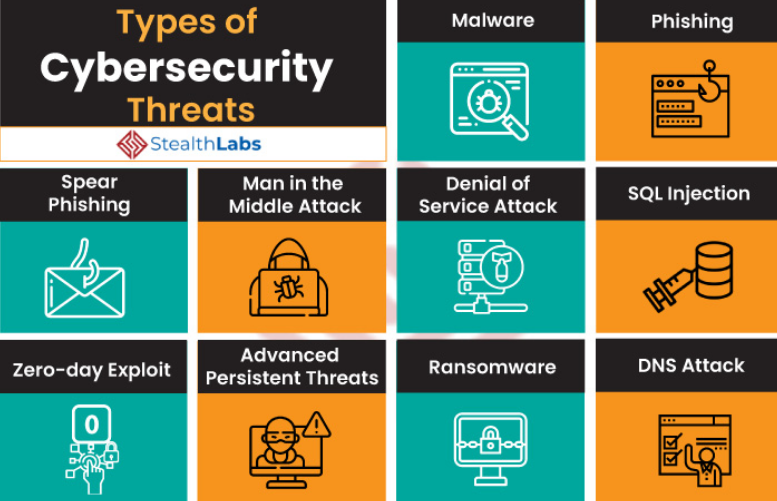
Hardware Cybersecurity Examples . Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices to the global infrastructure. All cyber systems are built using the physical hardware of the semiconductor chips found in all modern electronics, computers,. Meltdown and spectre raised the alarm over vulnerabilities that. As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. By operating at the physical layer, they ensure security against. A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. A guide to the threats. Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity of. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a.
from support.aiesec.org
By operating at the physical layer, they ensure security against. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. All cyber systems are built using the physical hardware of the semiconductor chips found in all modern electronics, computers,. A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. A guide to the threats. Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity of. Meltdown and spectre raised the alarm over vulnerabilities that. Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices to the global infrastructure.
Cyber Security Threats and Attacks AIESEC Help Center
Hardware Cybersecurity Examples Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices to the global infrastructure. Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices to the global infrastructure. Meltdown and spectre raised the alarm over vulnerabilities that. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. By operating at the physical layer, they ensure security against. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. A guide to the threats. All cyber systems are built using the physical hardware of the semiconductor chips found in all modern electronics, computers,. Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity of. As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and.
From geeks.co.uk
How to defend your business against cyber attacks Computer Geeks Hardware Cybersecurity Examples Meltdown and spectre raised the alarm over vulnerabilities that. Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity of. A guide to the threats. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. A common example of hardware security is a device that scans employee endpoints or monitors network. Hardware Cybersecurity Examples.
From tech.co
12 Cyber Security Measures Your Small Business Needs Hardware Cybersecurity Examples Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. By operating at the physical layer, they ensure security against. A common example of hardware security is a device that scans. Hardware Cybersecurity Examples.
From www.slideteam.net
Top 10 Cybersecurity Dashboard Templates With Samples and Examples Hardware Cybersecurity Examples All cyber systems are built using the physical hardware of the semiconductor chips found in all modern electronics, computers,. Meltdown and spectre raised the alarm over vulnerabilities that. Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity of. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. Cybersecurity is. Hardware Cybersecurity Examples.
From eduinput.com
Cyber Security Types, Threats, and Certifications Hardware Cybersecurity Examples Meltdown and spectre raised the alarm over vulnerabilities that. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. A guide to the threats. Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices. Hardware Cybersecurity Examples.
From www.rambus.com
The importance of hardwarebased security solutions Hardware Cybersecurity Examples Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices to the global infrastructure. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. A guide to the threats. Meltdown and spectre raised the. Hardware Cybersecurity Examples.
From blog.acer.com
Understanding Hardware Security and the Risks of Hardware Attacks — Acer Corner Hardware Cybersecurity Examples Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware. Hardware Cybersecurity Examples.
From knowledge.rtds.com
Realtime Simulation for Cybersecurity RTDS Technologies Hardware Cybersecurity Examples Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices to the global infrastructure. By operating at the physical layer, they ensure security against.. Hardware Cybersecurity Examples.
From www.slideteam.net
Top 10 Cybersecurity Dashboard Templates With Samples and Examples Hardware Cybersecurity Examples A guide to the threats. By operating at the physical layer, they ensure security against. Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices to the global infrastructure. Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity of. A common example of. Hardware Cybersecurity Examples.
From www.dell.com
Strengthen Security of Your Data Center with the NIST Cybersecurity Framework Dell USA Hardware Cybersecurity Examples By operating at the physical layer, they ensure security against. A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. A guide to the threats. Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity of. Meltdown and spectre raised. Hardware Cybersecurity Examples.
From gkaccess.com
Hardware Security Examples in Cyber Security GateKeeper 2FA Hardware Cybersecurity Examples By operating at the physical layer, they ensure security against. All cyber systems are built using the physical hardware of the semiconductor chips found in all modern electronics, computers,. Meltdown and spectre raised the alarm over vulnerabilities that. As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. Cybersecurity is a critical. Hardware Cybersecurity Examples.
From www.commercialintegrator.com
Cybersecurity Basics Terms & Definitions Integrators Should Know Commercial Integrator Hardware Cybersecurity Examples A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. All cyber systems are built using the physical hardware of the semiconductor chips found in all modern electronics, computers,. A guide to the threats. By operating at the physical layer, they ensure security against.. Hardware Cybersecurity Examples.
From sprinto.com
Top 16 Cyber Security tools You Must Know in 2024 Sprinto Hardware Cybersecurity Examples A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. Meltdown and spectre raised the alarm over vulnerabilities that. As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. Cybersecurity is a critical foundation of our. Hardware Cybersecurity Examples.
From assignmenthelp4me.com
A comprehensive study of Cyber Security and its types Hardware Cybersecurity Examples Meltdown and spectre raised the alarm over vulnerabilities that. As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. Cybersecurity is a critical foundation of our. Hardware Cybersecurity Examples.
From seletex.com
What is Cybersecurity Hardware? Seletex Hardware Cybersecurity Examples Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity of. Meltdown and spectre raised the alarm over vulnerabilities that. A guide to the threats. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. As enterprises begin to install the various. Hardware Cybersecurity Examples.
From www.slideserve.com
PPT Cybersecurity of Smart Grid Systems PowerPoint Presentation, free download ID4605430 Hardware Cybersecurity Examples Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. Meltdown and spectre raised the alarm over vulnerabilities that. As. Hardware Cybersecurity Examples.
From support.aiesec.org
Cyber Security Threats and Attacks AIESEC Help Center Hardware Cybersecurity Examples Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity of. Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices to the global infrastructure. Meltdown and spectre raised the alarm over vulnerabilities that. Hardware security is vulnerability protection that comes in the form. Hardware Cybersecurity Examples.
From www.1rti.com
HardwareBased Security for Computers Riverside Technologies, Inc. Hardware Cybersecurity Examples As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. All cyber systems are built using the physical hardware of the semiconductor chips found in all modern electronics, computers,. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of. Hardware Cybersecurity Examples.
From www.csoonline.com
5 computer security facts that surprise most people CSO Online Hardware Cybersecurity Examples Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. A guide to the threats. Meltdown and spectre raised the alarm over vulnerabilities that. As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. A common example of hardware security is a device that scans employee endpoints. Hardware Cybersecurity Examples.
From www.electric.ai
12 Cybersecurity Best Practices to Implement Electric Hardware Cybersecurity Examples Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices to the global infrastructure. A guide to the threats. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity. Hardware Cybersecurity Examples.
From news.cnrs.fr
When cyberattacks target hardware CNRS News Hardware Cybersecurity Examples All cyber systems are built using the physical hardware of the semiconductor chips found in all modern electronics, computers,. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Meltdown and spectre raised the alarm over vulnerabilities that. Building secure products requires adjusting business priorities, maturing. Hardware Cybersecurity Examples.
From www.spiceworks.com
What Is Hardware Security? Definition, Threats, and Best Practices Spiceworks Hardware Cybersecurity Examples Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity of. As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. All. Hardware Cybersecurity Examples.
From ape-europe.org
Cybersecurity Frameworks — Types, Strategies, Implementation and Benefits Ape Europe Hardware Cybersecurity Examples Meltdown and spectre raised the alarm over vulnerabilities that. A guide to the threats. A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. Building secure. Hardware Cybersecurity Examples.
From sprinto.com
Top 16 Cyber Security tools You Must Know in 2024 Sprinto Hardware Cybersecurity Examples A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. A guide to the threats. Meltdown and spectre raised the. Hardware Cybersecurity Examples.
From www.e-spincorp.com
Most common Cybersecurity Frameworks and types ESPIN Group Hardware Cybersecurity Examples Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. By operating at the physical layer, they ensure security against. A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. A guide to the threats. Meltdown and spectre raised. Hardware Cybersecurity Examples.
From www.tcaregs.com
Cybersecurity A Quick Overview in 5 Easy Steps TCA Hardware Cybersecurity Examples Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity of. Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices to the global infrastructure. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. A guide to the. Hardware Cybersecurity Examples.
From www.innovationnewsnetwork.com
400,000 awarded to establish computer hardware cybersecurity course Hardware Cybersecurity Examples By operating at the physical layer, they ensure security against. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server.. Hardware Cybersecurity Examples.
From blog.totalprosource.com
6 Common Types of Cyber Attacks Hardware Cybersecurity Examples As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. A guide to the threats. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware. Hardware Cybersecurity Examples.
From www.insightsonindia.com
Meaning and Types of Cybersecurity Threats INSIGHTS IAS Simplifying UPSC IAS Exam Preparation Hardware Cybersecurity Examples As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. Securing semiconductors and hardware and their supply chains helps protect sensitive information, maintain integrity of. Hardware security is vulnerability protection that comes in the form of a. Hardware Cybersecurity Examples.
From safety4sea.com
Infographic Ten steps to cyber security SAFETY4SEA Hardware Cybersecurity Examples Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything. Hardware Cybersecurity Examples.
From distantjob.com
8 Most Powerful Cybersecurity Tools in 2023 DistantJob Remote Recruitment Agency Hardware Cybersecurity Examples A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from. Hardware Cybersecurity Examples.
From www.slideteam.net
Top 10 Cybersecurity Dashboard Templates With Samples and Examples Hardware Cybersecurity Examples Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. A guide to the threats. Meltdown and spectre raised the alarm over vulnerabilities that. Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices to the global infrastructure. All cyber systems are built. Hardware Cybersecurity Examples.
From www.conceptdraw.com
Cyber Security Degrees IT Security Solutions Network Security Devices It Security Risks Hardware Cybersecurity Examples All cyber systems are built using the physical hardware of the semiconductor chips found in all modern electronics, computers,. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers. Hardware Cybersecurity Examples.
From studyonline.ecu.edu.au
Cyber Attacks Tips for Protecting Your Organisation ECU Online Hardware Cybersecurity Examples By operating at the physical layer, they ensure security against. Building secure products requires adjusting business priorities, maturing organizations and processes, and establishing clear metrics. Hardware security is vulnerability protection that comes in the form of a physical device rather than software that's installed on the hardware of a. Meltdown and spectre raised the alarm over vulnerabilities that. Cybersecurity is. Hardware Cybersecurity Examples.
From www.infosectrain.com
Common Security Attacks in the OSI Layer Model Hardware Cybersecurity Examples Cybersecurity is a critical foundation of our rapidly expanding digital world spanning hardware and software that powers everything from our personal devices to the global infrastructure. As enterprises begin to install the various autonomous sensors, controllers and monitors found in smart building, iot and. Meltdown and spectre raised the alarm over vulnerabilities that. By operating at the physical layer, they. Hardware Cybersecurity Examples.
From techcommunity.microsoft.com
Understanding CyberPhysical System and IoT/OT Risk, Featuring Gartner® Microsoft Community Hub Hardware Cybersecurity Examples A common example of hardware security is a device that scans employee endpoints or monitors network traffic, such as a hardware firewall or a proxy server. Meltdown and spectre raised the alarm over vulnerabilities that. All cyber systems are built using the physical hardware of the semiconductor chips found in all modern electronics, computers,. By operating at the physical layer,. Hardware Cybersecurity Examples.