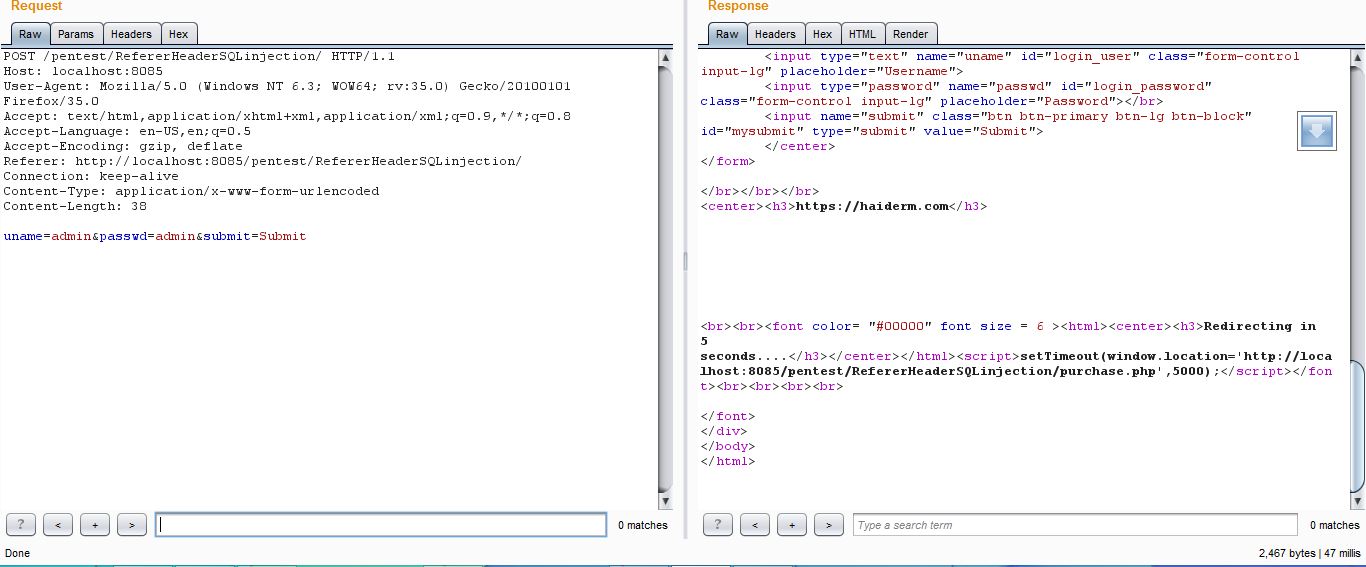
Header Injection Example . Finally, we will see how to protect against them. To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application.
from haiderm.com
To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. Finally, we will see how to protect against them. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application.
HTTP header Blind SQL injection Example
Header Injection Example Finally, we will see how to protect against them. Finally, we will see how to protect against them. To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful.
From mulesy.com
Header Injection Policy MuleSoft API Manager Policy Header Injection Example Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. You probably did not hear about this injection because it is not too popular, despite the fact that. Header Injection Example.
From github.com
GitHub DinoChiesa/ApigeeHeaderInjectionExample Header Injection Example In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. Finally, we will see how to protect against them. To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. You. Header Injection Example.
From haiderm.com
HTTP header Blind SQL injection Example Header Injection Example To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. In this story i will explain briefly what. Header Injection Example.
From haiderm.com
HTTP header Blind SQL injection Example Header Injection Example In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. Finally, we will see how to protect against them. To prevent host header injection attacks, it is. Header Injection Example.
From try4try4try.blogspot.com
bWAPP Mail Header Injection [ SMTP ] Header Injection Example You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. To prevent host header injection attacks, it is important to follow secure coding practices and. Header Injection Example.
From mulesy.com
Header Injection Policy MuleSoft API Manager Policy Header Injection Example Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. Finally, we will see how to protect against them. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. To prevent host header injection attacks, it is important. Header Injection Example.
From cyberdaily.securelayer7.net
Making response queue poisoning crucial for HTTP header injection The Header Injection Example You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. Finally, we will see how to protect against them. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. To prevent host header injection attacks, it is. Header Injection Example.
From www.youtube.com
Host Header Injection Password Reset Poisoning Detailed Explanation Header Injection Example To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. Host header injection occurs when an attacker exploits weaknesses in. Header Injection Example.
From medium.com
List Host header injection Curated by ParagBagul Medium Header Injection Example In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. Finally, we will see how to protect against them. You probably did not hear about this injection because. Header Injection Example.
From haiderm.com
HTTP header Blind SQL injection Example Header Injection Example Finally, we will see how to protect against them. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. You probably did not hear about this injection because. Header Injection Example.
From www.wallarm.com
What is Email Injection?💉Examples & Prevention Header Injection Example To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. Host header injection occurs when an attacker exploits weaknesses in. Header Injection Example.
From haiderm.com
HTTP header Blind SQL injection Example Header Injection Example To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. You probably did not hear about this injection. Header Injection Example.
From www.youtube.com
Host Header Injection Attack Authentication Bypass bugbounty Header Injection Example Finally, we will see how to protect against them. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. You. Header Injection Example.
From binfintech.com
Host Header Injection How to Attack the Header of a Request Header Injection Example You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. Finally, we will see how to protect. Header Injection Example.
From medium.com
Understanding Host Header Injection Attacks and How to Prevent Them Header Injection Example In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. Finally, we will see how to protect against them. Host header injection occurs when an attacker exploits. Header Injection Example.
From github.com
Host header injection in the password reset · Advisory · pimcore/admin Header Injection Example Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. Finally, we will see how to protect against them. In this story i will explain. Header Injection Example.
From haiderm.com
HTTP header Blind SQL injection Example Header Injection Example You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. Finally, we will see how to protect against them. In this story i will explain. Header Injection Example.
From medium.com
Understanding Host Header Injection Script to Detect Vulnerability and Header Injection Example Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. To prevent host header injection attacks, it is important to follow secure coding practices and configure your web. Header Injection Example.
From www.youtube.com
How to HTTP Header Injection Manual and Burp suite online YouTube Header Injection Example In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. You probably did not hear about this injection because it. Header Injection Example.
From www.pdfprof.com
http response header injection exploit Header Injection Example To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. In this story i will explain briefly. Header Injection Example.
From haiderm.com
HTTP header Blind SQL injection Example Header Injection Example In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. Finally, we will see how to protect against them. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. You probably did not hear about this injection because. Header Injection Example.
From www.ubsecure.jp
HTTPヘッダインジェクション【HTTP Header Injection】とは|図でわかる脆弱性の仕組み ユービーセキュア Header Injection Example You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. In this story i will explain briefly. Header Injection Example.
From securitycipher.medium.com
2 Host Header Injection — Secure Code Explain by Piyush Kumawat Header Injection Example Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. To prevent host header injection attacks, it is important to follow secure coding practices and. Header Injection Example.
From medium.com
HOST HEADER INJECTION ATTACK Ram Kumar Medium Header Injection Example Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. Finally, we will see how to protect against them. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. To prevent host header injection attacks,. Header Injection Example.
From www.youtube.com
Host Header Injection Attack Authentication Bypass YouTube Header Injection Example Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. In this story i will explain briefly what. Header Injection Example.
From whatismyipaddress.com
SQL Injection What It Is and How Does It Work Header Injection Example To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. Finally, we will see how to protect against them. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or. Header Injection Example.
From mulesy.com
Header Injection Policy MuleSoft API Manager Policy Header Injection Example You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value. Header Injection Example.
From www.researchgate.net
(PDF) Email Header Injection Vulnerabilities Header Injection Example Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. Finally, we will see how to protect against them. In this story i will explain. Header Injection Example.
From www.acunetix.com
What is HTTP header injection Header Injection Example To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. In this story i will explain briefly. Header Injection Example.
From mulesy.com
Header Injection Policy MuleSoft API Manager Policy Header Injection Example Finally, we will see how to protect against them. To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or. Header Injection Example.
From aithietke.com
Làm sao để phòng tránh lỗ hổng "Host header injection" AI Design Header Injection Example Finally, we will see how to protect against them. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. You probably did not hear about this injection because. Header Injection Example.
From medium.com
List host header injection Curated by Pavanbovilla Medium Header Injection Example In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. Finally, we will see how to protect against them. Host header injection occurs when an attacker exploits. Header Injection Example.
From www.youtube.com
Host Header Injection in Hindi What is Host Header Injection? How Header Injection Example You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. In this story i will explain briefly what the host header is, how vulnerabilities can arise, then give several examples. To prevent host header injection attacks, it is important to follow secure coding practices and configure your. Header Injection Example.
From www.hackingtruth.in
host header injection explain with practical Header Injection Example To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. Host header injection occurs when an attacker exploits weaknesses in the handling of the host header value by the server or application. You probably did not hear about this injection. Header Injection Example.
From mulesy.com
Header Injection Policy MuleSoft API Manager Policy Header Injection Example To prevent host header injection attacks, it is important to follow secure coding practices and configure your web server to use strict parsing rules and ignore unexpected host header values. You probably did not hear about this injection because it is not too popular, despite the fact that attacks can be very impactful. Finally, we will see how to protect. Header Injection Example.