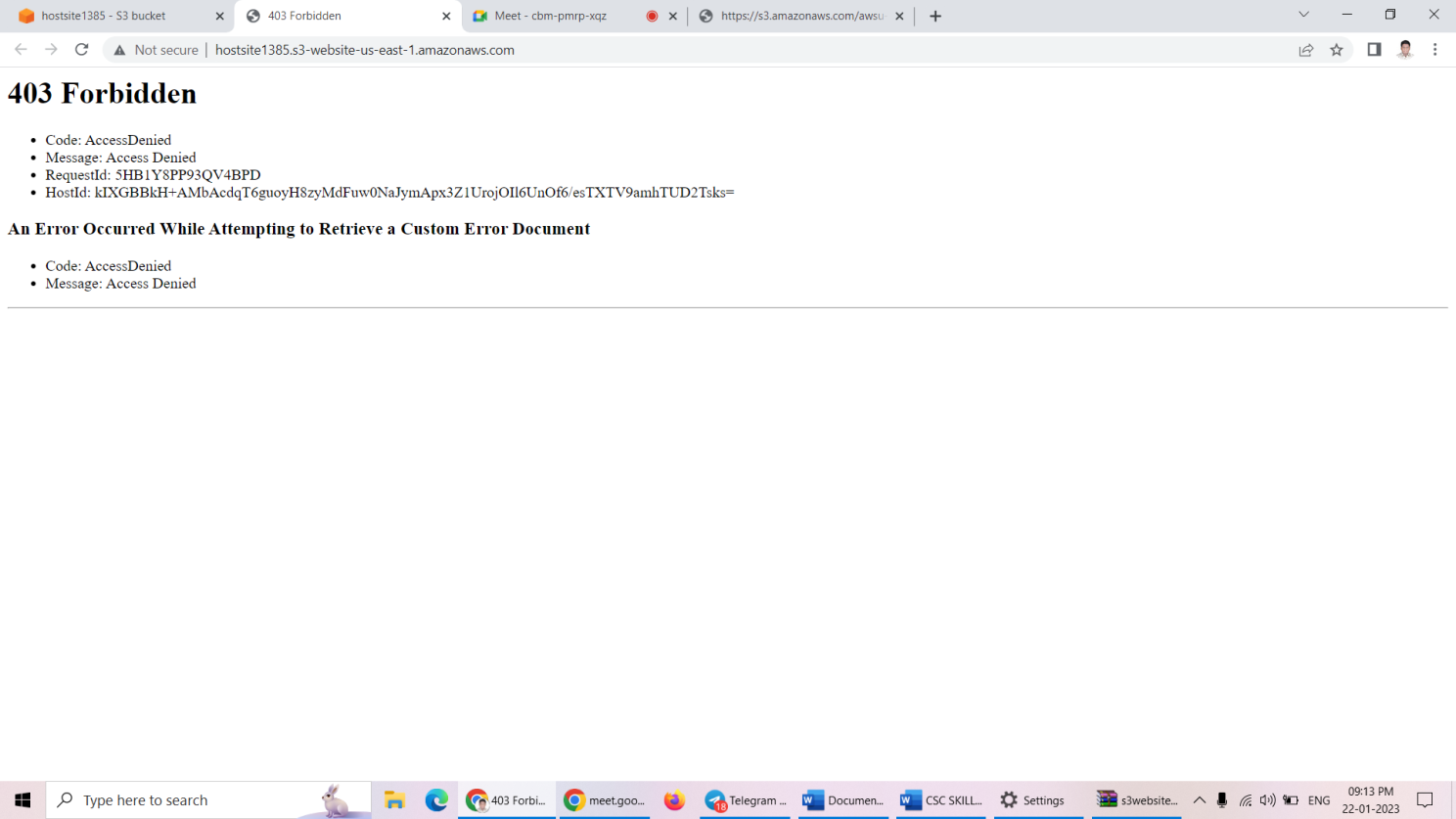
Aws S3 Bucket Restrict Ip . With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. Answering to your question, yes you can restrict access to s3 bucket to specific ip address or range using a bucket policy. You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. This is useful if you have multiple vpc. You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition.
from codelido.com
This is useful if you have multiple vpc. If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. Answering to your question, yes you can restrict access to s3 bucket to specific ip address or range using a bucket policy. You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition. With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access.
{1, plural, =1 {{AWS CloudFront Distribution for Content Delivery
Aws S3 Bucket Restrict Ip With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition. You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. This is useful if you have multiple vpc. With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. Answering to your question, yes you can restrict access to s3 bucket to specific ip address or range using a bucket policy. I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have.
From github.com
CloudFronttoS3 need to change restrict access to an Amazon S3 bucket Aws S3 Bucket Restrict Ip You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition. You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. If you want to allow servers in your network access to internal s3 buckets, without making the objects. Aws S3 Bucket Restrict Ip.
From codelido.com
{1, plural, =1 {{AWS CloudFront Distribution for Content Delivery Aws S3 Bucket Restrict Ip I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. If you want to allow servers in your network access. Aws S3 Bucket Restrict Ip.
From aws.amazon.com
Restrict Access to your Amazon Connect S3 Bucket AWS Contact Center Aws S3 Bucket Restrict Ip Answering to your question, yes you can restrict access to s3 bucket to specific ip address or range using a bucket policy. If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. With amazon s3 bucket. Aws S3 Bucket Restrict Ip.
From codelido.com
{1, plural, =1 {{AWS CloudFront Distribution for Content Delivery Aws S3 Bucket Restrict Ip You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. This is useful if you have multiple vpc. If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a. Aws S3 Bucket Restrict Ip.
From kloudle.com
How to enable public access block to restrict access in S3 using AWS Aws S3 Bucket Restrict Ip If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. Answering to. Aws S3 Bucket Restrict Ip.
From aws.amazon.com
Restrict Access to your Amazon Connect S3 Bucket AWS Contact Center Aws S3 Bucket Restrict Ip If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. Answering to. Aws S3 Bucket Restrict Ip.
From aws.amazon.com
Restrict Access to your Amazon Connect S3 Bucket AWS Contact Center Aws S3 Bucket Restrict Ip You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition. This is useful if you have multiple vpc. If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution.. Aws S3 Bucket Restrict Ip.
From codelido.com
{1, plural, =1 {{AWS CloudFront Distribution for Content Delivery Aws S3 Bucket Restrict Ip This is useful if you have multiple vpc. I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access. Aws S3 Bucket Restrict Ip.
From 000069.awsstudygroup.com
Restrict access to S3 VPC Endpoint S3 SECURITY BEST PRACTICES Aws S3 Bucket Restrict Ip I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. Answering to your question, yes you can restrict access to s3 bucket to specific ip address or range using a bucket policy. This is useful if you have multiple vpc. If you want to. Aws S3 Bucket Restrict Ip.
From codelido.com
{1, plural, =1 {{AWS CloudFront Distribution for Content Delivery Aws S3 Bucket Restrict Ip Answering to your question, yes you can restrict access to s3 bucket to specific ip address or range using a bucket policy. I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. If you want to allow servers in your network access to internal. Aws S3 Bucket Restrict Ip.
From confluence.atlassian.com
Configuring Amazon S3 object storage Atlassian Support Atlassian Aws S3 Bucket Restrict Ip This is useful if you have multiple vpc. I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. You can. Aws S3 Bucket Restrict Ip.
From www.youtube.com
S3 Bucket Security like a PRO How to Restrict Amazon S3 Bucket Access Aws S3 Bucket Restrict Ip This is useful if you have multiple vpc. You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition. Answering to your question, yes you can restrict access to s3 bucket to specific ip address or range using a bucket policy. I am trying this policy to allow users to put and list. Aws S3 Bucket Restrict Ip.
From codelido.com
{1, plural, =1 {{AWS CloudFront Distribution for Content Delivery Aws S3 Bucket Restrict Ip This is useful if you have multiple vpc. If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access. Aws S3 Bucket Restrict Ip.
From kloudle.com
How to secure AWS S3 buckets with sensitive data Kloudle Cloud Aws S3 Bucket Restrict Ip This is useful if you have multiple vpc. With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. I am trying this. Aws S3 Bucket Restrict Ip.
From codelido.com
{1, plural, =1 {{AWS CloudFront Distribution for Content Delivery Aws S3 Bucket Restrict Ip You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. Answering to your question, yes you can restrict access to s3 bucket to specific ip address or range using a bucket policy. I am trying this policy to allow users to put and list object access. Aws S3 Bucket Restrict Ip.
From medium.com
Amazon S3 Bucket Policy — Different Usecase to Allow & Restrict Access Aws S3 Bucket Restrict Ip This is useful if you have multiple vpc. I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. Answering to. Aws S3 Bucket Restrict Ip.
From www.geeksforgeeks.org
Amazon S3 Creating a S3 Bucket Aws S3 Bucket Restrict Ip This is useful if you have multiple vpc. I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. Answering to your question, yes you can restrict access to s3 bucket to specific ip address or range using a bucket policy. You can create a. Aws S3 Bucket Restrict Ip.
From aws.amazon.com
How to Use AWS Config to Monitor for and Respond to Amazon S3 Buckets Aws S3 Bucket Restrict Ip I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition. Answering to your question, yes you can restrict access to s3 bucket to specific ip address. Aws S3 Bucket Restrict Ip.
From www.youtube.com
AWS S3 Bucket Security 👮 Restrict Privileges🔒to User using IAM Policy Aws S3 Bucket Restrict Ip This is useful if you have multiple vpc. If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. I am trying this policy to allow users to put and list object access with a particular ip. Aws S3 Bucket Restrict Ip.
From www.linkedin.com
How to Restrict Amazon S3 Bucket Access to a Specific IAM Role Aws S3 Bucket Restrict Ip You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. I am. Aws S3 Bucket Restrict Ip.
From aws.amazon.com
Managing Amazon S3 access with VPC endpoints and S3 Access Points AWS Aws S3 Bucket Restrict Ip With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. Answering to your question, yes you can restrict access to s3 bucket to specific ip address or range using a bucket policy. You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition. Aws S3 Bucket Restrict Ip.
From www.youtube.com
How To Restrict S3 Bucket Access To CloudFront (3 Min) AWS YouTube Aws S3 Bucket Restrict Ip You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. You can create a bucket policy that restricts access to. Aws S3 Bucket Restrict Ip.
From codelido.com
{1, plural, =1 {{AWS CloudFront Distribution for Content Delivery Aws S3 Bucket Restrict Ip I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition. If you want to allow servers in your network access to internal s3 buckets, without making. Aws S3 Bucket Restrict Ip.
From exodkftil.blob.core.windows.net
Aws S3 Bucket Policies Examples at Guy Deaton blog Aws S3 Bucket Restrict Ip You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition. I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. This is useful if you have multiple vpc. If you want to allow servers in your. Aws S3 Bucket Restrict Ip.
From aws.amazon.com
Restrict Access to your Amazon Connect S3 Bucket AWS Contact Center Aws S3 Bucket Restrict Ip If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. You can. Aws S3 Bucket Restrict Ip.
From www.ibm.com
Attaching an AWS S3 Bucket Aws S3 Bucket Restrict Ip Answering to your question, yes you can restrict access to s3 bucket to specific ip address or range using a bucket policy. If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. You can create a. Aws S3 Bucket Restrict Ip.
From aws.amazon.com
Restrict Access to your Amazon Connect S3 Bucket AWS Contact Center Aws S3 Bucket Restrict Ip You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition. This is useful if you have multiple vpc. If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution.. Aws S3 Bucket Restrict Ip.
From 000069.awsstudygroup.com
Restrict access to S3 VPC Endpoint S3 SECURITY BEST PRACTICES Aws S3 Bucket Restrict Ip With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition. You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access. Aws S3 Bucket Restrict Ip.
From codelido.com
{1, plural, =1 {{AWS CloudFront Distribution for Content Delivery Aws S3 Bucket Restrict Ip If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. This is. Aws S3 Bucket Restrict Ip.
From www.easydeploy.io
AWS S3 Handson Aws S3 Bucket Restrict Ip I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. You can create a bucket policy that restricts access to. Aws S3 Bucket Restrict Ip.
From ip-slip.com
IP SLIP Over 100 Public AWS S3 Buckets Identified Aws S3 Bucket Restrict Ip I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. You can also create an amazon s3 bucket policy with the iam aws:sourcevpc condition key to restrict access to buckets from specific amazon vpcs. With amazon s3 bucket policies, you can secure access to. Aws S3 Bucket Restrict Ip.
From www.geekfeed.co.jp
Restrict S3 Bucket Access from Specified Resource ソフトウェア開発のギークフィード Aws S3 Bucket Restrict Ip If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. This is. Aws S3 Bucket Restrict Ip.
From codelido.com
{1, plural, =1 {{AWS CloudFront Distribution for Content Delivery Aws S3 Bucket Restrict Ip With amazon s3 bucket policies, you can secure access to objects in your buckets, so that only users with the appropriate permissions can access. This is useful if you have multiple vpc. You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition. I am trying this policy to allow users to put. Aws S3 Bucket Restrict Ip.
From www.youtube.com
AWS S3 (AWS S3) Restrict bucket access awss3 secure transport Aws S3 Bucket Restrict Ip If you want to allow servers in your network access to internal s3 buckets, without making the objects within them open to the internet, whitelisting access with a bucket policy is a simple solution. You can create a bucket policy that restricts access to a specific vpc by using the aws:sourcevpc condition. With amazon s3 bucket policies, you can secure. Aws S3 Bucket Restrict Ip.
From aws.amazon.com
Restrict Access to your Amazon Connect S3 Bucket AWS Contact Center Aws S3 Bucket Restrict Ip I am trying this policy to allow users to put and list object access with a particular ip (56.160.12.114) only and all the rest should have. Answering to your question, yes you can restrict access to s3 bucket to specific ip address or range using a bucket policy. If you want to allow servers in your network access to internal. Aws S3 Bucket Restrict Ip.