Gdb Reverse Engineering Ctf . Reverse engineering and malware analysis are now becoming fields of growing research. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging workflow. Here’s a jump start for all of you. It can be used to trace program. Peda, pwndbg, and gef, try all 3 and use what you prefer. 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt 0x08048350. Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. In their own words, from the gnu.org website: Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the.
from ahmedheltaher.github.io
Reverse engineering and malware analysis are now becoming fields of growing research. 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt 0x08048350. Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. Peda, pwndbg, and gef, try all 3 and use what you prefer. Here’s a jump start for all of you. In their own words, from the gnu.org website: Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging workflow. It can be used to trace program.
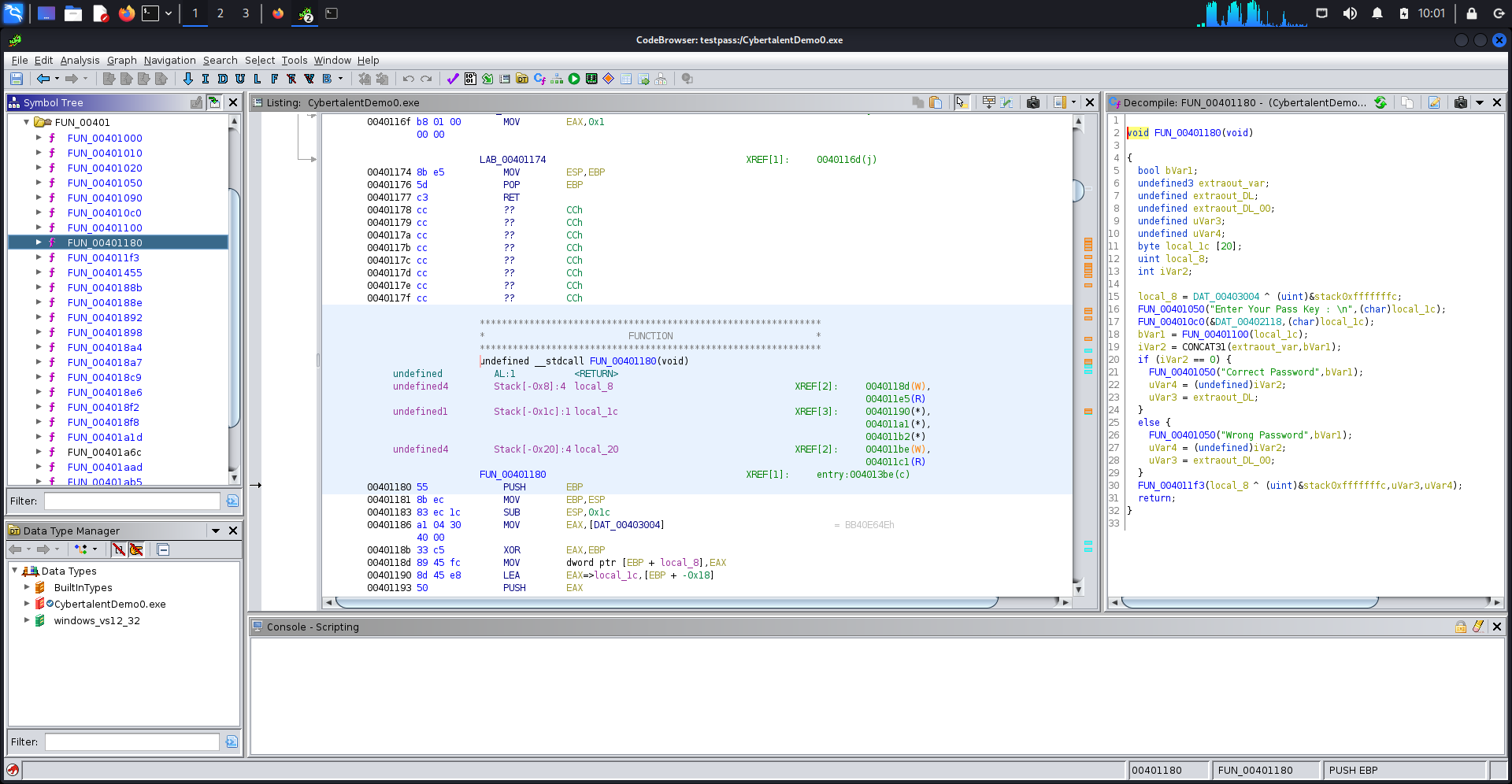
Lesson 23 Introduction to Reverse Engineering ctfwriteups
Gdb Reverse Engineering Ctf Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. It can be used to trace program. Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. In their own words, from the gnu.org website: 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt 0x08048350. Peda, pwndbg, and gef, try all 3 and use what you prefer. Reverse engineering and malware analysis are now becoming fields of growing research. Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. Here’s a jump start for all of you. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging workflow.
From www.youtube.com
Basic Reverse Engineering using GDB YouTube Gdb Reverse Engineering Ctf In their own words, from the gnu.org website: Peda, pwndbg, and gef, try all 3 and use what you prefer. Reverse engineering and malware analysis are now becoming fields of growing research. 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt 0x08048350. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands. Gdb Reverse Engineering Ctf.
From www.youtube.com
Candy Bowl Hack The Boo CTF Reverse Engineering GDB Ghidra Gdb Reverse Engineering Ctf In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging workflow. Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. Peda, pwndbg, and gef, try all 3 and use what you prefer.. Gdb Reverse Engineering Ctf.
From flippingbitz.com
Playsecure CTF 2021 Reverse Engineering 0x03 UB3RSEC Gdb Reverse Engineering Ctf Reverse engineering and malware analysis are now becoming fields of growing research. In their own words, from the gnu.org website: Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. Gdb is a tool developed for linux systems with the goal of helping developers. Gdb Reverse Engineering Ctf.
From www.youtube.com
Reverse Engineering w/GDB and Ghidra! picoCTF 2022 08 "Keygenme Gdb Reverse Engineering Ctf Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. Reverse engineering and malware analysis are now becoming fields of growing research. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging workflow.. Gdb Reverse Engineering Ctf.
From www.youtube.com
[English] Pico Ctf Challenge solved GDB Test Drive Reverse Gdb Reverse Engineering Ctf 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt 0x08048350. Peda, pwndbg, and gef, try all 3 and use what you prefer. It can be used to trace program. Reverse engineering and malware analysis are now becoming fields of growing research. Here’s a jump start for all of you. In this video, i’m gonna walk you through gdb setup for reverse engineering and. Gdb Reverse Engineering Ctf.
From formlabs.com
Guide to Reverse Engineering All You Need To Know Formlabs Gdb Reverse Engineering Ctf In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging workflow. Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. Navigate to the picoctf website, locate the challenge named “gdb baby step. Gdb Reverse Engineering Ctf.
From medium.com
Reverse Engineering Crackmes With GDB (Alx ./crackme3 …) by Gdb Reverse Engineering Ctf It can be used to trace program. Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt 0x08048350. Here’s a jump start for all of you. In this video, i’m gonna walk you through gdb setup for reverse. Gdb Reverse Engineering Ctf.
From github.com
GitHub CyberShieldDev/reverseengineeringchallengesctf reverse Gdb Reverse Engineering Ctf Reverse engineering and malware analysis are now becoming fields of growing research. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging workflow. Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with. Gdb Reverse Engineering Ctf.
From www.youtube.com
How to install GEF (GDB Extenstion) Advanced Exploit Development and Gdb Reverse Engineering Ctf Peda, pwndbg, and gef, try all 3 and use what you prefer. Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. Here’s. Gdb Reverse Engineering Ctf.
From www.youtube.com
Reverse Engineering GDB and Dynamic Analysis UCLA ACM Cyber YouTube Gdb Reverse Engineering Ctf Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. It can be used to trace program. Here’s a jump start for all. Gdb Reverse Engineering Ctf.
From github.com
GitHub CyberShieldDev/reverseengineeringchallengesctf reverse Gdb Reverse Engineering Ctf It can be used to trace program. Peda, pwndbg, and gef, try all 3 and use what you prefer. In their own words, from the gnu.org website: Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. Navigate to the picoctf website, locate the challenge named “gdb baby step. Gdb Reverse Engineering Ctf.
From slideplayer.com
Reverse Engineering for CTFs ppt download Gdb Reverse Engineering Ctf Here’s a jump start for all of you. Peda, pwndbg, and gef, try all 3 and use what you prefer. In their own words, from the gnu.org website: Reverse engineering and malware analysis are now becoming fields of growing research. It can be used to trace program. Gdb is a tool developed for linux systems with the goal of helping. Gdb Reverse Engineering Ctf.
From igio90.github.io
frick frick aka the first debugger built on top of frida is a Gdb Reverse Engineering Ctf It can be used to trace program. Here’s a jump start for all of you. Reverse engineering and malware analysis are now becoming fields of growing research. Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. Gdb is a tool developed for linux. Gdb Reverse Engineering Ctf.
From medium.com
Reverseengineering Using Linux GDB by Rick Harris Medium Gdb Reverse Engineering Ctf In their own words, from the gnu.org website: Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. Here’s a jump start for all of you. Reverse engineering and malware analysis are now becoming fields of growing research. Peda, pwndbg, and gef, try all. Gdb Reverse Engineering Ctf.
From csea-iitb.github.io
Reverse Engineering using Cutter CTFwiki Gdb Reverse Engineering Ctf Here’s a jump start for all of you. It can be used to trace program. Peda, pwndbg, and gef, try all 3 and use what you prefer. 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt 0x08048350. Reverse engineering and malware analysis are now becoming fields of growing research. Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in. Gdb Reverse Engineering Ctf.
From www.youtube.com
Reverse Engineering with Ollydbg CTF Walkthrough YouTube Gdb Reverse Engineering Ctf It can be used to trace program. Here’s a jump start for all of you. Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for. Gdb Reverse Engineering Ctf.
From www.youtube.com
CTF Reverse Engineering Challenges Its working and tools to be used Gdb Reverse Engineering Ctf Here’s a jump start for all of you. Reverse engineering and malware analysis are now becoming fields of growing research. It can be used to trace program. Peda, pwndbg, and gef, try all 3 and use what you prefer. Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs.. Gdb Reverse Engineering Ctf.
From lockpin010.medium.com
ReverseEngineering Reloaded CTF by Ahmet Göker Medium Gdb Reverse Engineering Ctf Peda, pwndbg, and gef, try all 3 and use what you prefer. Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt 0x08048350. Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself. Gdb Reverse Engineering Ctf.
From wiki.compass.college
Reverse Engineering COMPASS CTF Wiki Gdb Reverse Engineering Ctf Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. Peda, pwndbg, and gef, try all 3 and use what you prefer. 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt 0x08048350. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary. Gdb Reverse Engineering Ctf.
From blog.tetrane.com
Tetrane Automated Reverse Engineering Platform Gdb Reverse Engineering Ctf Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. Peda, pwndbg, and gef, try all 3 and use what you prefer. In their own words, from the gnu.org website: It can be used to trace program. Gdb is a tool developed for linux. Gdb Reverse Engineering Ctf.
From www.youtube.com
Introduction to reverse engineering CTF challenges YouTube Gdb Reverse Engineering Ctf In their own words, from the gnu.org website: Reverse engineering and malware analysis are now becoming fields of growing research. Here’s a jump start for all of you. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging workflow. Navigate to the picoctf website,. Gdb Reverse Engineering Ctf.
From payatu.com
Learning to Reverse Engineer with GDB Payatu Gdb Reverse Engineering Ctf Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. In their own words, from the gnu.org website: Peda, pwndbg, and gef, try all 3 and use what you prefer. Reverse engineering and malware analysis are now becoming fields of growing research. Navigate to the picoctf website, locate the. Gdb Reverse Engineering Ctf.
From www.youtube.com
Install Ghidra, USE GDB TO SOLVE FIRST CRACKME, Software Gdb Reverse Engineering Ctf Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. It can be used to trace program. Here’s a jump start for all of you. Peda, pwndbg, and gef, try all 3 and use what you prefer. In this video, i’m gonna walk you. Gdb Reverse Engineering Ctf.
From github.com
GitHub minminlittleshrimp/CTF_Reverse_Engineering CTF Reverse Gdb Reverse Engineering Ctf Peda, pwndbg, and gef, try all 3 and use what you prefer. In their own words, from the gnu.org website: Here’s a jump start for all of you. 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt 0x08048350. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your. Gdb Reverse Engineering Ctf.
From ahmedheltaher.github.io
Lesson 23 Introduction to Reverse Engineering ctfwriteups Gdb Reverse Engineering Ctf In their own words, from the gnu.org website: It can be used to trace program. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging workflow. Peda, pwndbg, and gef, try all 3 and use what you prefer. 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt. Gdb Reverse Engineering Ctf.
From www.linkedin.com
GDB Tutorial for Reverse Engineers Breakpoints, Modifying Memory and Gdb Reverse Engineering Ctf It can be used to trace program. Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. Here’s a jump start for all of you. Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in. Gdb Reverse Engineering Ctf.
From wiki.compass.college
Reverse Engineering COMPASS CTF Wiki Gdb Reverse Engineering Ctf Reverse engineering and malware analysis are now becoming fields of growing research. It can be used to trace program. Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself. Gdb Reverse Engineering Ctf.
From www.youtube.com
reverse engineering with gdb crackme0x04 YouTube Gdb Reverse Engineering Ctf It can be used to trace program. Peda, pwndbg, and gef, try all 3 and use what you prefer. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging workflow. Gdb is a tool developed for linux systems with the goal of helping developers. Gdb Reverse Engineering Ctf.
From csea-iitb.github.io
Introduction To Reverse Engineering CTFwiki Gdb Reverse Engineering Ctf Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. It can be used to trace program. Peda, pwndbg, and gef, try all 3 and use what you prefer. 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt 0x08048350. In this video, i’m gonna walk you through gdb setup for reverse engineering. Gdb Reverse Engineering Ctf.
From www.youtube.com
Reverse Engineering GDB (AntiDebugging)/Patching? YouTube Gdb Reverse Engineering Ctf Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. Here’s a jump start for all of you. Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. In their own words, from. Gdb Reverse Engineering Ctf.
From www.reddit.com
MultiArchitecture GDB Enhanced Features for Exploiters & Reverse Gdb Reverse Engineering Ctf Reverse engineering and malware analysis are now becoming fields of growing research. In their own words, from the gnu.org website: Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt 0x08048350. It can be used to trace program.. Gdb Reverse Engineering Ctf.
From www.youtube.com
Picoctf GDB TEST DRIVEReverseengineering 2022 YouTube Gdb Reverse Engineering Ctf Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. Here’s a jump start for all of you. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging. Gdb Reverse Engineering Ctf.
From csea-iitb.github.io
Introduction To Reverse Engineering CTFwiki Gdb Reverse Engineering Ctf Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. Navigate to the picoctf website, locate the challenge named “gdb baby step 1,” in the “reverse engineering section”, familiarize yourself with the task by reading the. In this video, i’m gonna walk you through gdb setup for reverse engineering. Gdb Reverse Engineering Ctf.
From www.youtube.com
easy reverse engineering ctf walkthrough. YouTube Gdb Reverse Engineering Ctf Gdb is a tool developed for linux systems with the goal of helping developers identify sources of bugs in their programs. Here’s a jump start for all of you. Peda, pwndbg, and gef, try all 3 and use what you prefer. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the. Gdb Reverse Engineering Ctf.
From docs.google.com
GDB Reverse Engineering Cheat Sheet Google Docs Gdb Reverse Engineering Ctf Here’s a jump start for all of you. Reverse engineering and malware analysis are now becoming fields of growing research. It can be used to trace program. In this video, i’m gonna walk you through gdb setup for reverse engineering and show you all of the necessary commands and shortcuts for your debugging workflow. 0x080482f4 _init 0x08048330 malloc@plt 0x08048340 puts@plt. Gdb Reverse Engineering Ctf.