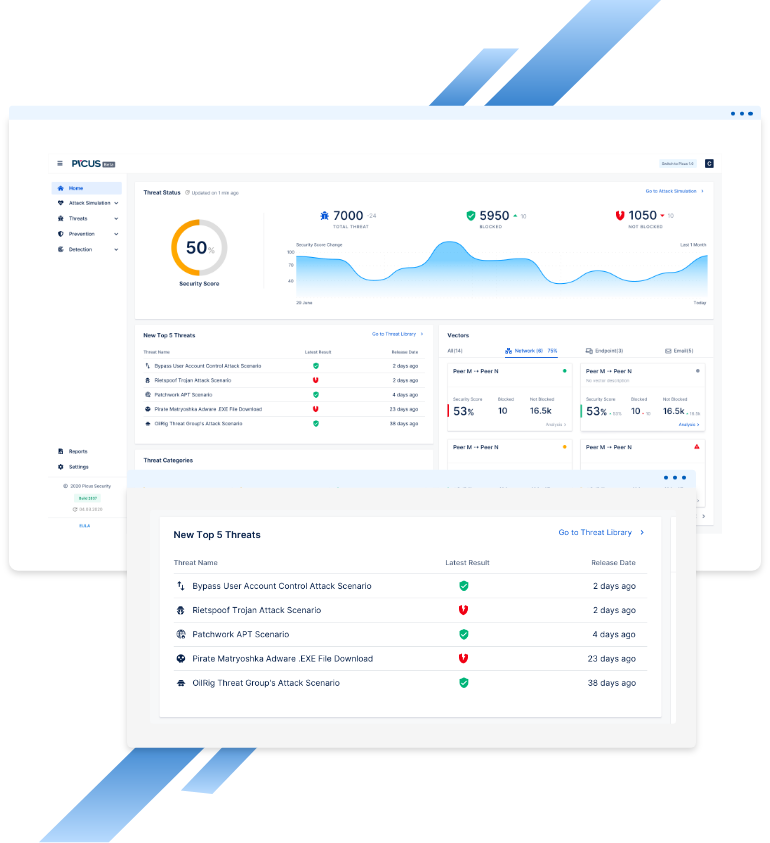
Security Control Validation . In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. Proactively test and validate the effectiveness of your security controls to help protect your. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. Continuous security validation will help a company: Improving cyber resilience with security controls validation is an attainable ideal. In this guide to security controls validation, we delve into the nuts and bolts of security controls. Measure your cyber defense effectiveness. Increase its cyber resiliency by frequent testing and validation.
from www.picussecurity.com
Improving cyber resilience with security controls validation is an attainable ideal. Measure your cyber defense effectiveness. Increase its cyber resiliency by frequent testing and validation. Proactively test and validate the effectiveness of your security controls to help protect your. Continuous security validation will help a company: In this guide to security controls validation, we delve into the nuts and bolts of security controls. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an.
Security Control Validation & Mitigation Picus
Security Control Validation This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. Improving cyber resilience with security controls validation is an attainable ideal. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. Increase its cyber resiliency by frequent testing and validation. In this guide to security controls validation, we delve into the nuts and bolts of security controls. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Measure your cyber defense effectiveness. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. Proactively test and validate the effectiveness of your security controls to help protect your. Continuous security validation will help a company:
From www.picussecurity.com
What Is Security Control Validation? Security Control Validation Increase its cyber resiliency by frequent testing and validation. Improving cyber resilience with security controls validation is an attainable ideal. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. Continuous security validation will help a company: In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why. Security Control Validation.
From www.picussecurity.com
Security Control Validation Attack Modules Security Control Validation Measure your cyber defense effectiveness. Continuous security validation will help a company: Increase its cyber resiliency by frequent testing and validation. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. This. Security Control Validation.
From www.picussecurity.com
Security Control Validation Security Control Validation Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. Improving cyber resilience with security controls validation is an attainable ideal. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security. Security Control Validation.
From techjournal.org
Why Security Control Validation is Essential Tech Journal Security Control Validation Increase its cyber resiliency by frequent testing and validation. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. Continuous security validation will help a company: Measure your cyber defense effectiveness. Proactively test and validate the effectiveness. Security Control Validation.
From cybersecurity-excellence-awards.com
The Picus Complete Security Validation Platform Cybersecurity Security Control Validation This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. In this guide to security controls validation, we delve into the nuts and bolts of security controls. Increase its cyber resiliency by frequent testing and validation. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. Proactively. Security Control Validation.
From www.picussecurity.com
Security Control Validation Security Control Validation This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. In this guide to security controls validation, we delve into the nuts and bolts of security controls. Measure your. Security Control Validation.
From validato.io
A Guide to Security Controls Validation Validato Security Control Validation Improving cyber resilience with security controls validation is an attainable ideal. Continuous security validation will help a company: Measure your cyber defense effectiveness. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. Proactively test and validate the effectiveness of your security controls to help protect your. This approach enables security teams to safely deploy. Security Control Validation.
From cybersecurity-excellence-awards.com
The Picus Complete Security Control Validation Platform Cybersecurity Security Control Validation Improving cyber resilience with security controls validation is an attainable ideal. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Measure your cyber defense effectiveness. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. In this guide. Security Control Validation.
From kz.iitd.com.ua
Security Control Validation for Prevention Controls iIT Distribution Security Control Validation In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Proactively test and validate the effectiveness of your security controls to help protect your. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. Continuous security validation will help. Security Control Validation.
From www.picussecurity.com
Why Security Control Validation is a must for every organization Security Control Validation Proactively test and validate the effectiveness of your security controls to help protect your. Continuous security validation will help a company: In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. This. Security Control Validation.
From validato.io
US CISA's of Security Controls Validation a major Security Control Validation Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. Measure your cyber defense effectiveness. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. In this guide to security controls validation, we delve into the nuts and bolts of security controls. Increase its cyber resiliency by. Security Control Validation.
From www.youtube.com
Validate your Security Controls with The Picus Complete Security Security Control Validation In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. In this guide to security controls validation, we delve into the nuts and bolts of security controls. Improving cyber resilience with security controls validation is an attainable ideal. Increase its cyber resiliency by frequent testing and validation.. Security Control Validation.
From validato.io
A Guide to Security Controls Validation Validato Security Control Validation Measure your cyber defense effectiveness. In this guide to security controls validation, we delve into the nuts and bolts of security controls. Proactively test and validate the effectiveness of your security controls to help protect your. Improving cyber resilience with security controls validation is an attainable ideal. Continuous security validation will help a company: Increase its cyber resiliency by frequent. Security Control Validation.
From www.attackiq.com
Security Control Validation in the DoD AttackIQ Security Control Validation In this guide to security controls validation, we delve into the nuts and bolts of security controls. Improving cyber resilience with security controls validation is an attainable ideal. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Continuous security validation will help a company: Measure your. Security Control Validation.
From keypointintelligence.com
Security Validation Testing Keypoint Intelligence Security Control Validation Increase its cyber resiliency by frequent testing and validation. Proactively test and validate the effectiveness of your security controls to help protect your. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. Continuous security validation will help a company: In this guide to security controls validation, we delve into the nuts. Security Control Validation.
From www.picussecurity.com
Data sheet Security Control Validation Security Control Validation Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. Proactively test and validate the effectiveness of your security controls to help protect your. Increase its cyber resiliency by frequent testing and validation. In this guide to security controls validation, we delve into the nuts and bolts of security controls. Measure your cyber defense effectiveness.. Security Control Validation.
From www.picussecurity.com
Security Control Validation & Mitigation Picus Security Control Validation This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. Proactively test and validate the effectiveness of your security controls to help protect your. Increase its cyber resiliency by frequent testing and validation. In this guide to. Security Control Validation.
From www.picussecurity.com
THE COMPLETE SECURITY CONTROL VALIDATION FOR THE FINANCE INDUSTRY Security Control Validation In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. Proactively test and validate the effectiveness of your security controls to help protect your. Measure your cyber defense effectiveness. Continuous security validation. Security Control Validation.
From www.picussecurity.com
Security Control Validation Security Control Validation Proactively test and validate the effectiveness of your security controls to help protect your. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Continuous security validation will help. Security Control Validation.
From www.picussecurity.com
Data sheet Security Control Validation Security Control Validation Measure your cyber defense effectiveness. Increase its cyber resiliency by frequent testing and validation. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. Proactively test and validate the effectiveness of your. Security Control Validation.
From www.picussecurity.com
What Is Security Control Validation? Security Control Validation This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. In this guide to security controls validation, we delve into the nuts and bolts of security controls. Improving cyber resilience with security controls validation is an attainable ideal. Security control validation is a continuous security assessment approach that evaluates the effectiveness of. Security Control Validation.
From resources.safebreach.com
Security Control Validation Solution Brief Security Control Validation Improving cyber resilience with security controls validation is an attainable ideal. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Continuous security validation will help a company: Measure your cyber defense. Security Control Validation.
From www.picussecurity.com
What Is Security Control Validation? Security Control Validation Increase its cyber resiliency by frequent testing and validation. Continuous security validation will help a company: In this guide to security controls validation, we delve into the nuts and bolts of security controls. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. This approach enables security teams to safely deploy real attacks—informed by authentic,. Security Control Validation.
From www.satius.io
Security Controls Validation Security Control Validation Improving cyber resilience with security controls validation is an attainable ideal. Increase its cyber resiliency by frequent testing and validation. Proactively test and validate the effectiveness of your security controls to help protect your. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. In this guide to security controls validation, we delve into the. Security Control Validation.
From www.picussecurity.com
Security Control Validation for Prevention Controls Security Control Validation Proactively test and validate the effectiveness of your security controls to help protect your. Continuous security validation will help a company: In this guide to security controls validation, we delve into the nuts and bolts of security controls. Increase its cyber resiliency by frequent testing and validation. Measure your cyber defense effectiveness. Improving cyber resilience with security controls validation is. Security Control Validation.
From www.researchgate.net
Security Checklist Input Validation (CS1) Security checklist Security Control Validation Proactively test and validate the effectiveness of your security controls to help protect your. Increase its cyber resiliency by frequent testing and validation. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. In this guide to security controls validation, we delve into the nuts and bolts of security controls. In his keynote at gsx. Security Control Validation.
From www.safebreach.com
SafeBreach for Security Control Validation SafeBreach Security Control Validation This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Measure your cyber defense. Security Control Validation.
From cybersecurity-excellence-awards.com
The Picus Complete Security Validation Platform Cybersecurity Security Control Validation Measure your cyber defense effectiveness. Increase its cyber resiliency by frequent testing and validation. In this guide to security controls validation, we delve into the nuts and bolts of security controls. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. Improving cyber resilience with security controls validation is an attainable ideal. Continuous security validation. Security Control Validation.
From www.linkedin.com
Five Ways to Lockdown Security Control Validation Security Control Validation In this guide to security controls validation, we delve into the nuts and bolts of security controls. Improving cyber resilience with security controls validation is an attainable ideal. Measure your cyber defense effectiveness. Proactively test and validate the effectiveness of your security controls to help protect your. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant. Security Control Validation.
From www.dtonomy.com
Security Control Validation Automation AIDriven Security Operations Security Control Validation In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Proactively test and validate the effectiveness of your security controls to help protect your. Continuous security validation will help a company: Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. In. Security Control Validation.
From grcready.com
ISO 27002 Information Security Control Validation GRCReady Security Control Validation Increase its cyber resiliency by frequent testing and validation. This approach enables security teams to safely deploy real attacks—informed by authentic, relevant and active threat intelligence—in an. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Improving cyber resilience with security controls validation is an attainable. Security Control Validation.
From www.qseap.com
Security Validation Via Hyacinth qSEAp Information Security Company Security Control Validation Increase its cyber resiliency by frequent testing and validation. Continuous security validation will help a company: In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Measure your cyber defense effectiveness. Improving cyber resilience with security controls validation is an attainable ideal. Security control validation is a. Security Control Validation.
From www.picussecurity.com
What Is Security Control Validation? Security Control Validation Improving cyber resilience with security controls validation is an attainable ideal. Proactively test and validate the effectiveness of your security controls to help protect your. Increase its cyber resiliency by frequent testing and validation. Continuous security validation will help a company: In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important. Security Control Validation.
From www.picussecurity.com
Security Control Validation for Detection Controls Security Control Validation Improving cyber resilience with security controls validation is an attainable ideal. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. Measure your cyber defense effectiveness. Continuous security validation will help a. Security Control Validation.
From cymulate.com
Continuous Security Control Validation Cymulate Security Control Validation Security control validation is a continuous security assessment approach that evaluates the effectiveness of an. In his keynote at gsx 2022, jake williams—director of cyber threat intelligence at scythe—shares why security controls are important for both cyber and. In this guide to security controls validation, we delve into the nuts and bolts of security controls. Continuous security validation will help. Security Control Validation.