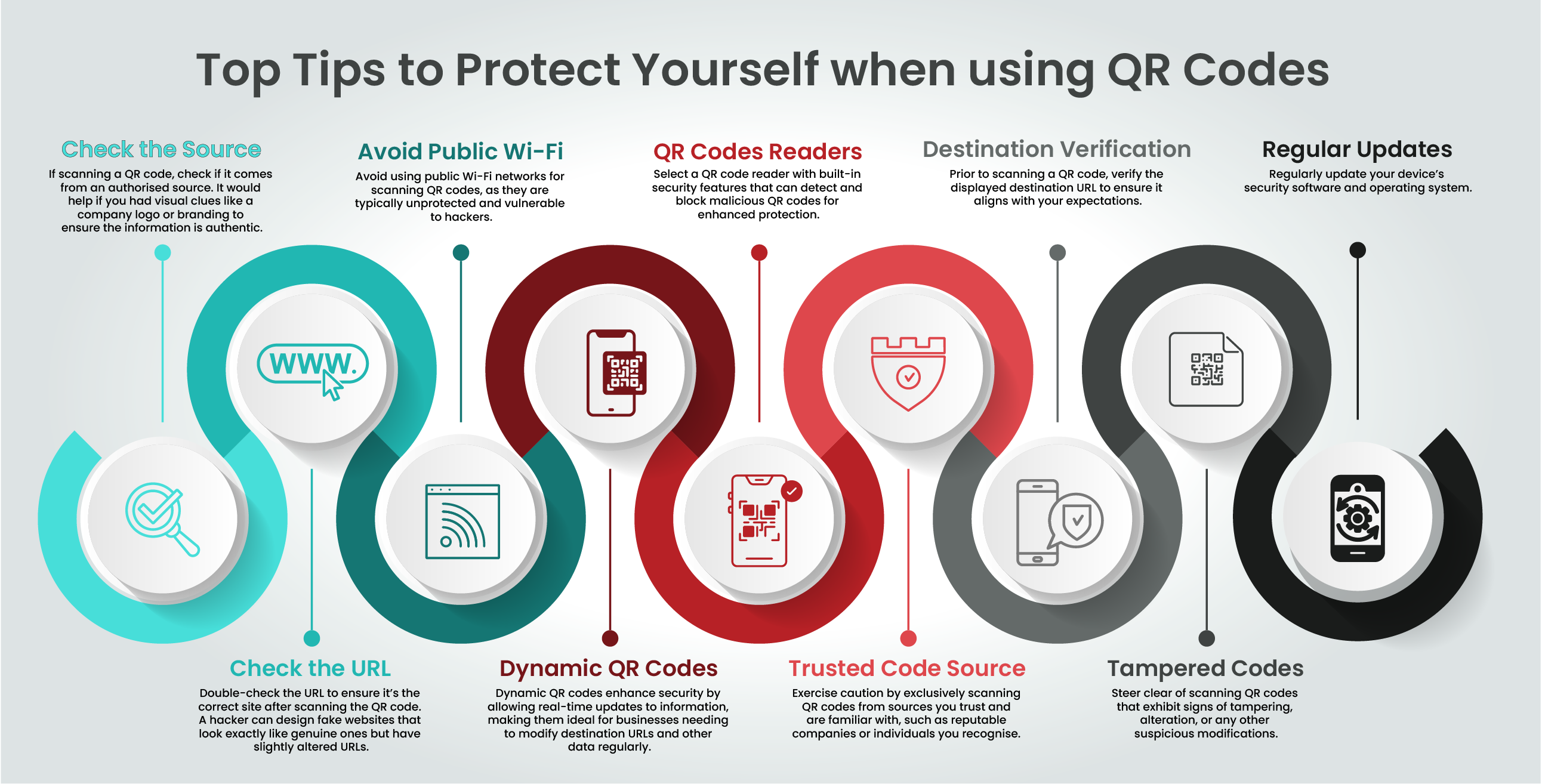
Qr Code Security System . Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. Attackers are taking advantage of the increased use of qr codes to steal sensitive information or conduct phishing campaigns. 7 qr code security best practices. This data can be in the form of a website url, a pdf file, landing page, questionnaire, video or audio, and more. Explore qr code security and how to prevent scams. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. As mentioned earlier, qr codes are inherently a secure technology. Manage your security staff from everywhere. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. Qr codes as attack vectors.
from www.onecollab.co.uk
This data can be in the form of a website url, a pdf file, landing page, questionnaire, video or audio, and more. They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. Manage your security staff from everywhere. As mentioned earlier, qr codes are inherently a secure technology. Explore qr code security and how to prevent scams. Qr codes as attack vectors. Attackers are taking advantage of the increased use of qr codes to steal sensitive information or conduct phishing campaigns. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. 7 qr code security best practices.
QR Code Security Risks What You Need to Know OneCollab
Qr Code Security System Attackers are taking advantage of the increased use of qr codes to steal sensitive information or conduct phishing campaigns. Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. Qr codes as attack vectors. They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. Explore qr code security and how to prevent scams. Manage your security staff from everywhere. This data can be in the form of a website url, a pdf file, landing page, questionnaire, video or audio, and more. Attackers are taking advantage of the increased use of qr codes to steal sensitive information or conduct phishing campaigns. 7 qr code security best practices. As mentioned earlier, qr codes are inherently a secure technology. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes.
From www.youtube.com
QR Code Based Door Lock Access Control System for Visitors QR Code Qr Code Security System As mentioned earlier, qr codes are inherently a secure technology. 7 qr code security best practices. Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. Qr codes as attack vectors. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device.. Qr Code Security System.
From www.youtube.com
QR Code Checkpoint for Security Patrol Marki Solution YouTube Qr Code Security System Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. Qr codes as attack vectors. Explore qr code security and how to prevent scams. Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. They simply direct users to the data. Qr Code Security System.
From www.semanticscholar.org
Figure 1 from Secure QR code system Semantic Scholar Qr Code Security System Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. Attackers are taking advantage of the increased use of qr codes to steal sensitive information or conduct phishing campaigns. They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. 7 qr code security. Qr Code Security System.
From www.qrcodechimp.com
QR Code Security A Complete Guide for Brands and Users Qr Code Security System Qr codes as attack vectors. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. Explore qr code security and how to prevent scams. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. Attackers are taking advantage of the increased use of qr codes to steal. Qr Code Security System.
From civintec.en.made-in-china.com
Qr Code Security System Qr Code Reader 4G IP Network Qr Code Qr Code Security System 7 qr code security best practices. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. They simply direct users to the data encoded within their native smartphone camera apps or. Qr Code Security System.
From www.kaspersky.com
What is a QR code and are they safe? Qr Code Security System With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. This data can be in the form of a website url, a pdf file, landing page, questionnaire, video or audio, and more. Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. Attackers are. Qr Code Security System.
From civintec.en.made-in-china.com
Qr Code Security System Qr Code Reader Qr Code Scanner China Qr Code Security System Manage your security staff from everywhere. 7 qr code security best practices. As mentioned earlier, qr codes are inherently a secure technology. Qr codes as attack vectors. Explore qr code security and how to prevent scams. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. This data can be in the form of a. Qr Code Security System.
From www.invixium.com
QR Code Door Access Control Dynamic Mobile Access QR Code Qr Code Security System Attackers are taking advantage of the increased use of qr codes to steal sensitive information or conduct phishing campaigns. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. As mentioned earlier, qr codes are inherently a secure technology. With consumers and businesses embracing touchless solutions, threat actors also find uses for. Qr Code Security System.
From www.freepik.com
Premium Vector Isometric style illustration of how to open locker Qr Code Security System Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. This data can be in the form of a website url, a pdf file, landing page, questionnaire, video or audio, and more. Manage your security staff from everywhere. As mentioned earlier, qr codes are inherently a secure technology. With. Qr Code Security System.
From www.mdpi.com
Information Free FullText Security and Privacy of QR Code Qr Code Security System Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. Manage your security staff from everywhere. Explore qr code security and how to prevent scams. With consumers and businesses embracing touchless. Qr Code Security System.
From portswigger.net
QR code security Best approaches to using the technology safely and Qr Code Security System With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. Qr codes as attack vectors. Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. Explore. Qr Code Security System.
From hsysecurity.com
1D 2D QR Code Wiegand Scanner Barcode Reader HSY Security HSY Security Qr Code Security System Manage your security staff from everywhere. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. This data can be in the form of a website url, a pdf file, landing page, questionnaire, video or audio, and more. Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for. Qr Code Security System.
From rakinda.com
RD006 QR Code Access Control System with IC card Reader Qr Code Security System They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. As mentioned earlier, qr codes are inherently a secure technology. Explore qr code security and how to prevent scams. Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. Manage. Qr Code Security System.
From www.qrcodechimp.com
QR Code Security A Complete Guide for Brands and Users Qr Code Security System Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. Qr codes as attack vectors. 7 qr code security best practices. With consumers and businesses embracing touchless solutions, threat actors also. Qr Code Security System.
From www.epicbrander.com
QR Code Security and Privacy The Complete & Updated 2023 Guide Qr Code Security System Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. Manage your security staff from everywhere. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. This data. Qr Code Security System.
From cybernews.com
Be careful when you scan QR codes Cybernews Qr Code Security System Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. Manage your security staff from everywhere. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. Explore qr code security and how to prevent scams. As mentioned earlier, qr codes are inherently a secure technology. 7 qr. Qr Code Security System.
From transmitsecurity.com
What is a QR Code? Transmit Security Qr Code Security System This data can be in the form of a website url, a pdf file, landing page, questionnaire, video or audio, and more. As mentioned earlier, qr codes are inherently a secure technology. Qr codes as attack vectors. Attackers are taking advantage of the increased use of qr codes to steal sensitive information or conduct phishing campaigns. 7 qr code security. Qr Code Security System.
From www.epicbrander.com
QR Code Security Best Practices The Ultimate 2024 Guide Qr Code Security System With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. As mentioned earlier, qr codes are inherently a secure technology. Manage your security staff from everywhere. 7 qr code security best practices. Explore qr code security. Qr Code Security System.
From www.qrcodechimp.com
QR Code Security A Complete Guide for Brands and Users Qr Code Security System Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. This data can be in the form of a website url, a pdf file, landing page, questionnaire, video or audio, and more. They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. Attackers. Qr Code Security System.
From www.jotform.com
How secure are QR codes? The Jotform Blog Qr Code Security System They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. 7 qr code security best practices. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. Qr codes as attack vectors. Explore qr code security and how to prevent scams. This data can be in the. Qr Code Security System.
From www.qrcodechimp.com
QR Code Security A Complete Guide for Brands and Users Qr Code Security System With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. Qr codes as attack vectors. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. Manage your security staff from everywhere. As mentioned earlier, qr codes are inherently a secure technology. Qr code access control empowers tenants. Qr Code Security System.
From www.qrpatrol.com
How to use QRPatrol (infographic) QRPatrol Real Time and Online Qr Code Security System With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. Attackers are taking advantage of the increased use of qr codes to steal sensitive information or conduct phishing campaigns. 7 qr code security best practices. Manage your security staff from everywhere. This data can be in the form of a website url, a pdf file,. Qr Code Security System.
From www.onecollab.co.uk
QR Code Security Risks What You Need to Know OneCollab Qr Code Security System They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. Qr codes as attack vectors. Attackers are taking advantage of the increased use of qr codes to steal sensitive information or conduct phishing campaigns. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your. Qr Code Security System.
From www.alamy.com
Mobile verification system and QR code scanning security technology Qr Code Security System Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. 7 qr code security best practices. This data can be in the form of a website url, a pdf file, landing page, questionnaire, video or audio, and more. Explore qr code security and how to prevent scams. Manage your. Qr Code Security System.
From qrcodesaustralia.com.au
QR Code Security QR Codes Australia Qr Code Security System They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. Manage your security staff from everywhere. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. This data. Qr Code Security System.
From www.nanomatrixsecure.com
The Complete Guide to QR Code Security Qr Code Security System Manage your security staff from everywhere. Attackers are taking advantage of the increased use of qr codes to steal sensitive information or conduct phishing campaigns. As mentioned earlier, qr codes are inherently a secure technology. Explore qr code security and how to prevent scams. 7 qr code security best practices. Threat actors clone an authentic qr code that redirects you. Qr Code Security System.
From www.abijita.com
How Secure Are QR Codes? Qr Code Security System Manage your security staff from everywhere. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. As mentioned earlier, qr codes are inherently a secure technology. This data can be in the form of a website url, a pdf file, landing page, questionnaire, video or audio, and more. 7 qr code security best practices. Qr. Qr Code Security System.
From www.alibaba.com
QR Code Scanner Gate Access Control System Qr Code Security System With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. Attackers are taking advantage of the increased use of qr codes to steal sensitive information or conduct phishing campaigns. As mentioned earlier, qr codes are inherently a secure technology. Manage your security staff from everywhere. Qr code access control empowers tenants and visitors to scan. Qr Code Security System.
From civintec.en.made-in-china.com
Qr Code Security System Qr Code Reader 4G IP Network Qr Code Qr Code Security System Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. This data can be in the form of a website url, a pdf file, landing page, questionnaire, video or audio, and more. Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure. Qr Code Security System.
From sites.google.com
Funlux 4CH 960H+600TVL Security System, P2P, QRCode Connection, 500GB Qr Code Security System Qr codes as attack vectors. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. As mentioned earlier, qr codes are inherently a secure technology. Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. Manage your security staff from everywhere. 7 qr code. Qr Code Security System.
From www.teamgo.co
QR Codes for Instant Visitor Checkin Qr Code Security System With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. As mentioned earlier, qr codes are inherently a secure technology. Explore qr code security and how to prevent scams. This data can be in the form of. Qr Code Security System.
From www.diytrade.com
qr code entry system CXT (China Manufacturer) Access Control System Qr Code Security System Attackers are taking advantage of the increased use of qr codes to steal sensitive information or conduct phishing campaigns. As mentioned earlier, qr codes are inherently a secure technology. 7 qr code security best practices. They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. Qr code access control empowers tenants. Qr Code Security System.
From www.1tapcard.one
Top 5 Things You Should Know About QR Code Security 1Tapcard Qr Code Security System They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. Qr codes as attack vectors. As mentioned earlier, qr codes are inherently a secure technology. Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. Manage your security staff from. Qr Code Security System.
From bumppy.com
QR Code Security What are QR Codes and How do QR Codes work Bumppy Qr Code Security System Qr codes as attack vectors. They simply direct users to the data encoded within their native smartphone camera apps or standalone qr code readers. Threat actors clone an authentic qr code that redirects you to a malicious site or infects your device. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. Manage your security. Qr Code Security System.
From www.demandtalk.com
QR Code Security A Concern Introduction DemandTalk Qr Code Security System Qr codes as attack vectors. Qr code access control empowers tenants and visitors to scan a qr code on their smartphones for quick and secure access. Explore qr code security and how to prevent scams. With consumers and businesses embracing touchless solutions, threat actors also find uses for qr codes. 7 qr code security best practices. As mentioned earlier, qr. Qr Code Security System.