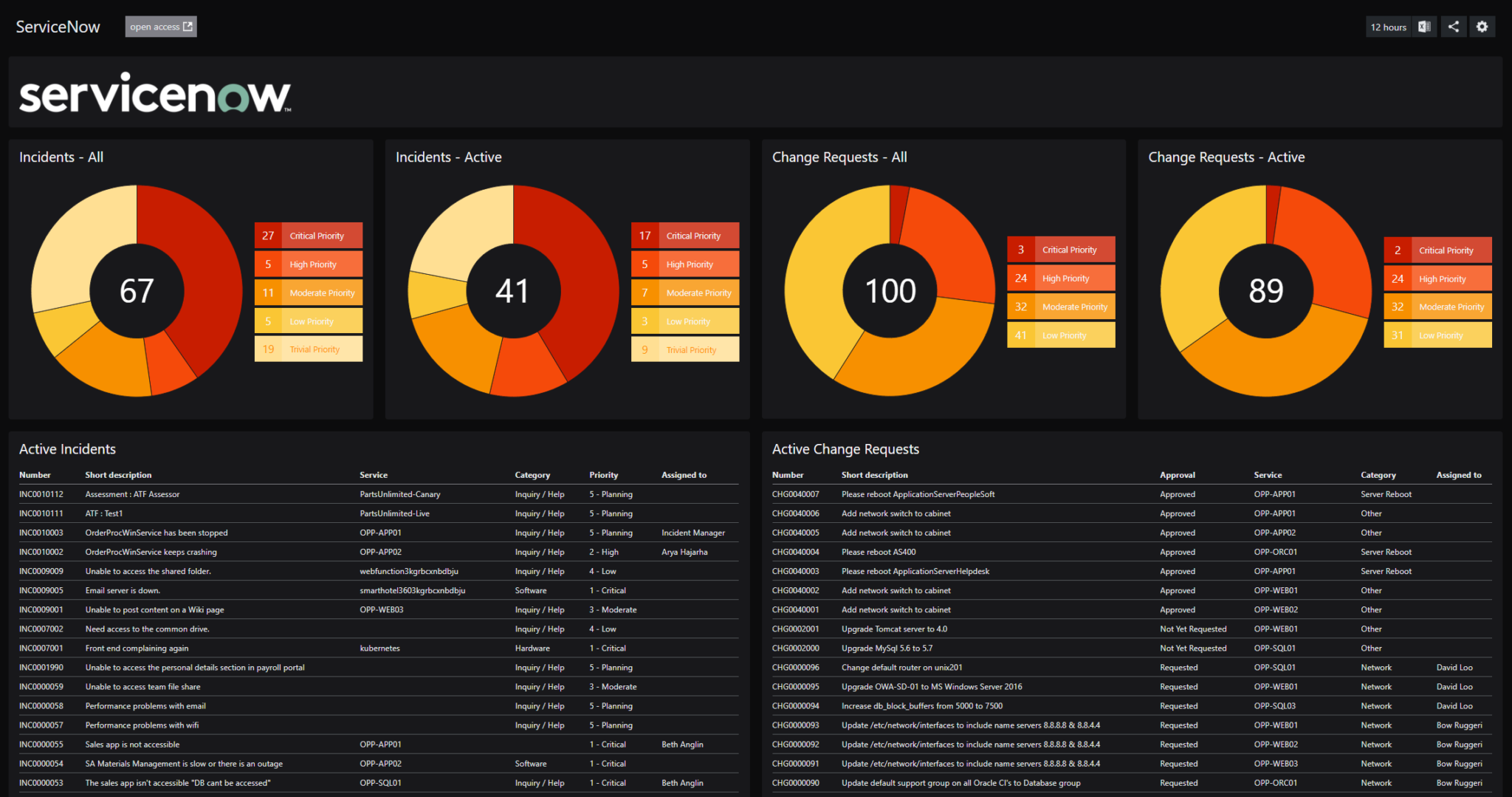
Security Scan Request Servicenow . Servicenow healthscan helps you understand and improve the health of your servicenow instance. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat.
from squaredup.com
Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Servicenow healthscan helps you understand and improve the health of your servicenow instance. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat.
ServiceNow SquaredUp
Security Scan Request Servicenow The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. Servicenow healthscan helps you understand and improve the health of your servicenow instance. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that.
From github.com
Feature request Run associated Guardium assessment scan from Security Scan Request Servicenow To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Logs are a valuable source. Security Scan Request Servicenow.
From edgile.com
ServiceNow Security Operations (SecOps) Edgile Security Scan Request Servicenow Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. The process starts. Security Scan Request Servicenow.
From kanini.com
How to Leverage the ServiceNow Vulnerability Response Application Security Scan Request Servicenow To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. This is to ensure are. Security Scan Request Servicenow.
From documentation.sailpoint.com
Configuring ServiceNow for a Service Request Security Scan Request Servicenow To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Servicenow healthscan helps you understand. Security Scan Request Servicenow.
From davidmac.pro
How to use a custom ServiceNow login page, and why you should Security Scan Request Servicenow To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. The process starts. Security Scan Request Servicenow.
From www.avancercorp.com
SailPoint ServiceNow Integration Avancer Coporation Security Scan Request Servicenow This is to ensure are we compliant with all security checks established by our information security team, aligned with our. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Servicenow healthscan helps you understand. Security Scan Request Servicenow.
From www.youtube.com
ServiceNow Quebec Instance Scan Instance Scan in Quebec ServiceNow Security Scan Request Servicenow Servicenow healthscan helps you understand and improve the health of your servicenow instance. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. To speed up response, security incident response automates many. Security Scan Request Servicenow.
From www.recastsoftware.com
How to Request a ServiceNow Developer Instance to Integrate with SCCM Security Scan Request Servicenow This is to ensure are we compliant with all security checks established by our information security team, aligned with our. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. Servicenow healthscan helps you understand and improve the health of your servicenow instance. The process starts with setting policies to define secure configurations. Security Scan Request Servicenow.
From www.aspiresys.com
Cloud Integration with OnPremise Ecosystem using ServiceNow Security Scan Request Servicenow This is to ensure are we compliant with all security checks established by our information security team, aligned with our. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. Logs are a valuable source. Security Scan Request Servicenow.
From www.vrogue.co
What Is Servicenow Itil Complete Overview Of Servicen vrogue.co Security Scan Request Servicenow To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Logs are a valuable source. Security Scan Request Servicenow.
From success.myshn.net
Create an OnDemand Scan for ServiceNow Skyhigh Security Security Scan Request Servicenow Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. Servicenow healthscan helps. Security Scan Request Servicenow.
From www.youtube.com
ServiceNow Incident Management (Part One) YouTube Security Scan Request Servicenow Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. Servicenow healthscan helps. Security Scan Request Servicenow.
From www.paloaltonetworks.ca
Prisma Cloud Secures Containers with ServiceNow Vulnerability Response Security Scan Request Servicenow This is to ensure are we compliant with all security checks established by our information security team, aligned with our. Servicenow healthscan helps you understand and improve the health of your servicenow instance. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. To speed up response, security incident response. Security Scan Request Servicenow.
From squaredup.com
ServiceNow SquaredUp Security Scan Request Servicenow To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Logs are a valuable source. Security Scan Request Servicenow.
From infocenter.io
How ServiceNow ITSM Makes CIOs’ Jobs Easier Infocenter Security Scan Request Servicenow The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. Servicenow healthscan. Security Scan Request Servicenow.
From orca.security
ServiceNow and Orca Security Cloud Security Solutions Security Scan Request Servicenow The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Servicenow healthscan helps you understand and improve the health of your servicenow instance. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. Logs are a valuable source of security information that. Security Scan Request Servicenow.
From www.youtube.com
ServiceNow integration with Barcode Scanner YouTube Security Scan Request Servicenow Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. To speed. Security Scan Request Servicenow.
From scan.netsecurity.ne.jp
ITSMを実現するクラウドサービス「ServiceNow」の提供を開始(日立ソリューションズ) 1枚目の写真・画像 Security Scan Request Servicenow This is to ensure are we compliant with all security checks established by our information security team, aligned with our. Servicenow healthscan helps you understand and improve the health of your servicenow instance. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. The process starts with setting policies to define secure configurations. Security Scan Request Servicenow.
From www.youtube.com
Create Incident Demo Automated Testing for ServiceNow YouTube Security Scan Request Servicenow Servicenow healthscan helps you understand and improve the health of your servicenow instance. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. The process starts with setting policies to define secure configurations. Security Scan Request Servicenow.
From blog.vsoftconsulting.com
Understanding Multifactor Authentication In ServiceNow Madrid Release Security Scan Request Servicenow The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. Servicenow healthscan helps you understand and improve the health of your servicenow instance. To speed up response, security incident response automates many. Security Scan Request Servicenow.
From www.soft-boys.com
Servicenow Run Point Scan Security Scan Request Servicenow Servicenow healthscan helps you understand and improve the health of your servicenow instance. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. The process starts with setting policies to define secure configurations. Security Scan Request Servicenow.
From www.channelpronetwork.com
ServiceNow Automates Security Incident Response with new CloudBased Security Scan Request Servicenow The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Servicenow healthscan helps you understand and improve the health of your servicenow instance. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. To speed up response, security incident response automates many. Security Scan Request Servicenow.
From hkrtrainings.com
Servicenow Workflow Workflow Creation in Servicenow Security Scan Request Servicenow This is to ensure are we compliant with all security checks established by our information security team, aligned with our. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. Servicenow healthscan helps you understand. Security Scan Request Servicenow.
From www.youtube.com
Unlock The Power of ServiceNow How Instance Scan Can Help to optimize Security Scan Request Servicenow The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. Logs are a valuable source. Security Scan Request Servicenow.
From success.myshn.net
Create an OnDemand Scan for ServiceNow Skyhigh Security Security Scan Request Servicenow The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. Servicenow healthscan helps you understand and improve the health of your servicenow instance. To speed up response, security incident response automates many. Security Scan Request Servicenow.
From www.youtube.com
Instance Scan in ServiceNow Quebec YouTube Security Scan Request Servicenow Servicenow healthscan helps you understand and improve the health of your servicenow instance. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. This is to ensure are we compliant with all security checks established. Security Scan Request Servicenow.
From www.youtube.com
ServiceNow Quebec Feature Instance Scan and Scan Check YouTube Security Scan Request Servicenow The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. Logs are a valuable source. Security Scan Request Servicenow.
From www.servicenowelite.com
Security Operations — ServiceNow Elite Security Scan Request Servicenow The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Servicenow healthscan helps you understand and improve the health of your servicenow instance. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. To speed up response, security incident response automates many. Security Scan Request Servicenow.
From template.unfs.edu.pe
Servicenow Incident Templates Security Scan Request Servicenow Servicenow healthscan helps you understand and improve the health of your servicenow instance. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Logs are a valuable source of security information that. Security Scan Request Servicenow.
From www.twilio.com
Create a Notification System in ServiceNow using Twilio SMS and Voice Security Scan Request Servicenow Servicenow healthscan helps you understand and improve the health of your servicenow instance. This is to ensure are we compliant with all security checks established by our information security team, aligned with our. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. To speed up response, security incident response. Security Scan Request Servicenow.
From docs.sciencelogic.com
Introduction to the ServiceNow Service Graph Connector SyncPack Security Scan Request Servicenow This is to ensure are we compliant with all security checks established by our information security team, aligned with our. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. Servicenow healthscan helps you understand and improve the health of your servicenow instance. Logs are a valuable source of security information that help. Security Scan Request Servicenow.
From plat4mation.com
Top 10 Best New Features From The ServiceNow Quebec Release Security Scan Request Servicenow Servicenow healthscan helps you understand and improve the health of your servicenow instance. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. This is to ensure are we compliant with all security checks established. Security Scan Request Servicenow.
From help.kennasecurity.com
ServiceNow Ticketing Integration Kenna FAQ Security Scan Request Servicenow Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. Servicenow healthscan helps you understand and improve the health of your servicenow instance. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. This is to ensure are we compliant with all. Security Scan Request Servicenow.
From www.servicenow.com
Instance Security Center Enterprise IT Security ServiceNow Security Scan Request Servicenow Servicenow healthscan helps you understand and improve the health of your servicenow instance. To speed up response, security incident response automates many tasks, including approval requests, malware scans, and threat. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. This is to ensure are we compliant with all security. Security Scan Request Servicenow.
From success.myshn.net
Create an OnDemand Scan for ServiceNow Skyhigh Security Security Scan Request Servicenow This is to ensure are we compliant with all security checks established by our information security team, aligned with our. The process starts with setting policies to define secure configurations (for example, minimum password length requirements), and integrating. Logs are a valuable source of security information that help highlight suspicious or malicious activity, so it is essential that. Servicenow healthscan. Security Scan Request Servicenow.