Power Bi Security Groups . There are 4 access roles available for a. Learn two possible ways to implement the access control. there are 3 primary ways to set up user permissions in power bi: while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. “who sees what in the report?” is one of the key security questions in power bi.
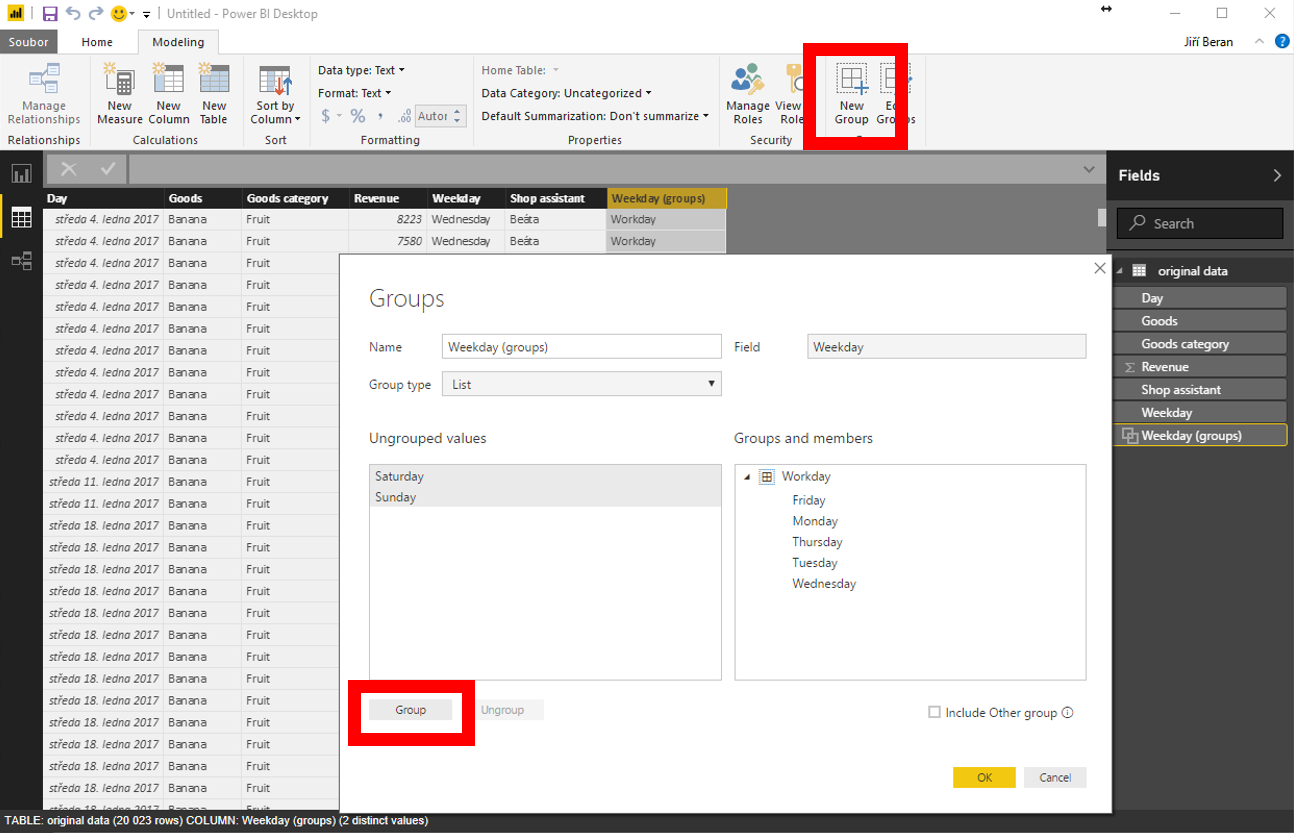
from exceltown.com
while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. Learn two possible ways to implement the access control. there are 3 primary ways to set up user permissions in power bi: “who sees what in the report?” is one of the key security questions in power bi. There are 4 access roles available for a.
Groups in Power BI Trainings, consultancy, tutorials
Power Bi Security Groups while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. there are 3 primary ways to set up user permissions in power bi: while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. “who sees what in the report?” is one of the key security questions in power bi. Learn two possible ways to implement the access control. There are 4 access roles available for a.
From www.kasperonbi.com
Power BI Desktop Dynamic security cheat sheet Kasper On BI Power Bi Security Groups Learn two possible ways to implement the access control. “who sees what in the report?” is one of the key security questions in power bi. there are 3 primary ways to set up user permissions in power bi: while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network. Power Bi Security Groups.
From www.sqlchick.com
Groups in Power BI How Sharing and Security Works — SQL Chick Power Bi Security Groups while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. “who sees what in the report?” is one of the key security questions in power bi. there are 3 primary ways to set up user permissions in power bi: Learn two possible ways. Power Bi Security Groups.
From skypoint.ai
How Do We Improve Power BI Security? Skypoint Power Bi Security Groups There are 4 access roles available for a. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. there are 3 primary ways to set up user permissions in power bi: “who sees what in the report?” is one of the key security. Power Bi Security Groups.
From thewindowsupdate.com
Row Level Security in Power BI Desktop Power Bi Security Groups Learn two possible ways to implement the access control. There are 4 access roles available for a. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. there are 3 primary ways to set up user permissions in power bi: “who sees what. Power Bi Security Groups.
From learn.microsoft.com
Power BI security white paper Power BI Microsoft Learn Power Bi Security Groups There are 4 access roles available for a. “who sees what in the report?” is one of the key security questions in power bi. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. Learn two possible ways to implement the access control. . Power Bi Security Groups.
From www.youtube.com
Power BI Security Combined Column Level Security & Row Level Security Power Bi Security Groups There are 4 access roles available for a. Learn two possible ways to implement the access control. “who sees what in the report?” is one of the key security questions in power bi. there are 3 primary ways to set up user permissions in power bi: while the power bi security white paper focuses on key technical. Power Bi Security Groups.
From www.youtube.com
Data Security in Power BI YouTube Power Bi Security Groups “who sees what in the report?” is one of the key security questions in power bi. there are 3 primary ways to set up user permissions in power bi: There are 4 access roles available for a. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation,. Power Bi Security Groups.
From qmetrix.com.au
Power BI Architecture And Security What You Need To Know Power Bi Security Groups Learn two possible ways to implement the access control. there are 3 primary ways to set up user permissions in power bi: while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. “who sees what in the report?” is one of the key. Power Bi Security Groups.
From www.youtube.com
Dynamic Row Level Security in Power BI with Exclude and Include Rules Power Bi Security Groups “who sees what in the report?” is one of the key security questions in power bi. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. there are 3 primary ways to set up user permissions in power bi: Learn two possible ways. Power Bi Security Groups.
From dbakevlar.com
Securing Data in Power BI an Interactive Diagram DBAKevlar Power Bi Security Groups Learn two possible ways to implement the access control. “who sees what in the report?” is one of the key security questions in power bi. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. there are 3 primary ways to set up. Power Bi Security Groups.
From www.dtonomy.com
Create Power BI Reporting for CrowdStrike AIDriven Security Operations Power Bi Security Groups There are 4 access roles available for a. Learn two possible ways to implement the access control. “who sees what in the report?” is one of the key security questions in power bi. there are 3 primary ways to set up user permissions in power bi: while the power bi security white paper focuses on key technical. Power Bi Security Groups.
From www.sqlchick.com
Power BI Security Overview — SQL Chick Power Bi Security Groups there are 3 primary ways to set up user permissions in power bi: Learn two possible ways to implement the access control. There are 4 access roles available for a. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. “who sees what. Power Bi Security Groups.
From www.biinsight.com
Good Practice Use Security Groups in Role Mapping Instead of User Power Bi Security Groups while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. “who sees what in the report?” is one of the key security questions in power bi. there are 3 primary ways to set up user permissions in power bi: Learn two possible ways. Power Bi Security Groups.
From www.sqlchick.com
Groups in Power BI How Sharing and Security Works — SQL Chick Power Bi Security Groups there are 3 primary ways to set up user permissions in power bi: There are 4 access roles available for a. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. Learn two possible ways to implement the access control. “who sees what. Power Bi Security Groups.
From slidesharetrick.blogspot.com
Power Bi Row Level Security Groups slidesharetrick Power Bi Security Groups “who sees what in the report?” is one of the key security questions in power bi. Learn two possible ways to implement the access control. there are 3 primary ways to set up user permissions in power bi: while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network. Power Bi Security Groups.
From skypoint.ai
How Do We Improve Power BI Security? Skypoint Power Bi Security Groups there are 3 primary ways to set up user permissions in power bi: while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. Learn two possible ways to implement the access control. “who sees what in the report?” is one of the key. Power Bi Security Groups.
From databear.com
Rowlevel security (RLS) in Power BI Power BI Tips Power Bi Security Groups while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. There are 4 access roles available for a. there are 3 primary ways to set up user permissions in power bi: “who sees what in the report?” is one of the key security. Power Bi Security Groups.
From www.ilink-digital.com
Microsoft Power BI Security 6 Best Practices iLink Digital Power Bi Security Groups while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. there are 3 primary ways to set up user permissions in power bi: Learn two possible ways to implement the access control. “who sees what in the report?” is one of the key. Power Bi Security Groups.
From www.acuitytraining.co.uk
Improving Power BI Security 7 Checks You Can Do In Under 7 Minutes Power Bi Security Groups There are 4 access roles available for a. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. Learn two possible ways to implement the access control. “who sees what in the report?” is one of the key security questions in power bi. . Power Bi Security Groups.
From skypoint.ai
How Do We Improve Power BI Security? Skypoint Power Bi Security Groups “who sees what in the report?” is one of the key security questions in power bi. There are 4 access roles available for a. Learn two possible ways to implement the access control. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. . Power Bi Security Groups.
From www.sqlchick.com
Groups in Power BI How Sharing and Security Works — SQL Chick Power Bi Security Groups Learn two possible ways to implement the access control. “who sees what in the report?” is one of the key security questions in power bi. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. there are 3 primary ways to set up. Power Bi Security Groups.
From www.vrogue.co
Power Bi Row Level Security Rls Setup Step By Guide Groups Power Bi Security Groups Learn two possible ways to implement the access control. there are 3 primary ways to set up user permissions in power bi: There are 4 access roles available for a. “who sees what in the report?” is one of the key security questions in power bi. while the power bi security white paper focuses on key technical. Power Bi Security Groups.
From www.pk-anexcelexpert.com
Static and Dynamic Row Level Security in Power BI PK An Excel Expert Power Bi Security Groups while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. There are 4 access roles available for a. there are 3 primary ways to set up user permissions in power bi: “who sees what in the report?” is one of the key security. Power Bi Security Groups.
From www.vrogue.co
Security And Collaboration In Power Bi vrogue.co Power Bi Security Groups “who sees what in the report?” is one of the key security questions in power bi. There are 4 access roles available for a. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. there are 3 primary ways to set up user. Power Bi Security Groups.
From www.kasperonbi.com
Power BI Desktop Dynamic security cheat sheet Kasper On BI Power Bi Security Groups There are 4 access roles available for a. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. “who sees what in the report?” is one of the key security questions in power bi. there are 3 primary ways to set up user. Power Bi Security Groups.
From www.journeyteam.com
9 Power BI Security Best Practices Power Bi Security Groups There are 4 access roles available for a. Learn two possible ways to implement the access control. there are 3 primary ways to set up user permissions in power bi: while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. “who sees what. Power Bi Security Groups.
From 3cloudsolutions.com
Understanding Power BI Security and Data Access 3Cloud Power Bi Security Groups there are 3 primary ways to set up user permissions in power bi: “who sees what in the report?” is one of the key security questions in power bi. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. There are 4 access. Power Bi Security Groups.
From slidesharetrick.blogspot.com
Power Bi Row Level Security Groups slidesharetrick Power Bi Security Groups Learn two possible ways to implement the access control. “who sees what in the report?” is one of the key security questions in power bi. there are 3 primary ways to set up user permissions in power bi: while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network. Power Bi Security Groups.
From www.youtube.com
Security in Power BI Quick Overview YouTube Power Bi Security Groups there are 3 primary ways to set up user permissions in power bi: There are 4 access roles available for a. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. Learn two possible ways to implement the access control. “who sees what. Power Bi Security Groups.
From dxoqaiqof.blob.core.windows.net
Power Bi Security By Tab at Chris Gladney blog Power Bi Security Groups There are 4 access roles available for a. while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. “who sees what in the report?” is one of the key security questions in power bi. Learn two possible ways to implement the access control. . Power Bi Security Groups.
From subscription.packtpub.com
Mastering Microsoft Power BI Power Bi Security Groups Learn two possible ways to implement the access control. There are 4 access roles available for a. there are 3 primary ways to set up user permissions in power bi: “who sees what in the report?” is one of the key security questions in power bi. while the power bi security white paper focuses on key technical. Power Bi Security Groups.
From data-flair.training
Power BI Security What is Dynamic RowLevel Security DataFlair Power Bi Security Groups there are 3 primary ways to set up user permissions in power bi: There are 4 access roles available for a. Learn two possible ways to implement the access control. “who sees what in the report?” is one of the key security questions in power bi. while the power bi security white paper focuses on key technical. Power Bi Security Groups.
From www.michaelroth42.com
Set up security groups for your environments Power Bi Security Groups there are 3 primary ways to set up user permissions in power bi: while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. There are 4 access roles available for a. “who sees what in the report?” is one of the key security. Power Bi Security Groups.
From www.cloudfronts.com
Fig 2 CEO Dashboard Power Bi Security Groups while the power bi security white paper focuses on key technical topics such as authentication, data residency, and network isolation, the primary goal of. There are 4 access roles available for a. there are 3 primary ways to set up user permissions in power bi: Learn two possible ways to implement the access control. “who sees what. Power Bi Security Groups.
From exceltown.com
Groups in Power BI Trainings, consultancy, tutorials Power Bi Security Groups There are 4 access roles available for a. “who sees what in the report?” is one of the key security questions in power bi. there are 3 primary ways to set up user permissions in power bi: Learn two possible ways to implement the access control. while the power bi security white paper focuses on key technical. Power Bi Security Groups.