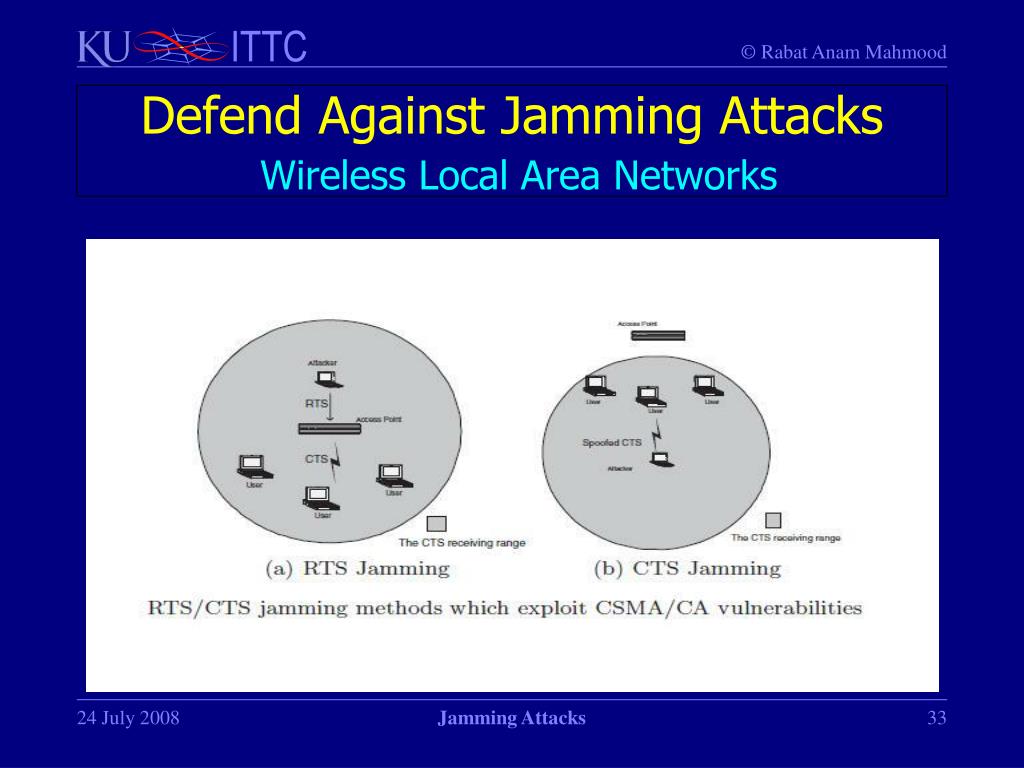
Jamming Attack Definition . jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how to.
from www.slideserve.com
jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how to. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received.
PPT Resilience To Jamming Attacks PowerPoint Presentation, free
Jamming Attack Definition jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how to. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally.
From github.com
GitHub kasturi710/JammingAttackDetectionandClassification Jamming Attack Definition this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how. Jamming Attack Definition.
From www.researchgate.net
Jamming Attack Characteristics. Figure 5. JammersNo FirewallNo VPN Jamming Attack Definition jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted. Jamming Attack Definition.
From www.slideshare.net
Preventing jamming attack by combining cryptography Jamming Attack Definition jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming attack defense is. Jamming Attack Definition.
From www.slideserve.com
PPT Resilience To Jamming Attacks PowerPoint Presentation, free Jamming Attack Definition jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted. Jamming Attack Definition.
From www.slideserve.com
PPT Resilience To Jamming Attacks PowerPoint Presentation, free Jamming Attack Definition jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless. Jamming Attack Definition.
From www.researchgate.net
Reactive Jamming Attack Security Modeling in IoT Download Scientific Jamming Attack Definition a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. in this article, i’ll break down the. Jamming Attack Definition.
From www.slideserve.com
PPT Resilience To Jamming Attacks PowerPoint Presentation, free Jamming Attack Definition a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting. Jamming Attack Definition.
From www.slideserve.com
PPT Optimal Jamming Attacks and Network Defense Policies in Wireless Jamming Attack Definition a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how to. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming attack. Jamming Attack Definition.
From dxoqrckgf.blob.core.windows.net
How Does Electronic Jamming Work at Mary Baldwin blog Jamming Attack Definition jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. a jamming attack. Jamming Attack Definition.
From www.slideserve.com
PPT Resilience To Jamming Attacks PowerPoint Presentation, free Jamming Attack Definition in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how to. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio. Jamming Attack Definition.
From www.slideserve.com
PPT A REVIEW “The Feasibility of Launching and Detecting Jamming Jamming Attack Definition jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. in this article,. Jamming Attack Definition.
From www.researchgate.net
Jamming attack in IoTbased smart home Download Scientific Diagram Jamming Attack Definition in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how to. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming attack. Jamming Attack Definition.
From www.researchgate.net
Example of jamming attack. Adapted from [79]. Download Scientific Diagram Jamming Attack Definition this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming in cyber security refers to a. Jamming Attack Definition.
From www.researchgate.net
Jamming and spoofing attacks. Download Scientific Diagram Jamming Attack Definition a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. in this article, i’ll break down the three types of jamming attacks, explain how they work, and. Jamming Attack Definition.
From github.com
GitHub jordib123/replayjammingattack Automated replay and jamming Jamming Attack Definition jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how to. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming. Jamming Attack Definition.
From www.scribd.com
The Feasibility of Launching and Detecting Jamming Attacks PDF Jamming Attack Definition jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. in this article, i’ll. Jamming Attack Definition.
From www.slideserve.com
PPT Resilience To Jamming Attacks PowerPoint Presentation, free Jamming Attack Definition jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how. Jamming Attack Definition.
From www.slideserve.com
PPT Security in Sensor Networks PowerPoint Presentation, free Jamming Attack Definition this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how to. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming attack. Jamming Attack Definition.
From www.semanticscholar.org
Figure 1 from Jamming Attack Mitigation in CRIoT Using Game Theory Jamming Attack Definition jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. in this article,. Jamming Attack Definition.
From www.slideserve.com
PPT A REVIEW “The Feasibility of Launching and Detecting Jamming Jamming Attack Definition this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how to. a. Jamming Attack Definition.
From www.slideserve.com
PPT The Feasibility of Launching and Detecting Jamming Attacks in Jamming Attack Definition jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how. Jamming Attack Definition.
From www.slideserve.com
PPT The Feasibility of Launching and Detecting Jamming Attacks in Jamming Attack Definition a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. in this article, i’ll break down the three types of jamming attacks, explain how they work, and. Jamming Attack Definition.
From slideplayer.com
Qi Dong and Donggang Liu Presented by Ying Xuan ppt download Jamming Attack Definition jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. in this article, i’ll break down the three types of jamming attacks, explain how they work,. Jamming Attack Definition.
From www.researchgate.net
Jamming Attack Characteristics. Figure 5. JammersNo FirewallNo VPN Jamming Attack Definition jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some. Jamming Attack Definition.
From www.youtube.com
Jamming Attack in Network Security Jamming Attack in Network Security Jamming Attack Definition jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming in cyber security refers to a. Jamming Attack Definition.
From www.slideserve.com
PPT Resilience To Jamming Attacks PowerPoint Presentation, free Jamming Attack Definition jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. a jamming attack. Jamming Attack Definition.
From www.researchgate.net
Jamming attack impact Download Scientific Diagram Jamming Attack Definition in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how to. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming attack defense is a measure performed by wireless devices to ensure that information can. Jamming Attack Definition.
From www.slideserve.com
PPT Resilience To Jamming Attacks PowerPoint Presentation, free Jamming Attack Definition in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how to. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming in. Jamming Attack Definition.
From www.thesecuritybuddy.com
What is Jamming Attack and how to prevent it? The Security Buddy Jamming Attack Definition this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. jamming in cyber security refers to a. Jamming Attack Definition.
From www.slideserve.com
PPT Resilience To Jamming Attacks PowerPoint Presentation, free Jamming Attack Definition this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how to. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming in. Jamming Attack Definition.
From www.semanticscholar.org
[PDF] Jamming Attacks and AntiJamming Strategies in Wireless Networks Jamming Attack Definition jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless. Jamming Attack Definition.
From www.researchgate.net
Reactive Jamming Attack Security Modeling in IoT Download Scientific Jamming Attack Definition a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. in this article, i’ll break down the. Jamming Attack Definition.
From www.researchgate.net
Reactive Jamming Attack and Mitigation by Identification of the Jamming Attack Definition this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. in this article, i’ll break down the three types of jamming attacks, explain how they work, and give you some tips on how. Jamming Attack Definition.
From www.researchgate.net
Jamming attack in IoTbased smart home Download Scientific Diagram Jamming Attack Definition this research unveils a comprehensive taxonomy addressing jamming attacks on 5g networks. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. jamming attack defense is a measure performed by wireless devices to ensure that information can be transmitted and received. in this article, i’ll break down the. Jamming Attack Definition.
From www.researchgate.net
Enhanced RollJam Attack Model. Download Scientific Diagram Jamming Attack Definition jamming in cyber security refers to a type of attack that is carried out with the sole intention of disrupting radio broadcast. a jamming attack is an attack in which an attacker transfers interfering signals on a wireless network intentionally. in this article, i’ll break down the three types of jamming attacks, explain how they work, and. Jamming Attack Definition.