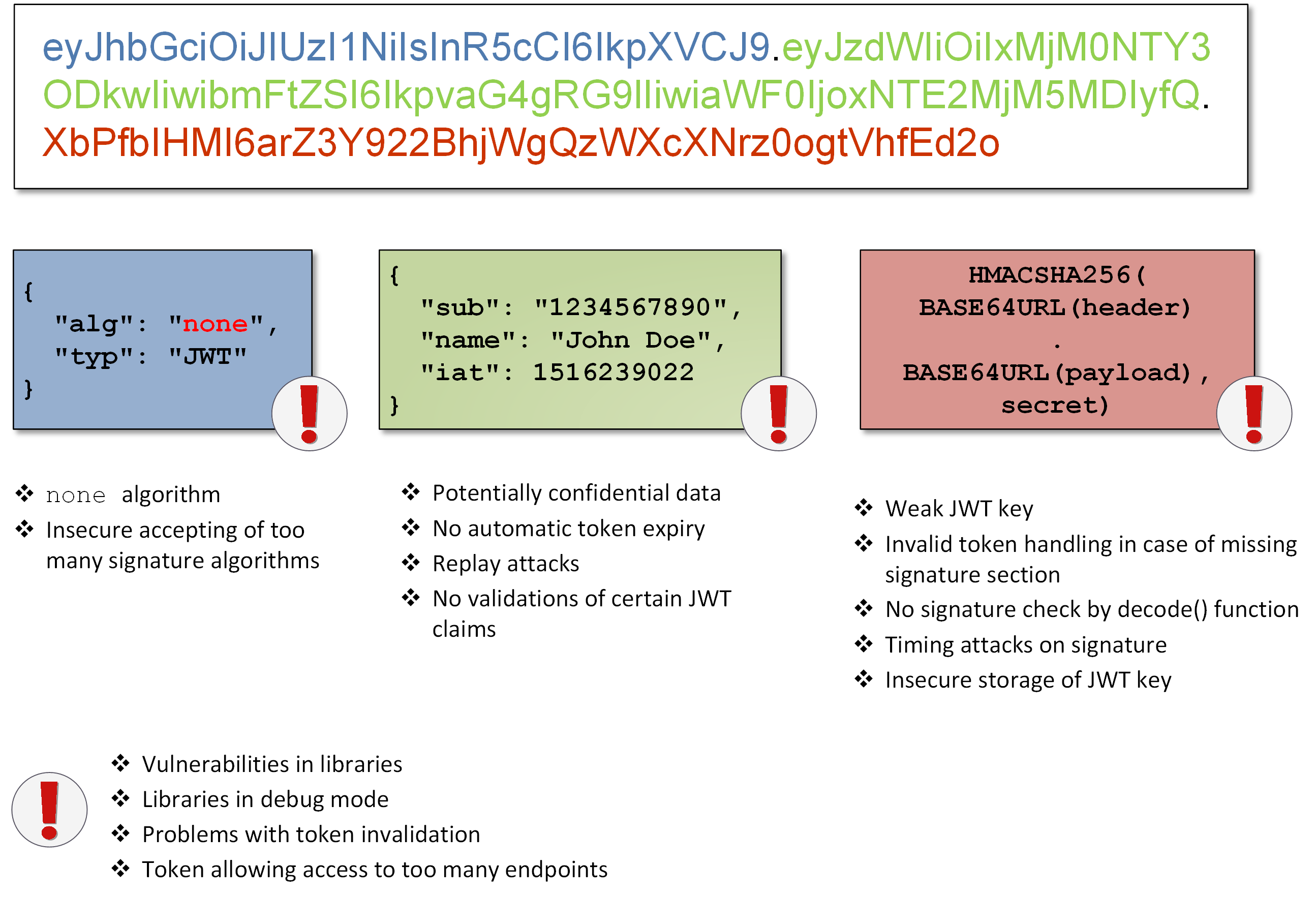
Security Issues With Jwt . a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. which libraries are vulnerable to attacks and how to prevent them. jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. Protection of the crypto keys (server side). organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. See jwt.io for more information on the vulnerable libraries. An attacker can create a jwt with a modified.
from research.securitum.com
See jwt.io for more information on the vulnerable libraries. which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. Protection of the crypto keys (server side). jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. An attacker can create a jwt with a modified.
JWT (JSON Token) (in)security
Security Issues With Jwt See jwt.io for more information on the vulnerable libraries. jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. which libraries are vulnerable to attacks and how to prevent them. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. An attacker can create a jwt with a modified. this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. See jwt.io for more information on the vulnerable libraries. Protection of the crypto keys (server side).
From velog.io
[Spring] Security JWT Security Issues With Jwt which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. An attacker can create a jwt with a modified. See jwt.io for more information on the vulnerable libraries. this article shows some best practices for using jwts so that you. Security Issues With Jwt.
From apisecurity.io
Issue 112 Vulnerability in Paginator, Microsoft RESTLer, talks on API Security Issues With Jwt this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. Protection of the crypto keys (server side). a guide for using jwt authentication to prevent basic security issues while. Security Issues With Jwt.
From github.com
Security Issue Authorization bypass · Issue 489 · dgrijalva/jwtgo Security Issues With Jwt organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. See jwt.io for more information on the vulnerable libraries. Protection of the crypto keys (server side). this article shows some best practices. Security Issues With Jwt.
From gamma.app
Java Security JWT vs JSession_ID Security Issues With Jwt a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. Protection of the crypto keys (server side). organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. this article shows some best practices for using jwts so that you can maintain a high level. Security Issues With Jwt.
From github.com
securityjwt/application.properties at master · Rodsafreitas/security Security Issues With Jwt jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. Protection of the crypto keys (server side). organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings. Security Issues With Jwt.
From github.com
A JWT secret must be defined grails.plugin.springsecurity.conf.rest Security Issues With Jwt Protection of the crypto keys (server side). which libraries are vulnerable to attacks and how to prevent them. jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. See jwt.io for. Security Issues With Jwt.
From www.toptal.com
Spring Security Tutorial REST Security with JWT Toptal Security Issues With Jwt Protection of the crypto keys (server side). See jwt.io for more information on the vulnerable libraries. jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure. Security Issues With Jwt.
From research.securitum.com
JWT (JSON Token) (in)security Security Issues With Jwt which libraries are vulnerable to attacks and how to prevent them. See jwt.io for more information on the vulnerable libraries. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. An attacker can create. Security Issues With Jwt.
From docs.cyberark.com
JWT Authentication Security Issues With Jwt a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. which libraries are vulnerable to attacks and how to prevent them. An attacker can create a jwt with. Security Issues With Jwt.
From github.com
java.security.spec.InvalidKeySpecException encoded key spec not Security Issues With Jwt organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. See jwt.io for more information on the vulnerable libraries. An attacker can create a jwt with a modified. Protection of the crypto keys (server side).. Security Issues With Jwt.
From toptal.com
Spring Security Tutorial REST Security with JWT Toptal Security Issues With Jwt which libraries are vulnerable to attacks and how to prevent them. this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. See jwt.io for more information. Security Issues With Jwt.
From github.com
[Security Issue] Auth JWT does not have expiration time and is sent in Security Issues With Jwt a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. An attacker can create a jwt with a modified. which libraries are vulnerable to attacks and how to. Security Issues With Jwt.
From www.eclipse.org
Stateless security with MicroProfile JWT The Eclipse Foundation Security Issues With Jwt this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json. Security Issues With Jwt.
From apisecurity.io
Issue 56 Common JWT Attacks, OWASP API Security Top 10 cheat sheet Security Issues With Jwt which libraries are vulnerable to attacks and how to prevent them. An attacker can create a jwt with a modified. Protection of the crypto keys (server side). See jwt.io for more information on the vulnerable libraries. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. jwts play a critical. Security Issues With Jwt.
From github.com
Security Issues With Jwt Protection of the crypto keys (server side). organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. See jwt.io for more information on the vulnerable libraries. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. jwts play a critical role in web and. Security Issues With Jwt.
From brunofuga.adv.br
Spring Boot Security And JWT Tutorial With Example BezKoder, 47 OFF Security Issues With Jwt a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. which libraries are vulnerable to attacks and how to prevent them. See jwt.io for more information on the vulnerable libraries. Protection of the crypto keys (server side). jwts play a critical role in web and api security by providing a. Security Issues With Jwt.
From research.securitum.com
JWT (JSON Token) (in)security Security Issues With Jwt An attacker can create a jwt with a modified. which libraries are vulnerable to attacks and how to prevent them. jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. See. Security Issues With Jwt.
From docs.workato.com
JWT Token Workato Docs Security Issues With Jwt which libraries are vulnerable to attacks and how to prevent them. An attacker can create a jwt with a modified. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. See jwt.io for more information on the vulnerable libraries. this article shows some best practices for using jwts so that you. Security Issues With Jwt.
From github.com
GitHub pagadalarupa/vivrity_jwt_security Security Issues With Jwt See jwt.io for more information on the vulnerable libraries. this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. which libraries are vulnerable to attacks and how to. Security Issues With Jwt.
From www.onlyoffice.com
How JWT protects your documents ONLYOFFICE Blog Security Issues With Jwt this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json web token. Security Issues With Jwt.
From www.pingidentity.com
The Hard Parts of JWT Security Nobody Talks About Security Issues With Jwt jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. An attacker can create a jwt with a modified. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. which libraries are vulnerable to attacks and how to prevent them. Protection. Security Issues With Jwt.
From github.com
Critical Security Fix Required You disclose the correct signature with Security Issues With Jwt a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. which libraries are vulnerable to attacks and how to prevent them. jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. this article shows some best practices for using jwts. Security Issues With Jwt.
From buraktas.com
Spring Security with JWT Tutorial Burak Aktas Security Issues With Jwt a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. See jwt.io for more information on the vulnerable libraries. which libraries are vulnerable to attacks and how to. Security Issues With Jwt.
From auth0.com
A Look at The Draft for JWT Best Current Practices Security Issues With Jwt this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. See jwt.io for more information on the vulnerable libraries. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. a guide for using jwt authentication to prevent basic security. Security Issues With Jwt.
From devpress.csdn.net
Sessions vs JWTs A Complete Guide to Authentication_weixin_0010034Redis Security Issues With Jwt this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,.. Security Issues With Jwt.
From www.cnblogs.com
How JWT (JSON Token) authentication works? 威少 博客园 Security Issues With Jwt this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. Protection of the crypto keys (server side). organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. a guide for using jwt authentication to prevent basic security issues while. Security Issues With Jwt.
From github.com
GitHub NetDevPack/Security.Jwt Jwt Manager. Set of components to Security Issues With Jwt An attacker can create a jwt with a modified. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. See jwt.io for more information on the vulnerable libraries. this article shows some best practices. Security Issues With Jwt.
From www.youtube.com
[HINDI] Introduction to JWT JSON Token Security Concerns of JWT Security Issues With Jwt An attacker can create a jwt with a modified. which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. Protection of the crypto keys (server side). this article shows some best practices for using jwts so that you can maintain. Security Issues With Jwt.
From dzone.com
JWT Token Lightweight, TokenBased Authentication DZone Security Security Issues With Jwt jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. Protection of the crypto keys (server side). this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. a guide for using jwt authentication to prevent basic. Security Issues With Jwt.
From github.com
jwtsecurityexample/application.properties at master · TechPrimers/jwt Security Issues With Jwt a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. Protection of the crypto keys (server side). See jwt.io for more information on the vulnerable libraries. which libraries are vulnerable to. Security Issues With Jwt.
From content.noroff.dev
JWT Noroff Frontend Development Security Issues With Jwt which libraries are vulnerable to attacks and how to prevent them. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. An attacker can create a jwt with a. Security Issues With Jwt.
From infosecwriteups.com
All About Attacking JWT. JWT The Weak Link in Your Security… by Security Issues With Jwt See jwt.io for more information on the vulnerable libraries. jwts play a critical role in web and api security by providing a method for authenticating and authorizing users. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. Protection of the crypto keys (server side). which libraries are vulnerable to attacks. Security Issues With Jwt.
From www.pinterest.com
Using JWT to authenticate and authorize requests in Postman in 2022 Security Issues With Jwt a guide for using jwt authentication to prevent basic security issues while understanding the shortcomings of jwts. this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. which libraries are vulnerable to attacks and how to prevent them. jwts play a critical role in. Security Issues With Jwt.
From www.wallarm.com
💥OAuth vs JWT What is the Difference? Security Issues With Jwt An attacker can create a jwt with a modified. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. which libraries are vulnerable to attacks and how to prevent them. Protection of the crypto keys (server side). a guide for using jwt authentication to prevent basic security issues while understanding the. Security Issues With Jwt.
From medium.com
Implementing JWT with Spring Boot and Spring Security Security Issues With Jwt this article shows some best practices for using jwts so that you can maintain a high level of security in your applications. organizations can mitigate json web token (jwt) vulnerabilities by implementing secure token generation and validation procedures,. An attacker can create a jwt with a modified. Protection of the crypto keys (server side). a guide for. Security Issues With Jwt.