Different Forms Of Authentication . August 15, 2024 | 15 min read Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. The five most common authentication methods companies use include the following: What are the different types of authentication? Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. There are lots of authentication methods out there, but they all generally fall under the following 5 types: If you work within the. Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively.
from ondato.com
Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. The five most common authentication methods companies use include the following: There are lots of authentication methods out there, but they all generally fall under the following 5 types: August 15, 2024 | 15 min read If you work within the. What are the different types of authentication? Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively.
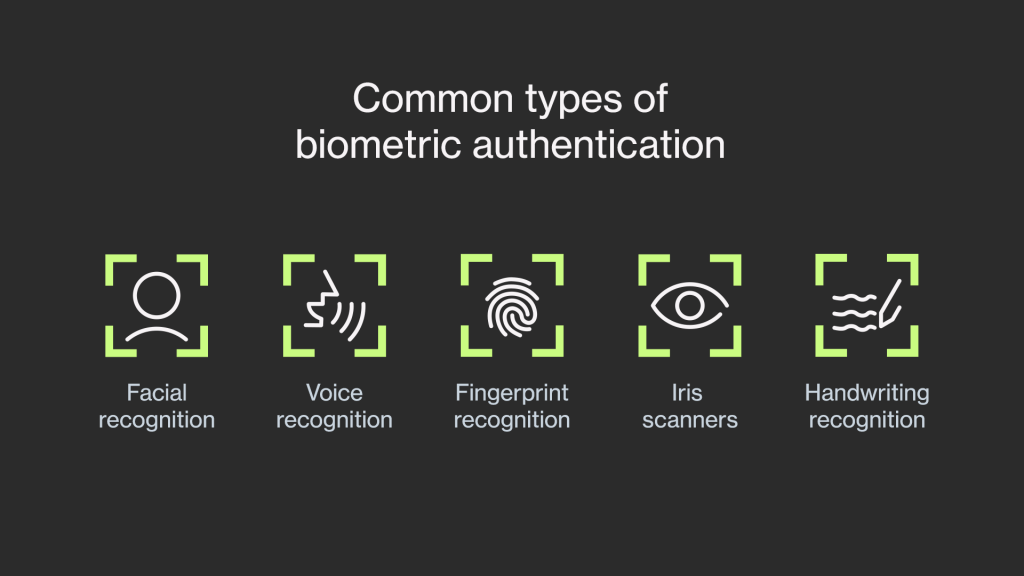
A Complete Guide to Biometric Authentication Methods Ondato Blog
Different Forms Of Authentication August 15, 2024 | 15 min read What are the different types of authentication? The five most common authentication methods companies use include the following: There are lots of authentication methods out there, but they all generally fall under the following 5 types: If you work within the. Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively. August 15, 2024 | 15 min read Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol.
From research.g2.com
The Ultimate Guide to Passwordless Authentication Different Forms Of Authentication Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. The five most common authentication methods companies use include the following: There are lots of authentication methods out there, but they all generally fall under the following 5 types: August 15, 2024 | 15 min read Understand the key authentication methods and protocols that protect your systems, from mfa. Different Forms Of Authentication.
From www.miniorange.com
What is Authentication? Different Types of Authentication Different Forms Of Authentication Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. The five most common authentication methods companies use include the following: Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. If you work within the. Understand the key authentication methods and protocols that protect your systems, from mfa to saml,. Different Forms Of Authentication.
From www.getapp.com
5 Types of Authentication To Secure Your Small Business Different Forms Of Authentication August 15, 2024 | 15 min read If you work within the. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. There are lots of authentication methods out there, but they all generally fall under the following 5 types: Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement. Different Forms Of Authentication.
From www.researchgate.net
A Summary of Three Major Types of Authentication Methods Download Table Different Forms Of Authentication Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively. There are lots of authentication methods out there, but they all generally fall under the following 5 types: August 15, 2024 | 15 min read If you work within the. Authentication methods, including challenge handshake authentication protocol (chap), extensible. Different Forms Of Authentication.
From rublon.com
Types of Authentication The Definitive Guide Rublon Different Forms Of Authentication Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively. There are lots of authentication methods out there, but they all generally fall under the following 5 types: Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. If you work. Different Forms Of Authentication.
From tavish.fun
what is the Different Types of Authentication Cyber Security Different Forms Of Authentication Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. August 15, 2024 | 15 min read The five most common authentication methods companies use include the following: Understand the key authentication methods and protocols that protect your systems, from mfa. Different Forms Of Authentication.
From optimalidm.com
3 Types of Authentication Methods Optimal IdM Different Forms Of Authentication August 15, 2024 | 15 min read If you work within the. There are lots of authentication methods out there, but they all generally fall under the following 5 types: What are the different types of authentication? Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. The five most common authentication. Different Forms Of Authentication.
From learn.microsoft.com
An Overview of Forms Authentication (VB) Microsoft Learn Different Forms Of Authentication Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. If you work within the. The five most common authentication methods companies use include the following: Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. There are lots of authentication methods out there, but they all generally fall under the. Different Forms Of Authentication.
From www.secureauth.com
The Different Types of Authentication 4 Examples of MultiFactor Different Forms Of Authentication Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. The five most common authentication methods companies use include the following: There are lots of authentication methods out there, but they all generally fall under the following 5 types: Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. What are. Different Forms Of Authentication.
From www.researchgate.net
Different types of authentication attacks with their corresponding Different Forms Of Authentication Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. What are the different types of authentication? There are lots of authentication methods out there, but they all generally fall under the following 5 types: Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. August 15, 2024 | 15 min. Different Forms Of Authentication.
From www.slideserve.com
PPT Chapter 10 Authentication PowerPoint Presentation, free download Different Forms Of Authentication If you work within the. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. What are the different types of authentication? August 15, 2024 | 15 min read There are lots of authentication methods out there, but they all generally fall under the following 5 types: The five most common authentication methods companies use include the following: Compare. Different Forms Of Authentication.
From optimalidm.com
3 Types of Authentication Methods Optimal IdM Different Forms Of Authentication Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. There are lots of authentication methods out there, but they all generally fall under the following 5 types: If you work within the. Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Understand the key authentication methods and protocols that. Different Forms Of Authentication.
From www.cryptomathic.com
Digital authentication factors, mechanisms and schemes Different Forms Of Authentication August 15, 2024 | 15 min read What are the different types of authentication? The five most common authentication methods companies use include the following: Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. There are lots of authentication methods. Different Forms Of Authentication.
From www.slideserve.com
PPT Authentication Applications PowerPoint Presentation, free Different Forms Of Authentication If you work within the. There are lots of authentication methods out there, but they all generally fall under the following 5 types: The five most common authentication methods companies use include the following: What are the different types of authentication? Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement. Different Forms Of Authentication.
From www.educba.com
Authentication Types Functions & Guide to Types of Authentication Different Forms Of Authentication Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. There are lots of authentication methods out there, but they all generally fall under the following 5 types: The five most common authentication methods companies use include the following: If you work within the. Understand the key authentication methods and protocols that protect your systems, from mfa to saml,. Different Forms Of Authentication.
From www.infosectrain.com
Authentication Vs. Authorization Different Forms Of Authentication There are lots of authentication methods out there, but they all generally fall under the following 5 types: Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively. August 15, 2024 | 15 min read What are the different types of authentication? If you work within the. Authentication methods,. Different Forms Of Authentication.
From www.youtube.com
Types of Authentication YouTube Different Forms Of Authentication August 15, 2024 | 15 min read Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively. If you work within the. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. Compare six user authentication types that help companies secure networks, as well protocols designed to secure. Different Forms Of Authentication.
From www.miniorange.com
What is Authentication? Different Types of Authentication Different Forms Of Authentication If you work within the. What are the different types of authentication? The five most common authentication methods companies use include the following: August 15, 2024 | 15 min read Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Understand the key authentication methods and protocols that protect your systems, from. Different Forms Of Authentication.
From cybersecurityreviews.net
How effective are traditional authentication methods? Cyber Security Different Forms Of Authentication Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively. If you work within the. The five most common authentication methods companies use include the following: There are lots of authentication methods out there, but they all generally fall under the following 5 types: Compare six user authentication types. Different Forms Of Authentication.
From www.embedded.com
How to properly authenticate IoT device identity Different Forms Of Authentication If you work within the. The five most common authentication methods companies use include the following: What are the different types of authentication? Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. There are lots of authentication methods out there,. Different Forms Of Authentication.
From www.slideserve.com
PPT MVC Advanced Topics PowerPoint Presentation, free Different Forms Of Authentication The five most common authentication methods companies use include the following: If you work within the. August 15, 2024 | 15 min read Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. Understand the key authentication methods and protocols that. Different Forms Of Authentication.
From www.strongdm.com
Authentication Definition, Types, Uses & More StrongDM Different Forms Of Authentication The five most common authentication methods companies use include the following: Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. There are lots of authentication methods out there, but they all generally fall under the following 5 types: What are. Different Forms Of Authentication.
From www.freepik.com
Premium Vector Infographic authentication template icons in different Different Forms Of Authentication The five most common authentication methods companies use include the following: Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. If you work within the. There are lots of authentication methods out there, but they all generally fall under the following 5 types: What are the different types of authentication? Compare six user authentication types that help companies. Different Forms Of Authentication.
From www.slideserve.com
PPT The Authenticity Factor™ PowerPoint Presentation, free download Different Forms Of Authentication Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. August 15, 2024 | 15 min read Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. There are lots. Different Forms Of Authentication.
From blogs.truststamp.ai
MultiFactor Authentication (MFA) Explained Different Forms Of Authentication The five most common authentication methods companies use include the following: If you work within the. What are the different types of authentication? August 15, 2024 | 15 min read There are lots of authentication methods out there, but they all generally fall under the following 5 types: Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. Understand. Different Forms Of Authentication.
From www.spiceworks.com
What Is MultiFactor Authentication? Definition, Key Components, and Different Forms Of Authentication If you work within the. Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. The five most common authentication methods companies use include the following: August 15, 2024 | 15 min read Understand the key authentication methods and protocols that. Different Forms Of Authentication.
From rublon.com
What Are the Three Authentication Factors? Rublon Different Forms Of Authentication There are lots of authentication methods out there, but they all generally fall under the following 5 types: Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. If you work within the. August 15, 2024 | 15 min read The five most common authentication methods companies use include the following: Understand the key authentication methods and protocols that. Different Forms Of Authentication.
From www.klippa.com
What is 2FA (Twofactor authentication)? Klippa Different Forms Of Authentication There are lots of authentication methods out there, but they all generally fall under the following 5 types: Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. The five most common authentication methods companies use include the following: Understand the. Different Forms Of Authentication.
From www.spiceworks.com
Authentication Meaning, Types, and Tools Spiceworks Spiceworks Different Forms Of Authentication Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. The five most common authentication methods companies use include the following: August 15, 2024 | 15 min read Compare six user authentication types that help companies secure networks,. Different Forms Of Authentication.
From www.coursehero.com
[Solved] . 13. Identify five different types of authentication Different Forms Of Authentication Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively. The five most common authentication methods companies use include the following: What are the different types of authentication? August 15, 2024 | 15 min read If you work within the. There are lots of authentication methods out there, but. Different Forms Of Authentication.
From blog.vcloudtech.com
Authentication in Network Security vCloud Tech Different Forms Of Authentication Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. What are the different types of authentication? Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively. August 15, 2024 | 15 min read If you work within the. The five. Different Forms Of Authentication.
From ondato.com
A Complete Guide to Biometric Authentication Methods Ondato Blog Different Forms Of Authentication There are lots of authentication methods out there, but they all generally fall under the following 5 types: If you work within the. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Understand the key authentication methods and protocols that. Different Forms Of Authentication.
From www.iproov.com
What's the Best Authentication Method? Analysis [2024] Different Forms Of Authentication What are the different types of authentication? Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively. The five most. Different Forms Of Authentication.
From youverify.co
What are The Types of Authentication? Youverify Different Forms Of Authentication What are the different types of authentication? Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how to implement them effectively. The five most common authentication methods companies use include the following: Authentication methods, including challenge handshake authentication protocol (chap), extensible authentication protocol. There are lots of authentication methods out there, but they. Different Forms Of Authentication.
From research.g2.com
The Ultimate Guide to Passwordless Authentication Different Forms Of Authentication There are lots of authentication methods out there, but they all generally fall under the following 5 types: August 15, 2024 | 15 min read Compare six user authentication types that help companies secure networks, as well protocols designed to secure the transfer. Understand the key authentication methods and protocols that protect your systems, from mfa to saml, and how. Different Forms Of Authentication.