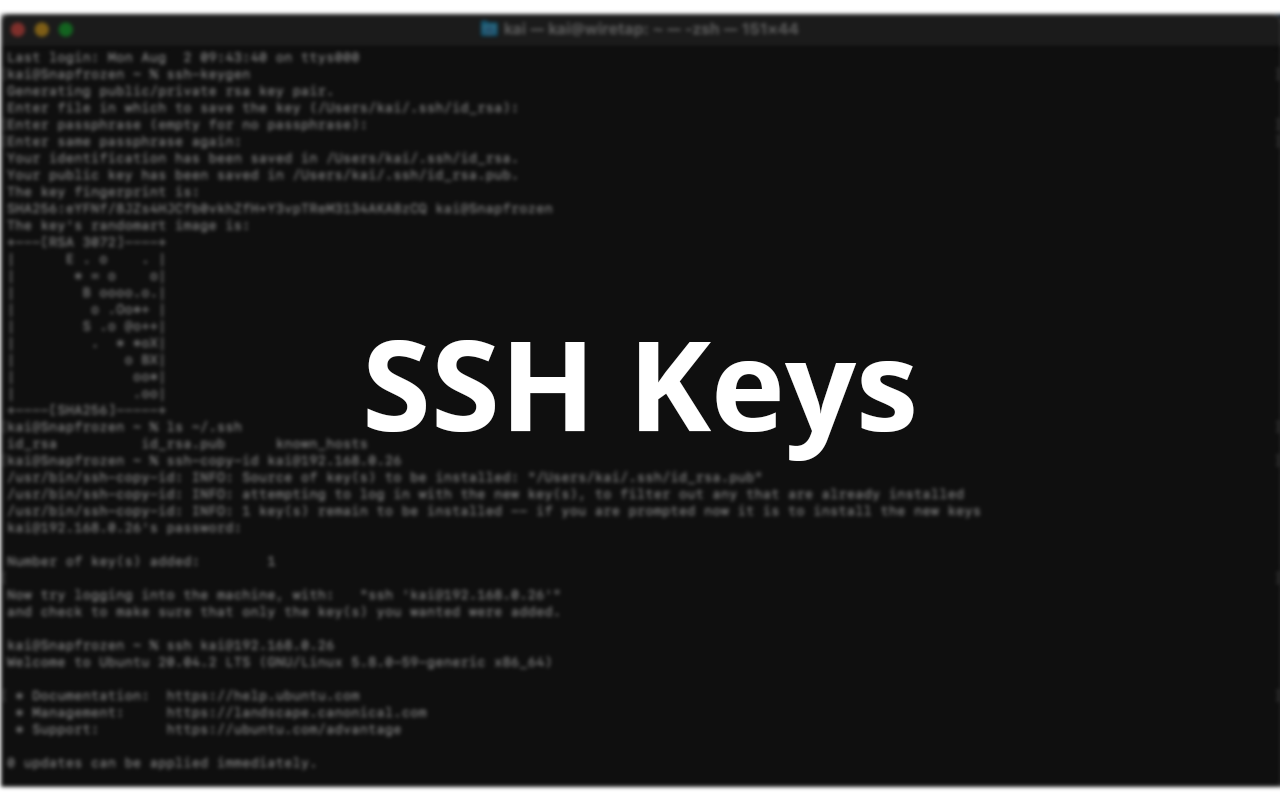
Ssh Keys Networking . The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. Learn best practices and tips for handling ssh keys efficiently. Welcome to our ultimate guide to setting up ssh (secure shell) keys. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. You may already have an ssh key, but it doesn't hurt to create a new one. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. The client creates a key pair and then uploads the public. To log in securely to another computer without a password, you must have an ssh key. Ssh key pairs can be used to authenticate a client to a server.
from www.snapfrozen.com.au
Welcome to our ultimate guide to setting up ssh (secure shell) keys. You may already have an ssh key, but it doesn't hurt to create a new one. The client creates a key pair and then uploads the public. The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. Ssh key pairs can be used to authenticate a client to a server. Learn best practices and tips for handling ssh keys efficiently. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. To log in securely to another computer without a password, you must have an ssh key. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys.
How to setup and use SSH keys Snapfrozen
Ssh Keys Networking You may already have an ssh key, but it doesn't hurt to create a new one. To log in securely to another computer without a password, you must have an ssh key. The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. You may already have an ssh key, but it doesn't hurt to create a new one. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. Welcome to our ultimate guide to setting up ssh (secure shell) keys. Ssh key pairs can be used to authenticate a client to a server. Learn best practices and tips for handling ssh keys efficiently. The client creates a key pair and then uploads the public.
From wpengine.com
Getting Started with SSH Gateway WP Engine® Ssh Keys Networking Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. Learn best practices and tips for handling ssh keys efficiently. Welcome to our ultimate guide to setting up ssh (secure shell) keys. Ssh key pairs. Ssh Keys Networking.
From www.geeksforgeeks.org
How to use SSH to connect to a remote server in Linux ssh Command Ssh Keys Networking Welcome to our ultimate guide to setting up ssh (secure shell) keys. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. Ssh key pairs can be used to authenticate a client to a server. The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between. Ssh Keys Networking.
From www.stackscale.com
Guide to setting up SSH keys on a Linux server [Tutorial] Ssh Keys Networking Ssh key pairs can be used to authenticate a client to a server. You may already have an ssh key, but it doesn't hurt to create a new one. The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. Welcome to our ultimate guide to setting up ssh (secure shell) keys. Learn best. Ssh Keys Networking.
From inspirezone.tech
Git SSH keys simplified and how to setup on GitHub Ssh Keys Networking The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. The client creates a key pair and then uploads the public. You may already have an ssh key, but it doesn't hurt to create. Ssh Keys Networking.
From www.keycdn.com
How to Create an SSH Key KeyCDN Support Ssh Keys Networking To log in securely to another computer without a password, you must have an ssh key. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. The client creates a key pair and then uploads the public. This tutorial will walk you through the basics of creating ssh keys, and also how to manage. Ssh Keys Networking.
From blog.ishosting.com
SSH Сonnecting to a Server How to Сreate a Key Ssh Keys Networking This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. You may already have an ssh key, but it doesn't hurt to create a new one. Learn best practices and tips for handling ssh. Ssh Keys Networking.
From www.slideserve.com
PPT SSH Key Authentication PowerPoint Presentation, free download Ssh Keys Networking To log in securely to another computer without a password, you must have an ssh key. The client creates a key pair and then uploads the public. Welcome to our ultimate guide to setting up ssh (secure shell) keys. Ssh key pairs can be used to authenticate a client to a server. Discover 13 simple ways to effectively manage ssh. Ssh Keys Networking.
From ulhpc-tutorials.readthedocs.io
SSH and OpenOnDemand UL HPC Tutorials Ssh Keys Networking The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. Ssh key pairs can be used to authenticate a client to a server. The client creates a key pair and then uploads the public. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys.. Ssh Keys Networking.
From p8t.net
SSH Keys All You Need to Know About Managing Them P8t Ssh Keys Networking Ssh key pairs can be used to authenticate a client to a server. The client creates a key pair and then uploads the public. You may already have an ssh key, but it doesn't hurt to create a new one. Learn best practices and tips for handling ssh keys efficiently. The secure shell (ssh) protocol sets up encrypted connections for. Ssh Keys Networking.
From www.youtube.com
How does the SSH protocol work? YouTube Ssh Keys Networking The client creates a key pair and then uploads the public. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. To log in securely to another computer without a password, you must have an ssh key. Ssh key pairs can be used to authenticate a client to a server. Learn best practices and. Ssh Keys Networking.
From spectralops.io
The complete guide to SSH keys in GitLab Spectral Ssh Keys Networking Welcome to our ultimate guide to setting up ssh (secure shell) keys. The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. You may already have an ssh key, but it doesn't hurt to create a new one. Ssh key pairs can be used to authenticate a client to a server. This tutorial. Ssh Keys Networking.
From upcloud.com
How to use SSH keys for authentication UpCloud Ssh Keys Networking Welcome to our ultimate guide to setting up ssh (secure shell) keys. The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. You may already have an ssh key, but it doesn't hurt to create a new one. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access. Ssh Keys Networking.
From www.omnisecu.com
How SSH works Ssh Keys Networking Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. Ssh key pairs can be used to authenticate a client to a server. You may already have an ssh key, but it doesn't hurt to create a new one. The client creates a key pair and then uploads the public. This tutorial will walk. Ssh Keys Networking.
From www.sectigo.com
SSH Key Pair Explained How SSH Private & Public Keys Work Sectigo Ssh Keys Networking You may already have an ssh key, but it doesn't hurt to create a new one. The client creates a key pair and then uploads the public. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. Welcome to our ultimate guide to setting up ssh (secure shell) keys. To log. Ssh Keys Networking.
From www.manageengine.com
Consolidate the SSH keys ManageEngine Key Manager Plus Ssh Keys Networking Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. To log in securely to another computer without a password, you must have an ssh key. Ssh key pairs can be used to authenticate a client to a server. Welcome to our ultimate guide to setting up ssh (secure shell) keys. Learn best practices. Ssh Keys Networking.
From www.ssh.com
What is an SSH Key? An Overview of SSH Keys Ssh Keys Networking This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. Learn best practices and tips for handling ssh keys efficiently. The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined. Ssh Keys Networking.
From iot.samteck.net
What are SSH Keys and How to use them Of Things Ssh Keys Networking To log in securely to another computer without a password, you must have an ssh key. You may already have an ssh key, but it doesn't hurt to create a new one. Learn best practices and tips for handling ssh keys efficiently. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. Welcome to. Ssh Keys Networking.
From www.cloudns.net
What is SSH? ClouDNS Blog Ssh Keys Networking To log in securely to another computer without a password, you must have an ssh key. Welcome to our ultimate guide to setting up ssh (secure shell) keys. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. Learn best practices and tips for handling ssh keys efficiently. The secure shell (ssh) protocol sets. Ssh Keys Networking.
From www.nodespace.com
How to Setup SSH Key Authentication on Linux Servers NodeSpace Ssh Keys Networking To log in securely to another computer without a password, you must have an ssh key. You may already have an ssh key, but it doesn't hurt to create a new one. Learn best practices and tips for handling ssh keys efficiently. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple. Ssh Keys Networking.
From contabo.com
How to Use SSH Keys with Your Server Contabo Blog Ssh Keys Networking The client creates a key pair and then uploads the public. The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. To log in securely to another computer without a password, you must have. Ssh Keys Networking.
From www.youtube.com
How to generate SSH key pair using sshkeygen YouTube Ssh Keys Networking You may already have an ssh key, but it doesn't hurt to create a new one. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. Welcome to our ultimate guide to setting up ssh. Ssh Keys Networking.
From www.slideserve.com
PPT Management System of SSH Keys!! PowerPoint Presentation, free Ssh Keys Networking This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. Ssh key pairs can be used to authenticate a client to a server. To log in securely to another computer without a password, you must have an ssh key. The client creates a key pair and then uploads the public. Discover. Ssh Keys Networking.
From techacad.net
How To Set Up SSH Keys With YubiKey as twofactor authentication (U2F Ssh Keys Networking You may already have an ssh key, but it doesn't hurt to create a new one. Welcome to our ultimate guide to setting up ssh (secure shell) keys. To log in securely to another computer without a password, you must have an ssh key. The client creates a key pair and then uploads the public. Discover 13 simple ways to. Ssh Keys Networking.
From unifiedguru.com
How to View Your SSH Keys in Linux, macOS and Windows Unified Networking Ssh Keys Networking The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. Ssh key pairs can be used to authenticate a client to a server. To log in securely to another computer without a password, you. Ssh Keys Networking.
From www.youtube.com
Networking SSH (Secure shell) YouTube Ssh Keys Networking Learn best practices and tips for handling ssh keys efficiently. You may already have an ssh key, but it doesn't hurt to create a new one. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. Welcome to our ultimate guide to setting up ssh (secure shell) keys. The client creates. Ssh Keys Networking.
From www.snapfrozen.com.au
How to setup and use SSH keys Snapfrozen Ssh Keys Networking To log in securely to another computer without a password, you must have an ssh key. Welcome to our ultimate guide to setting up ssh (secure shell) keys. The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. The client creates a key pair and then uploads the public. This tutorial will walk. Ssh Keys Networking.
From www.ionos.ca
How to use SSH keys IONOS CA Ssh Keys Networking The client creates a key pair and then uploads the public. The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. To log in securely to another computer without a password, you must have an ssh key. This tutorial will walk you through the basics of creating ssh keys, and also how to. Ssh Keys Networking.
From morioh.com
Networking SSH Key Authentication Public & Private Key on Linux Ssh Keys Networking To log in securely to another computer without a password, you must have an ssh key. Welcome to our ultimate guide to setting up ssh (secure shell) keys. You may already have an ssh key, but it doesn't hurt to create a new one. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control.. Ssh Keys Networking.
From www.hostinger.my
SSH Tutorial What is SSH, Encryptions and Ports Ssh Keys Networking This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. The client creates a key pair and then uploads the public. To log in securely to another computer without a password, you must have an ssh key. Learn best practices and tips for handling ssh keys efficiently. Discover 13 simple ways. Ssh Keys Networking.
From www.gtxgaming.co.uk
How To Use SSH Keys Ssh Keys Networking Welcome to our ultimate guide to setting up ssh (secure shell) keys. The client creates a key pair and then uploads the public. Ssh key pairs can be used to authenticate a client to a server. To log in securely to another computer without a password, you must have an ssh key. Discover 13 simple ways to effectively manage ssh. Ssh Keys Networking.
From www.geeksforgeeks.org
Introduction to SSH(Secure Shell) Keys Ssh Keys Networking The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. Welcome to our ultimate guide to setting up ssh (secure shell) keys. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. You may already have an ssh key, but it doesn't hurt to create a new. Ssh Keys Networking.
From www.works-hub.com
Managing remote servers with SSH and SFTP connections a stepbystep guide Ssh Keys Networking You may already have an ssh key, but it doesn't hurt to create a new one. To log in securely to another computer without a password, you must have an ssh key. Ssh key pairs can be used to authenticate a client to a server. The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers. Ssh Keys Networking.
From www.fosslinux.com
How to Generate SSH Keys on Linux FOSS Linux Ssh Keys Networking To log in securely to another computer without a password, you must have an ssh key. Learn best practices and tips for handling ssh keys efficiently. This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access. Ssh Keys Networking.
From insidethenation.com
Choosing the Right SSH Key Type for Your Network with Foxpass Inside Ssh Keys Networking This tutorial will walk you through the basics of creating ssh keys, and also how to manage multiple keys. Welcome to our ultimate guide to setting up ssh (secure shell) keys. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined access control. You may already have an ssh key, but it doesn't hurt to create. Ssh Keys Networking.
From techgenix.com
Setting up SSH keys to improve your network security Ssh Keys Networking The secure shell (ssh) protocol sets up encrypted connections for remote logins and file transfers between computers. Ssh key pairs can be used to authenticate a client to a server. You may already have an ssh key, but it doesn't hurt to create a new one. Discover 13 simple ways to effectively manage ssh keys for enhanced security and streamlined. Ssh Keys Networking.