How Does Ntlm Relay Work . How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards them to the server. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. First, the client tells the server that it wants to authenticate. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The principle of ntlm authentication is as follows:
from securityboulevard.com
How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards them to the server. First, the client tells the server that it wants to authenticate. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The principle of ntlm authentication is as follows:
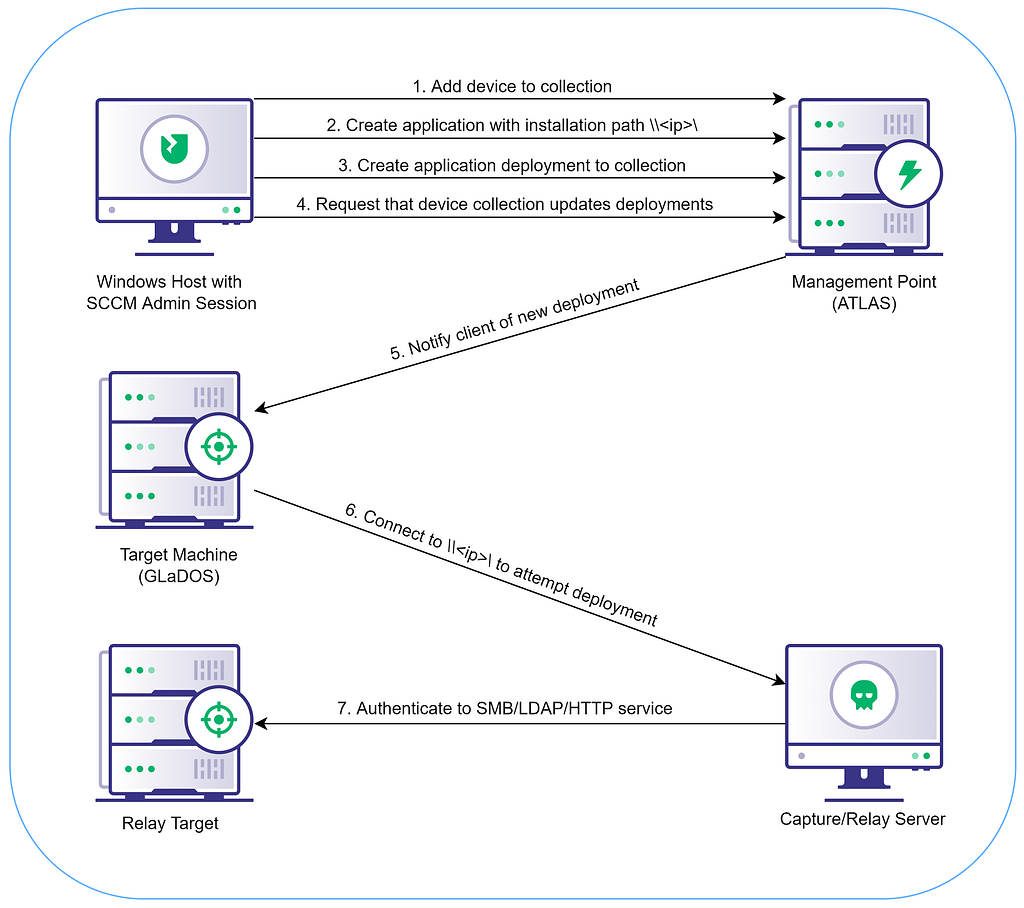
Relaying NTLM Authentication from SCCM Clients Security Boulevard
How Does Ntlm Relay Work The principle of ntlm authentication is as follows: The approach we’re using is to authenticate users locally, against our server, grab their identities, and. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards them to the server. First, the client tells the server that it wants to authenticate. The principle of ntlm authentication is as follows:
From www.crowdstrike.com
Security Advisory MSRPC Printer Spooler Relay (CVE20211678) How Does Ntlm Relay Work In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. First, the client tells the server that it wants to authenticate. How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards them to the server. The approach we’re using is to authenticate users locally,. How Does Ntlm Relay Work.
From tocontactme.blogspot.com
Active Directory Concepts (2) How Does Ntlm Relay Work The principle of ntlm authentication is as follows: The approach we’re using is to authenticate users locally, against our server, grab their identities, and. An attacker intercepts legitimate authentication requests and then forwards them to the server. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. How. How Does Ntlm Relay Work.
From en.hackndo.com
NTLM Relay hackndo How Does Ntlm Relay Work An attacker intercepts legitimate authentication requests and then forwards them to the server. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. First, the client tells the server that it wants to authenticate. How does ntlm authentication work? In a ntlm relay attack, an attacker establishes a position between the client and server. How Does Ntlm Relay Work.
From manesec.blogspot.com
DFSCoerce NTLM Relay Attack to Domain Admin How Does Ntlm Relay Work An attacker intercepts legitimate authentication requests and then forwards them to the server. How does ntlm authentication work? The principle of ntlm authentication is as follows: In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The approach we’re using is to authenticate users locally, against our server,. How Does Ntlm Relay Work.
From www.extrahop.com
PetitPotam Expanding NTLM Relay Attacks ExtraHop How Does Ntlm Relay Work How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards them to the server. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. First, the client tells the server that it wants to authenticate. In a ntlm relay attack, an attacker establishes a position between the client and server. How Does Ntlm Relay Work.
From www.extrahop.com
PetitPotam Expanding NTLM Relay Attacks ExtraHop How Does Ntlm Relay Work First, the client tells the server that it wants to authenticate. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. The principle of ntlm authentication is as follows: How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards them to the server. In a ntlm relay attack, an attacker. How Does Ntlm Relay Work.
From www.fortalicesolutions.com
Keeping Up with the NTLM Relay How Does Ntlm Relay Work First, the client tells the server that it wants to authenticate. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The principle of ntlm authentication is as follows: An attacker intercepts. How Does Ntlm Relay Work.
From gbhackers.com
Microsoft NTLM Vulnerability Let Hackers to Compromise DC How Does Ntlm Relay Work In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards them to the server. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. First, the client tells. How Does Ntlm Relay Work.
From www.youtube.com
What is NTLM? What is the NTLM process & how does it work? NTLM vs How Does Ntlm Relay Work First, the client tells the server that it wants to authenticate. How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards them to the server. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. In a ntlm relay attack, an attacker establishes a position between the client and server. How Does Ntlm Relay Work.
From securityboulevard.com
The Elephant In the Room NTLM Coercion and Understanding Its Impact How Does Ntlm Relay Work First, the client tells the server that it wants to authenticate. An attacker intercepts legitimate authentication requests and then forwards them to the server. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The approach we’re using is to authenticate users locally, against our server, grab their. How Does Ntlm Relay Work.
From medium.com
NTLM Relay Attack. NetBIOS Basic Input / Output… by Orhan How Does Ntlm Relay Work An attacker intercepts legitimate authentication requests and then forwards them to the server. First, the client tells the server that it wants to authenticate. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts. How Does Ntlm Relay Work.
From www.redlings.com
NTLM Authentication Definition, Protocol & Vulnerabilities >>Redlings How Does Ntlm Relay Work First, the client tells the server that it wants to authenticate. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. The principle of ntlm authentication is as follows: How does ntlm authentication work? In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts. How Does Ntlm Relay Work.
From www.redlings.com
NTLMAuthentifizierung Definition, Protokoll & Sicherheitslücken How Does Ntlm Relay Work In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. First, the client tells the server that it wants to authenticate. An attacker intercepts legitimate authentication requests and then forwards them to the server. The principle of ntlm authentication is as follows: How does ntlm authentication work? The. How Does Ntlm Relay Work.
From engineerfix.com
How Do Relays Work? (All You Need To Know) Engineer Fix How Does Ntlm Relay Work The approach we’re using is to authenticate users locally, against our server, grab their identities, and. How does ntlm authentication work? In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The principle of ntlm authentication is as follows: First, the client tells the server that it wants. How Does Ntlm Relay Work.
From www.vaadata.com
Understanding NTLM Authentication and NTLM Relay Attacks How Does Ntlm Relay Work First, the client tells the server that it wants to authenticate. An attacker intercepts legitimate authentication requests and then forwards them to the server. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The principle of ntlm authentication is as follows: How does ntlm authentication work? The. How Does Ntlm Relay Work.
From redcursor.com.au
Capturing & Relaying NTLM Authentication Testing Sydney How Does Ntlm Relay Work The approach we’re using is to authenticate users locally, against our server, grab their identities, and. How does ntlm authentication work? First, the client tells the server that it wants to authenticate. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. An attacker intercepts legitimate authentication requests. How Does Ntlm Relay Work.
From en.hackndo.com
NTLM Relay hackndo How Does Ntlm Relay Work In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards them to the server. First, the client tells. How Does Ntlm Relay Work.
From academy.hackthebox.com
NTLM Relay Attacks Course HTB Academy How Does Ntlm Relay Work In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. First, the client tells the server that it wants to authenticate. How does ntlm authentication work? An attacker intercepts legitimate authentication requests. How Does Ntlm Relay Work.
From www.fortalicesolutions.com
Keeping Up with the NTLM Relay How Does Ntlm Relay Work The principle of ntlm authentication is as follows: In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards. How Does Ntlm Relay Work.
From posts.specterops.io
Coercing NTLM Authentication from SCCM by Chris Thompson Posts By How Does Ntlm Relay Work How does ntlm authentication work? The approach we’re using is to authenticate users locally, against our server, grab their identities, and. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. An attacker intercepts legitimate authentication requests and then forwards them to the server. First, the client tells. How Does Ntlm Relay Work.
From en.hackndo.com
NTLM Relay hackndo How Does Ntlm Relay Work How does ntlm authentication work? The approach we’re using is to authenticate users locally, against our server, grab their identities, and. First, the client tells the server that it wants to authenticate. An attacker intercepts legitimate authentication requests and then forwards them to the server. The principle of ntlm authentication is as follows: In a ntlm relay attack, an attacker. How Does Ntlm Relay Work.
From kapitanhack.pl
Przeprowadzenie ataku NTLM Relay z wykorzystaniem usług Active How Does Ntlm Relay Work An attacker intercepts legitimate authentication requests and then forwards them to the server. First, the client tells the server that it wants to authenticate. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. How does ntlm authentication work? In a ntlm relay attack, an attacker establishes a position between the client and server. How Does Ntlm Relay Work.
From en.hackndo.com
NTLM Relay hackndo How Does Ntlm Relay Work First, the client tells the server that it wants to authenticate. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. An attacker intercepts legitimate authentication requests and then forwards them to. How Does Ntlm Relay Work.
From www.slideserve.com
PPT NTLM Relay Attacks PowerPoint Presentation, free download ID How Does Ntlm Relay Work The principle of ntlm authentication is as follows: The approach we’re using is to authenticate users locally, against our server, grab their identities, and. An attacker intercepts legitimate authentication requests and then forwards them to the server. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. How. How Does Ntlm Relay Work.
From www.semperis.com
How to Defend Against an NTLM Relay Attack AD Security 101 How Does Ntlm Relay Work The principle of ntlm authentication is as follows: The approach we’re using is to authenticate users locally, against our server, grab their identities, and. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. First, the client tells the server that it wants to authenticate. How does ntlm. How Does Ntlm Relay Work.
From en.hackndo.com
NTLM Relay hackndo How Does Ntlm Relay Work How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards them to the server. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The principle of ntlm. How Does Ntlm Relay Work.
From socradar.io
NTLM Relay Attack Leads to Windows Domain Takeover SOCRadar® Cyber How Does Ntlm Relay Work The approach we’re using is to authenticate users locally, against our server, grab their identities, and. First, the client tells the server that it wants to authenticate. An attacker intercepts legitimate authentication requests and then forwards them to the server. How does ntlm authentication work? The principle of ntlm authentication is as follows: In a ntlm relay attack, an attacker. How Does Ntlm Relay Work.
From en.hackndo.com
NTLM Relay hackndo How Does Ntlm Relay Work The principle of ntlm authentication is as follows: How does ntlm authentication work? In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. First, the client tells the server that it wants. How Does Ntlm Relay Work.
From www.usenix.org
NTLM Authentication How Does Ntlm Relay Work How does ntlm authentication work? In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. An attacker intercepts legitimate authentication requests and then forwards them to the server. First, the client tells. How Does Ntlm Relay Work.
From academy.hackthebox.com
NTLM Relay Attacks Course HTB Academy How Does Ntlm Relay Work An attacker intercepts legitimate authentication requests and then forwards them to the server. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. First, the client tells the server that it wants to authenticate. The approach we’re using is to authenticate users locally, against our server, grab their. How Does Ntlm Relay Work.
From securityboulevard.com
Relaying NTLM Authentication from SCCM Clients Security Boulevard How Does Ntlm Relay Work How does ntlm authentication work? The approach we’re using is to authenticate users locally, against our server, grab their identities, and. In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The principle of ntlm authentication is as follows: An attacker intercepts legitimate authentication requests and then forwards. How Does Ntlm Relay Work.
From blog.csdn.net
NTLMrelay攻击的原理与实现_ntlmssp攻击CSDN博客 How Does Ntlm Relay Work In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The principle of ntlm authentication is as follows: How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards them to the server. The approach we’re using is to authenticate users locally, against our server,. How Does Ntlm Relay Work.
From www.vaadata.com
Internal Pentesting Objective, Methodology & Use Cases How Does Ntlm Relay Work In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. First, the client tells the server that it wants to authenticate. The principle of ntlm authentication is as follows: The approach we’re using is to authenticate users locally, against our server, grab their identities, and. An attacker intercepts. How Does Ntlm Relay Work.
From en.hackndo.com
NTLM Relay hackndo How Does Ntlm Relay Work How does ntlm authentication work? The principle of ntlm authentication is as follows: In a ntlm relay attack, an attacker establishes a position between the client and server on the network and intercepts authentication traffic. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. First, the client tells the server that it wants. How Does Ntlm Relay Work.
From blog.compass-security.com
Relaying NTLM to MSSQL Compass Security Blog How Does Ntlm Relay Work How does ntlm authentication work? An attacker intercepts legitimate authentication requests and then forwards them to the server. The approach we’re using is to authenticate users locally, against our server, grab their identities, and. The principle of ntlm authentication is as follows: In a ntlm relay attack, an attacker establishes a position between the client and server on the network. How Does Ntlm Relay Work.