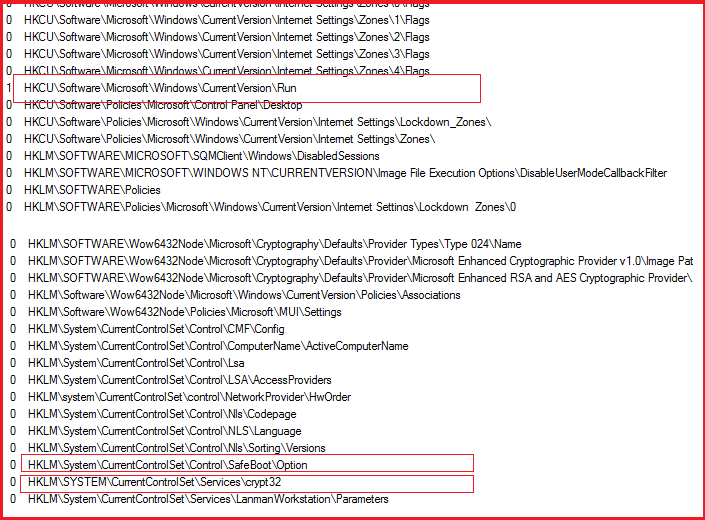
Mitre Registry Run Keys . Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. 230 rows the following run keys are created by default on windows systems:
from www.cyfirma.com
147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. 230 rows the following run keys are created by default on windows systems:
TECHNICAL ANALYSIS BIGLOCK RANSOMWARE CYFIRMA
Mitre Registry Run Keys Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. 230 rows the following run keys are created by default on windows systems: Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values.
From www.mydamus.com
Mitre Strip Outer Damus Building Solutions Mitre Registry Run Keys Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Registry run keys / startup folder technique. Mitre Registry Run Keys.
From any.run
Using MITRE ATT&CK ANY.RUN Blog Mitre Registry Run Keys Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. 230 rows the following run keys are created by default on windows systems: Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious. Mitre Registry Run Keys.
From medium.com
Finding Related ATT&CK Techniques MITRE ATT&CK™ Medium Mitre Registry Run Keys 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. 230 rows the following run keys are created by default on windows systems: Adding an entry to the run keys, or. Mitre Registry Run Keys.
From www.thepcinsider.com
How to Edit Windows Registry? How to Modify, Create, and Delete Mitre Registry Run Keys 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look. Mitre Registry Run Keys.
From innoem.eng.psu.ac.th
How To Tell If A Registry Key Was Edited Recently on Sale innoem.eng Mitre Registry Run Keys 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. Adding an entry to the run keys,. Mitre Registry Run Keys.
From goods4cybersec.com
Blogs Goods4CyberSec Mitre Registry Run Keys Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. Adversaries may interact with the windows registry to hide. Mitre Registry Run Keys.
From www.paloaltonetworks.co.uk
Correlation, Curation, and Completeness What MITRE Results Can Tell Us Mitre Registry Run Keys Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. 230 rows the following run keys are created by default on windows systems: Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look. Mitre Registry Run Keys.
From davescomputertips.com
How to Manage Windows 10 Startup Programs Daves Computer Tips Mitre Registry Run Keys 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when. Mitre Registry Run Keys.
From any.run
Malware analysis EXTRE RE INVOICE527370 from Davis Graphic Mitre Registry Run Keys Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. 230 rows the following run keys are created by default on windows systems: Adding an entry to the run keys, or creating. Mitre Registry Run Keys.
From any.run
Malware analysis Mitre Registry Run Keys Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname]. Mitre Registry Run Keys.
From any.run
Malware analysis Mitre Registry Run Keys Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. 230 rows the following run keys are. Mitre Registry Run Keys.
From local23.org
Cómo utilizar el Editor del Registro de Windows Local 23 Mitre Registry Run Keys 230 rows the following run keys are created by default on windows systems: Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when. Mitre Registry Run Keys.
From www.experts-exchange.com
Solved Add registry key using GPO Experts Exchange Mitre Registry Run Keys Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname]. Mitre Registry Run Keys.
From www.mydamus.com
Mitre Strip Inner Damus Building Solutions Mitre Registry Run Keys 230 rows the following run keys are created by default on windows systems: Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. 147 rows mosquito can modify registry keys. Mitre Registry Run Keys.
From www.remosoftware.com
Remove Unwanted Registry Entries Remo Optimizer Mitre Registry Run Keys 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. 230 rows the following run keys are created by default on windows systems: Adversaries may interact with the windows registry to hide. Mitre Registry Run Keys.
From juggernaut-sec.com
Autorun Startup Registry Keys Windows Privilege Escalation Mitre Registry Run Keys 230 rows the following run keys are created by default on windows systems: Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when. Mitre Registry Run Keys.
From www.cyfirma.com
TECHNICAL ANALYSIS BIGLOCK RANSOMWARE CYFIRMA Mitre Registry Run Keys 230 rows the following run keys are created by default on windows systems: Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when. Mitre Registry Run Keys.
From kravensecurity.com
Hunting For Persistence With Cympire Part I — Registry Run Keys Mitre Registry Run Keys Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. Adding an entry to the run. Mitre Registry Run Keys.
From any.run
Using MITRE ATT&CK ANY.RUN Blog Mitre Registry Run Keys Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. 230 rows the following run keys are created by default on windows systems: 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious. Mitre Registry Run Keys.
From www.odt.co.nz
Mitre 10 Cup season preview Otago Daily Times Online News Mitre Registry Run Keys Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname]. Mitre Registry Run Keys.
From any.run
Malware analysis Mitre Registry Run Keys Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence. Mitre Registry Run Keys.
From fossbytes.com
What Is Windows Registry And How To Use It — Complete Guide Mitre Registry Run Keys 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. Adding an entry to the run. Mitre Registry Run Keys.
From www.tenforums.com
CCleaner keeps reverting registry keys Windows 10 Forums Mitre Registry Run Keys 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a. Mitre Registry Run Keys.
From any.run
Malware Trends Report Q1, 2024 ANY.RUN's Cybersecurity Blog Mitre Registry Run Keys Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. 230 rows the following run keys are created by default on windows systems: Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. Adding an entry to the run keys. Mitre Registry Run Keys.
From www.chegg.com
Solved BBSRAT 10 The Windows Registry is a large Mitre Registry Run Keys Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to. Mitre Registry Run Keys.
From www.linkedin.com
Understanding MITRE Framework from a CISO's Prospective Mitre Registry Run Keys Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Registry run keys / startup folder technique. Mitre Registry Run Keys.
From www.minitool.com
Windows 10 Startup Folder Everything You Need to Know MiniTool Mitre Registry Run Keys Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be. Mitre Registry Run Keys.
From technoresult.com
Backup and restore Taskbar Pinned items on Windows 11 Technoresult Mitre Registry Run Keys Adding an entry to the run keys in the registry or startup folder will cause the program referenced to be executed when a user logs in. Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence. Mitre Registry Run Keys.
From www.youtube.com
HOW TO OPEN WINDOWS REGISTRY EDITOR FROM RUN COMMAND YouTube Mitre Registry Run Keys Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. 230 rows the following run keys are created by default on windows systems: 147 rows mosquito can modify registry keys. Mitre Registry Run Keys.
From pubhistoryproject.co.uk
MITRE AND KEYS, 26 APPLEGATE STREET Pub History Project Leicester Mitre Registry Run Keys 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look. Mitre Registry Run Keys.
From www.sentinelone.com
What is the MITRE ATT&CK Framework? An Easy Guide Mitre Registry Run Keys Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code. Mitre Registry Run Keys.
From xsoar.pan.dev
MITRE ATT&CK CoA T1547.001 Registry Run Keys Startup Folder Mitre Registry Run Keys Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. Adding an entry to the run keys,. Mitre Registry Run Keys.
From blueteamresources.in
Detecting MITRE Initial Access Valid Domain Accounts Mitre Registry Run Keys Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. 230 rows the following run keys are created by default on windows systems: Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. 147 rows mosquito can modify registry keys. Mitre Registry Run Keys.
From www.minitool.com
How to Create, Add, Change, Delete Registry Key Windows 10 MiniTool Mitre Registry Run Keys 230 rows the following run keys are created by default on windows systems: Registry run keys / startup folder technique in summary, an easy way to start using att&ck for threat intelligence is to look at a single. 147 rows mosquito can modify registry keys under hkcu\software\microsoft[dllname] to store configuration values. Adversaries may interact with the windows registry to hide. Mitre Registry Run Keys.
From urlscan.io
www.cybrary.it urlscan.io Mitre Registry Run Keys Adding an entry to the run keys, or creating a shortcut in startup folder is enough to execute malicious code when a user logs in. 230 rows the following run keys are created by default on windows systems: Adversaries may interact with the windows registry to hide configuration information within registry keys, remove. Registry run keys / startup folder technique. Mitre Registry Run Keys.