Clipboard Buffer Caching Vulnerability Example . Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. But this creates serious issue when some other application. Example scenarios for unintended data leakage. What is unintended data leakage? In most cases, attackers leverage malware that either steals data. What is the difference between insecure data storage and unintended data leakage? How does unintended data leakage work? This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. Leveraging clipboards can enable attackers to collect target information and exfiltrate useful data. How to prevent unintended data leakage? Below is the list of example scenarios where unintended data leakage flaws. Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. Are you vulnerable to unintended data leakage? Example of unintended data leakage.
from www.slideserve.com
Are you vulnerable to unintended data leakage? How does unintended data leakage work? What is unintended data leakage? But this creates serious issue when some other application. Below is the list of example scenarios where unintended data leakage flaws. Leveraging clipboards can enable attackers to collect target information and exfiltrate useful data. Example scenarios for unintended data leakage. Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. What is the difference between insecure data storage and unintended data leakage?
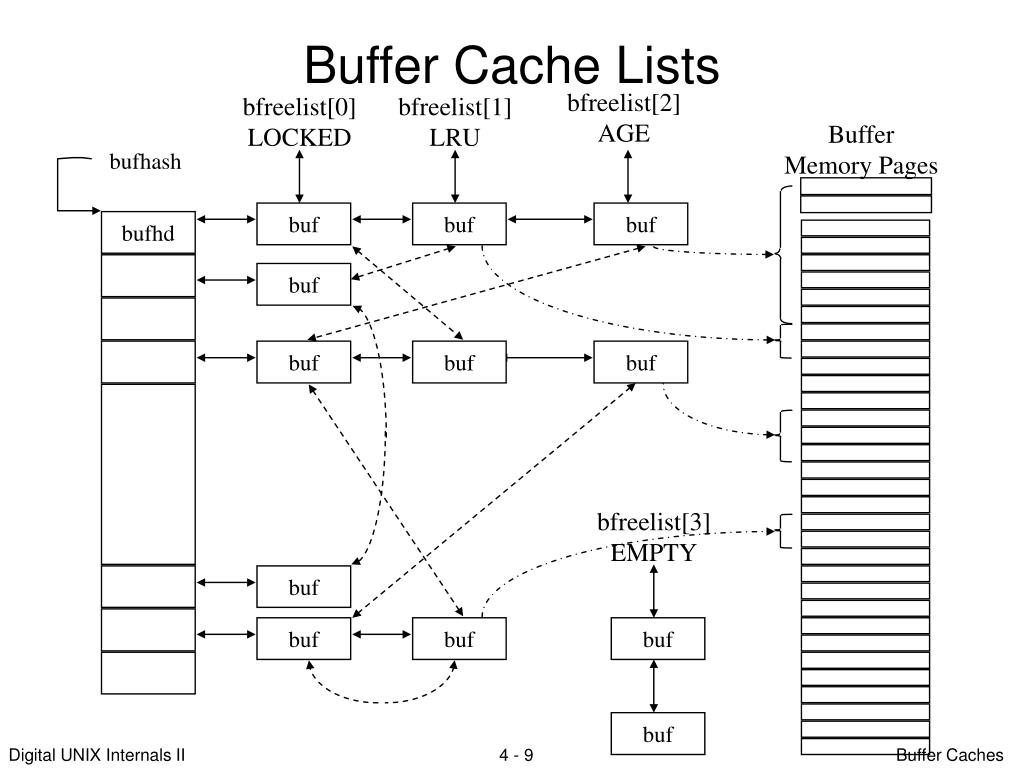
PPT Buffer Caches PowerPoint Presentation, free download ID3268607
Clipboard Buffer Caching Vulnerability Example Leveraging clipboards can enable attackers to collect target information and exfiltrate useful data. Example scenarios for unintended data leakage. But this creates serious issue when some other application. Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. What is unintended data leakage? What is the difference between insecure data storage and unintended data leakage? Example of unintended data leakage. Below is the list of example scenarios where unintended data leakage flaws. How to prevent unintended data leakage? In most cases, attackers leverage malware that either steals data. Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. Leveraging clipboards can enable attackers to collect target information and exfiltrate useful data. Are you vulnerable to unintended data leakage? How does unintended data leakage work? This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can.
From www.slideserve.com
PPT Informed Prefetching and Caching PowerPoint Presentation, free Clipboard Buffer Caching Vulnerability Example Example of unintended data leakage. Example scenarios for unintended data leakage. What is unintended data leakage? Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. This will be a very prevalent vulnerability for code. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT Buffer Cache Waits PowerPoint Presentation, free download ID319874 Clipboard Buffer Caching Vulnerability Example Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. Are you vulnerable to unintended data leakage? What is the difference between insecure data storage and unintended. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT Caching for File Systems PowerPoint Presentation, free download Clipboard Buffer Caching Vulnerability Example What is the difference between insecure data storage and unintended data leakage? How to prevent unintended data leakage? How does unintended data leakage work? Example of unintended data leakage. This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. Are you vulnerable to unintended data leakage?. Clipboard Buffer Caching Vulnerability Example.
From blog.bytebytego.com
A Crash Course in Caching Part 1 by Alex Xu Clipboard Buffer Caching Vulnerability Example In most cases, attackers leverage malware that either steals data. Are you vulnerable to unintended data leakage? How to prevent unintended data leakage? Example scenarios for unintended data leakage. Example of unintended data leakage. Below is the list of example scenarios where unintended data leakage flaws. Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes,. Clipboard Buffer Caching Vulnerability Example.
From slideplayer.com
CS 414 Multimedia Systems Design Lecture 31 Media Server (Part 5 Clipboard Buffer Caching Vulnerability Example Are you vulnerable to unintended data leakage? Leveraging clipboards can enable attackers to collect target information and exfiltrate useful data. Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. Example of unintended data leakage.. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT Supporting Cooperative Caching in Disruption Tolerant Networks Clipboard Buffer Caching Vulnerability Example What is unintended data leakage? What is the difference between insecure data storage and unintended data leakage? This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. How does unintended data leakage work? Are you vulnerable to unintended data leakage? Leveraging clipboards can enable attackers to. Clipboard Buffer Caching Vulnerability Example.
From sematext.com
What Is Buffer Memory? Differences Compared to Cache Sematext Clipboard Buffer Caching Vulnerability Example Below is the list of example scenarios where unintended data leakage flaws. This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. But this creates serious issue when some other application. How to prevent unintended data leakage? Example of unintended data leakage. How does unintended data. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT Chapter 14 File System Implementation PowerPoint Presentation Clipboard Buffer Caching Vulnerability Example Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. Example scenarios for unintended data leakage.. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT Buffer Caches PowerPoint Presentation, free download ID3268607 Clipboard Buffer Caching Vulnerability Example How does unintended data leakage work? What is the difference between insecure data storage and unintended data leakage? Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. In most cases, attackers leverage malware that. Clipboard Buffer Caching Vulnerability Example.
From www.opennaukri.com
Buffer Memory and the Difference in Buffer and Cache Clipboard Buffer Caching Vulnerability Example Example scenarios for unintended data leakage. Leveraging clipboards can enable attackers to collect target information and exfiltrate useful data. In most cases, attackers leverage malware that either steals data. What is the difference between insecure data storage and unintended data leakage? What is unintended data leakage? Are you vulnerable to unintended data leakage? Example of unintended data leakage. Examples even. Clipboard Buffer Caching Vulnerability Example.
From vigilance.fr
Vulnerability about Squid cache buffer overflow via ESI Vigilance.fr Clipboard Buffer Caching Vulnerability Example Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. Below is the list of example scenarios where unintended data leakage flaws. How to prevent unintended data leakage? How does unintended data leakage work? Clipboard. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT Buffer Caches PowerPoint Presentation, free download ID3268607 Clipboard Buffer Caching Vulnerability Example How to prevent unintended data leakage? Are you vulnerable to unintended data leakage? Example of unintended data leakage. Below is the list of example scenarios where unintended data leakage flaws. But this creates serious issue when some other application. In most cases, attackers leverage malware that either steals data. What is unintended data leakage? Leveraging clipboards can enable attackers to. Clipboard Buffer Caching Vulnerability Example.
From anasbetis023.medium.com
Don’t Trust the Cache Exposing Cache Poisoning and Deception Clipboard Buffer Caching Vulnerability Example What is unintended data leakage? How does unintended data leakage work? Example scenarios for unintended data leakage. Below is the list of example scenarios where unintended data leakage flaws. Are you vulnerable to unintended data leakage? This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can.. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT The Buffer Cache PowerPoint Presentation, free download ID3713441 Clipboard Buffer Caching Vulnerability Example How to prevent unintended data leakage? But this creates serious issue when some other application. Leveraging clipboards can enable attackers to collect target information and exfiltrate useful data. What is unintended data leakage? In most cases, attackers leverage malware that either steals data. Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for. Clipboard Buffer Caching Vulnerability Example.
From vitolavecchia.altervista.org
Differenza tra cache e buffer in informatica Informatica e Ingegneria Clipboard Buffer Caching Vulnerability Example Example scenarios for unintended data leakage. Example of unintended data leakage. Below is the list of example scenarios where unintended data leakage flaws. Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. But this. Clipboard Buffer Caching Vulnerability Example.
From cs.brown.edu
Project 3 Caching I/O HackMD Clipboard Buffer Caching Vulnerability Example This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. But this creates serious issue when some other application. In most cases, attackers leverage malware that either steals data. Below is the list of example scenarios where unintended data leakage flaws. Leveraging clipboards can enable attackers. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT File Drivers and I/O Caching PowerPoint Presentation, free Clipboard Buffer Caching Vulnerability Example Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. What is unintended data leakage? How does unintended data leakage work? But this creates serious issue when some other application. Clipboard hijacking is an illicit. Clipboard Buffer Caching Vulnerability Example.
From www.enjoyalgorithms.com
Introduction to Caching and Caching Strategies Clipboard Buffer Caching Vulnerability Example Below is the list of example scenarios where unintended data leakage flaws. In most cases, attackers leverage malware that either steals data. How to prevent unintended data leakage? This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. How does unintended data leakage work? But this. Clipboard Buffer Caching Vulnerability Example.
From slideplayer.com
Authentication and Identification ppt download Clipboard Buffer Caching Vulnerability Example Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. How to prevent unintended data leakage? Leveraging clipboards can enable attackers to collect target information and exfiltrate useful data. This will be a very prevalent. Clipboard Buffer Caching Vulnerability Example.
From blog.gerwinhendriksen.com
The Oracle Database Buffer Cache should it be bigger… blog Clipboard Buffer Caching Vulnerability Example In most cases, attackers leverage malware that either steals data. What is unintended data leakage? How does unintended data leakage work? But this creates serious issue when some other application. Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto. Clipboard Buffer Caching Vulnerability Example.
From slideplayer.com
Prof John D. Kubiatowicz ppt download Clipboard Buffer Caching Vulnerability Example What is unintended data leakage? Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. But this creates serious issue when some other application. Are you vulnerable to unintended data leakage? Clipboard hijacking is an. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT Buffer Cache Waits PowerPoint Presentation, free download ID319874 Clipboard Buffer Caching Vulnerability Example Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. Are you vulnerable to unintended data leakage? Example of unintended data leakage. How to prevent unintended data leakage? Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT Buffer Cache PowerPoint Presentation, free download ID614424 Clipboard Buffer Caching Vulnerability Example Below is the list of example scenarios where unintended data leakage flaws. How to prevent unintended data leakage? What is the difference between insecure data storage and unintended data leakage? Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT The Buffer Cache PowerPoint Presentation, free download ID3713441 Clipboard Buffer Caching Vulnerability Example Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. What is the difference between insecure data storage and unintended data leakage? This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. But this creates serious issue. Clipboard Buffer Caching Vulnerability Example.
From eclecticlight.co
Explainer caching The Eclectic Light Company Clipboard Buffer Caching Vulnerability Example How does unintended data leakage work? Example of unintended data leakage. Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. But this creates serious issue when. Clipboard Buffer Caching Vulnerability Example.
From slideplayer.com
The Buffer Cache. ppt download Clipboard Buffer Caching Vulnerability Example Leveraging clipboards can enable attackers to collect target information and exfiltrate useful data. Are you vulnerable to unintended data leakage? How does unintended data leakage work? Below is the list of example scenarios where unintended data leakage flaws. How to prevent unintended data leakage? What is the difference between insecure data storage and unintended data leakage? Example scenarios for unintended. Clipboard Buffer Caching Vulnerability Example.
From slideplayer.com
CS162 Operating Systems and Systems Programming Lecture 19 File Systems Clipboard Buffer Caching Vulnerability Example How does unintended data leakage work? Below is the list of example scenarios where unintended data leakage flaws. Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. Leveraging clipboards can enable attackers to collect target information and exfiltrate useful data. But this creates serious issue when some other application. Example. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT Buffer Cache PowerPoint Presentation, free download ID614424 Clipboard Buffer Caching Vulnerability Example Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. Example scenarios for unintended data leakage. Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message.. Clipboard Buffer Caching Vulnerability Example.
From www.chegg.com
Solved ext Caching example install local cache Calculating Clipboard Buffer Caching Vulnerability Example What is the difference between insecure data storage and unintended data leakage? How does unintended data leakage work? Example of unintended data leakage. Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. But this creates serious issue when some other application. Example scenarios for unintended data leakage. Examples even exist. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT The Buffer Cache PowerPoint Presentation, free download ID3300623 Clipboard Buffer Caching Vulnerability Example This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. What is the difference between insecure data storage and unintended data leakage? What is unintended data leakage? Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied. Clipboard Buffer Caching Vulnerability Example.
From www.secrss.com
缓存失陷:缓存投毒拒绝服务攻击 安全内参 决策者的网络安全知识库 Clipboard Buffer Caching Vulnerability Example Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. This will be a very prevalent. Clipboard Buffer Caching Vulnerability Example.
From ops-class.org
File System Caching and Consistency Clipboard Buffer Caching Vulnerability Example What is unintended data leakage? This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. Are you vulnerable to unintended data leakage? But this creates serious issue when some other application. How does unintended data leakage work? Below is the list of example scenarios where unintended. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT Buffer Cache PowerPoint Presentation, free download ID6911487 Clipboard Buffer Caching Vulnerability Example Are you vulnerable to unintended data leakage? Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. Examples even exist of attackers hijacking and replacing the clipboard contents for malicious purposes, such as modifying a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat. Clipboard Buffer Caching Vulnerability Example.
From www.youtube.com
Buffer vs Cache Memory Key Differences and Parameters ARM YouTube Clipboard Buffer Caching Vulnerability Example How to prevent unintended data leakage? Clipboard hijacking is an illicit practice of taking data from the victims' clipboards and using it for malicious purposes. How does unintended data leakage work? In most cases, attackers leverage malware that either steals data. Example of unintended data leakage. This will be a very prevalent vulnerability for code produced by a developer that. Clipboard Buffer Caching Vulnerability Example.
From www.slideserve.com
PPT Exploiting GrayBox Knowledge of Buffer Cache Management Clipboard Buffer Caching Vulnerability Example This will be a very prevalent vulnerability for code produced by a developer that does not have intimate knowledge of how that information can. How does unintended data leakage work? Are you vulnerable to unintended data leakage? In most cases, attackers leverage malware that either steals data. Clipboard hijacking is an illicit practice of taking data from the victims' clipboards. Clipboard Buffer Caching Vulnerability Example.