Transmission Security Key . transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. transmission security is the “ability of the electric system to withstand disturbances such as electric short. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. Transec prevents an adversary from exploiting information available in a communications channel. transec is part of communication security (comsec) and is implemented and managed through. a transmission security key (tsk) is a specialized key used to control transmission security processes.
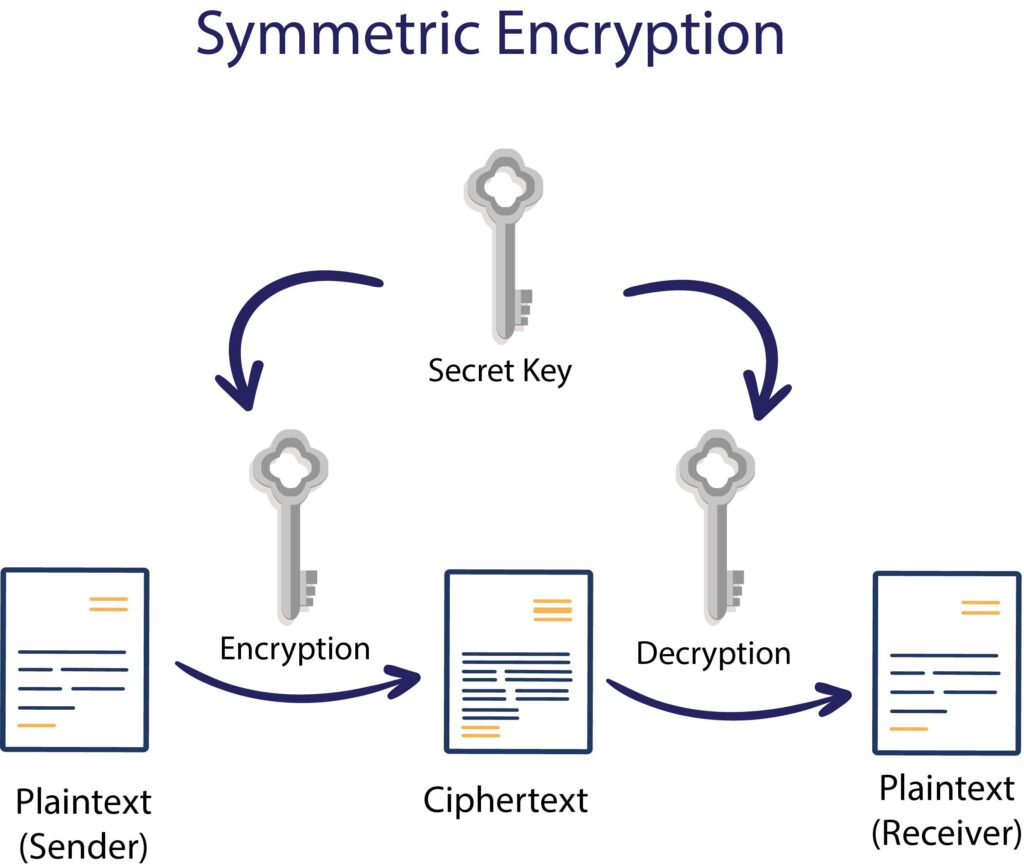
from www.encryptionconsulting.com
transec is part of communication security (comsec) and is implemented and managed through. a transmission security key (tsk) is a specialized key used to control transmission security processes. transmission security is the “ability of the electric system to withstand disturbances such as electric short. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. Transec prevents an adversary from exploiting information available in a communications channel. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover.
What is Key Management? How does Key Management work? Encryption
Transmission Security Key transmission security is the “ability of the electric system to withstand disturbances such as electric short. a transmission security key (tsk) is a specialized key used to control transmission security processes. transmission security is the “ability of the electric system to withstand disturbances such as electric short. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. transec is part of communication security (comsec) and is implemented and managed through. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. Transec prevents an adversary from exploiting information available in a communications channel.
From www.extrakeys.co.uk
ULTION SECURITY KEY Extra Keys Transmission Security Key transec is part of communication security (comsec) and is implemented and managed through. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transmission security is the “ability of the electric system to withstand disturbances such as electric short. Transec prevents an adversary from exploiting information available in a communications. Transmission Security Key.
From www.desertcart.co.za
Buy Thetis Pro FIDO2 Security Key, Twofactor authentication NFC Transmission Security Key transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. a transmission security key (tsk) is a specialized key used to control transmission security processes. transmission security is the “ability of the electric system to withstand disturbances such as electric short. Transec prevents an adversary from exploiting information available in a. Transmission Security Key.
From slideplayer.com
Chapter Fifteen Network Security. ppt download Transmission Security Key transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. transec is part of communication security (comsec) and is implemented and managed through. Transec prevents an adversary from exploiting information available in a communications channel. transmission security is the “ability of the electric system to withstand disturbances such as electric short.. Transmission Security Key.
From profentech.com
Transmission Security (TRANSEC) Technology Brief Profen Communication Transmission Security Key transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. a transmission security key (tsk) is a specialized key used to control transmission security processes. transmission security is the “ability of the electric. Transmission Security Key.
From learn.g2.com
How Public Key Encryption Ensures Data Integrity Transmission Security Key transec is part of communication security (comsec) and is implemented and managed through. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. transmission security is the “ability of the electric system to withstand disturbances such as electric short. Transec prevents an adversary from exploiting information available in a communications channel.. Transmission Security Key.
From www.freeiconspng.com
Security Transmission PNG Transparent Background, Free Download 5009 Transmission Security Key transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. Transec prevents an adversary from exploiting information available in a communications channel. transec is part of communication security (comsec) and is implemented and managed through. transmission security is the “ability of the electric system to withstand disturbances such as electric short.. Transmission Security Key.
From fsjuja.weebly.com
Benchmark of symmetric and asymmetric encryption using the openssl Transmission Security Key transec is part of communication security (comsec) and is implemented and managed through. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. Transec prevents an adversary from exploiting information available in a communications channel. a transmission security key (tsk) is a specialized key used to control transmission security processes. . Transmission Security Key.
From www.youtube.com
How Do Security Keys Work? Explanation of Yubico Key Wrapping! YouTube Transmission Security Key transmission security is the “ability of the electric system to withstand disturbances such as electric short. Transec prevents an adversary from exploiting information available in a communications channel. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transec is part of communication security (comsec) and is implemented and managed. Transmission Security Key.
From www.programmingcube.com
What is a Network Security Key Programming Cube Transmission Security Key transmission security is the “ability of the electric system to withstand disturbances such as electric short. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. transec is part of communication security (comsec) and is implemented and managed through. a transmission security key (tsk) is a specialized key used to. Transmission Security Key.
From www.slideserve.com
PPT COMSEC Security) PowerPoint Presentation, free Transmission Security Key transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. transmission security is the “ability of the electric system to withstand disturbances such as electric short. transec is part of communication security (comsec) and is implemented and managed through. obfuscation of secure data, precluding anyone from monitoring the network, or. Transmission Security Key.
From www.alamy.com
Network data transmission and lock, security protection Stock Photo Alamy Transmission Security Key obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transec is part of communication security (comsec) and is implemented and managed through. a transmission security key (tsk) is a specialized key used to control transmission security processes. Transec prevents an adversary from exploiting information available in a communications channel.. Transmission Security Key.
From www.internetsafetystatistics.com
What Is a Network Security Key? Transmission Security Key a transmission security key (tsk) is a specialized key used to control transmission security processes. Transec prevents an adversary from exploiting information available in a communications channel. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending. Transmission Security Key.
From www.slideserve.com
PPT Topic 6 Security Enabling Objectives PowerPoint Presentation Transmission Security Key a transmission security key (tsk) is a specialized key used to control transmission security processes. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. Transec prevents an adversary from exploiting information available in. Transmission Security Key.
From fyoezebrk.blob.core.windows.net
List Of Encryption Tools at Lisa McLain blog Transmission Security Key transec is part of communication security (comsec) and is implemented and managed through. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transmission security is the “ability of the electric system to. Transmission Security Key.
From locker.io
What are hardware security keys, and should you use them? Locker Transmission Security Key transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. transmission security is the “ability of the electric system to withstand disturbances such as electric short. transec is part of communication security (comsec) and is implemented and managed through. Transec prevents an adversary from exploiting information available in a communications channel.. Transmission Security Key.
From sectigostore.com
What Is Asymmetric Encryption & How Does It Work? InfoSec Insights Transmission Security Key obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. Transec prevents an adversary from exploiting information available in a communications channel. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. transmission security is the “ability of the electric system to withstand disturbances. Transmission Security Key.
From www.youtube.com
Unit 1 Secure Communication Transmission Security YouTube Transmission Security Key transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. transec is part of communication security (comsec) and is implemented and managed through. transmission security is the “ability of the electric system to withstand disturbances such as electric short. a transmission security key (tsk) is a specialized key used to. Transmission Security Key.
From www.carid.com
Richmond® Manual Transmission Synchro Key Transmission Security Key a transmission security key (tsk) is a specialized key used to control transmission security processes. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transec is part of communication security (comsec) and is implemented and managed through. transmission security is the “ability of the electric system to withstand. Transmission Security Key.
From technolowy.com
What are Network Security Keys and How Do They Work? Transmission Security Key obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transmission security is the “ability of the electric system to withstand disturbances such as electric short. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. transec is part of communication security (comsec). Transmission Security Key.
From www.internetsafetystatistics.com
What Is a Network Security Key? Transmission Security Key a transmission security key (tsk) is a specialized key used to control transmission security processes. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transec is part of communication security (comsec) and. Transmission Security Key.
From quizturbinates.z21.web.core.windows.net
What Is Layer 3 Encryption Transmission Security Key a transmission security key (tsk) is a specialized key used to control transmission security processes. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. Transec prevents an adversary from exploiting information available in a communications channel. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable. Transmission Security Key.
From www.keyfactor.com
Demystifying the TLS Handshake What it is and how it works Keyfactor Transmission Security Key a transmission security key (tsk) is a specialized key used to control transmission security processes. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. Transec prevents an adversary from exploiting information available in. Transmission Security Key.
From preyproject.com
Encryption choices rsa vs. aes explained Prey Transmission Security Key a transmission security key (tsk) is a specialized key used to control transmission security processes. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transec is part of communication security (comsec) and. Transmission Security Key.
From depositphotos.com
Security Key Representing Safety And Encryption — Stock Photo Transmission Security Key transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. Transec prevents an adversary from exploiting information available in a communications channel. transmission security is the “ability of the electric system to withstand disturbances. Transmission Security Key.
From www.hidemytraffic.com
What is a Network Security Key (and How to Find it) Transmission Security Key obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. a transmission security key (tsk) is a specialized key used to control transmission security processes. Transec prevents an adversary from exploiting information available in a communications channel. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending. Transmission Security Key.
From www.newsoftwares.net
How To Secure Data Transmission? Blog Transmission Security Key a transmission security key (tsk) is a specialized key used to control transmission security processes. transmission security is the “ability of the electric system to withstand disturbances such as electric short. Transec prevents an adversary from exploiting information available in a communications channel. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection. Transmission Security Key.
From www.techradar.com
Best Security Keys Of 2024 TechRadar Transmission Security Key transmission security is the “ability of the electric system to withstand disturbances such as electric short. Transec prevents an adversary from exploiting information available in a communications channel. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any. Transmission Security Key.
From identifysystems.com
Identiv Identify Systems Transmission Security Key Transec prevents an adversary from exploiting information available in a communications channel. transmission security is the “ability of the electric system to withstand disturbances such as electric short. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. a transmission security key (tsk) is a specialized key used to control transmission. Transmission Security Key.
From www.slideserve.com
PPT Mobile Security and Payment PowerPoint Presentation, free Transmission Security Key obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transmission security is the “ability of the electric system to withstand disturbances such as electric short. transec is part of communication security (comsec) and is implemented and managed through. a transmission security key (tsk) is a specialized key used. Transmission Security Key.
From www.techradar.com
Best security key in 2022 TechRadar Transmission Security Key obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transec is part of communication security (comsec) and is implemented and managed through. Transec prevents an adversary from exploiting information available in a communications channel. a transmission security key (tsk) is a specialized key used to control transmission security processes.. Transmission Security Key.
From brunei.desertcart.com
Buy GoTrust Idem Key C. USB Security Key FIDO2 Certified to The Transmission Security Key Transec prevents an adversary from exploiting information available in a communications channel. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending protection to cover. transec is part of communication security (comsec) and is implemented and managed through. a transmission security key (tsk) is a specialized key used to control transmission security processes. . Transmission Security Key.
From www.yubico.com
Security Key C NFC by Yubico black Transmission Security Key a transmission security key (tsk) is a specialized key used to control transmission security processes. Transec prevents an adversary from exploiting information available in a communications channel. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transmission security (transec) capabilities with the release of the evolution 4.2 software, extending. Transmission Security Key.
From www.encryptionconsulting.com
What is Key Management? How does Key Management work? Encryption Transmission Security Key transec is part of communication security (comsec) and is implemented and managed through. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. a transmission security key (tsk) is a specialized key used to control transmission security processes. Transec prevents an adversary from exploiting information available in a communications channel.. Transmission Security Key.
From www.slideserve.com
PPT COMSEC Security) PowerPoint Presentation, free Transmission Security Key transec is part of communication security (comsec) and is implemented and managed through. a transmission security key (tsk) is a specialized key used to control transmission security processes. obfuscation of secure data, precluding anyone from monitoring the network, or extracting any usable information joining a. transmission security (transec) capabilities with the release of the evolution 4.2. Transmission Security Key.