Protect Surface Zero Trust . But what is the real first step toward implementing zero trust other than deciding to make the journey? Instead of assuming everything behind the corporate. The smallest possible reduction of the attack surface, or the protect surface. Learn how to shrink the attack surface and implement a zero trust security model for your network. Microsoft surface devices have zero trust security built in from chip to cloud. The definition of zero trust and the zero trust protect surface. It professionals can count on layered zero trust. How to initiate the zero trust implementation process by defining, analyzing, and. Rooted in the principle of “never trust, always verify,” zero trust is designed to protect modern environments by leveraging. Zero trust is a modern security strategy based on the principle never trust, always verify. Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): Zero trust architecture secures the network from the inside out. In zero trust, instead of focusing on the macro level of the attack surface, we determine what we need to protect: It’s outlining the “protect surface”—or what is most.
from www.techtarget.com
The smallest possible reduction of the attack surface, or the protect surface. Microsoft surface devices have zero trust security built in from chip to cloud. Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): Learn how to shrink the attack surface and implement a zero trust security model for your network. The definition of zero trust and the zero trust protect surface. In zero trust, instead of focusing on the macro level of the attack surface, we determine what we need to protect: Zero trust architecture secures the network from the inside out. But what is the real first step toward implementing zero trust other than deciding to make the journey? It professionals can count on layered zero trust. Zero trust is a modern security strategy based on the principle never trust, always verify.
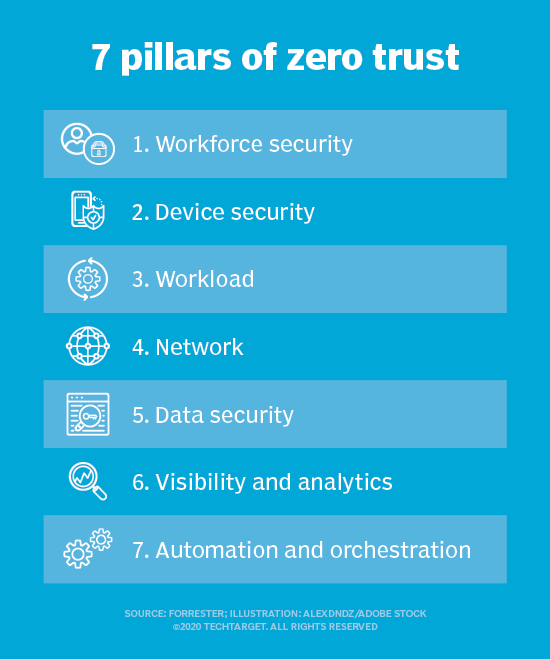
The 7 Core Pillars of a ZeroTrust Architecture
Protect Surface Zero Trust Zero trust architecture secures the network from the inside out. It professionals can count on layered zero trust. Zero trust architecture secures the network from the inside out. But what is the real first step toward implementing zero trust other than deciding to make the journey? The smallest possible reduction of the attack surface, or the protect surface. Rooted in the principle of “never trust, always verify,” zero trust is designed to protect modern environments by leveraging. Microsoft surface devices have zero trust security built in from chip to cloud. The definition of zero trust and the zero trust protect surface. Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): In zero trust, instead of focusing on the macro level of the attack surface, we determine what we need to protect: It’s outlining the “protect surface”—or what is most. Instead of assuming everything behind the corporate. Zero trust is a modern security strategy based on the principle never trust, always verify. How to initiate the zero trust implementation process by defining, analyzing, and. Learn how to shrink the attack surface and implement a zero trust security model for your network.
From www.globaldots.com
Zero Trust Explained Protect Surface Zero Trust Zero trust architecture secures the network from the inside out. Instead of assuming everything behind the corporate. Microsoft surface devices have zero trust security built in from chip to cloud. Rooted in the principle of “never trust, always verify,” zero trust is designed to protect modern environments by leveraging. The smallest possible reduction of the attack surface, or the protect. Protect Surface Zero Trust.
From ardalyst.com
AllThreat™ (Zero Trust) Architecture Ardalyst Protect Surface Zero Trust But what is the real first step toward implementing zero trust other than deciding to make the journey? Instead of assuming everything behind the corporate. Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): It’s outlining the “protect surface”—or what is most. How to initiate the. Protect Surface Zero Trust.
From www.insentragroup.com
The Ultimate Guide to Zero Trust United Kingdom Protect Surface Zero Trust But what is the real first step toward implementing zero trust other than deciding to make the journey? Instead of assuming everything behind the corporate. Learn how to shrink the attack surface and implement a zero trust security model for your network. It’s outlining the “protect surface”—or what is most. The definition of zero trust and the zero trust protect. Protect Surface Zero Trust.
From www.infotech.com
Build a Zero Trust Roadmap InfoTech Research Group Protect Surface Zero Trust The smallest possible reduction of the attack surface, or the protect surface. But what is the real first step toward implementing zero trust other than deciding to make the journey? Learn how to shrink the attack surface and implement a zero trust security model for your network. Typically, a zero trust network defines a protect surface based upon at least. Protect Surface Zero Trust.
From gcore.com
What Is Zero Trust? Zero Trust Security Explained Gcore Protect Surface Zero Trust Microsoft surface devices have zero trust security built in from chip to cloud. It professionals can count on layered zero trust. The smallest possible reduction of the attack surface, or the protect surface. Zero trust is a modern security strategy based on the principle never trust, always verify. The definition of zero trust and the zero trust protect surface. In. Protect Surface Zero Trust.
From www.serenoclouds.com
Microsoft Zero Trust Security Sereno Cloud Solution Protect Surface Zero Trust How to initiate the zero trust implementation process by defining, analyzing, and. Instead of assuming everything behind the corporate. The definition of zero trust and the zero trust protect surface. Microsoft surface devices have zero trust security built in from chip to cloud. It professionals can count on layered zero trust. In zero trust, instead of focusing on the macro. Protect Surface Zero Trust.
From www.splunk.com
A Zero Trust Security Approach for Government Increasing Security but Protect Surface Zero Trust Learn how to shrink the attack surface and implement a zero trust security model for your network. How to initiate the zero trust implementation process by defining, analyzing, and. The smallest possible reduction of the attack surface, or the protect surface. It professionals can count on layered zero trust. Instead of assuming everything behind the corporate. Zero trust architecture secures. Protect Surface Zero Trust.
From www.strongdm.com
What is Zero Trust? StrongDM Protect Surface Zero Trust The smallest possible reduction of the attack surface, or the protect surface. But what is the real first step toward implementing zero trust other than deciding to make the journey? Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): How to initiate the zero trust implementation. Protect Surface Zero Trust.
From www.youtube.com
Zero Trust Explained Cybersecurity Insights 17 YouTube Protect Surface Zero Trust Instead of assuming everything behind the corporate. Zero trust is a modern security strategy based on the principle never trust, always verify. Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): The smallest possible reduction of the attack surface, or the protect surface. The definition of. Protect Surface Zero Trust.
From www.paloaltonetworks.in
The Zero Trust Learning Curve Deploying Zero Trust One Step at a Time Protect Surface Zero Trust It professionals can count on layered zero trust. Instead of assuming everything behind the corporate. Rooted in the principle of “never trust, always verify,” zero trust is designed to protect modern environments by leveraging. Zero trust is a modern security strategy based on the principle never trust, always verify. But what is the real first step toward implementing zero trust. Protect Surface Zero Trust.
From www.infotech.com
Build a Zero Trust Roadmap InfoTech Research Group Protect Surface Zero Trust Zero trust is a modern security strategy based on the principle never trust, always verify. The definition of zero trust and the zero trust protect surface. Zero trust architecture secures the network from the inside out. How to initiate the zero trust implementation process by defining, analyzing, and. Microsoft surface devices have zero trust security built in from chip to. Protect Surface Zero Trust.
From www.sentinelone.com
What is Zero Trust Architecture? Protect Surface Zero Trust Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): The definition of zero trust and the zero trust protect surface. Learn how to shrink the attack surface and implement a zero trust security model for your network. But what is the real first step toward implementing. Protect Surface Zero Trust.
From onclavenetworks.com
What's Zero Trust? The Need for Zero Trust Protect Surface Zero Trust In zero trust, instead of focusing on the macro level of the attack surface, we determine what we need to protect: It professionals can count on layered zero trust. Learn how to shrink the attack surface and implement a zero trust security model for your network. Zero trust is a modern security strategy based on the principle never trust, always. Protect Surface Zero Trust.
From 10xds.com
Zero Trust security model Never Trust, Always Verify Protect Surface Zero Trust Microsoft surface devices have zero trust security built in from chip to cloud. In zero trust, instead of focusing on the macro level of the attack surface, we determine what we need to protect: The smallest possible reduction of the attack surface, or the protect surface. Instead of assuming everything behind the corporate. But what is the real first step. Protect Surface Zero Trust.
From www.csoonline.com
The ZeroTrust Pillars of Security CSO Online Protect Surface Zero Trust Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): Zero trust architecture secures the network from the inside out. But what is the real first step toward implementing zero trust other than deciding to make the journey? In zero trust, instead of focusing on the macro. Protect Surface Zero Trust.
From www.microsoft.com
Implementing a Zero Trust security model at Microsoft Protect Surface Zero Trust It professionals can count on layered zero trust. The definition of zero trust and the zero trust protect surface. It’s outlining the “protect surface”—or what is most. Instead of assuming everything behind the corporate. The smallest possible reduction of the attack surface, or the protect surface. In zero trust, instead of focusing on the macro level of the attack surface,. Protect Surface Zero Trust.
From www.filecloud.com
Zero Trust will be the Leading Strategy for Cybersecurity and Risk Protect Surface Zero Trust In zero trust, instead of focusing on the macro level of the attack surface, we determine what we need to protect: Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): Zero trust architecture secures the network from the inside out. Instead of assuming everything behind the. Protect Surface Zero Trust.
From pixelplex.io
How to Implement Zero Trust Architecture in 5 Steps [Checklist] Protect Surface Zero Trust Zero trust is a modern security strategy based on the principle never trust, always verify. Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): The smallest possible reduction of the attack surface, or the protect surface. Learn how to shrink the attack surface and implement a. Protect Surface Zero Trust.
From cloudsecurityalliance.org
Zero Trust Training Curriculum Overview CSA Protect Surface Zero Trust How to initiate the zero trust implementation process by defining, analyzing, and. Microsoft surface devices have zero trust security built in from chip to cloud. Instead of assuming everything behind the corporate. Rooted in the principle of “never trust, always verify,” zero trust is designed to protect modern environments by leveraging. In zero trust, instead of focusing on the macro. Protect Surface Zero Trust.
From dzone.com
Implementing Zero Trust Architecture on Azure Hybrid Cloud DZone Protect Surface Zero Trust It’s outlining the “protect surface”—or what is most. Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): Zero trust architecture secures the network from the inside out. The smallest possible reduction of the attack surface, or the protect surface. In zero trust, instead of focusing on. Protect Surface Zero Trust.
From www.translucentcomputing.com
Why is ZERO TRUST SECURITY important for your business? Translucent Protect Surface Zero Trust The smallest possible reduction of the attack surface, or the protect surface. Zero trust is a modern security strategy based on the principle never trust, always verify. Learn how to shrink the attack surface and implement a zero trust security model for your network. Instead of assuming everything behind the corporate. The definition of zero trust and the zero trust. Protect Surface Zero Trust.
From on2it.net
ON2IT Zero Trust Innovators Zero Trust Innovators Protect Surface Zero Trust Microsoft surface devices have zero trust security built in from chip to cloud. Zero trust architecture secures the network from the inside out. The smallest possible reduction of the attack surface, or the protect surface. Rooted in the principle of “never trust, always verify,” zero trust is designed to protect modern environments by leveraging. In zero trust, instead of focusing. Protect Surface Zero Trust.
From sudoconsultants.com
Implement Zero Trust on AWS SUDO Consultants Protect Surface Zero Trust Microsoft surface devices have zero trust security built in from chip to cloud. In zero trust, instead of focusing on the macro level of the attack surface, we determine what we need to protect: Rooted in the principle of “never trust, always verify,” zero trust is designed to protect modern environments by leveraging. Zero trust architecture secures the network from. Protect Surface Zero Trust.
From www.infotech.com
Build a Zero Trust Roadmap InfoTech Research Group Protect Surface Zero Trust The definition of zero trust and the zero trust protect surface. It’s outlining the “protect surface”—or what is most. Learn how to shrink the attack surface and implement a zero trust security model for your network. Zero trust is a modern security strategy based on the principle never trust, always verify. Instead of assuming everything behind the corporate. Zero trust. Protect Surface Zero Trust.
From tekmart.co.za
The 5 principles of zerotrust security tBlog Protect Surface Zero Trust The definition of zero trust and the zero trust protect surface. Learn how to shrink the attack surface and implement a zero trust security model for your network. The smallest possible reduction of the attack surface, or the protect surface. Zero trust architecture secures the network from the inside out. Typically, a zero trust network defines a protect surface based. Protect Surface Zero Trust.
From www.splunk.com
Zero Trust Security Model In Government Splunk Protect Surface Zero Trust It’s outlining the “protect surface”—or what is most. Instead of assuming everything behind the corporate. It professionals can count on layered zero trust. How to initiate the zero trust implementation process by defining, analyzing, and. Microsoft surface devices have zero trust security built in from chip to cloud. Zero trust architecture secures the network from the inside out. Typically, a. Protect Surface Zero Trust.
From www.manageengine.com
Zero Trust Security Explained Zero Trust Components & Implementation Protect Surface Zero Trust The smallest possible reduction of the attack surface, or the protect surface. The definition of zero trust and the zero trust protect surface. Instead of assuming everything behind the corporate. In zero trust, instead of focusing on the macro level of the attack surface, we determine what we need to protect: Zero trust is a modern security strategy based on. Protect Surface Zero Trust.
From blog.barracuda.com
The Zero Trust Maturity Model Protect Surface Zero Trust Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): Rooted in the principle of “never trust, always verify,” zero trust is designed to protect modern environments by leveraging. Zero trust architecture secures the network from the inside out. How to initiate the zero trust implementation process. Protect Surface Zero Trust.
From vertikal6.com
What is Zero Trust Security Architecture A Framework for More Protect Surface Zero Trust Zero trust architecture secures the network from the inside out. But what is the real first step toward implementing zero trust other than deciding to make the journey? It’s outlining the “protect surface”—or what is most. The definition of zero trust and the zero trust protect surface. Microsoft surface devices have zero trust security built in from chip to cloud.. Protect Surface Zero Trust.
From www.optiv.com
Zero Trust Attack Surface Management Five Easy Steps Optiv Protect Surface Zero Trust Instead of assuming everything behind the corporate. Microsoft surface devices have zero trust security built in from chip to cloud. Learn how to shrink the attack surface and implement a zero trust security model for your network. The definition of zero trust and the zero trust protect surface. Rooted in the principle of “never trust, always verify,” zero trust is. Protect Surface Zero Trust.
From www.paloaltonetworks.com
The Need for Zero Trust for Enterprise Public Cloud Protect Surface Zero Trust Zero trust is a modern security strategy based on the principle never trust, always verify. Zero trust architecture secures the network from the inside out. Learn how to shrink the attack surface and implement a zero trust security model for your network. Rooted in the principle of “never trust, always verify,” zero trust is designed to protect modern environments by. Protect Surface Zero Trust.
From zpesystems.com
Zero Trust Security Framework ZPE Systems Protect Surface Zero Trust It professionals can count on layered zero trust. The smallest possible reduction of the attack surface, or the protect surface. Zero trust is a modern security strategy based on the principle never trust, always verify. Learn how to shrink the attack surface and implement a zero trust security model for your network. How to initiate the zero trust implementation process. Protect Surface Zero Trust.
From logrhythm.com
Embracing a Zero Trust Security Model LogRhythm Protect Surface Zero Trust Learn how to shrink the attack surface and implement a zero trust security model for your network. The definition of zero trust and the zero trust protect surface. But what is the real first step toward implementing zero trust other than deciding to make the journey? The smallest possible reduction of the attack surface, or the protect surface. It professionals. Protect Surface Zero Trust.
From www.techtarget.com
The 7 Core Pillars of a ZeroTrust Architecture Protect Surface Zero Trust In zero trust, instead of focusing on the macro level of the attack surface, we determine what we need to protect: Zero trust is a modern security strategy based on the principle never trust, always verify. Typically, a zero trust network defines a protect surface based upon at least one of these four things (remembered by the acronym daas): Zero. Protect Surface Zero Trust.