What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy . Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. The nat policy elements must all reference the original packet, so don’t think about where you want the packet to go, but rather. This section discusses how to write security policies when a translation of ip addresses is. How to add groups to security policy. Then the nat policy lookup is 2nd (dnat. Security policies with nated ip addresses. Security objectives and operational security rules, which together. In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. Of the order you mentioned, the route lookup is done 1st (forwarding lookup). When the traffic matches a policy rule, the defined action is triggered and all subsequent policies are disregarded. What is the order of opertaion when it comes to source nat and security policy on srx ? The evaluation order of the rules is:
from readiness.solutions
Then the nat policy lookup is 2nd (dnat. The evaluation order of the rules is: Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. The nat policy elements must all reference the original packet, so don’t think about where you want the packet to go, but rather. Of the order you mentioned, the route lookup is done 1st (forwarding lookup). Security objectives and operational security rules, which together. How to add groups to security policy. This section discusses how to write security policies when a translation of ip addresses is. Security policies with nated ip addresses. What is the order of opertaion when it comes to source nat and security policy on srx ?
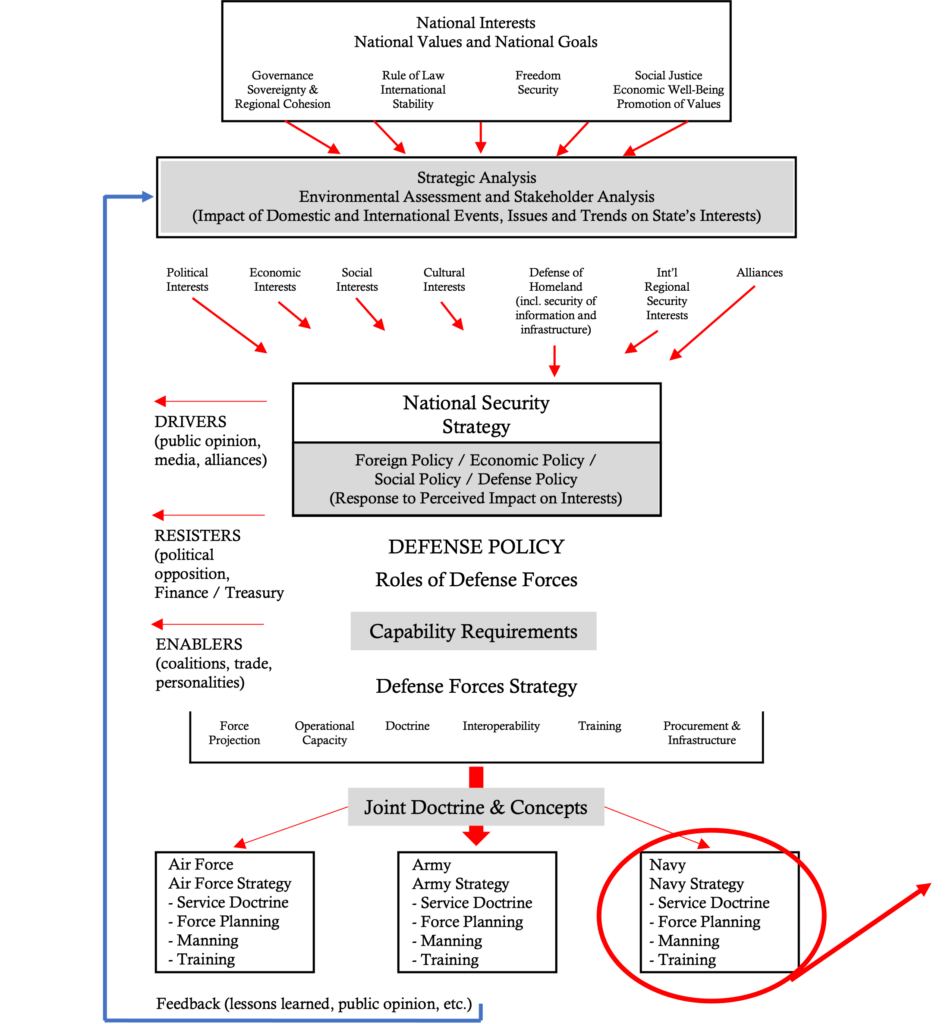
2a National Security Framework
What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy This section discusses how to write security policies when a translation of ip addresses is. Of the order you mentioned, the route lookup is done 1st (forwarding lookup). This section discusses how to write security policies when a translation of ip addresses is. Then the nat policy lookup is 2nd (dnat. In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. Security policies with nated ip addresses. How to add groups to security policy. The evaluation order of the rules is: Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. Security objectives and operational security rules, which together. The nat policy elements must all reference the original packet, so don’t think about where you want the packet to go, but rather. What is the order of opertaion when it comes to source nat and security policy on srx ? When the traffic matches a policy rule, the defined action is triggered and all subsequent policies are disregarded.
From sprinto.com
What is Security Policy? (Creation & Examples) Sprinto What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. This section discusses how to write security policies when a translation of ip addresses is. The nat policy elements must all reference the original packet, so don’t think about where you want the packet to go, but rather.. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From atriade.com
7 Elements of Effective Security Plan Security Plan Components Atriade What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy How to add groups to security policy. Security objectives and operational security rules, which together. This section discusses how to write security policies when a translation of ip addresses is. In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. Then the nat policy lookup is 2nd (dnat.. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From securitypolicyzenchiba.blogspot.com
Security Policy Security Policy Framework What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Security policies with nated ip addresses. What is the order of opertaion when it comes to source nat and security policy on srx ? Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.ccsinet.com
Policy and Procedures Security Compliance What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy The nat policy elements must all reference the original packet, so don’t think about where you want the packet to go, but rather. Then the nat policy lookup is 2nd (dnat. The evaluation order of the rules is: In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can.. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From barokoks.github.io
Security Requirements Check List for Information TECHNOLOGY and What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. Security policies with nated ip addresses. This section discusses how to write security policies when a translation of ip addresses is. What is the order of opertaion when it comes to source nat and security policy on srx ? Security objectives and operational security. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.slideteam.net
Risk Assessment Flowchart For Cyber Security Management What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy What is the order of opertaion when it comes to source nat and security policy on srx ? Security policies with nated ip addresses. The nat policy elements must all reference the original packet, so don’t think about where you want the packet to go, but rather. In this lab, you will allow network traffic from the users_net security zone. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.sampletemplates.com
Sample IT Security Policy Template 9+ Free Documents Download in Word What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy What is the order of opertaion when it comes to source nat and security policy on srx ? Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. Security objectives and operational security rules, which together. Of the order you mentioned, the route lookup is done 1st (forwarding lookup). Then the nat policy lookup. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.sxlixintex.com
Types of Security Policy bartleby What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy What is the order of opertaion when it comes to source nat and security policy on srx ? How to add groups to security policy. Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. Security policies with nated ip addresses. Then the nat policy lookup is 2nd (dnat. The evaluation order of the. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.alpinesecurity.com
How to Perform a Cybersecurity Risk Assessment A StepbyStep Guide What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy What is the order of opertaion when it comes to source nat and security policy on srx ? How to add groups to security policy. In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. This section discusses how to write security policies when a translation of ip. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.scribd.com
Information Security Policy Checklist Information Security Online What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy The evaluation order of the rules is: How to add groups to security policy. Security policies with nated ip addresses. When the traffic matches a policy rule, the defined action is triggered and all subsequent policies are disregarded. Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. This section discusses how to write. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.examples.com
Security Policy 16+ Examples, Format, Pdf What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. Security objectives and operational security rules, which together. What is the order of opertaion when it comes to source nat and security policy on srx ? How to add groups to security policy. Then the nat policy lookup. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From sprinto.com
10 Most Important Elements of Information Security Policy Sprinto What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy The evaluation order of the rules is: What is the order of opertaion when it comes to source nat and security policy on srx ? Of the order you mentioned, the route lookup is done 1st (forwarding lookup). In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can.. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.reflectiz.com
The Complete List of Data Security Standards Reflectiz What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. Security objectives and operational security rules, which together. In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. Security policies with nated ip addresses. The nat policy elements must all reference the. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.examples.com
Security Policy 16+ Examples, Format, Pdf What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy The evaluation order of the rules is: What is the order of opertaion when it comes to source nat and security policy on srx ? Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. When the traffic matches a policy rule, the defined action is triggered and all subsequent policies are disregarded. How. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From totalsecurityadvisor.blr.com
An 8Step Process for Facility Security Risk Assessment Total What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy This section discusses how to write security policies when a translation of ip addresses is. Security objectives and operational security rules, which together. Security policies with nated ip addresses. How to add groups to security policy. The evaluation order of the rules is: The nat policy elements must all reference the original packet, so don’t think about where you want. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From sprinto.com
What is an Information Security Policy and Why is it Important? What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. What is the order of opertaion when it comes to source nat and security policy on srx ? This section discusses how to write security policies when a translation of ip addresses is. Security policies with nated ip addresses. The nat policy elements must. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.researchgate.net
(PDF) EEA guidance document policy evaluation What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Security objectives and operational security rules, which together. Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. Of the order you mentioned, the route lookup is done 1st (forwarding lookup). The. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.ekransystem.com
10 Information Security Policies Organizations Should Implement What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Security objectives and operational security rules, which together. Then the nat policy lookup is 2nd (dnat. Security policies with nated ip addresses. The nat policy elements must all reference the original packet, so don’t think about where you want the packet to go, but rather. Is security policy is evaluated first i.e pre nat src ip is taken into considertaion. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.slideshare.net
Importance Of A Security Policy What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy How to add groups to security policy. In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. Security policies with nated ip addresses. The nat policy elements must all reference the original packet, so don’t think about where you want the packet to go, but rather. When the. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.researchgate.net
Security policyprocedurepractice Download Scientific Diagram What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Then the nat policy lookup is 2nd (dnat. How to add groups to security policy. Security objectives and operational security rules, which together. What is the order of opertaion when it comes to source nat and security policy on srx ? The evaluation order of the rules is: The nat policy elements must all reference the original packet, so don’t. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From noted.kairostay.com
[NS Wk 3] Security Policy and NAT Policy Noted What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Then the nat policy lookup is 2nd (dnat. How to add groups to security policy. Of the order you mentioned, the route lookup is done 1st (forwarding lookup). When the traffic matches a policy rule, the defined action is triggered and all subsequent policies are disregarded. The nat policy elements must all reference the original packet, so don’t think about. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From readiness.solutions
2a National Security Framework What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy This section discusses how to write security policies when a translation of ip addresses is. Security objectives and operational security rules, which together. Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. Security policies with nated ip addresses. In this lab, you will allow network traffic from the users_net security zone to the. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.sampletemplates.com
FREE 8+ Security Policy Samples in MS Word PDF What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy What is the order of opertaion when it comes to source nat and security policy on srx ? How to add groups to security policy. When the traffic matches a policy rule, the defined action is triggered and all subsequent policies are disregarded. Then the nat policy lookup is 2nd (dnat. Security objectives and operational security rules, which together. Of. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.pinterest.com
Security Policy Framework CertMike Work infographic, Technology What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Security objectives and operational security rules, which together. Then the nat policy lookup is 2nd (dnat. In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. Security policies with nated ip addresses. What is the order of opertaion when it comes to source nat and security policy on. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From kyloot.com
What is a Security Policy? Definition, Elements, and Examples (2022) What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy When the traffic matches a policy rule, the defined action is triggered and all subsequent policies are disregarded. This section discusses how to write security policies when a translation of ip addresses is. Then the nat policy lookup is 2nd (dnat. Of the order you mentioned, the route lookup is done 1st (forwarding lookup). Security policies with nated ip addresses.. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From studylib.net
Security Policies, Standards, and Planning What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy This section discusses how to write security policies when a translation of ip addresses is. When the traffic matches a policy rule, the defined action is triggered and all subsequent policies are disregarded. The evaluation order of the rules is: How to add groups to security policy. In this lab, you will allow network traffic from the users_net security zone. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.sampletemplates.com
FREE 8+ Security Policy Samples in MS Word PDF What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy This section discusses how to write security policies when a translation of ip addresses is. Security policies with nated ip addresses. The nat policy elements must all reference the original packet, so don’t think about where you want the packet to go, but rather. In this lab, you will allow network traffic from the users_net security zone to the extranet. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.azets.com
Information security policy requirements What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. This section discusses how to write security policies when a translation of ip addresses is. Of the order you mentioned, the route lookup is done 1st (forwarding lookup). Then the nat policy lookup is 2nd (dnat. The evaluation order of the rules is: When. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From sprinto.com
What is an Information Security Policy and Why is it Important? What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. The evaluation order of the rules is: What is the order of opertaion when it comes to source nat and security policy on srx ? This section discusses how to write security policies when a translation of ip. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.sampletemplates.com
FREE 8+ Security Policy Samples in MS Word PDF What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Security objectives and operational security rules, which together. In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. Is security policy is evaluated first i.e pre nat src ip is taken into considertaion or. When the traffic matches a policy rule, the defined action is triggered and all. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.slideteam.net
Roles And Responsibilities In Information Security Formulating What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy The nat policy elements must all reference the original packet, so don’t think about where you want the packet to go, but rather. Of the order you mentioned, the route lookup is done 1st (forwarding lookup). The evaluation order of the rules is: How to add groups to security policy. Then the nat policy lookup is 2nd (dnat. In this. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.threatanalysis.com
SECURITY RISK MANAGEMENT Threat Analysis Group What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Then the nat policy lookup is 2nd (dnat. The evaluation order of the rules is: Security objectives and operational security rules, which together. What is the order of opertaion when it comes to source nat and security policy on srx ? The nat policy elements must all reference the original packet, so don’t think about where you want the packet. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.upguard.com
What is an Information Security Policy? UpGuard What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy Then the nat policy lookup is 2nd (dnat. Of the order you mentioned, the route lookup is done 1st (forwarding lookup). When the traffic matches a policy rule, the defined action is triggered and all subsequent policies are disregarded. This section discusses how to write security policies when a translation of ip addresses is. In this lab, you will allow. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.slideserve.com
PPT Session 3 Information Security Policies PowerPoint Presentation What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy The evaluation order of the rules is: This section discusses how to write security policies when a translation of ip addresses is. Security objectives and operational security rules, which together. In this lab, you will allow network traffic from the users_net security zone to the extranet security zone so that employees can. The nat policy elements must all reference the. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.
From www.dexform.com
Security policy template in Word and Pdf formats What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy What is the order of opertaion when it comes to source nat and security policy on srx ? This section discusses how to write security policies when a translation of ip addresses is. Security policies with nated ip addresses. Security objectives and operational security rules, which together. Of the order you mentioned, the route lookup is done 1st (forwarding lookup).. What Is The Correct Order Of Evaluation Between The Security Policy And The Nat Policy.