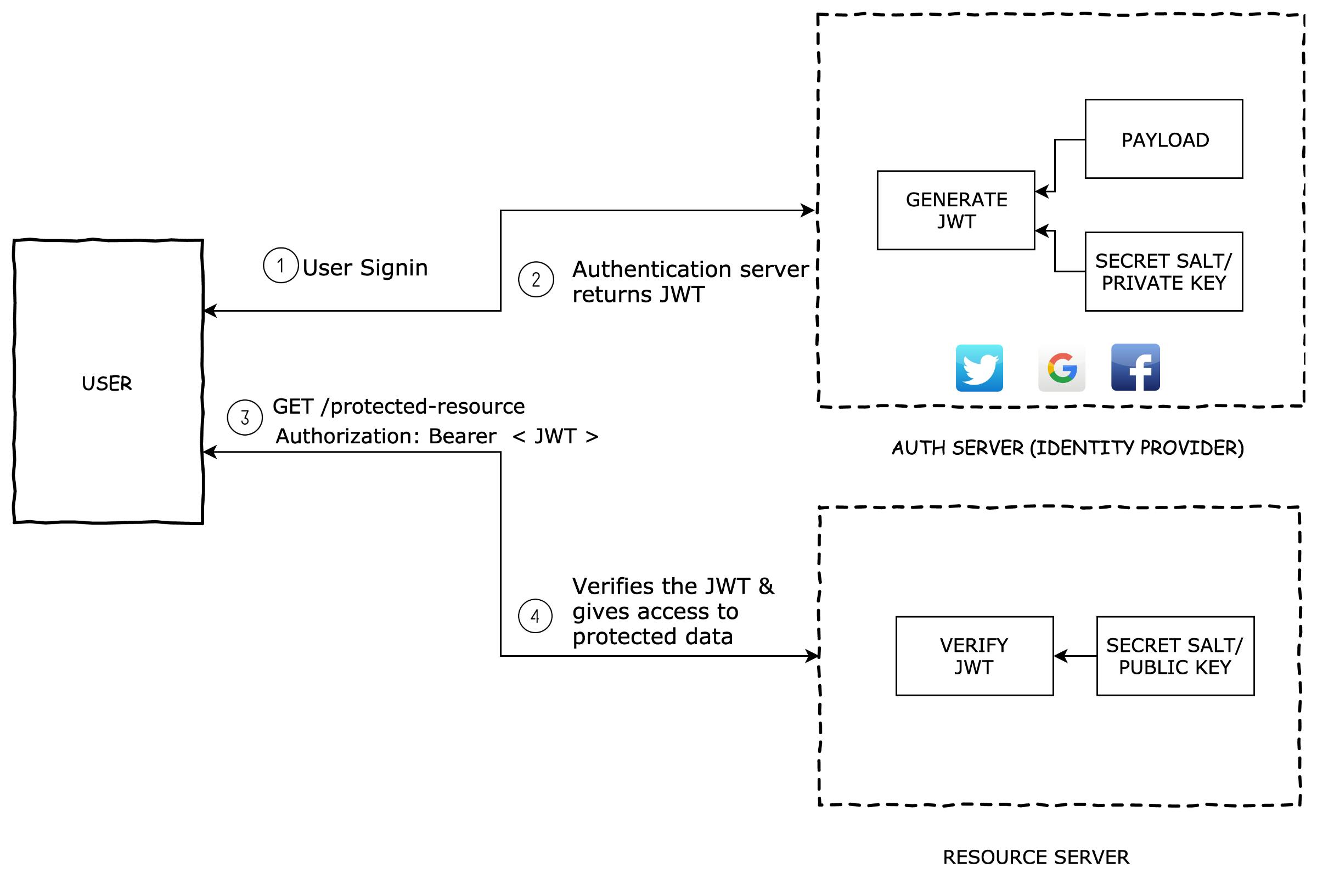
How To Prevent Jwt Attacks . organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing additional security measures such as token expiration and access control. this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. An attacker can now impersonate a client and. Once a jwt has been stolen, you’ll be in a bad situation: the most common methods of storing the jwt are through html5 web storage or cookies. what to do if your jwt is stolen. which libraries are vulnerable to attacks and how to prevent them. Protection of the crypto keys (server side). There are two ways of storing the.
from kathan19.gitbook.io
An attacker can now impersonate a client and. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing additional security measures such as token expiration and access control. the most common methods of storing the jwt are through html5 web storage or cookies. what to do if your jwt is stolen. There are two ways of storing the. this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. Once a jwt has been stolen, you’ll be in a bad situation: Protection of the crypto keys (server side). which libraries are vulnerable to attacks and how to prevent them.
JWT HowToHunt
How To Prevent Jwt Attacks which libraries are vulnerable to attacks and how to prevent them. the most common methods of storing the jwt are through html5 web storage or cookies. Once a jwt has been stolen, you’ll be in a bad situation: Protection of the crypto keys (server side). There are two ways of storing the. this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. what to do if your jwt is stolen. which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing additional security measures such as token expiration and access control. An attacker can now impersonate a client and.
From hackernoon.com
Avoid XSS and CSRF Attacks in JWT (React + Golang) A Tutorial HackerNoon How To Prevent Jwt Attacks An attacker can now impersonate a client and. the most common methods of storing the jwt are through html5 web storage or cookies. which libraries are vulnerable to attacks and how to prevent them. Protection of the crypto keys (server side). this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with. How To Prevent Jwt Attacks.
From ably.com
Socket security How to prevent 9 common vulnerabilities How To Prevent Jwt Attacks Once a jwt has been stolen, you’ll be in a bad situation: There are two ways of storing the. Protection of the crypto keys (server side). the most common methods of storing the jwt are through html5 web storage or cookies. An attacker can now impersonate a client and. which libraries are vulnerable to attacks and how to. How To Prevent Jwt Attacks.
From apisecurity.io
Issue 56 Common JWT Attacks, OWASP API Security Top 10 cheat sheet How To Prevent Jwt Attacks which libraries are vulnerable to attacks and how to prevent them. An attacker can now impersonate a client and. what to do if your jwt is stolen. the most common methods of storing the jwt are through html5 web storage or cookies. There are two ways of storing the. this cheatsheet provides tips to prevent common. How To Prevent Jwt Attacks.
From www.invicti.com
JSON Token attacks and vulnerabilities Invicti How To Prevent Jwt Attacks the most common methods of storing the jwt are through html5 web storage or cookies. An attacker can now impersonate a client and. which libraries are vulnerable to attacks and how to prevent them. what to do if your jwt is stolen. There are two ways of storing the. Protection of the crypto keys (server side). . How To Prevent Jwt Attacks.
From www.coreprogramm.com
Introduction to JWT Token CoreProgram How To Prevent Jwt Attacks which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing additional security measures such as token expiration and access control. this cheatsheet provides tips to prevent common security issues when using json. How To Prevent Jwt Attacks.
From redfoxsec.com
JWT Authentication Bypass Redfox Security How To Prevent Jwt Attacks Protection of the crypto keys (server side). the most common methods of storing the jwt are through html5 web storage or cookies. what to do if your jwt is stolen. An attacker can now impersonate a client and. Once a jwt has been stolen, you’ll be in a bad situation: which libraries are vulnerable to attacks and. How To Prevent Jwt Attacks.
From www.youtube.com
Introduction to JWT Attacks YouTube How To Prevent Jwt Attacks There are two ways of storing the. this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. the most common methods of storing the jwt are through html5 web storage or cookies. Once a jwt has been stolen, you’ll be in a bad situation: Protection of the crypto keys (server side).. How To Prevent Jwt Attacks.
From www.youtube.com
JWT authentication bypass via flawed signature verification How To Prevent Jwt Attacks Once a jwt has been stolen, you’ll be in a bad situation: the most common methods of storing the jwt are through html5 web storage or cookies. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing additional security measures such as token expiration. How To Prevent Jwt Attacks.
From amandaguglieri.github.io
JWT tool Hacking Life How To Prevent Jwt Attacks which libraries are vulnerable to attacks and how to prevent them. An attacker can now impersonate a client and. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing additional security measures such as token expiration and access control. the most common methods. How To Prevent Jwt Attacks.
From kathan19.gitbook.io
JWT HowToHunt How To Prevent Jwt Attacks the most common methods of storing the jwt are through html5 web storage or cookies. this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. An attacker can now impersonate a client and. what to do if your jwt is stolen. which libraries are vulnerable to attacks and how. How To Prevent Jwt Attacks.
From medium.com
Securing Microservices with JWT. Secured Order Management System with How To Prevent Jwt Attacks what to do if your jwt is stolen. Once a jwt has been stolen, you’ll be in a bad situation: Protection of the crypto keys (server side). which libraries are vulnerable to attacks and how to prevent them. An attacker can now impersonate a client and. this cheatsheet provides tips to prevent common security issues when using. How To Prevent Jwt Attacks.
From bornsec.com
PenTesting JWT (JSON WEB TOKEN) Bornsec Consulting is Security How To Prevent Jwt Attacks Protection of the crypto keys (server side). There are two ways of storing the. which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing additional security measures such as token expiration and access. How To Prevent Jwt Attacks.
From github.com
How to prevent log out users when changing JWT secret? · Issue 2053 How To Prevent Jwt Attacks Once a jwt has been stolen, you’ll be in a bad situation: what to do if your jwt is stolen. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing additional security measures such as token expiration and access control. the most common. How To Prevent Jwt Attacks.
From cyberw1ng.medium.com
JWT attack vulnerabilities in App Testing 2023 by How To Prevent Jwt Attacks Protection of the crypto keys (server side). There are two ways of storing the. what to do if your jwt is stolen. which libraries are vulnerable to attacks and how to prevent them. this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. the most common methods of storing. How To Prevent Jwt Attacks.
From blog.bytebytego.com
Password, Session, Cookie, Token, JWT, SSO, OAuth Authentication How To Prevent Jwt Attacks Once a jwt has been stolen, you’ll be in a bad situation: this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. There are two ways of storing the. what to do if your jwt is stolen. the most common methods of storing the jwt are through html5 web storage. How To Prevent Jwt Attacks.
From ritikchourasiya.medium.com
What is JWT Token and How it works by Ritik Chourasiya Medium How To Prevent Jwt Attacks An attacker can now impersonate a client and. this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. the most common methods of storing the jwt are through html5 web storage or cookies. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using. How To Prevent Jwt Attacks.
From www.youtube.com
JSON Token Vulnerabilty JWT Authentication Bypass Via Algorithm How To Prevent Jwt Attacks An attacker can now impersonate a client and. which libraries are vulnerable to attacks and how to prevent them. the most common methods of storing the jwt are through html5 web storage or cookies. There are two ways of storing the. this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with. How To Prevent Jwt Attacks.
From medium.com
All about JWT attacks Portswigger web academy lab solutions, JWT How To Prevent Jwt Attacks There are two ways of storing the. this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. the most common methods of storing the jwt are through html5 web storage or cookies. Protection of the crypto keys (server side). which libraries are vulnerable to attacks and how to prevent them.. How To Prevent Jwt Attacks.
From towardsdev.com
JWT attacks. How it normally works vs How jwt works… by How To Prevent Jwt Attacks There are two ways of storing the. Protection of the crypto keys (server side). An attacker can now impersonate a client and. which libraries are vulnerable to attacks and how to prevent them. Once a jwt has been stolen, you’ll be in a bad situation: organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation. How To Prevent Jwt Attacks.
From www.youtube.com
ATTACKING JWT FOR BEGINNERS! YouTube How To Prevent Jwt Attacks which libraries are vulnerable to attacks and how to prevent them. the most common methods of storing the jwt are through html5 web storage or cookies. Once a jwt has been stolen, you’ll be in a bad situation: organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and. How To Prevent Jwt Attacks.
From content.noroff.dev
JWT Noroff Frontend Development How To Prevent Jwt Attacks There are two ways of storing the. which libraries are vulnerable to attacks and how to prevent them. Once a jwt has been stolen, you’ll be in a bad situation: organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing additional security measures such. How To Prevent Jwt Attacks.
From payatu.com
JWT Vulnerabilities Application Security in the Modern Age How To Prevent Jwt Attacks An attacker can now impersonate a client and. which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing additional security measures such as token expiration and access control. Protection of the crypto keys. How To Prevent Jwt Attacks.
From tcrsecurity.com
jwt attacks How To Prevent Jwt Attacks There are two ways of storing the. Once a jwt has been stolen, you’ll be in a bad situation: which libraries are vulnerable to attacks and how to prevent them. this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. An attacker can now impersonate a client and. organizations can. How To Prevent Jwt Attacks.
From auth0.com
A Look at The Draft for JWT Best Current Practices How To Prevent Jwt Attacks which libraries are vulnerable to attacks and how to prevent them. There are two ways of storing the. this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately,. How To Prevent Jwt Attacks.
From app.letsdefend.io
JWT Attacks and Detection LetsDefend How To Prevent Jwt Attacks organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing additional security measures such as token expiration and access control. An attacker can now impersonate a client and. Protection of the crypto keys (server side). this cheatsheet provides tips to prevent common security issues. How To Prevent Jwt Attacks.
From research.securitum.com
JWT (JSON Token) (in)security How To Prevent Jwt Attacks An attacker can now impersonate a client and. which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing additional security measures such as token expiration and access control. this cheatsheet provides tips. How To Prevent Jwt Attacks.
From medium.com
JWT Things to be CAREFul. Security risks from weak JWT by Subh Medium How To Prevent Jwt Attacks what to do if your jwt is stolen. There are two ways of storing the. Protection of the crypto keys (server side). which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing. How To Prevent Jwt Attacks.
From velog.io
[Spring] Security JWT How To Prevent Jwt Attacks There are two ways of storing the. the most common methods of storing the jwt are through html5 web storage or cookies. Protection of the crypto keys (server side). An attacker can now impersonate a client and. Once a jwt has been stolen, you’ll be in a bad situation: which libraries are vulnerable to attacks and how to. How To Prevent Jwt Attacks.
From medium.com
Implementing JWT Authentication in Laravel A StepbyStep Guide by How To Prevent Jwt Attacks which libraries are vulnerable to attacks and how to prevent them. Once a jwt has been stolen, you’ll be in a bad situation: this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. what to do if your jwt is stolen. There are two ways of storing the. Protection of. How To Prevent Jwt Attacks.
From sec.ud64.com
Your Guide To JWT Attacks Security Alert How To Prevent Jwt Attacks An attacker can now impersonate a client and. what to do if your jwt is stolen. the most common methods of storing the jwt are through html5 web storage or cookies. this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. which libraries are vulnerable to attacks and how. How To Prevent Jwt Attacks.
From www.vrogue.co
How To Use Oauth2 And Jwt To Secure Microservice Arch vrogue.co How To Prevent Jwt Attacks There are two ways of storing the. the most common methods of storing the jwt are through html5 web storage or cookies. An attacker can now impersonate a client and. Once a jwt has been stolen, you’ll be in a bad situation: organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. How To Prevent Jwt Attacks.
From www.youtube.com
Understanding JWT Vulnerabilities JWT Crack Attack YouTube How To Prevent Jwt Attacks this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. which libraries are vulnerable to attacks and how to prevent them. An attacker can now impersonate a client and. what to do if your jwt is stolen. Once a jwt has been stolen, you’ll be in a bad situation: . How To Prevent Jwt Attacks.
From aspiainfotech.com
JSON Tokens Recognizing And Preventing JWT Attacks ASPIA InfoTech How To Prevent Jwt Attacks this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. An attacker can now impersonate a client and. what to do if your jwt is stolen. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures, using encryption and signature algorithms appropriately, and implementing. How To Prevent Jwt Attacks.
From medium.com
Implementing JWT with Spring Boot and Spring Security How To Prevent Jwt Attacks There are two ways of storing the. An attacker can now impersonate a client and. which libraries are vulnerable to attacks and how to prevent them. what to do if your jwt is stolen. Protection of the crypto keys (server side). the most common methods of storing the jwt are through html5 web storage or cookies. . How To Prevent Jwt Attacks.
From www.youtube.com
JWT Authentication bypass via unverified Signature LAB JSON How To Prevent Jwt Attacks which libraries are vulnerable to attacks and how to prevent them. Protection of the crypto keys (server side). this cheatsheet provides tips to prevent common security issues when using json web tokens (jwt) with java. what to do if your jwt is stolen. Once a jwt has been stolen, you’ll be in a bad situation: There are. How To Prevent Jwt Attacks.