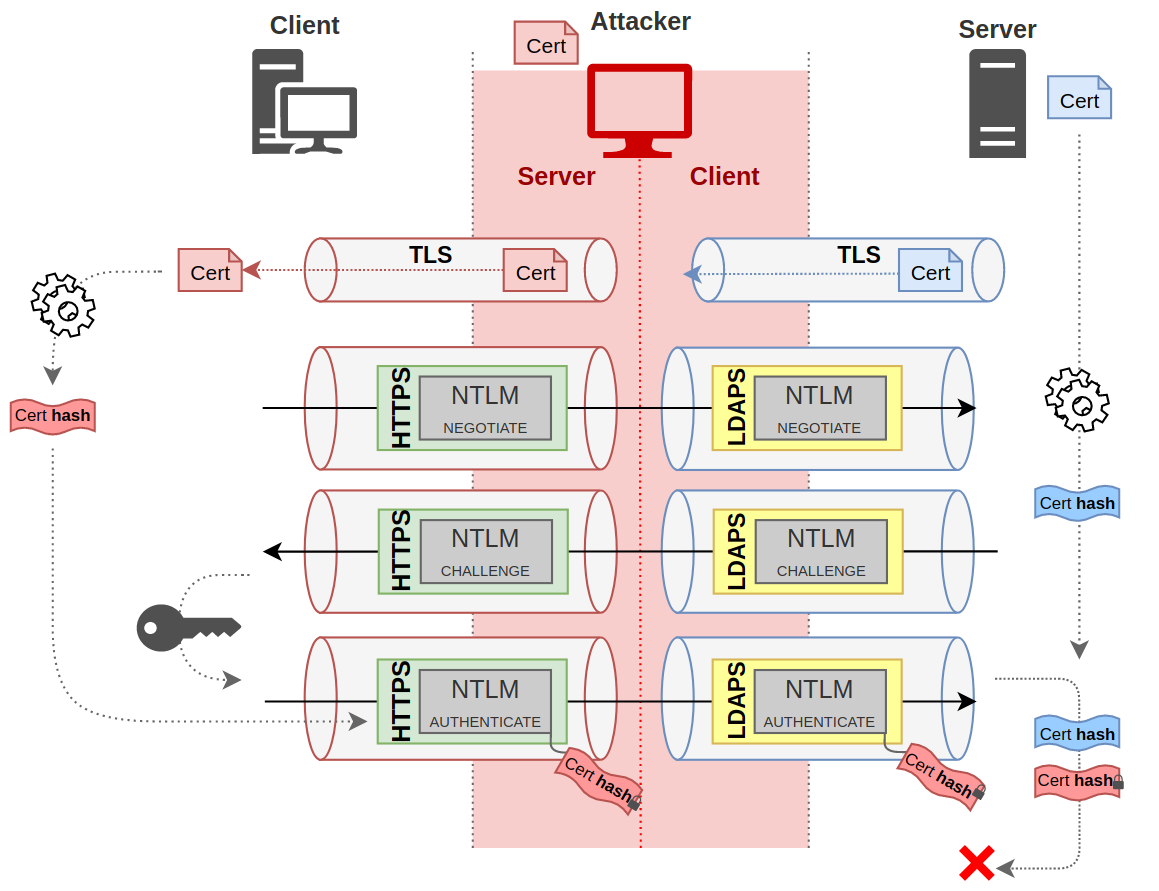
What Is An Ntlm Relay Attack . In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. An attacker intercepts legitimate authentication requests and then forwards them to. Microsoft is aware of petitpotam which can potentially be used to attack windows domain controllers or other windows servers. Exploiting this vulnerability involves coercing. A relay attack is the act of intercepting information passing over a network and relaying it. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. Petitpotam is a classic ntlm relay attack, and such.
from en.hackndo.com
Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. An attacker intercepts legitimate authentication requests and then forwards them to. A relay attack is the act of intercepting information passing over a network and relaying it. Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. Petitpotam is a classic ntlm relay attack, and such. Microsoft is aware of petitpotam which can potentially be used to attack windows domain controllers or other windows servers. Exploiting this vulnerability involves coercing.
NTLM Relay hackndo
What Is An Ntlm Relay Attack A relay attack is the act of intercepting information passing over a network and relaying it. Microsoft is aware of petitpotam which can potentially be used to attack windows domain controllers or other windows servers. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. An attacker intercepts legitimate authentication requests and then forwards them to. A relay attack is the act of intercepting information passing over a network and relaying it. Exploiting this vulnerability involves coercing. In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Petitpotam is a classic ntlm relay attack, and such. Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks.
From en.hackndo.com
NTLM Relay hackndo What Is An Ntlm Relay Attack A relay attack is the act of intercepting information passing over a network and relaying it. An attacker intercepts legitimate authentication requests and then forwards them to. Microsoft is aware of petitpotam which can potentially be used to attack windows domain controllers or other windows servers. Exploiting this vulnerability involves coercing. In an ntlm relay attack, the attacker sets up. What Is An Ntlm Relay Attack.
From medium.com
NTLM Relay Attack. NetBIOS Basic Input / Output… by Orhan What Is An Ntlm Relay Attack Exploiting this vulnerability involves coercing. Microsoft is aware of petitpotam which can potentially be used to attack windows domain controllers or other windows servers. Petitpotam is a classic ntlm relay attack, and such. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. In an ntlm relay attack, the attacker sets up a computer they. What Is An Ntlm Relay Attack.
From gbhackers.com
Microsoft NTLM Vulnerability Let Hackers to Compromise DC What Is An Ntlm Relay Attack Petitpotam is a classic ntlm relay attack, and such. A relay attack is the act of intercepting information passing over a network and relaying it. In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Petitpotam is a security flaw. What Is An Ntlm Relay Attack.
From www.redlings.com
NTLM Authentication Definition, Protocol & Vulnerabilities >>Redlings What Is An Ntlm Relay Attack A relay attack is the act of intercepting information passing over a network and relaying it. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. Exploiting this vulnerability involves coercing. An attacker intercepts legitimate authentication requests and then forwards them to. Petitpotam is a classic ntlm relay attack, and such. In an ntlm relay. What Is An Ntlm Relay Attack.
From www.thecybersecuritytimes.com
Critical Microsoft vulnerability threatens NTLM Relay Attack PetitPotam What Is An Ntlm Relay Attack A relay attack is the act of intercepting information passing over a network and relaying it. Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. Exploiting this vulnerability involves coercing. Petitpotam is a classic ntlm relay attack, and such. In an ntlm relay attack, the attacker sets up. What Is An Ntlm Relay Attack.
From redcursor.com.au
Capturing & Relaying NTLM Authentication Testing Sydney What Is An Ntlm Relay Attack Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. An attacker intercepts legitimate authentication requests and then forwards them to. Relay attacks can come. What Is An Ntlm Relay Attack.
From www.reconbee.com
New NTLM Relay Attack Lets Attackers Take Control Over Windows Domain What Is An Ntlm Relay Attack In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. Relay attacks can come in many forms, but the bottom line is that they can. What Is An Ntlm Relay Attack.
From www.semperis.com
How to Defend Against an NTLM Relay Attack AD Security 101 What Is An Ntlm Relay Attack Microsoft is aware of petitpotam which can potentially be used to attack windows domain controllers or other windows servers. Petitpotam is a classic ntlm relay attack, and such. Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. An attacker intercepts legitimate authentication requests and then forwards them to.. What Is An Ntlm Relay Attack.
From www.slideserve.com
PPT NTLM Relay Attacks PowerPoint Presentation, free download ID What Is An Ntlm Relay Attack Exploiting this vulnerability involves coercing. A relay attack is the act of intercepting information passing over a network and relaying it. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. Petitpotam is a classic ntlm relay attack, and such. Relay attacks can come in many forms, but the bottom line is that they can. What Is An Ntlm Relay Attack.
From en.hackndo.com
NTLM Relay hackndo What Is An Ntlm Relay Attack In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. Exploiting this vulnerability involves coercing. Microsoft is aware of petitpotam which can potentially be used. What Is An Ntlm Relay Attack.
From www.sans.org
SANS Testing SMB Relay Demystified and NTLMv2 Pwnage with What Is An Ntlm Relay Attack Exploiting this vulnerability involves coercing. A relay attack is the act of intercepting information passing over a network and relaying it. Microsoft is aware of petitpotam which can potentially be used to attack windows domain controllers or other windows servers. Petitpotam is a classic ntlm relay attack, and such. Relay attacks can come in many forms, but the bottom line. What Is An Ntlm Relay Attack.
From manesec.blogspot.com
DFSCoerce NTLM Relay Attack to Domain Admin What Is An Ntlm Relay Attack Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. An attacker intercepts legitimate authentication requests and then forwards them to. Microsoft is aware of petitpotam which can potentially be used to attack windows domain controllers or other windows servers. Exploiting this vulnerability involves coercing. Petitpotam is a classic ntlm relay attack, and such. In. What Is An Ntlm Relay Attack.
From www.fortalicesolutions.com
Keeping Up with the NTLM Relay What Is An Ntlm Relay Attack Petitpotam is a classic ntlm relay attack, and such. A relay attack is the act of intercepting information passing over a network and relaying it. Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. In an ntlm relay attack, the attacker sets up a computer they control that’s. What Is An Ntlm Relay Attack.
From academy.hackthebox.com
NTLM Relay Attacks Course HTB Academy What Is An Ntlm Relay Attack Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. Microsoft is aware of petitpotam which can potentially be used to attack windows domain controllers or other windows servers. A relay attack is the act of intercepting information passing over a network and relaying it. Petitpotam is a classic ntlm relay attack, and such. Relay. What Is An Ntlm Relay Attack.
From en.hackndo.com
NTLM Relay hackndo What Is An Ntlm Relay Attack A relay attack is the act of intercepting information passing over a network and relaying it. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. Microsoft is aware of petitpotam which can potentially be used to attack windows domain controllers or other windows servers. In an ntlm relay attack, the attacker sets up a. What Is An Ntlm Relay Attack.
From www.vaadata.com
Understanding NTLM Authentication and NTLM Relay Attacks What Is An Ntlm Relay Attack Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. Exploiting this vulnerability involves coercing. A relay attack is the act of intercepting information passing over a network and relaying it. Petitpotam is a classic ntlm relay attack, and such. Microsoft is aware of petitpotam which can potentially be used to attack windows domain controllers. What Is An Ntlm Relay Attack.
From www.youtube.com
DFSCoerce NTLM Relay Attack Threat SnapShot YouTube What Is An Ntlm Relay Attack In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Petitpotam is a classic ntlm relay attack, and such. Exploiting this vulnerability involves coercing. A relay attack is the act of intercepting information passing over a network and relaying it.. What Is An Ntlm Relay Attack.
From en.hackndo.com
NTLM Relay hackndo What Is An Ntlm Relay Attack An attacker intercepts legitimate authentication requests and then forwards them to. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Exploiting this vulnerability involves. What Is An Ntlm Relay Attack.
From www.extrahop.com
PetitPotam Expanding NTLM Relay Attacks ExtraHop What Is An Ntlm Relay Attack Exploiting this vulnerability involves coercing. In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. A relay attack is the act of intercepting information passing over a network and relaying it. An attacker intercepts legitimate authentication requests and then forwards. What Is An Ntlm Relay Attack.
From teckpath.com
NTLM Relay Attacks Explained For Businesses Stay Protected What Is An Ntlm Relay Attack In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. A relay attack is the act of intercepting information passing over a network and relaying it. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss. What Is An Ntlm Relay Attack.
From securityboulevard.com
The Elephant In the Room NTLM Coercion and Understanding Its Impact What Is An Ntlm Relay Attack Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. A relay attack is the act of intercepting information passing over a network and relaying it. Petitpotam is a classic ntlm relay attack, and such. In an ntlm relay attack, the attacker sets up a computer they control that’s. What Is An Ntlm Relay Attack.
From blog.csdn.net
NTLMrelay攻击的原理与实现_ntlmssp攻击CSDN博客 What Is An Ntlm Relay Attack An attacker intercepts legitimate authentication requests and then forwards them to. Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. Exploiting this vulnerability involves coercing. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. Petitpotam is a classic ntlm relay attack, and. What Is An Ntlm Relay Attack.
From www.vaadata.com
Understanding NTLM Authentication and NTLM Relay Attacks What Is An Ntlm Relay Attack Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Petitpotam is a classic ntlm relay attack, and such.. What Is An Ntlm Relay Attack.
From medium.com
NTLM Relay Attack. NetBIOS Basic Input / Output… by Orhan What Is An Ntlm Relay Attack Petitpotam is a classic ntlm relay attack, and such. Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. A relay attack is the act of intercepting information passing over a network and relaying it. Microsoft is aware of petitpotam which can potentially be used to attack windows domain. What Is An Ntlm Relay Attack.
From blog.compass-security.com
Relaying NTLM to MSSQL Compass Security Blog What Is An Ntlm Relay Attack Petitpotam is a classic ntlm relay attack, and such. A relay attack is the act of intercepting information passing over a network and relaying it. Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. Microsoft is aware of petitpotam which can potentially be used to attack windows domain. What Is An Ntlm Relay Attack.
From academy.hackthebox.com
NTLM Relay Attacks Course HTB Academy What Is An Ntlm Relay Attack A relay attack is the act of intercepting information passing over a network and relaying it. In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss. What Is An Ntlm Relay Attack.
From www.lansweeper.com
PetitPotam NTLM Relay Attack Allows Domain Takeover Lansweeper What Is An Ntlm Relay Attack Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. An attacker intercepts legitimate authentication requests and then forwards them to. Exploiting this vulnerability involves coercing. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. A relay attack is the act of intercepting. What Is An Ntlm Relay Attack.
From en.hackndo.com
NTLM Relay hackndo What Is An Ntlm Relay Attack An attacker intercepts legitimate authentication requests and then forwards them to. Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. Petitpotam is a classic ntlm relay attack, and such. A relay attack is the act of intercepting information passing over a network and relaying it. In an ntlm. What Is An Ntlm Relay Attack.
From www.slideserve.com
PPT NTLM Relay Attacks PowerPoint Presentation, free download ID What Is An Ntlm Relay Attack Petitpotam is a classic ntlm relay attack, and such. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. An attacker intercepts legitimate authentication requests and then forwards them to. Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. Exploiting this vulnerability involves. What Is An Ntlm Relay Attack.
From www.vaadata.com
Understanding NTLM Authentication and NTLM Relay Attacks What Is An Ntlm Relay Attack In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Exploiting this vulnerability involves coercing. Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. Microsoft is aware of petitpotam which can potentially be used. What Is An Ntlm Relay Attack.
From www.extrahop.com
PetitPotam Expanding NTLM Relay Attacks ExtraHop What Is An Ntlm Relay Attack In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. A relay attack is the act of intercepting information. What Is An Ntlm Relay Attack.
From www.slideserve.com
PPT NTLM Relay Attacks PowerPoint Presentation, free download ID What Is An Ntlm Relay Attack Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Exploiting this vulnerability involves coercing. A relay attack is. What Is An Ntlm Relay Attack.
From www.fortalicesolutions.com
Keeping Up with the NTLM Relay What Is An Ntlm Relay Attack Relay attacks can come in many forms, but the bottom line is that they can effectively subvert authentication on internal networks. Petitpotam is a classic ntlm relay attack, and such. Microsoft is aware of petitpotam which can potentially be used to attack windows domain controllers or other windows servers. A relay attack is the act of intercepting information passing over. What Is An Ntlm Relay Attack.
From cyberint.com
PetitPotam NTLM Relay Attack What Is An Ntlm Relay Attack Exploiting this vulnerability involves coercing. Petitpotam is a classic ntlm relay attack, and such. In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Relay attacks can come in many forms, but the bottom line is that they can effectively. What Is An Ntlm Relay Attack.
From www.sternsecurity.com
Local Network Attacks LLMNR and NBTNS Poisoning Stern Security What Is An Ntlm Relay Attack Petitpotam is a security flaw that impacts windows systems leveraging the microsoft windows rpcss service. In an ntlm relay attack, the attacker sets up a computer they control that’s running an smb server, and attempts to place the machine they control in the middle of. Exploiting this vulnerability involves coercing. Petitpotam is a classic ntlm relay attack, and such. Microsoft. What Is An Ntlm Relay Attack.