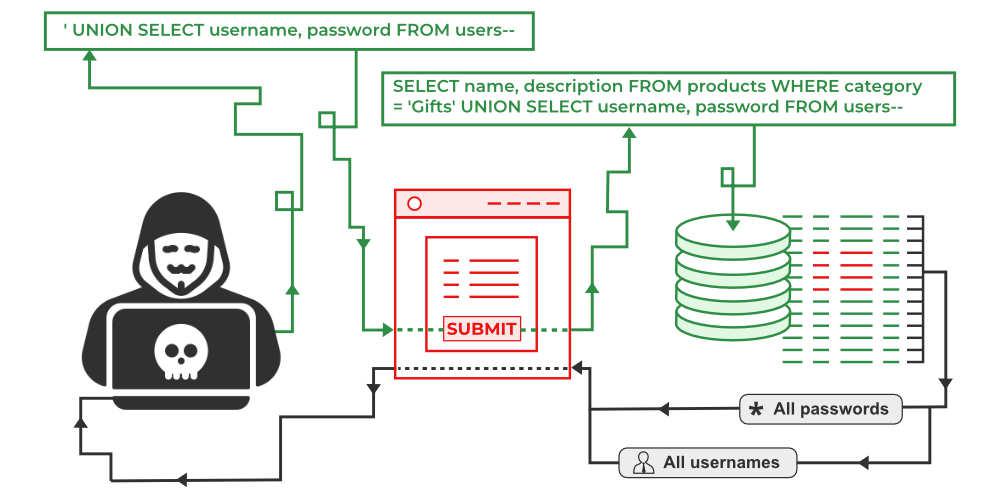
Sql Injection Get Password . This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. Use our sql injection cheat sheet to learn about the different variants of the sql injection vulnerability. In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. In this cheat sheet you can find detailed technical information about. The sql query is crafted in such a way that both username and. Evaluates to select * from users where. Select * from users where login='admin' and password='1' or '1'='1'; Using sql injection to bypass authentication. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password.
from blog.geekster.in
In this cheat sheet you can find detailed technical information about. Using sql injection to bypass authentication. Select * from users where login='admin' and password='1' or '1'='1'; Evaluates to select * from users where. In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. The sql query is crafted in such a way that both username and. Use our sql injection cheat sheet to learn about the different variants of the sql injection vulnerability. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the.
SQL Injection Prevention in Java Top Tips for Secure Code
Sql Injection Get Password As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password. In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. Evaluates to select * from users where. In this cheat sheet you can find detailed technical information about. Select * from users where login='admin' and password='1' or '1'='1'; After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. Use our sql injection cheat sheet to learn about the different variants of the sql injection vulnerability. As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password. Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. Using sql injection to bypass authentication. The sql query is crafted in such a way that both username and.
From github.com
GitHub taqiyeddinedj/SQLInjection The script will use a UNIONbased SQL injection attack to Sql Injection Get Password In this cheat sheet you can find detailed technical information about. Use our sql injection cheat sheet to learn about the different variants of the sql injection vulnerability. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. This sql injection cheat sheet contains examples of useful. Sql Injection Get Password.
From www.opentechinfo.com
Sql injection Tutorials Beginners Guide website hacking Sql Injection Get Password The sql query is crafted in such a way that both username and. Evaluates to select * from users where. As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password. Select * from users where login='admin' and password='1' or '1'='1'; Using sql injection to bypass authentication.. Sql Injection Get Password.
From www.youtube.com
Sqlmap (Sql injection) Get the root password YouTube Sql Injection Get Password As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. Select * from users where name= '' or '1'='1' and password= ''. Sql Injection Get Password.
From github.com
GitHub rdoix/SQLInjectionAuthenticationBypassCheatsheet Sql Injection Get Password Use our sql injection cheat sheet to learn about the different variants of the sql injection vulnerability. As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password. Select * from users where login='admin' and password='1' or '1'='1'; Select * from users where name= '' or '1'='1'. Sql Injection Get Password.
From www.youtube.com
Get all usernames and password sql injection union attack retrieving data from other tables Sql Injection Get Password After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. The sql query is crafted in such a way that both username and. In this cheat sheet you can find detailed technical information about. Select * from users where login='admin' and password='1' or '1'='1'; As a popular. Sql Injection Get Password.
From systemweakness.com
SQL Injection Attacks. What is a SQL Injection attack? by ADITYA KUMAR System Weakness Sql Injection Get Password This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password. In this cheat sheet you can find detailed technical information about. Select. Sql Injection Get Password.
From whatismyipaddress.com
SQL Injection What It Is and How Does It Work Sql Injection Get Password Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. Evaluates to select * from users where. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. After we confirm that the site is vulnerable to sql injection, the next step is. Sql Injection Get Password.
From cybr.com
SQL injection attacks part 3 Cybr Sql Injection Get Password The sql query is crafted in such a way that both username and. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. In this cheat sheet you can find detailed technical information about. Use our sql injection cheat sheet to learn about the different variants of. Sql Injection Get Password.
From blog.geekster.in
SQL Injection Prevention in Java Top Tips for Secure Code Sql Injection Get Password After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. Select * from users where login='admin' and password='1' or '1'='1'; This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. In this example. Sql Injection Get Password.
From cybr.com
Blind SQL Injections with SQLMap against the DVWA Cybr Sql Injection Get Password After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. Select * from users where name= '' or '1'='1' and password= '' or. Sql Injection Get Password.
From techyrick.com
Automating SQLi with SQLmap and custom code. Sql Injection Get Password Use our sql injection cheat sheet to learn about the different variants of the sql injection vulnerability. Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. Select * from users where login='admin' and password='1' or '1'='1'; Using sql injection to bypass authentication. In this cheat sheet you can find detailed technical information about. The sql. Sql Injection Get Password.
From hackr.io
Download SQL Injection Cheat Sheet PDF for Quick References Sql Injection Get Password In this cheat sheet you can find detailed technical information about. Using sql injection to bypass authentication. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate. Sql Injection Get Password.
From medium.com
Dumping Passwords From Databases — Unionbased SQL Injection Scripting by Lorenzo Stella Medium Sql Injection Get Password In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. The sql query is crafted in such a way that both username and. Select * from users where login='admin' and password='1' or '1'='1'; As a popular request, let's see how we can use sql injections to bypass vulnerable login pages. Sql Injection Get Password.
From computersecuritypgp.blogspot.com
Computer Security and PGP What is an SQL Injection Attack Sql Injection Get Password Select * from users where login='admin' and password='1' or '1'='1'; Use our sql injection cheat sheet to learn about the different variants of the sql injection vulnerability. Evaluates to select * from users where. Using sql injection to bypass authentication. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks. Sql Injection Get Password.
From www.qafox.com
SQL Injection order by Payload Part 6 QAFox Sql Injection Get Password Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. Select * from users where login='admin' and password='1' or '1'='1'; Using sql injection to bypass authentication. Evaluates to select * from users. Sql Injection Get Password.
From www.geeksforgeeks.org
What is SQL Injection UNION Attacks? Sql Injection Get Password Evaluates to select * from users where. In this cheat sheet you can find detailed technical information about. Using sql injection to bypass authentication. Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. Select * from users where login='admin' and password='1' or '1'='1'; After we confirm that the site is vulnerable to sql injection, the. Sql Injection Get Password.
From medium.com
SQL Injection in Password Function by khaled gaber Medium Sql Injection Get Password Using sql injection to bypass authentication. The sql query is crafted in such a way that both username and. As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password. Evaluates to select * from users where. After we confirm that the site is vulnerable to sql. Sql Injection Get Password.
From www.veracode.com
What is SQL Injection? SQL Injection Prevention Veracode Sql Injection Get Password Evaluates to select * from users where. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. Select * from users where login='admin' and password='1' or '1'='1'; In this cheat sheet you can find detailed technical information about. Using sql injection to bypass authentication. Use our sql. Sql Injection Get Password.
From www.scribd.com
SQL Injections PDF Password Transport Layer Security Sql Injection Get Password Select * from users where login='admin' and password='1' or '1'='1'; Using sql injection to bypass authentication. In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in the. In. Sql Injection Get Password.
From www.hackercoolmagazine.com
SQL Injection for beginners Hackercool Magazine Sql Injection Get Password Evaluates to select * from users where. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password. Use our sql injection cheat. Sql Injection Get Password.
From www.theknowledgeacademy.com
SQL Injection in Cyber Security A Brief Guide Sql Injection Get Password Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. Select * from users where login='admin' and password='1' or '1'='1'; In this cheat sheet you can find detailed technical information about. The sql query is crafted in such a way that both username and. Use our sql injection cheat sheet to learn about the different variants. Sql Injection Get Password.
From www.youtube.com
Log in a user using their Username and Password to an SQL database while avoiding SQL injections Sql Injection Get Password Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. Use our sql injection cheat sheet to learn about the different variants of the sql injection vulnerability. In this cheat sheet you can find detailed technical information about. The sql query is crafted in such a way that both username and. Using sql injection to bypass. Sql Injection Get Password.
From www.youtube.com
Ethical Hacking Compromising account passwords using SQL Injection attacks YouTube Sql Injection Get Password Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. Using sql injection to bypass authentication. In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. Evaluates to select * from users where. In this cheat sheet you can find detailed technical information about. Use our. Sql Injection Get Password.
From medium.com
Let’s Learn SQL Injection and Bypass Login by sachith sujeewa Medium Sql Injection Get Password Use our sql injection cheat sheet to learn about the different variants of the sql injection vulnerability. Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. In this cheat sheet you can find detailed technical information about. In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using. Sql Injection Get Password.
From www.youtube.com
SQL Injection 4 Stealing Passwords Hacking YouTube Sql Injection Get Password In this cheat sheet you can find detailed technical information about. Use our sql injection cheat sheet to learn about the different variants of the sql injection vulnerability. As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password. Select * from users where login='admin' and password='1'. Sql Injection Get Password.
From 0xma.github.io
Second Order SQL Injection Example 1 Sql Injection Get Password Select * from users where login='admin' and password='1' or '1'='1'; In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. Using sql injection to bypass authentication. The sql query is crafted in such a way that both username and. Evaluates to select * from users where. As a popular request,. Sql Injection Get Password.
From widehostmedia.com
Mengenal Apa itu SQL Injection Wide Host Media Sql Injection Get Password Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password. Select * from users where login='admin' and password='1' or '1'='1'; Use our sql injection cheat sheet to learn about the different variants. Sql Injection Get Password.
From www.slideserve.com
PPT SQL Injection PowerPoint Presentation, free download ID6662917 Sql Injection Get Password In this cheat sheet you can find detailed technical information about. Using sql injection to bypass authentication. In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. Sql Injection Get Password.
From www.youtube.com
OWASP A1 Injection extract username & passwords from database uisng SQL injection YouTube Sql Injection Get Password Evaluates to select * from users where. Select * from users where login='admin' and password='1' or '1'='1'; In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise. Sql Injection Get Password.
From indiancybersecuritysolutions.com
What is SQL Injection Indian Cyber Security Solutions Sql Injection Get Password Using sql injection to bypass authentication. Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks. Sql Injection Get Password.
From linuxhint.com
Blind SQL Injection Techniques Tutorial Sql Injection Get Password Evaluates to select * from users where. In this cheat sheet you can find detailed technical information about. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using. Sql Injection Get Password.
From adelwin505.blogspot.com
Tutorial SQL injection post method!!! Sql Injection Get Password Using sql injection to bypass authentication. This sql injection cheat sheet contains examples of useful syntax that you can use to perform a variety of tasks that often arise when. In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. As a popular request, let's see how we can use. Sql Injection Get Password.
From memoryleaks.blog
Memory Leaks Exploiting SQL Injections to Access User Passwords Sql Injection Get Password As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password. In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. After we confirm that the site is vulnerable to sql injection, the next step is to. Sql Injection Get Password.
From www.youtube.com
DVWA SQL Injection & Cracking Passwords! YouTube Sql Injection Get Password Evaluates to select * from users where. In this cheat sheet you can find detailed technical information about. In this example we will demonstrate a technique to bypass the authentication of a vulnerable login page using sql injection. After we confirm that the site is vulnerable to sql injection, the next step is to type the appropriate payload (input) in. Sql Injection Get Password.
From techofide.com
SQL Injection Attack (SQLi) SQL Injection Prevention Sql Injection Get Password Select * from users where name= '' or '1'='1' and password= '' or '1'='1'. In this cheat sheet you can find detailed technical information about. As a popular request, let's see how we can use sql injections to bypass vulnerable login pages without needing a valid username or password. Evaluates to select * from users where. The sql query is. Sql Injection Get Password.