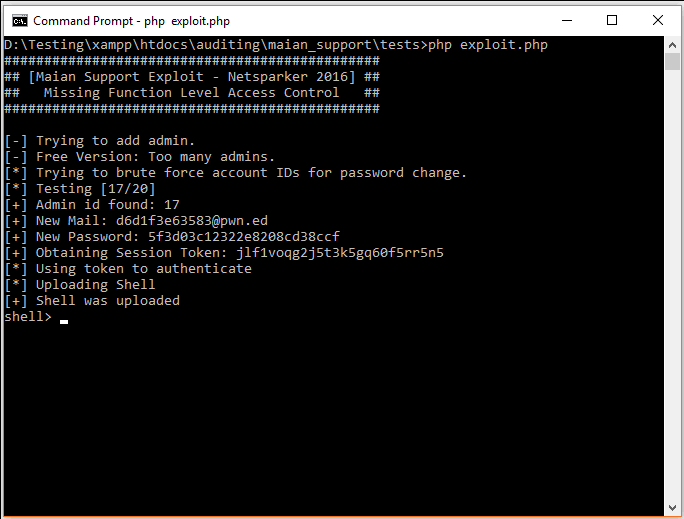
Missing Function Level Access Control Java Example . Usually admin access requires authentication, however, if the. There are a few ways that function level access controls can creep into an organization. The hacker simply forces target urls. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. How do missing function level access control exploits work? Ensure the jdk is correctly installed and the environment. Here is a classic example of missing function level access control − the hacker simply forces target urls. Missing function level access control. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. Below is a classic example of missing function level access control :
from www.invicti.com
Missing function level access control. Below is a classic example of missing function level access control : How do missing function level access control exploits work? The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Here is a classic example of missing function level access control − the hacker simply forces target urls. There are a few ways that function level access controls can creep into an organization. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. Usually admin access requires authentication, however, if the. Ensure the jdk is correctly installed and the environment. The hacker simply forces target urls.
Exploiting Missing Funtion Level Access Control Issues Invicti
Missing Function Level Access Control Java Example Usually admin access requires authentication, however, if the. How do missing function level access control exploits work? Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. There are a few ways that function level access controls can creep into an organization. Usually admin access requires authentication, however, if the. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Here is a classic example of missing function level access control − the hacker simply forces target urls. The hacker simply forces target urls. Missing function level access control. Ensure the jdk is correctly installed and the environment. Below is a classic example of missing function level access control :
From www.startertutorials.com
Access control Access modifiers in Java Missing Function Level Access Control Java Example The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Ensure the jdk is correctly installed and the environment. The hacker simply forces target urls. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. Usually. Missing Function Level Access Control Java Example.
From www.youtube.com
Ejercicio Goat Missing Function Level Access Control YouTube Missing Function Level Access Control Java Example There are a few ways that function level access controls can creep into an organization. Below is a classic example of missing function level access control : The hacker simply forces target urls. Missing function level access control. Ensure the jdk is correctly installed and the environment. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication. Missing Function Level Access Control Java Example.
From www.youtube.com
Goat 8 Missing Function Level Access Control Relying on Obscurity Missing Function Level Access Control Java Example Usually admin access requires authentication, however, if the. How do missing function level access control exploits work? The hacker simply forces target urls. There are a few ways that function level access controls can creep into an organization. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that. Missing Function Level Access Control Java Example.
From zhuanlan.zhihu.com
A1Missing Function Level Access Control 知乎 Missing Function Level Access Control Java Example The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Usually admin access requires authentication, however, if the. Here is a classic example of missing function level access control − the hacker simply forces target urls. The hacker simply forces target urls. How do missing. Missing Function Level Access Control Java Example.
From usemynotes.com
What are Access Modifiers in Java? UseMyNotes Missing Function Level Access Control Java Example There are a few ways that function level access controls can creep into an organization. Ensure the jdk is correctly installed and the environment. Usually admin access requires authentication, however, if the. The hacker simply forces target urls. Below is a classic example of missing function level access control : Missing function level access control. How do missing function level. Missing Function Level Access Control Java Example.
From www.youtube.com
Missing Function Level Access Control Exploits 2 YouTube Missing Function Level Access Control Java Example Below is a classic example of missing function level access control : Here is a classic example of missing function level access control − the hacker simply forces target urls. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. Missing function level access control. The missing function level access control. Missing Function Level Access Control Java Example.
From www.simplilearn.com
An Introduction to Methods in Java with Examples Simplilearn Missing Function Level Access Control Java Example How do missing function level access control exploits work? Missing function level access control. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. Below is a classic example of missing function level access control : The hacker simply forces target urls. Usually admin access requires authentication, however, if the. Here. Missing Function Level Access Control Java Example.
From www.youtube.com
OWASP TOP 10 A7 Missing Function Level Access Control YouTube Missing Function Level Access Control Java Example There are a few ways that function level access controls can creep into an organization. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. The hacker simply forces target urls. How do missing function level access control exploits work? Here is a classic example. Missing Function Level Access Control Java Example.
From zhuanlan.zhihu.com
A1Missing Function Level Access Control 知乎 Missing Function Level Access Control Java Example The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Below is a classic example of missing function level access control : Usually admin access requires authentication, however, if the. There are a few ways that function level access controls can creep into an organization.. Missing Function Level Access Control Java Example.
From www.technochops.com
Missing Function Level Access Control (FLAC) With Examples Missing Function Level Access Control Java Example Here is a classic example of missing function level access control − the hacker simply forces target urls. There are a few ways that function level access controls can creep into an organization. Below is a classic example of missing function level access control : The hacker simply forces target urls. Missing function level access control. The missing function level. Missing Function Level Access Control Java Example.
From zhuanlan.zhihu.com
A1Missing Function Level Access Control 知乎 Missing Function Level Access Control Java Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. There are a few ways that function level access controls can creep into an organization. Here is a classic example of missing function level access control − the hacker simply forces target urls. Ensure the jdk is correctly installed and the. Missing Function Level Access Control Java Example.
From www.youtube.com
OWASP Top 10 A7 Missing functionlevel access control YouTube Missing Function Level Access Control Java Example The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Ensure the jdk is correctly installed and the environment. There are a few ways that function level access controls can creep into an organization. How do missing function level access control exploits work? Here is. Missing Function Level Access Control Java Example.
From zhuanlan.zhihu.com
A1Missing Function Level Access Control 知乎 Missing Function Level Access Control Java Example Here is a classic example of missing function level access control − the hacker simply forces target urls. There are a few ways that function level access controls can creep into an organization. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Ensure the. Missing Function Level Access Control Java Example.
From www.slideshare.net
A7 Missing Function Level Access Control PPT Missing Function Level Access Control Java Example There are a few ways that function level access controls can creep into an organization. Usually admin access requires authentication, however, if the. How do missing function level access control exploits work? The hacker simply forces target urls. Below is a classic example of missing function level access control : Here is a classic example of missing function level access. Missing Function Level Access Control Java Example.
From www.slideserve.com
PPT Drupal Security Awareness (2) PowerPoint Presentation, free Missing Function Level Access Control Java Example Missing function level access control. How do missing function level access control exploits work? Usually admin access requires authentication, however, if the. The hacker simply forces target urls. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. Here is a classic example of missing function level access control − the. Missing Function Level Access Control Java Example.
From www.geeksforgeeks.org
Difference Between Class Level and Method Level Access Control in Java Missing Function Level Access Control Java Example How do missing function level access control exploits work? The hacker simply forces target urls. Missing function level access control. There are a few ways that function level access controls can creep into an organization. Here is a classic example of missing function level access control − the hacker simply forces target urls. Missing function level access control, an owasp. Missing Function Level Access Control Java Example.
From www.c-sharpcorner.com
Missing Function Level Access Control And Its Prevention Mechanism Missing Function Level Access Control Java Example There are a few ways that function level access controls can creep into an organization. How do missing function level access control exploits work? Ensure the jdk is correctly installed and the environment. Usually admin access requires authentication, however, if the. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient.. Missing Function Level Access Control Java Example.
From www.slideshare.net
19 owasp top 10 a7missing function level access control Missing Function Level Access Control Java Example The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. The hacker simply forces target urls. Here is a classic example of missing function level access control − the hacker simply forces target urls. There are a few ways that function level access controls can. Missing Function Level Access Control Java Example.
From www.youtube.com
Missing Function Level Access Control using burpsuite YouTube Missing Function Level Access Control Java Example Below is a classic example of missing function level access control : There are a few ways that function level access controls can creep into an organization. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Missing function level access control. Ensure the jdk. Missing Function Level Access Control Java Example.
From www.youtube.com
Goat 8 Missing Function Level Access Control Gathering User Info Missing Function Level Access Control Java Example Usually admin access requires authentication, however, if the. The hacker simply forces target urls. Below is a classic example of missing function level access control : Missing function level access control. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Missing function level access. Missing Function Level Access Control Java Example.
From www.youtube.com
Missing Function Level Access Control Explained YouTube Missing Function Level Access Control Java Example There are a few ways that function level access controls can creep into an organization. How do missing function level access control exploits work? The hacker simply forces target urls. Here is a classic example of missing function level access control − the hacker simply forces target urls. Missing function level access control, an owasp top 10 vulnerability, occurs when. Missing Function Level Access Control Java Example.
From www.youtube.com
[A1] Missing Function Level Access Control Goat YouTube Missing Function Level Access Control Java Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. How do missing function level access control exploits work? There are a few ways that function level access controls can creep into an organization. Missing function level access control. The hacker simply forces target urls. Usually admin access requires authentication, however,. Missing Function Level Access Control Java Example.
From www.youtube.com
Goat 8 Missing Function Level Access Control Solutions 2021 Missing Function Level Access Control Java Example Missing function level access control. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Ensure the jdk is correctly installed and the environment. How do missing function level access control exploits work? Usually admin access requires authentication, however, if the. Missing function level access. Missing Function Level Access Control Java Example.
From zhuanlan.zhihu.com
A1Missing Function Level Access Control 知乎 Missing Function Level Access Control Java Example Here is a classic example of missing function level access control − the hacker simply forces target urls. Ensure the jdk is correctly installed and the environment. How do missing function level access control exploits work? There are a few ways that function level access controls can creep into an organization. The hacker simply forces target urls. Below is a. Missing Function Level Access Control Java Example.
From zhuanlan.zhihu.com
A1Missing Function Level Access Control 知乎 Missing Function Level Access Control Java Example The hacker simply forces target urls. How do missing function level access control exploits work? The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Usually admin access requires authentication, however, if the. Here is a classic example of missing function level access control −. Missing Function Level Access Control Java Example.
From securitystudy.tistory.com
[Goat] Missing Function Level Access Control 2 Missing Function Level Access Control Java Example Missing function level access control. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Ensure the jdk is correctly installed and the environment. Usually admin access requires authentication, however, if the. Here is a classic example of missing function level access control − the. Missing Function Level Access Control Java Example.
From zhuanlan.zhihu.com
A1Missing Function Level Access Control 知乎 Missing Function Level Access Control Java Example Missing function level access control. There are a few ways that function level access controls can creep into an organization. Ensure the jdk is correctly installed and the environment. Below is a classic example of missing function level access control : How do missing function level access control exploits work? The missing function level access control vulnerability allows users to. Missing Function Level Access Control Java Example.
From www.youtube.com
What is Missing Function Level Access Control? OWASP Top 10 2013 Missing Function Level Access Control Java Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. Here is a classic example of missing function level access control − the hacker simply forces target urls. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should. Missing Function Level Access Control Java Example.
From www.slideshare.net
19 owasp top 10 a7missing function level access control Missing Function Level Access Control Java Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. There are a few ways that function level access controls can creep into an organization. Usually admin access requires authentication, however, if the. The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets. Missing Function Level Access Control Java Example.
From www.youtube.com
JAVA method 8. 부록 access level modifiers YouTube Missing Function Level Access Control Java Example How do missing function level access control exploits work? Here is a classic example of missing function level access control − the hacker simply forces target urls. The hacker simply forces target urls. Ensure the jdk is correctly installed and the environment. Below is a classic example of missing function level access control : Missing function level access control, an. Missing Function Level Access Control Java Example.
From www.youtube.com
Java Access Levels Public, Private, Protected, Default Java Tutorial Missing Function Level Access Control Java Example There are a few ways that function level access controls can creep into an organization. Below is a classic example of missing function level access control : The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. The hacker simply forces target urls. How do. Missing Function Level Access Control Java Example.
From www.researchgate.net
Outline of missing function level access control (MFLAC) vulnerability Missing Function Level Access Control Java Example How do missing function level access control exploits work? Missing function level access control. Here is a classic example of missing function level access control − the hacker simply forces target urls. Below is a classic example of missing function level access control : There are a few ways that function level access controls can creep into an organization. Missing. Missing Function Level Access Control Java Example.
From www.c-sharpcorner.com
Missing Function Level Access Control And Its Prevention Mechanism Missing Function Level Access Control Java Example The missing function level access control vulnerability allows users to perform functions that should be restricted, or lets them access resources that should be protected. Ensure the jdk is correctly installed and the environment. The hacker simply forces target urls. There are a few ways that function level access controls can creep into an organization. Missing function level access control.. Missing Function Level Access Control Java Example.
From www.youtube.com
OWASP A7 Missing Function Level Access Control IT 6873 Presentation Missing Function Level Access Control Java Example Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. Usually admin access requires authentication, however, if the. Here is a classic example of missing function level access control − the hacker simply forces target urls. There are a few ways that function level access controls can creep into an organization.. Missing Function Level Access Control Java Example.
From www.invicti.com
Exploiting Missing Funtion Level Access Control Issues Invicti Missing Function Level Access Control Java Example Ensure the jdk is correctly installed and the environment. Usually admin access requires authentication, however, if the. Missing function level access control, an owasp top 10 vulnerability, occurs when authentication checks in request handlers are insufficient. Below is a classic example of missing function level access control : How do missing function level access control exploits work? Missing function level. Missing Function Level Access Control Java Example.