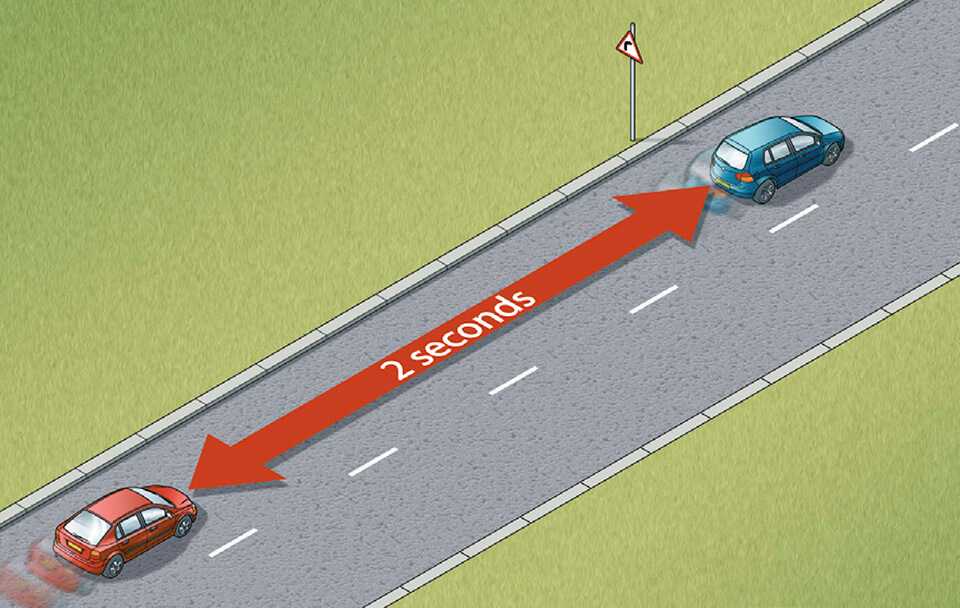
Tailgating Is An Example Of . A typical example of tailgating. Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted areas. This requires them to bring props such as a uniform, van,. Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due to human elements, as well as potential lapses in. The first car is being followed very closely by another. Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows an authorized individual to enter secured premises while. Tailgating is the action of a driver driving behind another. The most common example is to pretend to be a delivery driver or tradesperson. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are not permitted to be. A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains access to a physical facility by asking the person. The most common kind of tailgating attack involves.
from carfromjapan.com
The first car is being followed very closely by another. A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are not permitted to be. This requires them to bring props such as a uniform, van,. The most common example is to pretend to be a delivery driver or tradesperson. Tailgating is the action of a driver driving behind another. A typical example of tailgating. Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted areas. Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows an authorized individual to enter secured premises while. The most common kind of tailgating attack involves.
The 4 Types of Tailgaters and How to Avoid Them
Tailgating Is An Example Of A typical example of tailgating. This requires them to bring props such as a uniform, van,. Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due to human elements, as well as potential lapses in. Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows an authorized individual to enter secured premises while. Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains access to a physical facility by asking the person. A typical example of tailgating. Tailgating is the action of a driver driving behind another. The most common example is to pretend to be a delivery driver or tradesperson. A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are not permitted to be. The first car is being followed very closely by another. Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted areas. The most common kind of tailgating attack involves.
From carfromjapan.com
The 4 Types of Tailgaters and How to Avoid Them Tailgating Is An Example Of In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are not permitted to be. The most common example is to pretend to be a delivery driver or tradesperson. The first car is being followed very closely by another. Tailgating is the action of a driver driving behind. Tailgating Is An Example Of.
From improveyourgameday.com
How to Tailgate The Ultimate Tailgating Guide Improve Your Gameday Tailgating Is An Example Of The first car is being followed very closely by another. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are not permitted to be. Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains access to a physical facility by asking the person. Tailgating. Tailgating Is An Example Of.
From us.norton.com
What is a tailgating attack + how to protect yourself Tailgating Is An Example Of Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due to human elements, as well as potential lapses in. A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. A typical example of tailgating. The most common kind of tailgating attack involves. The first car is being followed. Tailgating Is An Example Of.
From www.hgtv.com
Fun Tailgating Ideas HGTV Tailgating Is An Example Of A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. A typical example of tailgating. The first car is being followed very closely by another. Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted. Tailgating Is An Example Of.
From www.itgovernance.co.uk
What is Tailgating? Definition, Examples & Prevention IT Governance Tailgating Is An Example Of The first car is being followed very closely by another. A typical example of tailgating. This requires them to bring props such as a uniform, van,. Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains access to a physical facility by asking the person. In essence, tailgating is a social engineering attack where the attacker follows. Tailgating Is An Example Of.
From giokipqxe.blob.core.windows.net
Tailgating Definition With Example at Elizabeth Marrero blog Tailgating Is An Example Of Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains access to a physical facility by asking the person. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are not permitted to be. Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due. Tailgating Is An Example Of.
From www.rentittoday.com
How to Tailgate at Football Games For First Time Tailgating Is An Example Of The first car is being followed very closely by another. The most common example is to pretend to be a delivery driver or tradesperson. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are not permitted to be. Tailgating is the action of a driver driving behind. Tailgating Is An Example Of.
From www.ranker.com
25 Perfect Examples of Tailgating Done Right Tailgating Is An Example Of Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due to human elements, as well as potential lapses in. Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows an authorized individual to enter secured premises while. Tailgating, also known as piggybacking, is one of the most common ways for. Tailgating Is An Example Of.
From www.terranovasecurity.com
What is a Tailgating Attack? Terranova Security Tailgating Is An Example Of A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. A typical example of tailgating. The first car is being followed very closely by another. The most common kind of tailgating attack involves. Tailgating is the action of a driver driving behind another. Tailgating, sometimes referred to as piggybacking,. Tailgating Is An Example Of.
From www.greatflorida.com
Tailgating Pro Tips The GreatFlorida Insurance Blog Tailgating Is An Example Of The most common kind of tailgating attack involves. This requires them to bring props such as a uniform, van,. Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted areas. Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due to human elements, as well. Tailgating Is An Example Of.
From reviewed.usatoday.com
The ultimate tailgating guide Reviewed Tailgating Is An Example Of The most common kind of tailgating attack involves. Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted areas. Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains access to a physical facility by asking the person. The most common example is. Tailgating Is An Example Of.
From www.wtol.com
How to tailgate at the Ohio State vs. Toledo game Tailgating Is An Example Of Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due to human elements, as well as potential lapses in. Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains access to a physical facility by asking the person. A social engineering attack that features more of a physical element than a virtual one is known as. Tailgating Is An Example Of.
From www.ranker.com
25 Perfect Examples of Tailgating Done Right Tailgating Is An Example Of The most common example is to pretend to be a delivery driver or tradesperson. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are not permitted to be. Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows. Tailgating Is An Example Of.
From www.slideshare.net
Tailgating Infographic Tailgating Is An Example Of Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted areas. Tailgating is the action of a driver driving behind another. A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. Tailgating, sometimes referred to. Tailgating Is An Example Of.
From vehq.com
What Is Tailgating in Driving? [and What You Need to Do When It Happens] Tailgating Is An Example Of This requires them to bring props such as a uniform, van,. The most common kind of tailgating attack involves. A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in. Tailgating Is An Example Of.
From www.telegraph.co.uk
What is an NFL tailgate party? Tailgating Is An Example Of The most common kind of tailgating attack involves. The most common example is to pretend to be a delivery driver or tradesperson. Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains access to a physical facility by asking the person. A social engineering attack that features more of a physical element than a virtual one is. Tailgating Is An Example Of.
From carfromjapan.com
The 4 Types of Tailgaters and How to Avoid Them CAR FROM JAPAN Tailgating Is An Example Of Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows an authorized individual to enter secured premises while. Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted areas. The most common kind of tailgating attack involves.. Tailgating Is An Example Of.
From fyotcqhva.blob.core.windows.net
Example Of Tailgating In Banking at Jaclyn Watson blog Tailgating Is An Example Of The most common example is to pretend to be a delivery driver or tradesperson. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are not permitted to be. This requires them to bring props such as a uniform, van,. Tailgating is the action of a driver driving. Tailgating Is An Example Of.
From exokopvml.blob.core.windows.net
Tailgating Attack Examples at Willis Cannon blog Tailgating Is An Example Of The most common kind of tailgating attack involves. Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted areas. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are not permitted to be.. Tailgating Is An Example Of.
From us.norton.com
What is a tailgating attack + how to protect yourself Tailgating Is An Example Of Tailgating is the action of a driver driving behind another. Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted areas. The first car is being followed very closely by another. A social engineering attack that features more of a physical element than a virtual one. Tailgating Is An Example Of.
From plattner-verderame.com
Why Tailgating Is Such a Dangerous Driving Behavior Plattner Verderame PC Tailgating Is An Example Of Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due to human elements, as well as potential lapses in. Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted areas. The first car is being followed very closely by another. This requires them to bring. Tailgating Is An Example Of.
From www.toyotaofclermont.com
Five safe driving tips for when you're being tailgated Toyota of Clermont Tailgating Is An Example Of Tailgating is the action of a driver driving behind another. This requires them to bring props such as a uniform, van,. A typical example of tailgating. A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains. Tailgating Is An Example Of.
From www.nphm.com
Tailgating Safety Nurenberg Paris Tailgating Is An Example Of Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains access to a physical facility by asking the person. This requires them to bring props such as a uniform, van,. Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows an authorized individual to enter secured premises while.. Tailgating Is An Example Of.
From improveyourgameday.com
What is Tailgating? Improve Your Gameday Tailgating Is An Example Of This requires them to bring props such as a uniform, van,. A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. The first car is being followed very closely by another. Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains access to a physical facility. Tailgating Is An Example Of.
From gogetsecure.com
What is Tailgating in Cyber Security? [A Simple Definition & Examples] Tailgating Is An Example Of The first car is being followed very closely by another. A typical example of tailgating. Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due to human elements, as well as potential lapses in. Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows an authorized individual to enter secured. Tailgating Is An Example Of.
From www.popularmechanics.com
The American Tailgating Tradition Dates Back to the Civil War Tailgating Is An Example Of A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. A typical example of tailgating. This requires them to bring props such as a uniform, van,. Tailgating is the action of a driver driving behind another. The most common kind of tailgating attack involves. Tailgating, also known as piggybacking,. Tailgating Is An Example Of.
From giokipqxe.blob.core.windows.net
Tailgating Definition With Example at Elizabeth Marrero blog Tailgating Is An Example Of A typical example of tailgating. This requires them to bring props such as a uniform, van,. Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due to human elements, as well as potential lapses in. Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains access to a physical facility by asking the person. The most. Tailgating Is An Example Of.
From blog.mailfence.com
Tailgating What Is It And How Does It Work Mailfence Blog Tailgating Is An Example Of Tailgating is the action of a driver driving behind another. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are not permitted to be. Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due to human elements, as well as potential lapses in. The most common. Tailgating Is An Example Of.
From carfromjapan.com
The 4 Types of Tailgaters and How to Avoid Them Tailgating Is An Example Of This requires them to bring props such as a uniform, van,. Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows an authorized individual to enter secured premises while. The most common example is to pretend to be a delivery driver or tradesperson. The first car is being followed very closely. Tailgating Is An Example Of.
From www.nytimes.com
Tailgating Goes Above and Beyond at the University of Mississippi The Tailgating Is An Example Of A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. This requires them to bring props such as a uniform, van,. Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted areas. Tailgating is the. Tailgating Is An Example Of.
From www.heartlandamerica.com
Top 5 Tailgating Essentials to Kick Off the Season Tailgating Is An Example Of Tailgating is the action of a driver driving behind another. Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows an authorized individual to enter secured premises while. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are. Tailgating Is An Example Of.
From www.pinterest.com
Everything You Need to Know About Tailgating Tailgating Is An Example Of Tailgating is the action of a driver driving behind another. Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows an authorized individual to enter secured premises while. The most common example is to pretend to be a delivery driver or tradesperson. A typical example of tailgating. Tailgating, also known as. Tailgating Is An Example Of.
From carfromjapan.com
The 4 Types of Tailgaters and How to Avoid Them Tailgating Is An Example Of Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due to human elements, as well as potential lapses in. The most common kind of tailgating attack involves. Tailgating, sometimes referred to as piggybacking, is a type of physical security breach in which an unauthorized person follows an authorized individual to enter secured premises while. A typical example of tailgating.. Tailgating Is An Example Of.
From gogetsecure.com
What is Tailgating in Cyber Security? [A Simple Definition & Examples] Tailgating Is An Example Of Tailgating, also known as piggybacking, is one of the most common ways for hackers, thieves and other unsavory characters to gain access to restricted areas. In essence, tailgating is a social engineering attack where the attacker follows an authorized person into a restricted area in which they are not permitted to be. Tailgating is the action of a driver driving. Tailgating Is An Example Of.
From dailyillini.com
Tips and tricks to maximize your tailgating experience The Daily Illini Tailgating Is An Example Of A social engineering attack that features more of a physical element than a virtual one is known as a “tailgating attack“. Tailgating, also known as piggybacking, is a physical breach whereby an attacker gains access to a physical facility by asking the person. Tailgating in cybersecurity is considered a threat that exploits vulnerabilities due to human elements, as well as. Tailgating Is An Example Of.