Incident Response Rules Of Engagement . Ttes are designed to prepare for real cybersecurity incidents. The aim of incident response is to identify the scope of the events,. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Incident response is an approach to handling security breaches. Computer security incident response has become an important component of information technology (it) programs. By conducting ttes, an incident response team increases its. This paper provides an overview of the cyber exercise process from inception to reporting. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and.
from www.pagerduty.com
The aim of incident response is to identify the scope of the events,. Incident response is the strategic, organized responsed an organization uses following a cyberattack. By conducting ttes, an incident response team increases its. Computer security incident response has become an important component of information technology (it) programs. Incident response is an approach to handling security breaches. This paper provides an overview of the cyber exercise process from inception to reporting. Ttes are designed to prepare for real cybersecurity incidents. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and.
What is an Incident Response Process PagerDuty
Incident Response Rules Of Engagement Computer security incident response has become an important component of information technology (it) programs. Ttes are designed to prepare for real cybersecurity incidents. Incident response is an approach to handling security breaches. This paper provides an overview of the cyber exercise process from inception to reporting. The aim of incident response is to identify the scope of the events,. By conducting ttes, an incident response team increases its. Computer security incident response has become an important component of information technology (it) programs. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Incident response is the strategic, organized responsed an organization uses following a cyberattack.
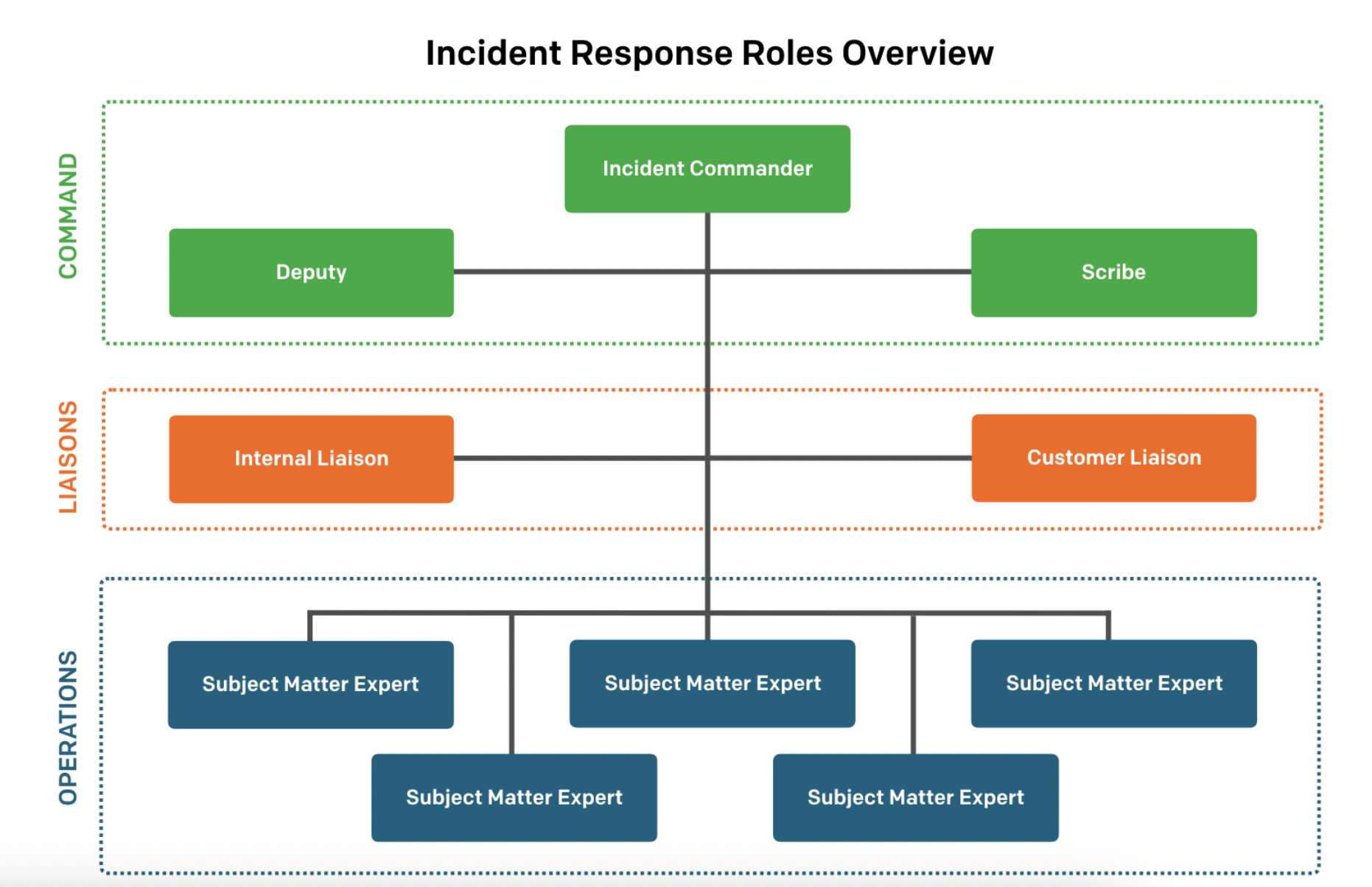
From rolesresponsibility.netlify.app
Roles and responsibilities of incident management team Incident Response Rules Of Engagement Computer security incident response has become an important component of information technology (it) programs. Incident response is an approach to handling security breaches. By conducting ttes, an incident response team increases its. The aim of incident response is to identify the scope of the events,. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to. Incident Response Rules Of Engagement.
From www.stealthlabs.com
7 Tips to Build an Effective Cyber Incident Response Plan Incident Response Rules Of Engagement Ttes are designed to prepare for real cybersecurity incidents. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. By conducting ttes, an incident response team increases its. Incident response is an approach to handling security breaches. This paper provides an overview of the cyber exercise process from inception to reporting. The. Incident Response Rules Of Engagement.
From www.agedcarequality.gov.au
About the Serious Incident Response Scheme (SIRS) Aged Care Quality Incident Response Rules Of Engagement Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. By conducting ttes, an incident response team increases its. The aim of incident response is to identify the scope of the events,. Ttes are designed to prepare for real cybersecurity incidents. Computer security incident response has become an important component of information. Incident Response Rules Of Engagement.
From www.esentire.com
eSentire OnDemand Incident Response Service Incident Response Rules Of Engagement Computer security incident response has become an important component of information technology (it) programs. Incident response is the strategic, organized responsed an organization uses following a cyberattack. The aim of incident response is to identify the scope of the events,. By conducting ttes, an incident response team increases its. Ttes are designed to prepare for real cybersecurity incidents. This paper. Incident Response Rules Of Engagement.
From www.pagerduty.com
What is an Incident Response Process PagerDuty Incident Response Rules Of Engagement The aim of incident response is to identify the scope of the events,. Ttes are designed to prepare for real cybersecurity incidents. Incident response is an approach to handling security breaches. Computer security incident response has become an important component of information technology (it) programs. This paper provides an overview of the cyber exercise process from inception to reporting. By. Incident Response Rules Of Engagement.
From www.cyberstonesecurity.com
Services Cyberstone Security Incident Response Rules Of Engagement Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Computer security incident response has become an important component of information technology (it) programs. The aim of incident response is to identify the scope of the events,. Ttes are designed to prepare for real cybersecurity incidents. This paper provides an overview of. Incident Response Rules Of Engagement.
From securityboulevard.com
What is Incident Response? Plans, Templates and Tools Security Boulevard Incident Response Rules Of Engagement Incident response is an approach to handling security breaches. By conducting ttes, an incident response team increases its. Ttes are designed to prepare for real cybersecurity incidents. This paper provides an overview of the cyber exercise process from inception to reporting. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Computer. Incident Response Rules Of Engagement.
From microage.com
Understanding the 6 Elements of the Incident Response (IR) Process Incident Response Rules Of Engagement This paper provides an overview of the cyber exercise process from inception to reporting. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Incident response is an approach to handling security breaches. Ttes are designed to prepare for. Incident Response Rules Of Engagement.
From www.tomassociatesng.com
INCIDENT INVESTIGATION AND REPORTING Tom Associates Training Incident Response Rules Of Engagement Ttes are designed to prepare for real cybersecurity incidents. Incident response is an approach to handling security breaches. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. This paper provides an overview of the cyber exercise process from. Incident Response Rules Of Engagement.
From www.titanfile.com
7 Phases of Incident Response Essential Steps for a Comprehensive Incident Response Rules Of Engagement Incident response is the strategic, organized responsed an organization uses following a cyberattack. This paper provides an overview of the cyber exercise process from inception to reporting. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Incident response is an approach to handling security breaches. Ttes are designed to prepare for. Incident Response Rules Of Engagement.
From www.collidu.com
Incident Response Timeline PowerPoint Presentation Slides PPT Template Incident Response Rules Of Engagement Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Computer security incident response has become an important component of information technology (it) programs. This paper provides an overview of the cyber exercise process from inception to reporting. Incident response is the strategic, organized responsed an organization uses following a cyberattack. The. Incident Response Rules Of Engagement.
From www.slideteam.net
Incident Response Procedures Employee Engagement Model Strategic Incident Response Rules Of Engagement This paper provides an overview of the cyber exercise process from inception to reporting. Incident response is the strategic, organized responsed an organization uses following a cyberattack. The aim of incident response is to identify the scope of the events,. Ttes are designed to prepare for real cybersecurity incidents. Incident response (ir) refers to an organization’s processes and systems for. Incident Response Rules Of Engagement.
From www.linkedin.com
Key Skills & Traits of an Effective Incident Response Team Incident Response Rules Of Engagement Ttes are designed to prepare for real cybersecurity incidents. Incident response is an approach to handling security breaches. By conducting ttes, an incident response team increases its. The aim of incident response is to identify the scope of the events,. Incident response is the strategic, organized responsed an organization uses following a cyberattack. This paper provides an overview of the. Incident Response Rules Of Engagement.
From old.sermitsiaq.ag
Dod Incident Response Plan Template Incident Response Rules Of Engagement Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Ttes are designed to prepare for real cybersecurity incidents. The aim of incident response is to identify the scope of the events,. This paper provides an overview of the. Incident Response Rules Of Engagement.
From metaorangedigital.com
Incident Response Process in Cybersecurity Incident Response Rules Of Engagement The aim of incident response is to identify the scope of the events,. Computer security incident response has become an important component of information technology (it) programs. By conducting ttes, an incident response team increases its. Ttes are designed to prepare for real cybersecurity incidents. This paper provides an overview of the cyber exercise process from inception to reporting. Incident. Incident Response Rules Of Engagement.
From cybersecurity.att.com
Building an Effective Incident Response Framework Infographic LevelBlue Incident Response Rules Of Engagement This paper provides an overview of the cyber exercise process from inception to reporting. The aim of incident response is to identify the scope of the events,. By conducting ttes, an incident response team increases its. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Incident response is an approach to handling security breaches. Ttes are. Incident Response Rules Of Engagement.
From www.zenduty.com
Mastering The Incident Response Lifecycle Zenduty Incident Response Rules Of Engagement This paper provides an overview of the cyber exercise process from inception to reporting. Computer security incident response has become an important component of information technology (it) programs. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Incident response is an approach to handling security breaches. The aim of incident response is to identify the scope. Incident Response Rules Of Engagement.
From www.slideteam.net
Nist Framework For Incident Response Phases PPT Sample Incident Response Rules Of Engagement Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. This paper provides an overview of the cyber exercise process from inception to reporting. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Incident response is an approach to handling security breaches. Computer security incident response has become. Incident Response Rules Of Engagement.
From venngage.com
Incident Response Plan Template Venngage Incident Response Rules Of Engagement By conducting ttes, an incident response team increases its. Incident response is an approach to handling security breaches. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Computer security incident response has become an important component of information. Incident Response Rules Of Engagement.
From cybersecurity.ng-it.co.uk
NG IT Incident Response NG IT Cybersecurity Hub Incident Response Rules Of Engagement By conducting ttes, an incident response team increases its. This paper provides an overview of the cyber exercise process from inception to reporting. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. The aim of incident response is to identify the scope of the events,. Computer security incident response has become. Incident Response Rules Of Engagement.
From ebrp.net
Incident Response Simplified An Infographic eBRP Solutions Network Incident Response Rules Of Engagement Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. The aim of incident response is to identify the scope of the events,. By conducting ttes, an incident response team increases its. Ttes are designed to prepare for real cybersecurity incidents. Computer security incident response has become an important component of information. Incident Response Rules Of Engagement.
From www.progressive.in
Incident Response Management Top Practices and Tips Incident Response Rules Of Engagement This paper provides an overview of the cyber exercise process from inception to reporting. Ttes are designed to prepare for real cybersecurity incidents. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Computer security incident response has become an important component of information technology (it) programs. Incident response (ir) refers to an organization’s processes and systems. Incident Response Rules Of Engagement.
From issuu.com
Incident Response Roles and Responsibilities by Secure Curve Issuu Incident Response Rules Of Engagement The aim of incident response is to identify the scope of the events,. Computer security incident response has become an important component of information technology (it) programs. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Incident response. Incident Response Rules Of Engagement.
From studymoose.com
Reflective Critical Incident Analysis of an Engagement Free Essay Example Incident Response Rules Of Engagement By conducting ttes, an incident response team increases its. Incident response is the strategic, organized responsed an organization uses following a cyberattack. This paper provides an overview of the cyber exercise process from inception to reporting. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. The aim of incident response is. Incident Response Rules Of Engagement.
From blueteamresources.in
10 Proven Incident Response Strategies for SOC Analysts Incident Response Rules Of Engagement By conducting ttes, an incident response team increases its. Incident response is an approach to handling security breaches. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Ttes are designed to prepare for real cybersecurity incidents. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. This paper. Incident Response Rules Of Engagement.
From www.smartsheet.com
Emergency Management Incident Command Smartsheet Incident Response Rules Of Engagement By conducting ttes, an incident response team increases its. The aim of incident response is to identify the scope of the events,. Ttes are designed to prepare for real cybersecurity incidents. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Computer security incident response has become an important component of information. Incident Response Rules Of Engagement.
From www.manageengine.com
Managing security incidents using SIEM Incident Response Rules Of Engagement By conducting ttes, an incident response team increases its. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Computer security incident response has become an important component of information technology (it) programs. This paper provides an overview of the cyber exercise process from inception to reporting. The aim of incident response. Incident Response Rules Of Engagement.
From keycore.dk
Incident Management Keycore Incident Response Rules Of Engagement Incident response is the strategic, organized responsed an organization uses following a cyberattack. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Ttes are designed to prepare for real cybersecurity incidents. Incident response is an approach to handling security breaches. Computer security incident response has become an important component of information. Incident Response Rules Of Engagement.
From medium.com
Incident Response Strategies Rakish Medium Incident Response Rules Of Engagement Incident response is an approach to handling security breaches. Computer security incident response has become an important component of information technology (it) programs. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Ttes are designed to prepare for real cybersecurity incidents. By conducting ttes, an incident response team increases its. The aim of incident response is. Incident Response Rules Of Engagement.
From secondvictim.co.uk
Supporting Second Victims Second Victim Incident Response Rules Of Engagement Ttes are designed to prepare for real cybersecurity incidents. Computer security incident response has become an important component of information technology (it) programs. By conducting ttes, an incident response team increases its. The aim of incident response is to identify the scope of the events,. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Incident response. Incident Response Rules Of Engagement.
From www.agedcarequality.gov.au
Serious Incident Response Scheme Guidelines for providers of home Incident Response Rules Of Engagement This paper provides an overview of the cyber exercise process from inception to reporting. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to cybersecurity threats and. Incident response is the strategic, organized responsed an organization uses following a cyberattack. By conducting ttes, an incident response team increases its. The aim of incident response is. Incident Response Rules Of Engagement.
From www.template.net
Incident Response Plan Flow Chart in Illustrator, PDF Download Incident Response Rules Of Engagement Incident response is an approach to handling security breaches. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Ttes are designed to prepare for real cybersecurity incidents. This paper provides an overview of the cyber exercise process from inception to reporting. By conducting ttes, an incident response team increases its. Incident response (ir) refers to an. Incident Response Rules Of Engagement.
From www.slideteam.net
Cyber Security Incident Response Process Flow Chart Deploying Computer Incident Response Rules Of Engagement Ttes are designed to prepare for real cybersecurity incidents. Computer security incident response has become an important component of information technology (it) programs. Incident response is the strategic, organized responsed an organization uses following a cyberattack. The aim of incident response is to identify the scope of the events,. By conducting ttes, an incident response team increases its. This paper. Incident Response Rules Of Engagement.
From www.zenduty.com
Mastering The Incident Response Lifecycle Zenduty Incident Response Rules Of Engagement Computer security incident response has become an important component of information technology (it) programs. This paper provides an overview of the cyber exercise process from inception to reporting. The aim of incident response is to identify the scope of the events,. Incident response is the strategic, organized responsed an organization uses following a cyberattack. Incident response is an approach to. Incident Response Rules Of Engagement.
From mavink.com
Incident Response Life Cycle Diagram Incident Response Rules Of Engagement This paper provides an overview of the cyber exercise process from inception to reporting. The aim of incident response is to identify the scope of the events,. Incident response is an approach to handling security breaches. Ttes are designed to prepare for real cybersecurity incidents. Incident response (ir) refers to an organization’s processes and systems for discovering and responding to. Incident Response Rules Of Engagement.