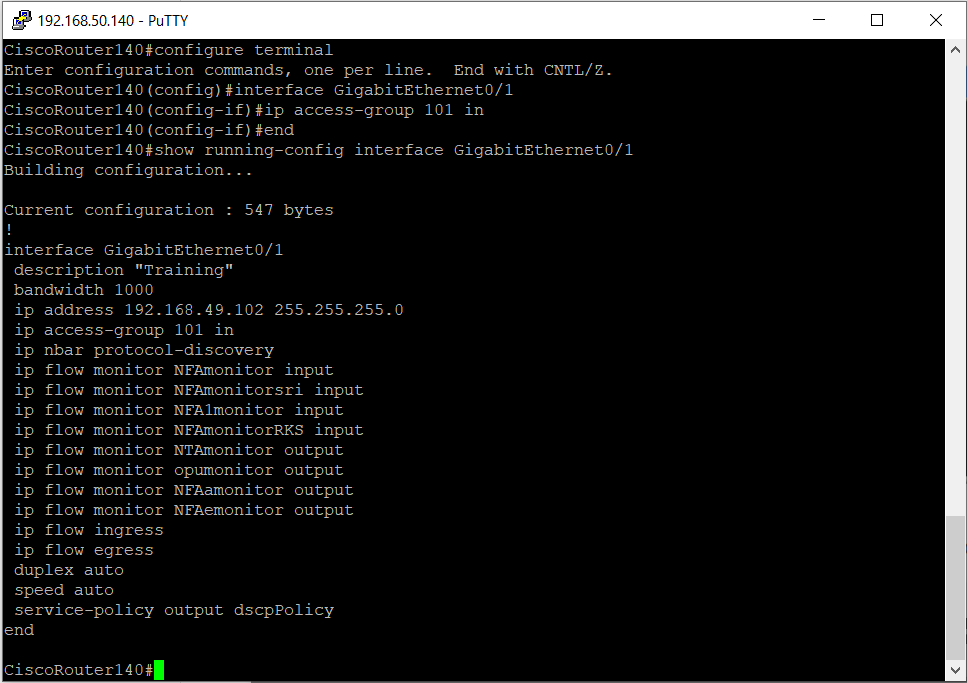
Network Acl Logs . One way to get much. They are essential for maintaining. Access control lists (acls) are a fundamental network security and management component. Acls act as a gatekeeper,. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. Use the acl log screen to view logs for access lists (acls) configured on a router. You can use the default network acl for your vpc, or you can create a custom network acl for your. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. Routers collect acl logs every 10 minutes.
from www.manageengine.com
One way to get much. They are essential for maintaining. Use the acl log screen to view logs for access lists (acls) configured on a router. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. Routers collect acl logs every 10 minutes. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. You can use the default network acl for your vpc, or you can create a custom network acl for your. Acls act as a gatekeeper,. Access control lists (acls) are a fundamental network security and management component. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level.
Cisco Access Control Software Cisco ACL List ManageEngine Network
Network Acl Logs Routers collect acl logs every 10 minutes. Acls act as a gatekeeper,. Routers collect acl logs every 10 minutes. Use the acl log screen to view logs for access lists (acls) configured on a router. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. They are essential for maintaining. You can use the default network acl for your vpc, or you can create a custom network acl for your. Access control lists (acls) are a fundamental network security and management component. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. One way to get much. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level.
From cloudiofy.com
How to control network traffic using Network ACL Network Acl Logs One way to get much. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. Access control lists (acls) are a fundamental network security and management component. They are essential for maintaining. You can use the default network acl for your vpc, or. Network Acl Logs.
From www.alibabacloud.com
Overview of network ACLs Virtual Private Cloud Alibaba Cloud Network Acl Logs They are essential for maintaining. Routers collect acl logs every 10 minutes. You can use the default network acl for your vpc, or you can create a custom network acl for your. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. Use the acl log screen to view logs for access. Network Acl Logs.
From www.sash.jp
DHCP & ACL Logs Network Acl Logs You can use the default network acl for your vpc, or you can create a custom network acl for your. One way to get much. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. A network access control list (acl) allows or denies specific inbound or outbound. Network Acl Logs.
From harvestingclouds.com
Azure for AWS professionals Networking AWS 04 Network ACLs Network Acl Logs A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. Use the acl log screen to view logs for access lists (acls) configured on a router. Routers collect acl logs every 10 minutes. They are essential for maintaining. Access control lists (acls) are a fundamental network security and management component. Acls act. Network Acl Logs.
From www.manageengine.com
Cisco Access Control Software Cisco ACL List ManageEngine Network Network Acl Logs As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. One way to get much. Access control lists (acls) are a fundamental network security and management component. Using acl logging can be a very useful tool not only to get info about whats. Network Acl Logs.
From networkustad.com
How to Configure Standard ACL to Secure a VTY Port » NetworkUstad Network Acl Logs Acls act as a gatekeeper,. They are essential for maintaining. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. One way to get much.. Network Acl Logs.
From serverfault.com
networking AWS Error accessing the with a custom Network Network Acl Logs A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. Access control lists (acls) are a fundamental network security and management component. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. Use the acl log screen to view logs. Network Acl Logs.
From www.manageengine.com
Cisco Access Control Software Cisco ACL List ManageEngine Network Network Acl Logs Acls act as a gatekeeper,. They are essential for maintaining. Routers collect acl logs every 10 minutes. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. You can use the default network acl for your vpc, or you can create a custom network acl for your. One. Network Acl Logs.
From aws.amazon.com
How to Help Prepare for DDoS Attacks by Reducing Your Attack Surface Network Acl Logs One way to get much. They are essential for maintaining. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. Acls act as a gatekeeper,. Routers collect acl logs every 10 minutes. Using acl logging can be a very useful tool not only. Network Acl Logs.
From www.youtube.com
What is ACL ( Access Control List ) ACL in networking Standard Network Acl Logs As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. One way to get much. Access control lists (acls) are a fundamental network security and management component. Routers collect acl logs every 10 minutes. Use the acl log screen to view logs for. Network Acl Logs.
From medium.com
Learn AWS Network ACL and Security Groups in 5 minutes Network Acl Logs Routers collect acl logs every 10 minutes. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. A network access control. Network Acl Logs.
From community.cisco.com
ASA IDFW (Identity Firewall) Step by Step configuration Cisco Community Network Acl Logs Use the acl log screen to view logs for access lists (acls) configured on a router. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. Access control lists (acls). Network Acl Logs.
From www.agilevision.io
AWS Networking connectivity, network ACLs, and security groups Network Acl Logs One way to get much. Access control lists (acls) are a fundamental network security and management component. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. Routers collect acl logs every 10 minutes. Acls act as a gatekeeper,. Using acl logging can. Network Acl Logs.
From cloudiofy.com
How to control network traffic using Network ACL Network Acl Logs Use the acl log screen to view logs for access lists (acls) configured on a router. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network. Network Acl Logs.
From codilime.com
Network ACL processing algorithms—optimizing firewall Network Acl Logs Acls act as a gatekeeper,. Routers collect acl logs every 10 minutes. They are essential for maintaining. Use the acl log screen to view logs for access lists (acls) configured on a router. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. As an integral part of network security, access control. Network Acl Logs.
From networkustad.com
How to Configure standard ACLs » NetworkUstad Network Acl Logs As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. Use the acl log screen to view logs for access lists. Network Acl Logs.
From www.slideserve.com
PPT Computer Security Network + Link Layer Security + Network Network Acl Logs A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. They are essential for maintaining. One way to get much. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. Routers collect acl logs every. Network Acl Logs.
From www.youtube.com
Network ACL (Access Control List) This is how you can use Standard Network Acl Logs One way to get much. You can use the default network acl for your vpc, or you can create a custom network acl for your. Acls act as a gatekeeper,. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. Use the acl. Network Acl Logs.
From www.agilevision.io
AWS Networking connectivity, network ACLs, and security groups Network Acl Logs Acls act as a gatekeeper,. Access control lists (acls) are a fundamental network security and management component. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. You can use. Network Acl Logs.
From www.youtube.com
Configuring cisco extended acl / extended named access control list Network Acl Logs You can use the default network acl for your vpc, or you can create a custom network acl for your. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. Use the acl log screen to view logs for access lists (acls) configured on a router. Access control. Network Acl Logs.
From techcommunity.microsoft.com
Active Directory Access Control List Attacks and Defense Microsoft Network Acl Logs As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. Routers collect acl logs every 10 minutes. Access control lists (acls) are a fundamental network security and management component. A network access control list (acl) allows or denies specific inbound or outbound traffic. Network Acl Logs.
From techhub.hpe.com
Enabling ACL logging on the switch Network Acl Logs Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. They are essential for maintaining. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. Use the acl log screen to view logs for access lists (acls) configured on a. Network Acl Logs.
From www.youtube.com
Configure Cisco Extended ACL/ Extended Numbered Access Control List ACL Network Acl Logs Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. Acls act as a gatekeeper,. One way to get much. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. Use the acl log screen to view logs for access. Network Acl Logs.
From www.ccnaacademy.com
Access Control Lists (ACLs) What They Are and How to Configure Them Network Acl Logs Routers collect acl logs every 10 minutes. One way to get much. They are essential for maintaining. Access control lists (acls) are a fundamental network security and management component. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. You can use the. Network Acl Logs.
From www.wiresandwi.fi
Cisco ISE MidUpgrade ACL (IOS/IOSXE) for Testing New ISE Deployment Network Acl Logs Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic. Network Acl Logs.
From www.youtube.com
Learn AWS VPC Route Table, Gateway, Network ACL, Security Network Acl Logs Routers collect acl logs every 10 minutes. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. Access control lists (acls) are a fundamental network security and management component. Use the acl log screen to view logs for access lists (acls) configured on a router. A network access. Network Acl Logs.
From www.securew2.com
Windows Access Control ACL, DACL, SACL, & ACE Network Acl Logs Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. You can use the default network acl for your vpc, or you can create a custom network acl for your. Use the acl log screen to view logs for access lists (acls) configured on a router. A network. Network Acl Logs.
From learnwithaniket.com
Network Access Control List (NACL) — Learn with Aniket Network Acl Logs Acls act as a gatekeeper,. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. Use the acl log screen to view logs for access lists (acls) configured on a router. You can use the default network acl for your vpc, or you can create a custom network. Network Acl Logs.
From pynetlabsnetwork.blogspot.com
What is Access Control List (ACL)? Network Acl Logs One way to get much. Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. Access control lists (acls) are a fundamental network security and management component. You can use the default network acl for your vpc, or you can create a custom network acl for your. Use. Network Acl Logs.
From cloudiofy.com
How to control network traffic using Network ACL Network Acl Logs One way to get much. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. Routers collect acl logs every 10 minutes. They are essential. Network Acl Logs.
From www.pinterest.com
ACL number Ccna, Network engineer, Osi model Network Acl Logs You can use the default network acl for your vpc, or you can create a custom network acl for your. Routers collect acl logs every 10 minutes. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. One way to get much. Use the acl log screen to view logs for access. Network Acl Logs.
From www.freecodecamp.org
What is An ACL? Access Control Lists Explained Network Acl Logs Using acl logging can be a very useful tool not only to get info about whats going on, but also for troubleshooting. Access control lists (acls) are a fundamental network security and management component. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network. Network Acl Logs.
From vinasupport.com
[AWS] Tìm hiểu về Network ACLs Một layer bảo mật VPC trong AWS Network Acl Logs They are essential for maintaining. Use the acl log screen to view logs for access lists (acls) configured on a router. A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. Routers collect acl logs every 10 minutes. You can use the default network acl for your vpc, or you can create. Network Acl Logs.
From cloudiofy.com
How to control network traffic using Network ACL Network Acl Logs A network access control list (acl) allows or denies specific inbound or outbound traffic at the subnet level. You can use the default network acl for your vpc, or you can create a custom network acl for your. They are essential for maintaining. Acls act as a gatekeeper,. Use the acl log screen to view logs for access lists (acls). Network Acl Logs.
From loemzkqeu.blob.core.windows.net
Network Acl Id at Grace blog Network Acl Logs Routers collect acl logs every 10 minutes. Use the acl log screen to view logs for access lists (acls) configured on a router. One way to get much. As an integral part of network security, access control lists (acls) play a crucial role in regulating and enforcing traffic flow in and out of network devices. They are essential for maintaining.. Network Acl Logs.