Trusted Systems In Information Security . Trusted systems rely on encryption. It’s crucial for organizations and. Safety is ensured by trusted. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. Trusted systems are special systems designed to serve the purpose of providing security. Trustworthy systems should prioritize data privacy and security as a top priority. The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access.
from www.brainkart.com
A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Trusted systems are special systems designed to serve the purpose of providing security. The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. Trusted systems rely on encryption. Safety is ensured by trusted. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. Trustworthy systems should prioritize data privacy and security as a top priority. It’s crucial for organizations and. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access.
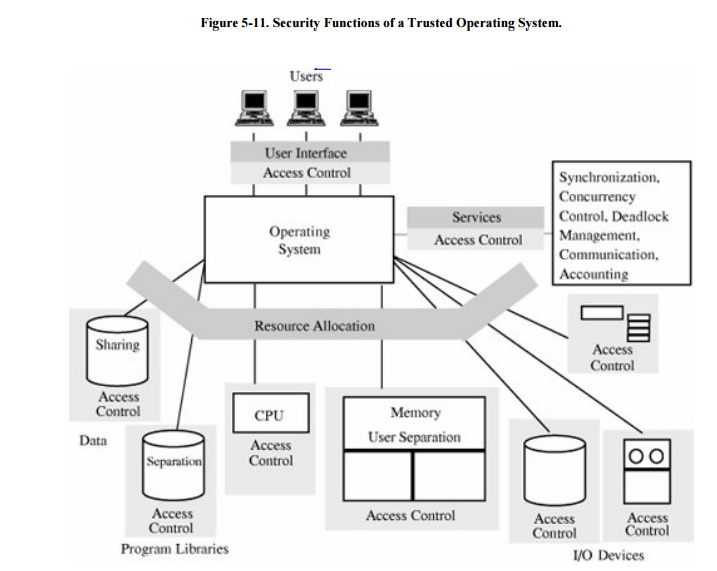
Security Features of Trusted Operating Systems
Trusted Systems In Information Security Trusted systems rely on encryption. Trustworthy systems should prioritize data privacy and security as a top priority. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. It’s crucial for organizations and. Trusted systems rely on encryption. Safety is ensured by trusted. Trusted systems are special systems designed to serve the purpose of providing security.
From cloudsecurityrisk.blogspot.com
Cloud, Security and Risk Management TPM (Trusted Platform Module) Trusted Systems In Information Security Trusted systems are special systems designed to serve the purpose of providing security. Trusted systems rely on encryption. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Safety is ensured by trusted. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. A. Trusted Systems In Information Security.
From trustedsys.com
IPS Security Containers Trusted Systems SCIFinaBox Solutions Trusted Systems In Information Security Safety is ensured by trusted. Trusted systems are special systems designed to serve the purpose of providing security. The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Provides a renewed focus on. Trusted Systems In Information Security.
From www.slideserve.com
PPT Trusted System? PowerPoint Presentation, free download ID6963895 Trusted Systems In Information Security Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Safety is ensured by trusted. In simple terms, a trusted system is a secure system that is specifically designed to resist any. Trusted Systems In Information Security.
From wentzwu.com
Trusted Path and Trusted Channel by Wentz Wu, ISSAP, ISSEP, ISSMP CISSP Trusted Systems In Information Security In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Trusted systems are special systems designed to serve the purpose of providing security. It’s crucial for organizations and. The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. Trustworthy systems should prioritize data. Trusted Systems In Information Security.
From www.brainkart.com
Security Features of Trusted Operating Systems Trusted Systems In Information Security Safety is ensured by trusted. Trusted systems rely on encryption. It’s crucial for organizations and. Trustworthy systems should prioritize data privacy and security as a top priority. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure. Trusted Systems In Information Security.
From www.slideserve.com
PPT ELEC5616 computer and network security PowerPoint Presentation Trusted Systems In Information Security Trusted systems are special systems designed to serve the purpose of providing security. It’s crucial for organizations and. The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. Trustworthy systems should prioritize data privacy and security as a top priority. Safety is ensured by trusted. A guide to understanding security modeling in. Trusted Systems In Information Security.
From trustedsys.com
Certified Integration Partners Trusted Systems Endpoint Security Trusted Systems In Information Security A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. It’s crucial for organizations and. Trustworthy systems should prioritize data privacy and security as a top priority. Trusted systems are special systems designed to serve the purpose of providing security. Safety is ensured by trusted. Provides a renewed focus. Trusted Systems In Information Security.
From www.slideserve.com
PPT Trusted System? PowerPoint Presentation, free download ID6963895 Trusted Systems In Information Security The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. Trusted systems rely on encryption. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. It’s crucial for organizations and. Safety is ensured by trusted. In simple terms, a trusted system. Trusted Systems In Information Security.
From www.slideserve.com
PPT Firewalls PowerPoint Presentation, free download ID2781984 Trusted Systems In Information Security Trusted systems are special systems designed to serve the purpose of providing security. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. A guide to understanding security modeling in trusted systems is intended for. Trusted Systems In Information Security.
From www.slideserve.com
PPT Operating System Security PowerPoint Presentation, free download Trusted Systems In Information Security The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. Trusted systems rely on encryption. Trustworthy systems should prioritize data privacy and security as a top priority. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. It’s crucial for organizations. Trusted Systems In Information Security.
From www.slideserve.com
PPT Chapter 7 Network Perimeter Security PowerPoint Presentation Trusted Systems In Information Security Trusted systems are special systems designed to serve the purpose of providing security. Trustworthy systems should prioritize data privacy and security as a top priority. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Trusted systems rely on encryption. In simple terms, a trusted system is a secure. Trusted Systems In Information Security.
From www.slideserve.com
PPT Security Models and Designing a Trusted Operating System Trusted Systems In Information Security Trusted systems are special systems designed to serve the purpose of providing security. Safety is ensured by trusted. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Provides a. Trusted Systems In Information Security.
From www.slideserve.com
PPT Security PowerPoint Presentation, free download ID408976 Trusted Systems In Information Security In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Safety is ensured by trusted. The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. It’s crucial for organizations and. Trusted systems rely on encryption. Provides a renewed focus on the design principles. Trusted Systems In Information Security.
From www.pivotpointsecurity.com
Trusted Framework in Information Security Strategy Trusted Systems In Information Security Safety is ensured by trusted. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Trusted systems rely on encryption. Trustworthy systems should prioritize data privacy and security as a. Trusted Systems In Information Security.
From www.researchgate.net
THE TRUSTED AND CONTROLLABLE NETWORK SECURITY ARCHITECTURE Download Trusted Systems In Information Security The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. Trusted systems are special systems designed. Trusted Systems In Information Security.
From www.lairdconnect.com
A Closer Look at the Chain of Trust Security Architecture Provisioning Trusted Systems In Information Security It’s crucial for organizations and. Trusted systems are special systems designed to serve the purpose of providing security. The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Trusted systems rely on encryption.. Trusted Systems In Information Security.
From www.slideserve.com
PPT Security Models and Designing a Trusted Operating System Trusted Systems In Information Security Trusted systems rely on encryption. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. It’s crucial for organizations and. The trusted computing group (tcg) is a non profit organization. Trusted Systems In Information Security.
From www.slideserve.com
PPT Security Models and Designing a Trusted Operating System Trusted Systems In Information Security It’s crucial for organizations and. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. In simple terms, a trusted system is a secure system that is specifically designed to resist any. Trusted Systems In Information Security.
From www.militaryaerospace.com
Cyber security robustness of an embedded computing system with trusted Trusted Systems In Information Security Safety is ensured by trusted. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models. Trusted Systems In Information Security.
From www.netscribes.com
Building digital trust amid rapid digital transformation Netscribes Trusted Systems In Information Security It’s crucial for organizations and. Trustworthy systems should prioritize data privacy and security as a top priority. The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Trusted systems rely on. Trusted Systems In Information Security.
From www.slideserve.com
PPT Computer and Information Security PowerPoint Presentation, free Trusted Systems In Information Security Trusted systems rely on encryption. Safety is ensured by trusted. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Trustworthy systems should prioritize data privacy and security as a. Trusted Systems In Information Security.
From www.youtube.com
Trusted SystemTrusted System in network security cryptography and Trusted Systems In Information Security Trustworthy systems should prioritize data privacy and security as a top priority. It’s crucial for organizations and. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. Trusted systems are special systems designed to serve the purpose of providing security. The trusted computing group (tcg) is a non profit organization that creates open. Trusted Systems In Information Security.
From www.slideserve.com
PPT Trusted System? PowerPoint Presentation, free download ID6963895 Trusted Systems In Information Security Safety is ensured by trusted. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Trusted systems are special systems designed to serve the purpose of providing security. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. It’s crucial. Trusted Systems In Information Security.
From www.curtisswrightds.com
COTSBased Trusted Computing Getting Started in NextGeneration Trusted Systems In Information Security In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. It’s crucial for organizations and. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Safety is ensured by trusted. The trusted computing group (tcg) is a non profit organization. Trusted Systems In Information Security.
From appcheck-ng.com
What is a trust boundary and how can I apply the principle to improve Trusted Systems In Information Security It’s crucial for organizations and. The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. Safety is ensured by trusted. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Trusted systems rely on encryption. Trustworthy systems should prioritize data privacy and security. Trusted Systems In Information Security.
From www.slideserve.com
PPT Computer Security Principles and Practice PowerPoint Trusted Systems In Information Security The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Trusted systems are special systems designed to serve the purpose of providing security. It’s crucial for organizations and. Provides a renewed focus on. Trusted Systems In Information Security.
From www.researchgate.net
Trust model system architecture. Download Scientific Diagram Trusted Systems In Information Security Trustworthy systems should prioritize data privacy and security as a top priority. Trusted systems are special systems designed to serve the purpose of providing security. It’s crucial for organizations and. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Provides a renewed focus on the design principles and. Trusted Systems In Information Security.
From www.slideserve.com
PPT Chapter 5 Network Security PowerPoint Presentation, free download Trusted Systems In Information Security Trusted systems rely on encryption. Trustworthy systems should prioritize data privacy and security as a top priority. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Trusted systems are special systems designed to serve the purpose of providing security. In simple terms, a trusted system is a secure. Trusted Systems In Information Security.
From www.slideserve.com
PPT Security Models and Designing a Trusted Operating System Trusted Systems In Information Security Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. Trustworthy systems should prioritize data privacy and security as a top priority. Trusted systems are special systems designed to serve the purpose of providing security. It’s crucial for organizations and. Safety is ensured by trusted. Trusted systems rely on encryption. In simple terms,. Trusted Systems In Information Security.
From slidetodoc.com
Chapter 8 Principles of Security Models Design and Trusted Systems In Information Security A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Trustworthy systems should prioritize data privacy and security as a top priority. Trusted systems are special systems designed to serve the purpose of providing security. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure. Trusted Systems In Information Security.
From www.slideserve.com
PPT Operating System Security PowerPoint Presentation, free download Trusted Systems In Information Security Safety is ensured by trusted. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Trustworthy systems should prioritize data privacy and security as a top priority. Trusted systems rely on encryption. In simple terms, a trusted system is a secure system that is specifically designed to resist any. Trusted Systems In Information Security.
From www.slideserve.com
PPT Trusted System? PowerPoint Presentation, free download ID6963895 Trusted Systems In Information Security A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Trusted systems are special systems designed to serve the purpose of providing security. Safety is ensured by trusted. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. Trusted systems rely on. Trusted Systems In Information Security.
From www.slideserve.com
PPT Computer and Information Security PowerPoint Presentation, free Trusted Systems In Information Security In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Trusted systems rely on encryption. A guide to understanding security modeling in trusted systems is intended for use by personnel responsible for developing models of the. Safety is ensured by trusted. The trusted computing group (tcg) is a non profit organization. Trusted Systems In Information Security.
From home.ubalt.edu
Security Trusted Systems In Information Security In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Safety is ensured by trusted. Trusted systems rely on encryption. Trustworthy systems should prioritize data privacy and security as a top priority. Provides a renewed focus on the design principles and concepts for engineering trustworthy secure systems, distributing the. A guide. Trusted Systems In Information Security.
From www.slideserve.com
PPT Security Models and Designing a Trusted Operating System Trusted Systems In Information Security The trusted computing group (tcg) is a non profit organization that creates open standards related to information security. Safety is ensured by trusted. Trusted systems rely on encryption. In simple terms, a trusted system is a secure system that is specifically designed to resist any unauthorized access. Provides a renewed focus on the design principles and concepts for engineering trustworthy. Trusted Systems In Information Security.