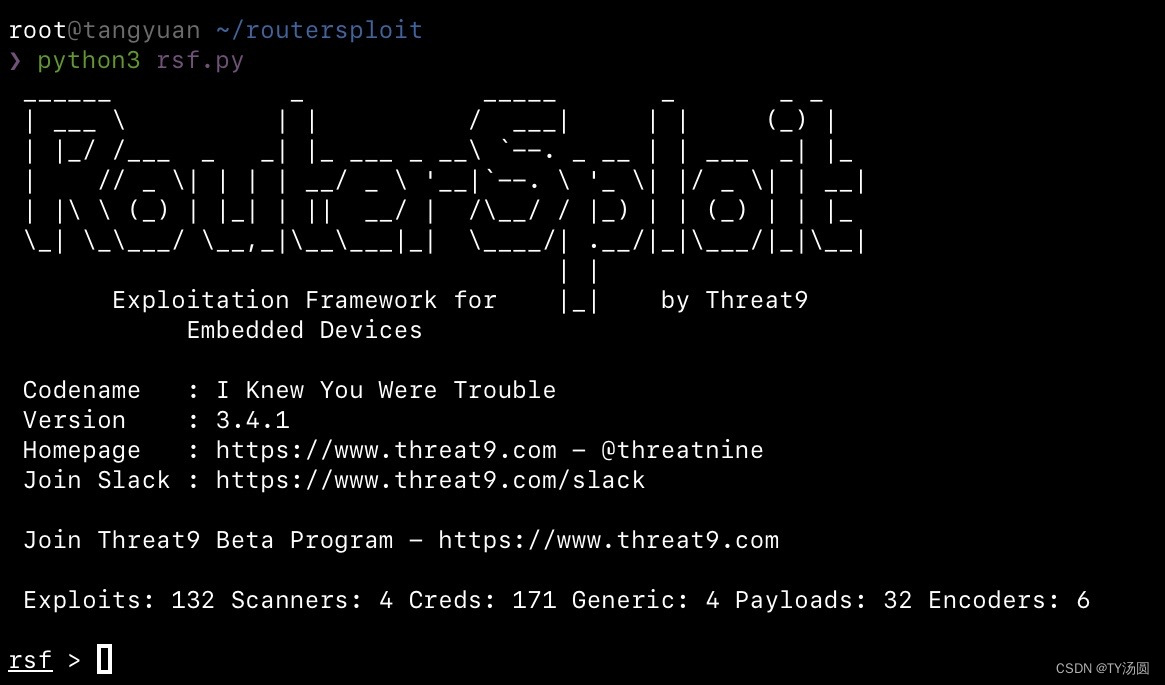
Routersploit Mikrotik . It consists of various modules that aid. — hey guys! Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. The scan total, 578,456, should be considered a floor, because i didn’t scan the. Hackersploit here back again with another video, in this video i. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Routersploit has a number of. The raw results are on github.
from www.bilibili.com
It consists of various modules that aid. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. The scan total, 578,456, should be considered a floor, because i didn’t scan the. The raw results are on github. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. — hey guys! Routersploit has a number of. Hackersploit here back again with another video, in this video i.
安卓手机通过termux免Root运行Routersploit对路由器进行渗透【渗透工具】 哔哩哔哩
Routersploit Mikrotik — the scan found 578,456 mikrotik routers with port 8291 open to the internet. Hackersploit here back again with another video, in this video i. Routersploit has a number of. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. — hey guys! It consists of various modules that aid. The scan total, 578,456, should be considered a floor, because i didn’t scan the. The raw results are on github. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. — the scan found 578,456 mikrotik routers with port 8291 open to the internet.
From www.bilibili.com
安卓手机通过termux免Root运行Routersploit对路由器进行渗透【渗透工具】 哔哩哔哩 Routersploit Mikrotik Routersploit has a number of. Hackersploit here back again with another video, in this video i. — hey guys! — the scan found 578,456 mikrotik routers with port 8291 open to the internet. The scan total, 578,456, should be considered a floor, because i didn’t scan the. Module bypass authentication through winbox service in mikrotik devices version from. Routersploit Mikrotik.
From www.true-tech.co.ke
MikroTik RB450Gx4 Gigabit Router Routersploit Mikrotik Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. The raw results are on github. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. The scan total, 578,456, should be considered a floor, because i didn’t scan the. — for vulnerability detection and exploitation of embedded systems there. Routersploit Mikrotik.
From www.itshopp.com
MikroTik RB951G2HnD 2.4GHz 600MHz 5xGbit 802.11bgn LAN Routersploit Mikrotik — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The scan total, 578,456, should be considered a floor, because i didn’t scan the. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. — hey guys! The raw results are on github. Module bypass authentication through winbox. Routersploit Mikrotik.
From www.prodefence.org
routersploit v3.2.0 released Router Exploitation Framework Routersploit Mikrotik — the scan found 578,456 mikrotik routers with port 8291 open to the internet. Routersploit has a number of. It consists of various modules that aid. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The raw results are on github. Hackersploit here back again with another video, in this video i.. Routersploit Mikrotik.
From www.mikrotik.org.pl
Mikrotik RouterOS Mikrotik system operacyjny Routersploit Mikrotik It consists of various modules that aid. Hackersploit here back again with another video, in this video i. The scan total, 578,456, should be considered a floor, because i didn’t scan the. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. — hey guys! — for vulnerability detection and exploitation of embedded. Routersploit Mikrotik.
From www.mikrotikusers.com
Lab 1.2 Installing MikroTik RouterOS on GNS3 Routersploit Mikrotik Hackersploit here back again with another video, in this video i. It consists of various modules that aid. Routersploit has a number of. The raw results are on github. — hey guys! — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Module bypass authentication through winbox service in mikrotik devices version from. Routersploit Mikrotik.
From www.lazada.sg
MikroTik hAP ax2 WiFi6 Wireless Router, QuadCore CPU ARM64, 1GB RAM, 5 Routersploit Mikrotik — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The scan total, 578,456, should be considered a floor, because i didn’t scan the. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. Routersploit has a number of. It consists of various modules that aid. The raw results are. Routersploit Mikrotik.
From hdyytechnology.en.made-in-china.com
Mikrotik Rb4011igs+RM 10Port Gigabit Router, New in Box Black Routersploit Mikrotik The scan total, 578,456, should be considered a floor, because i didn’t scan the. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. Routersploit has a number of. — for vulnerability detection and exploitation of embedded systems there is. Routersploit Mikrotik.
From mikrotik.com
MikroTik Routers and Wireless Products CRS51816XS2XQRM Routersploit Mikrotik It consists of various modules that aid. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. Hackersploit here back again with another video, in this video i. Routersploit has a number of. The raw results are on github. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. —. Routersploit Mikrotik.
From blog.linitx.com
How to Eliminate WiFi Dead Spots with a MikroTik Router (Repeater Routersploit Mikrotik The raw results are on github. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The scan total, 578,456, should be considered a floor, because i didn’t scan the. — hey guys! It consists of various modules that. Routersploit Mikrotik.
From www.lazada.com.ph
Mikrotik RB5009 ( RB5009UG+S+IN ) heavyduty home lab router Lazada PH Routersploit Mikrotik Hackersploit here back again with another video, in this video i. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. It consists of various modules that aid. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. — the scan found 578,456 mikrotik routers with port 8291 open. Routersploit Mikrotik.
From www.youtube.com
Exploit a Router Using RouterSploit [Tutorial] YouTube Routersploit Mikrotik It consists of various modules that aid. — hey guys! — the scan found 578,456 mikrotik routers with port 8291 open to the internet. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The scan total, 578,456, should be considered a floor, because i didn’t scan the. Hackersploit here back again. Routersploit Mikrotik.
From timigate.com
9 things you must do on a Mikrotik router to effectively secure your Routersploit Mikrotik It consists of various modules that aid. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Routersploit has a number of. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. Hackersploit here back. Routersploit Mikrotik.
From www.xbsasia.ph
Mikrotik RouterBOARD Dude Edition (RB1100Dx4) 1U rackmount router with Routersploit Mikrotik Hackersploit here back again with another video, in this video i. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. The raw results are on github. The scan total, 578,456, should be considered a floor, because i didn’t scan the. — for vulnerability detection and exploitation of embedded systems there is a framework called. Routersploit Mikrotik.
From mikrotik.com
MikroTik Routers and Wireless Products CRS3108G+2S+IN Routersploit Mikrotik Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. It consists of various modules that aid. — hey guys! Routersploit has a number of. Hackersploit here back again with another video, in this video i. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. The scan total, 578,456,. Routersploit Mikrotik.
From www.roc-noc.com
Mikrotik RouterBoard L009UiGSRM Dual core ARM64 CPU, 8 Gbit Routersploit Mikrotik Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. The raw results are on github. Routersploit has a number of. — hey guys! It consists of various modules that aid. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The scan total, 578,456, should be considered a. Routersploit Mikrotik.
From www.ispsupplies.ca
MikroTik 2.5 Gigabit 10 Gigabit SFP+, 1.4 GHz CPU, 1GB RAM Routersploit Mikrotik The raw results are on github. — hey guys! The scan total, 578,456, should be considered a floor, because i didn’t scan the. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Hackersploit here back again with another video, in this video i. — the scan found 578,456 mikrotik routers with. Routersploit Mikrotik.
From www.joinmywifi.com
MikroTik Router Configuration JoinMyWifi Routersploit Mikrotik Hackersploit here back again with another video, in this video i. Routersploit has a number of. — hey guys! — the scan found 578,456 mikrotik routers with port 8291 open to the internet. The scan total, 578,456, should be considered a floor, because i didn’t scan the. The raw results are on github. It consists of various modules. Routersploit Mikrotik.
From www.ispsupplies.com
MikroTik FiberBox Plus 4X10 Gigabit SFP+ ports 98DX226S 800 MHz Routersploit Mikrotik Routersploit has a number of. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. — hey guys! — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Hackersploit here back again with another. Routersploit Mikrotik.
From www.youtube.com
RouterSploit Complete Tutorial YouTube Routersploit Mikrotik Routersploit has a number of. It consists of various modules that aid. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. — hey guys! The raw results are on github. Hackersploit here back again with another video, in this. Routersploit Mikrotik.
From blog.linitx.com
mikrotik routers Archives LinITX Blog Routersploit Mikrotik Routersploit has a number of. It consists of various modules that aid. The scan total, 578,456, should be considered a floor, because i didn’t scan the. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. Hackersploit here back again with another video, in this video i. — the scan found 578,456 mikrotik routers with. Routersploit Mikrotik.
From www.kitploit.com
RouterSploit Router Exploitation Framework Routersploit Mikrotik It consists of various modules that aid. Hackersploit here back again with another video, in this video i. The raw results are on github. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. The scan total, 578,456, should. Routersploit Mikrotik.
From www.ispsupplies.com
MikroTik 2.4 GHz 802.11b/g/n/ax dualchain, 4 dBi Antenna 512MB RAM Routersploit Mikrotik — the scan found 578,456 mikrotik routers with port 8291 open to the internet. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. Routersploit has a number of. — hey guys! Hackersploit here back again with another video, in this video i. It consists of various modules that aid. Module bypass. Routersploit Mikrotik.
From bitmonger.blogspot.com
Bitmonger Using a MikroTik cAP as a Home Wireless Access Point Routersploit Mikrotik Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. Routersploit has a number of. Hackersploit here back again with another video, in this video i. — hey guys! The scan total, 578,456, should be considered a floor, because i didn’t scan the. The raw results are on github. — the scan found 578,456. Routersploit Mikrotik.
From www.minim.com
How to configure MikroTik router start here Routersploit Mikrotik Hackersploit here back again with another video, in this video i. It consists of various modules that aid. — hey guys! — the scan found 578,456 mikrotik routers with port 8291 open to the internet. The scan total, 578,456, should be considered a floor, because i didn’t scan the. — for vulnerability detection and exploitation of embedded. Routersploit Mikrotik.
From vibegaming.com.bd
Mikrotik Hex lite RB750R2 Plastic Body Router Vibe Gaming Routersploit Mikrotik — the scan found 578,456 mikrotik routers with port 8291 open to the internet. The scan total, 578,456, should be considered a floor, because i didn’t scan the. Hackersploit here back again with another video, in this video i. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. It consists of various modules that. Routersploit Mikrotik.
From www.wavonline.com
MikroTik L009UiGS2HaxDIN 2.5Gbit SFP 8Port Wireless Router Routersploit Mikrotik Hackersploit here back again with another video, in this video i. The raw results are on github. It consists of various modules that aid. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. Routersploit has a number of. — hey guys! — for vulnerability detection and exploitation of embedded systems there is. Routersploit Mikrotik.
From www.youtube.com
How to upgrade MikroTik RouterOS offline YouTube Routersploit Mikrotik — hey guys! The scan total, 578,456, should be considered a floor, because i didn’t scan the. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. It consists of various modules that aid. — for vulnerability detection and. Routersploit Mikrotik.
From tehnoblog.org
MikroTik router How to convert hAP or hAP lite into ordinary Switch Routersploit Mikrotik The raw results are on github. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. — hey guys! Routersploit has a number of.. Routersploit Mikrotik.
From www.ubnt.com.au
Buy MiktoTik WiFi 6 hAP ax² RouterOS L4 License Online in Australia Routersploit Mikrotik It consists of various modules that aid. The raw results are on github. — hey guys! Hackersploit here back again with another video, in this video i. The scan total, 578,456, should be considered a floor, because i didn’t scan the. Routersploit has a number of. — the scan found 578,456 mikrotik routers with port 8291 open to. Routersploit Mikrotik.
From www.geewiz.co.za
MikroTik hAP ax3 4 Port Gigabit 1 Port 2.5G PoE WiFi 6 Router GeeWiz Routersploit Mikrotik The scan total, 578,456, should be considered a floor, because i didn’t scan the. The raw results are on github. Hackersploit here back again with another video, in this video i. Routersploit has a number of. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. — hey guys! — the scan found 578,456. Routersploit Mikrotik.
From mikrotik.com
MikroTik Routers and Wireless Products CRS1128P4SIN Routersploit Mikrotik — hey guys! It consists of various modules that aid. The scan total, 578,456, should be considered a floor, because i didn’t scan the. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. — for vulnerability detection and. Routersploit Mikrotik.
From mikrotik.com
MikroTik Routers and Wireless Products RB2011UiAS2HnDIN Routersploit Mikrotik Routersploit has a number of. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. Hackersploit here back again with another video, in this video i. The scan total, 578,456, should be considered a floor, because i didn’t scan the. It consists of various modules that aid. The raw results are on github. — for. Routersploit Mikrotik.
From fadtee.weebly.com
Mikrotik routeros configuration fadtee Routersploit Mikrotik — for vulnerability detection and exploitation of embedded systems there is a framework called routersploit. It consists of various modules that aid. The raw results are on github. Hackersploit here back again with another video, in this video i. — hey guys! Routersploit has a number of. The scan total, 578,456, should be considered a floor, because i. Routersploit Mikrotik.
From www.youtube.com
MikroTik Router Configuration Step by Step MikroTik Series YouTube Routersploit Mikrotik It consists of various modules that aid. — the scan found 578,456 mikrotik routers with port 8291 open to the internet. Hackersploit here back again with another video, in this video i. Module bypass authentication through winbox service in mikrotik devices version from 6.29 (release date:. The raw results are on github. — for vulnerability detection and exploitation. Routersploit Mikrotik.