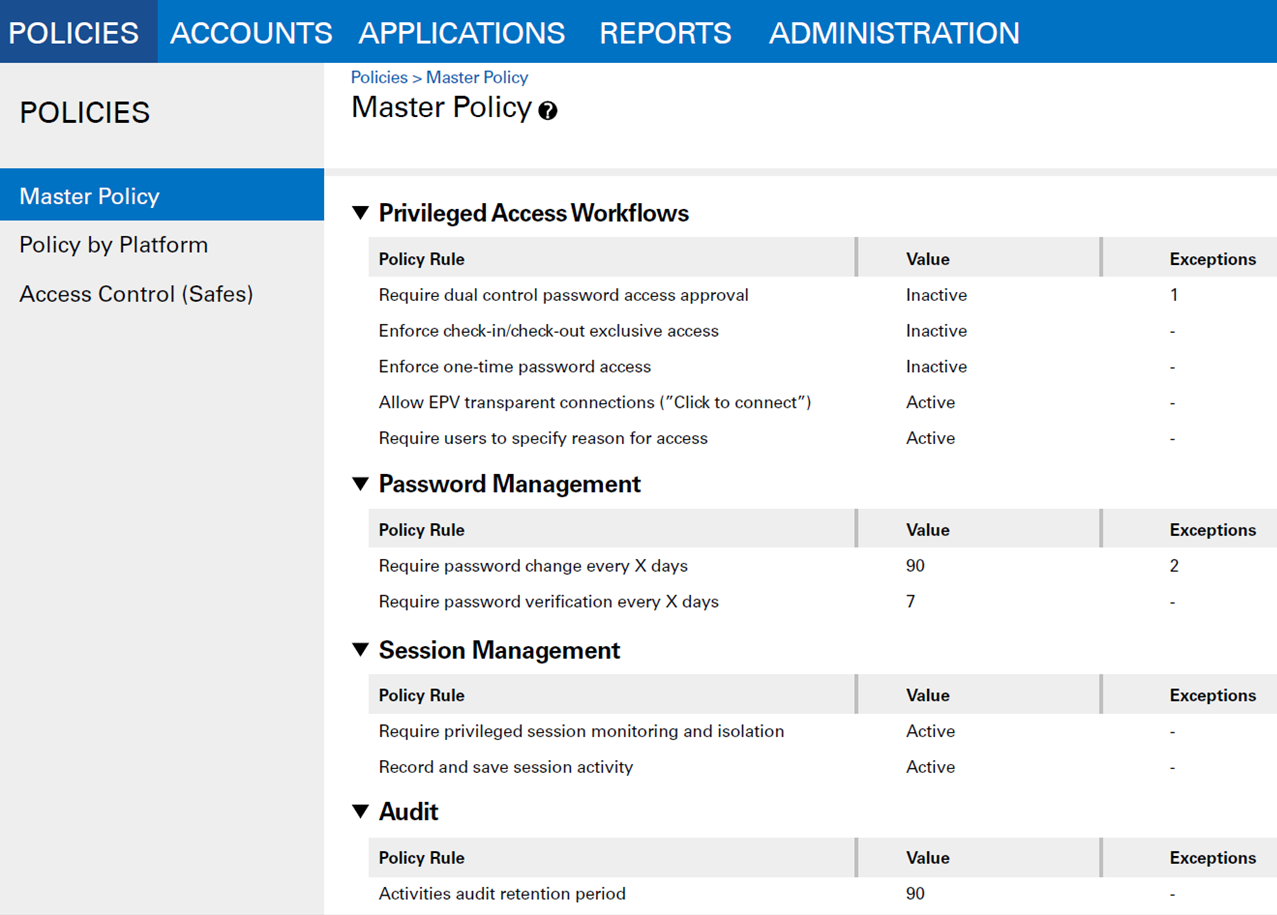
Cyberark Safe Management Best Practices . Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction. Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key, as well as the associated master password. There is no single correct or best way to design your access control methodology, but there are certainly best practice recommendations we. Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the rise*,. The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints. Safes enable you to store and organize accounts and secrets according to your organization's requirements. It is significantly easier to play around with the report or csv file output in excel or a text editor than it is to dive straight into siem (or getting your vault audit action codes.
from www.microfocus.com
However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key, as well as the associated master password. The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints. There is no single correct or best way to design your access control methodology, but there are certainly best practice recommendations we. Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the rise*,. It is significantly easier to play around with the report or csv file output in excel or a text editor than it is to dive straight into siem (or getting your vault audit action codes. Safes enable you to store and organize accounts and secrets according to your organization's requirements. Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction.
CyberArk Privileged Account Security Cybersecurity Marketplace
Cyberark Safe Management Best Practices Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key, as well as the associated master password. Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the rise*,. Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction. There is no single correct or best way to design your access control methodology, but there are certainly best practice recommendations we. Safes enable you to store and organize accounts and secrets according to your organization's requirements. Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. It is significantly easier to play around with the report or csv file output in excel or a text editor than it is to dive straight into siem (or getting your vault audit action codes. The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints.
From educate-u.com
Advanced CyberArk Training Educate U Cyberark Safe Management Best Practices However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key, as well as the associated master password. There is no single correct or best way to design your access control methodology, but there are certainly best practice recommendations we. Adopting best practices for securing cyberark pam environments with 97%. Cyberark Safe Management Best Practices.
From software.keyfactor.com
Preparing CyberArk to Work with Keyfactor Command Cyberark Safe Management Best Practices The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints. Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. However, at the very least organizations should develop a plan to both secure and retrieve the cyberark. Cyberark Safe Management Best Practices.
From www.youtube.com
Credential Hygiene Best Practices Cyberark YouTube Cyberark Safe Management Best Practices The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints. Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction. Safes enable you to store and organize accounts and secrets according to your organization's requirements. Users who have the relevant permissions can. Cyberark Safe Management Best Practices.
From www.youtube.com
How to Create a Safe CyberArk YouTube Cyberark Safe Management Best Practices Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the rise*,. However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key, as well as the associated master password. Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s. Cyberark Safe Management Best Practices.
From ic-consult.com
CyberArk Privilege Cloud QuickStart Guide PAM Offering Cyberark Safe Management Best Practices It is significantly easier to play around with the report or csv file output in excel or a text editor than it is to dive straight into siem (or getting your vault audit action codes. Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction. Adopting best practices for securing cyberark. Cyberark Safe Management Best Practices.
From securitybrief.co.nz
CyberArk emphasises identity safety on Identity Management Day Cyberark Safe Management Best Practices However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key, as well as the associated master password. Safes enable you to store and organize accounts and secrets according to your organization's requirements. There is no single correct or best way to design your access control methodology, but there are. Cyberark Safe Management Best Practices.
From cloudfoundation.com
What Is CyberArk? A Brief intro on various CyberArk Architectures Cyberark Safe Management Best Practices There is no single correct or best way to design your access control methodology, but there are certainly best practice recommendations we. The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints. Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials. Cyberark Safe Management Best Practices.
From www.lhtservices.com
[Checklist] 12 Top Tasks to Build a Business Cybersecurity Foundation Cyberark Safe Management Best Practices Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. Safes enable you to store and organize accounts and secrets according to your organization's requirements. Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the. Cyberark Safe Management Best Practices.
From www.strongdm.com
CyberArk vs. Delinea (Thycotic & Centrify) Which Is Better? StrongDM Cyberark Safe Management Best Practices The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints. Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the rise*,. It is significantly easier to play around with the report or csv file output in excel or a text. Cyberark Safe Management Best Practices.
From docs.cyberark.com
Vault Synchronizer with CyberArk Vault Cyberark Safe Management Best Practices Safes enable you to store and organize accounts and secrets according to your organization's requirements. There is no single correct or best way to design your access control methodology, but there are certainly best practice recommendations we. It is significantly easier to play around with the report or csv file output in excel or a text editor than it is. Cyberark Safe Management Best Practices.
From www.microfocus.com
CyberArk Privileged Account Security Cybersecurity Marketplace Cyberark Safe Management Best Practices It is significantly easier to play around with the report or csv file output in excel or a text editor than it is to dive straight into siem (or getting your vault audit action codes. However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key, as well as the. Cyberark Safe Management Best Practices.
From ic-consult.com
CyberArk Health Check & PAM Review QuickStart PAM Offering Cyberark Safe Management Best Practices Safes enable you to store and organize accounts and secrets according to your organization's requirements. However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key, as well as the associated master password. There is no single correct or best way to design your access control methodology, but there are. Cyberark Safe Management Best Practices.
From www.businesswire.com
CyberArk Named a Leader in 2022 Gartner Magic Quadrant for Access Cyberark Safe Management Best Practices Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction. Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the rise*,. There is no single correct or best way to design your access control methodology, but there are certainly best. Cyberark Safe Management Best Practices.
From www.pinterest.com
Learn CyberArk Advanced Privilege Management Online Training at Cyberark Safe Management Best Practices The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints. Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction. It is significantly easier to play around with the report or csv file output in excel or a text editor than it. Cyberark Safe Management Best Practices.
From asha24.net
CyberArk Tool Secure your business with this predominant security tool Cyberark Safe Management Best Practices Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the rise*,. The controls described in this section are the minimal requirements for protecting your epm. Cyberark Safe Management Best Practices.
From www.scmagazine.com
Best Identity Management Solution CyberArk Identity Security Platform Cyberark Safe Management Best Practices There is no single correct or best way to design your access control methodology, but there are certainly best practice recommendations we. However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key, as well as the associated master password. Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s. Cyberark Safe Management Best Practices.
From www.acte.in
CyberArk Tutorial For Beginners [ STEPIN ] Cyberark Safe Management Best Practices Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction. Safes enable you to store and organize accounts and secrets according to your organization's requirements. The controls. Cyberark Safe Management Best Practices.
From www.bankinfosecurity.com
CyberArk Privileged Access Management Solutions Cyberark Safe Management Best Practices Safes enable you to store and organize accounts and secrets according to your organization's requirements. Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the. Cyberark Safe Management Best Practices.
From www.youtube.com
Connect to Targets when Dual Control is Enforced CyberArk YouTube Cyberark Safe Management Best Practices Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. There is no single correct or best way to design your access control methodology, but there are certainly best practice recommendations we. However, at the very least organizations should develop a plan to both secure and. Cyberark Safe Management Best Practices.
From www.pwc.com.au
PwC and CyberArk PwC Cyberark Safe Management Best Practices Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction. Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the rise*,. The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints.. Cyberark Safe Management Best Practices.
From asha24.net
CyberArk Tutorial for Beginners Asha24 Blog Cyberark Safe Management Best Practices It is significantly easier to play around with the report or csv file output in excel or a text editor than it is to dive straight into siem (or getting your vault audit action codes. The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints. Users who have the relevant permissions. Cyberark Safe Management Best Practices.
From www.identityskills.com
Stay Ahead to master the CyberArk Tool with CyberArk Certification Cyberark Safe Management Best Practices Safes enable you to store and organize accounts and secrets according to your organization's requirements. Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the rise*,. It is significantly easier to play around with the report or csv file output in excel or a text editor than it is. Cyberark Safe Management Best Practices.
From docs.microfocus.com
How to Create and Configure CyberArk Account for the Integration Cyberark Safe Management Best Practices Safes enable you to store and organize accounts and secrets according to your organization's requirements. The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints. It is significantly easier to play around with the report or csv file output in excel or a text editor than it is to dive straight. Cyberark Safe Management Best Practices.
From cloudfoundation.com
What Is CyberArk? A Brief intro on various CyberArk Architectures Cyberark Safe Management Best Practices It is significantly easier to play around with the report or csv file output in excel or a text editor than it is to dive straight into siem (or getting your vault audit action codes. Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the rise*,. There is no. Cyberark Safe Management Best Practices.
From www.ndhanaraj.com
CyberArk PAM REST API What Is New on PAM V12 In Search of Identity Cyberark Safe Management Best Practices Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. There is no single correct or best way to design your access control methodology, but there are certainly best practice recommendations we. Safes enable you to store and organize accounts and secrets according to your organization's. Cyberark Safe Management Best Practices.
From appadvice.com
CyberArk SafeShare by CyberArk Cyberark Safe Management Best Practices The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints. Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction. However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key, as. Cyberark Safe Management Best Practices.
From www.wwt.com
Identity & Access Management with CyberArk WWT Cyberark Safe Management Best Practices Adopting best practices for securing cyberark pam environments with 97% of senior security executives seeing attempts to compromise credentials on the rise*,. Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. There is no single correct or best way to design your access control methodology,. Cyberark Safe Management Best Practices.
From www.mcsi.com.tw
CyberArk Access management Cyberark Safe Management Best Practices Safes enable you to store and organize accounts and secrets according to your organization's requirements. The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints. Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. However, at. Cyberark Safe Management Best Practices.
From apps.apple.com
CyberArk SafeShare on the App Store Cyberark Safe Management Best Practices Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction. There is no single correct or best way to design your access control methodology, but there are certainly best practice recommendations we. The controls described in this section are the minimal requirements for protecting your epm deployment, and therefore your endpoints.. Cyberark Safe Management Best Practices.
From cyberarkidentityskills.blogspot.com
CyberArk Training Your Gateway to Securing Critical Assets and Data Cyberark Safe Management Best Practices Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction. However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key, as well as the associated master password. Adopting best practices for securing cyberark pam environments with 97% of senior security. Cyberark Safe Management Best Practices.
From sennovate.com
The Ultimate Guide to CyberArk Access Management PAM Cyberark Safe Management Best Practices Safes enable you to store and organize accounts and secrets according to your organization's requirements. However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key, as well as the associated master password. It is significantly easier to play around with the report or csv file output in excel or. Cyberark Safe Management Best Practices.
From devolutions.net
Remote Desktop Manager & CyberArk Cyberark Safe Management Best Practices It is significantly easier to play around with the report or csv file output in excel or a text editor than it is to dive straight into siem (or getting your vault audit action codes. Safes enable you to store and organize accounts and secrets according to your organization's requirements. Users who have the relevant permissions can add safes in. Cyberark Safe Management Best Practices.
From support.pingidentity.com
CyberArk Core Privileged Access Security Solution SSO Cyberark Safe Management Best Practices Safes enable you to store and organize accounts and secrets according to your organization's requirements. Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as manage safe members and their. However, at the very least organizations should develop a plan to both secure and retrieve the cyberark master private encryption key,. Cyberark Safe Management Best Practices.
From cybersecurity-excellence-awards.com
CyberArk Cybersecurity Excellence Awards Cyberark Safe Management Best Practices Cyberark’s cio shares his perspective on ai trends, threats, cyberark’s approach to adoption and best practices for risk reduction. There is no single correct or best way to design your access control methodology, but there are certainly best practice recommendations we. Users who have the relevant permissions can add safes in the pvwa and modify their properties, as well as. Cyberark Safe Management Best Practices.
From www.youtube.com
CyberArk Workforce Password Management benefits YouTube Cyberark Safe Management Best Practices It is significantly easier to play around with the report or csv file output in excel or a text editor than it is to dive straight into siem (or getting your vault audit action codes. There is no single correct or best way to design your access control methodology, but there are certainly best practice recommendations we. Safes enable you. Cyberark Safe Management Best Practices.