Splunk Stats Bucket By Day . Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2, wd==wednesday,3, wd==thursday,4, wd==friday,5, wd==saturday,6 ,wd. I think we can correct that with stats. To create a splunk count by day chart, you will need to: | eval percent = (count/total)*100. Percentage of search field by day. Create a search that will return the events you want to. Import your data into splunk. The following are examples for using the spl2 stats command. Index=my_index | bucket _time span=day | stats count by _time. The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. Get total counts for each day: To learn more about the stats. I have a search string. Get just errors for each day:
from exofhdaxz.blob.core.windows.net
I think we can correct that with stats. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2, wd==wednesday,3, wd==thursday,4, wd==friday,5, wd==saturday,6 ,wd. Import your data into splunk. To learn more about the stats. The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. I have a search string. Percentage of search field by day. Create a search that will return the events you want to. Get just errors for each day: | eval percent = (count/total)*100.
Splunk Total Number Of Buckets at Norma Andrews blog
Splunk Stats Bucket By Day The following are examples for using the spl2 stats command. The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. Index=my_index | bucket _time span=day | stats count by _time. Get just errors for each day: Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2, wd==wednesday,3, wd==thursday,4, wd==friday,5, wd==saturday,6 ,wd. To create a splunk count by day chart, you will need to: Import your data into splunk. To learn more about the stats. I think we can correct that with stats. Create a search that will return the events you want to. The following are examples for using the spl2 stats command. | eval percent = (count/total)*100. Get total counts for each day: I have a search string. Percentage of search field by day.
From klarxuarr.blob.core.windows.net
Splunk Roll All Buckets at Linda Dicken blog Splunk Stats Bucket By Day Get just errors for each day: The following are examples for using the spl2 stats command. Create a search that will return the events you want to. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2, wd==wednesday,3, wd==thursday,4, wd==friday,5,. Splunk Stats Bucket By Day.
From bertjbrowno.blob.core.windows.net
Splunk Bucket Count By Day at bertjbrowno blog Splunk Stats Bucket By Day To create a splunk count by day chart, you will need to: I think we can correct that with stats. The following are examples for using the spl2 stats command. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2,. Splunk Stats Bucket By Day.
From infohub.delltechnologies.com
Splunk integration best practices Design Guide—Cloud Native Splunk Splunk Stats Bucket By Day | eval percent = (count/total)*100. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2, wd==wednesday,3, wd==thursday,4, wd==friday,5, wd==saturday,6 ,wd. The following are examples for using the spl2 stats command. I think we can correct that with stats. The stats,. Splunk Stats Bucket By Day.
From support.umbrella.com
Configuring Splunk with a S3 Bucket Cisco Umbrella Splunk Stats Bucket By Day To create a splunk count by day chart, you will need to: Import your data into splunk. Get just errors for each day: I think we can correct that with stats. To learn more about the stats. Percentage of search field by day. The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of. Splunk Stats Bucket By Day.
From blog.csdn.net
splunk VS elasticsearchCSDN博客 Splunk Stats Bucket By Day I think we can correct that with stats. | eval percent = (count/total)*100. I have a search string. Percentage of search field by day. To create a splunk count by day chart, you will need to: Create a search that will return the events you want to. Index=my_index | bucket _time span=day | stats count by _time. The stats, streamstats,. Splunk Stats Bucket By Day.
From www.stratosphereips.org
Getting Started With Splunk Basic Searching & Data Viz — Stratosphere IPS Splunk Stats Bucket By Day To create a splunk count by day chart, you will need to: Get total counts for each day: To learn more about the stats. Index=my_index | bucket _time span=day | stats count by _time. I have a search string. The following are examples for using the spl2 stats command. The stats, streamstats, and eventstats commands each enable you to calculate. Splunk Stats Bucket By Day.
From www.youtube.com
Splunk Index buckets. YouTube Splunk Stats Bucket By Day The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2, wd==wednesday,3, wd==thursday,4, wd==friday,5, wd==saturday,6 ,wd. I have a. Splunk Stats Bucket By Day.
From www.tutorialspoint.com
Splunk Stats Command Splunk Stats Bucket By Day Get total counts for each day: | eval percent = (count/total)*100. To create a splunk count by day chart, you will need to: I think we can correct that with stats. Create a search that will return the events you want to. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day. Splunk Stats Bucket By Day.
From community.splunk.com
Chart count with timespan Splunk Community Splunk Stats Bucket By Day Index=my_index | bucket _time span=day | stats count by _time. Get total counts for each day: Percentage of search field by day. | eval percent = (count/total)*100. The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. I think we can correct that with stats. The following are. Splunk Stats Bucket By Day.
From community.splunk.com
Solved Diagrams of how indexing works in the Splunk platf... Splunk Splunk Stats Bucket By Day I have a search string. Create a search that will return the events you want to. To learn more about the stats. The following are examples for using the spl2 stats command. | eval percent = (count/total)*100. Get just errors for each day: I think we can correct that with stats. Percentage of search field by day. Import your data. Splunk Stats Bucket By Day.
From cloudian.com
Splunk Storage Calculator Estimate Your Storage Costs Cloudian Splunk Stats Bucket By Day To create a splunk count by day chart, you will need to: I have a search string. Import your data into splunk. The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. Create a search that will return the events you want to. To learn more about the. Splunk Stats Bucket By Day.
From mindmajix.com
Introduction To Splunk Stats Function Options Splunk Stats Bucket By Day Import your data into splunk. I think we can correct that with stats. Index=my_index | bucket _time span=day | stats count by _time. To learn more about the stats. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2, wd==wednesday,3,. Splunk Stats Bucket By Day.
From docs.splunk.com
stats Splunk Documentation Splunk Stats Bucket By Day To create a splunk count by day chart, you will need to: | eval percent = (count/total)*100. I think we can correct that with stats. I have a search string. The following are examples for using the spl2 stats command. Get total counts for each day: Create a search that will return the events you want to. The stats, streamstats,. Splunk Stats Bucket By Day.
From techbullion.com
What is Splunk? Guide for Beginners TechBullion Splunk Stats Bucket By Day The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. I think we can correct that with stats. Percentage of search field by day. To create a splunk count by day chart, you will need to: Import your data into splunk. Get total counts for each day: To. Splunk Stats Bucket By Day.
From www.youtube.com
Splunk .conf 2016 buckets full of happy tiers YouTube Splunk Stats Bucket By Day The following are examples for using the spl2 stats command. Get just errors for each day: Get total counts for each day: | eval percent = (count/total)*100. The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. To create a splunk count by day chart, you will need. Splunk Stats Bucket By Day.
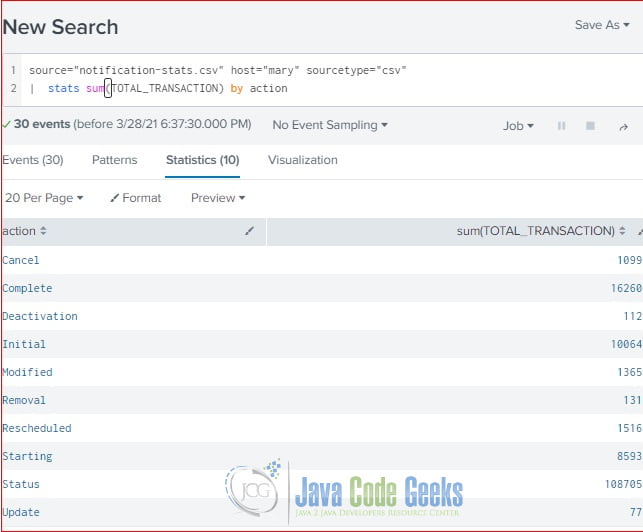
From examples.javacodegeeks.com
Splunk Stats Command Example Java Code Geeks Splunk Stats Bucket By Day | eval percent = (count/total)*100. Percentage of search field by day. Import your data into splunk. I think we can correct that with stats. Index=my_index | bucket _time span=day | stats count by _time. To create a splunk count by day chart, you will need to: Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count). Splunk Stats Bucket By Day.
From www.acte.in
Splunk Timechart Free Guide Tutorial & REALTIME Examples Splunk Stats Bucket By Day Percentage of search field by day. Import your data into splunk. I have a search string. Create a search that will return the events you want to. I think we can correct that with stats. To create a splunk count by day chart, you will need to: Get total counts for each day: | eval percent = (count/total)*100. To learn. Splunk Stats Bucket By Day.
From bceweb.org
Splunk Chart Command A Visual Reference of Charts Chart Master Splunk Stats Bucket By Day I have a search string. Index=my_index | bucket _time span=day | stats count by _time. Import your data into splunk. To create a splunk count by day chart, you will need to: Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval. Splunk Stats Bucket By Day.
From support.umbrella.com
Configuring Splunk with a Selfmanaged S3 Bucket Cisco Umbrella Splunk Stats Bucket By Day To create a splunk count by day chart, you will need to: Get just errors for each day: The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename. Splunk Stats Bucket By Day.
From www.thomashenson.com
5 Types of Buckets in Splunk Thomas Henson Splunk Stats Bucket By Day The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. To create a splunk count by day chart, you will need to: Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day). Splunk Stats Bucket By Day.
From subscription.packtpub.com
Advanced Splunk Splunk Stats Bucket By Day Index=my_index | bucket _time span=day | stats count by _time. Get just errors for each day: I think we can correct that with stats. | eval percent = (count/total)*100. To create a splunk count by day chart, you will need to: Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day |. Splunk Stats Bucket By Day.
From www.youtube.com
Splunk Day Wise or Week Wise Data Comparison Splunk Tutorials Learn Splunk Stats Bucket By Day | eval percent = (count/total)*100. Import your data into splunk. To create a splunk count by day chart, you will need to: Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2, wd==wednesday,3, wd==thursday,4, wd==friday,5, wd==saturday,6 ,wd. Index=my_index | bucket. Splunk Stats Bucket By Day.
From bertjbrowno.blob.core.windows.net
Splunk Bucket Count By Day at bertjbrowno blog Splunk Stats Bucket By Day Get total counts for each day: Index=my_index | bucket _time span=day | stats count by _time. Percentage of search field by day. The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. Create a search that will return the events you want to. | eval percent = (count/total)*100.. Splunk Stats Bucket By Day.
From securitysynapse.blogspot.com
SecuritySynapse Spelunking your Splunk Part V (Splunk Stats) Splunk Stats Bucket By Day | eval percent = (count/total)*100. Get total counts for each day: To learn more about the stats. To create a splunk count by day chart, you will need to: The following are examples for using the spl2 stats command. Import your data into splunk. Percentage of search field by day. Get just errors for each day: Create a search that. Splunk Stats Bucket By Day.
From mindmajix.com
Introduction To Splunk Stats Function Options Splunk Stats Bucket By Day To learn more about the stats. Percentage of search field by day. Get just errors for each day: The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. To create a splunk count by day chart, you will need to: Get total counts for each day: Create a. Splunk Stats Bucket By Day.
From docs.splunk.com
Buckets and indexer clusters Splunk Documentation Splunk Stats Bucket By Day To create a splunk count by day chart, you will need to: I have a search string. I think we can correct that with stats. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2, wd==wednesday,3, wd==thursday,4, wd==friday,5, wd==saturday,6 ,wd.. Splunk Stats Bucket By Day.
From www.pinterest.com
Splunk App for Salesforce Salesforce, Big data analytics, App Splunk Stats Bucket By Day | eval percent = (count/total)*100. I think we can correct that with stats. The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. Get just errors for each day: Create a search that will return the events you want to. To create a splunk count by day chart,. Splunk Stats Bucket By Day.
From klaxqeubd.blob.core.windows.net
Splunk Calculate Bucket Size at Ester Nicholson blog Splunk Stats Bucket By Day Get just errors for each day: I think we can correct that with stats. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2, wd==wednesday,3, wd==thursday,4, wd==friday,5, wd==saturday,6 ,wd. Index=my_index | bucket _time span=day | stats count by _time. The. Splunk Stats Bucket By Day.
From www.youtube.com
Splunk Tutorial For Beginners Stats vs Chart Command in Splunk YouTube Splunk Stats Bucket By Day Create a search that will return the events you want to. The following are examples for using the spl2 stats command. I have a search string. To learn more about the stats. | eval percent = (count/total)*100. Import your data into splunk. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day. Splunk Stats Bucket By Day.
From exobxaozf.blob.core.windows.net
Splunk Wiki Buckets at Esther Marler blog Splunk Stats Bucket By Day Index=my_index | bucket _time span=day | stats count by _time. I have a search string. The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. The following are examples for using the spl2 stats command. Import your data into splunk. Get total counts for each day: I think. Splunk Stats Bucket By Day.
From michaelilhan.blogspot.com
Splunk stacked bar chart MichaelIlhan Splunk Stats Bucket By Day Get total counts for each day: The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. Create a search that will return the events you want to. To create a splunk count by day chart, you will need to: Get just errors for each day: I think we. Splunk Stats Bucket By Day.
From iotloops.com
Discover the Power of RealTime Insights with Splunk Stats Splunk Stats Bucket By Day Index=my_index | bucket _time span=day | stats count by _time. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2, wd==wednesday,3, wd==thursday,4, wd==friday,5, wd==saturday,6 ,wd. Import your data into splunk. Percentage of search field by day. The following are examples. Splunk Stats Bucket By Day.
From exofhdaxz.blob.core.windows.net
Splunk Total Number Of Buckets at Norma Andrews blog Splunk Stats Bucket By Day Get just errors for each day: The stats, streamstats, and eventstats commands each enable you to calculate summary statistics on the results of a search or the events. Index=my_index | bucket _time span=day | stats count by _time. | eval percent = (count/total)*100. I have a search string. The following are examples for using the spl2 stats command. Index=_internal |. Splunk Stats Bucket By Day.
From queirozf.com
Splunk Groupby Examples with Stats Splunk Stats Bucket By Day I think we can correct that with stats. Index=_internal | timechart span=1d count | convert timeformat=%a ctime(_time) as day | stats sum(count) as count by day | rename count as sent | eval wd=lower(day) | eval sort_field=case(wd==monday,1, wd==tuesday,2, wd==wednesday,3, wd==thursday,4, wd==friday,5, wd==saturday,6 ,wd. | eval percent = (count/total)*100. Get just errors for each day: Percentage of search field by day.. Splunk Stats Bucket By Day.
From klarxuarr.blob.core.windows.net
Splunk Roll All Buckets at Linda Dicken blog Splunk Stats Bucket By Day Create a search that will return the events you want to. Import your data into splunk. Get just errors for each day: I have a search string. Percentage of search field by day. To learn more about the stats. To create a splunk count by day chart, you will need to: Get total counts for each day: Index=_internal | timechart. Splunk Stats Bucket By Day.