Remove Xss Javascript . Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. The owasp cheatsheet covers all possible scenarios for xss. Ensure that all user inputs are validated and sanitized before processing or displaying them. The purpose of output encoding (as it relates to cross site scripting) is to convert untrusted input into a safe form where the input is displayed as. If you are not outputting data within tags' definitions (not. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. This helps to remove any. Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. This could steal personal data, redirect visitors. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? All tags can harbour xss risks.
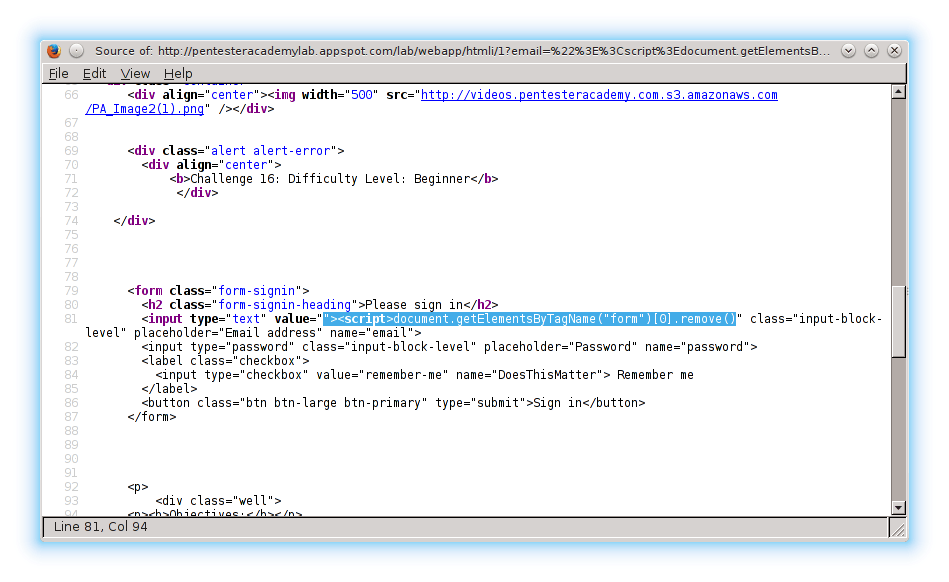
from exploit.ph
The purpose of output encoding (as it relates to cross site scripting) is to convert untrusted input into a safe form where the input is displayed as. This could steal personal data, redirect visitors. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? This helps to remove any. Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. All tags can harbour xss risks. Ensure that all user inputs are validated and sanitized before processing or displaying them. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. If you are not outputting data within tags' definitions (not.
eXploit Reflected XSS at PentesterAcademy
Remove Xss Javascript The purpose of output encoding (as it relates to cross site scripting) is to convert untrusted input into a safe form where the input is displayed as. This helps to remove any. This could steal personal data, redirect visitors. The owasp cheatsheet covers all possible scenarios for xss. All tags can harbour xss risks. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. The purpose of output encoding (as it relates to cross site scripting) is to convert untrusted input into a safe form where the input is displayed as. Ensure that all user inputs are validated and sanitized before processing or displaying them. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. If you are not outputting data within tags' definitions (not.
From www.indusface.com
What is XSS and How to Prevent It? Indusface Blog Remove Xss Javascript This helps to remove any. This could steal personal data, redirect visitors. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? If you are not outputting data within tags' definitions (not. Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. Ensure that all user inputs are. Remove Xss Javascript.
From www.youtube.com
How to Fix JavaScript XSS Vulnerabilities Simple Solutions Cross Site Remove Xss Javascript If you are not outputting data within tags' definitions (not. The owasp cheatsheet covers all possible scenarios for xss. All tags can harbour xss risks. Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. Ensure that all user inputs are validated and sanitized before processing or displaying them. The purpose of output. Remove Xss Javascript.
From escape.tech
What is CrossSite Scripting (XSS) and how to prevent it? Remove Xss Javascript This helps to remove any. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. If you are not outputting data within tags' definitions (not. This could steal personal data, redirect visitors.. Remove Xss Javascript.
From exploit.ph
eXploit Reflected XSS at PentesterAcademy Remove Xss Javascript The purpose of output encoding (as it relates to cross site scripting) is to convert untrusted input into a safe form where the input is displayed as. Ensure that all user inputs are validated and sanitized before processing or displaying them. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element. Remove Xss Javascript.
From www.youtube.com
Reflected XSS into a JavaScript string with single quote and Remove Xss Javascript This helps to remove any. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? Ensure that all user inputs are validated and sanitized before processing or displaying them. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. All tags can harbour xss. Remove Xss Javascript.
From cyberpointsolution.com
JavaScript Injection and XSS Attack with Examples Cyber Point Solution Remove Xss Javascript This helps to remove any. This could steal personal data, redirect visitors. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? If you are not outputting data within tags' definitions (not. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes,. Remove Xss Javascript.
From uexploit.blogspot.com
How to Do XSS and Resolve it in a site (Part 1) Umar Arfeen Shah Remove Xss Javascript This could steal personal data, redirect visitors. Ensure that all user inputs are validated and sanitized before processing or displaying them. This helps to remove any. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you. Remove Xss Javascript.
From flex0geek.blogspot.com
[Part 1] What is XSS and Example of Filters & Bypasses Remove Xss Javascript Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? If you are not outputting data within tags' definitions (not. All tags can harbour xss risks. This helps to remove any. The owasp cheatsheet covers all possible scenarios. Remove Xss Javascript.
From www.freecodecamp.org
What is XSS? How to Protect Your site from DOM CrossSite Scripting Remove Xss Javascript This helps to remove any. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? If you are not outputting data within tags' definitions (not. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. Xss allows attackers to inject malicious codes or scripts. Remove Xss Javascript.
From www.acunetix.com
How To Protect Your site Against A CrossSite Scripting (XSS) Attack Remove Xss Javascript This could steal personal data, redirect visitors. If you are not outputting data within tags' definitions (not. Ensure that all user inputs are validated and sanitized before processing or displaying them. All tags can harbour xss risks. Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. How can remove all of xss. Remove Xss Javascript.
From www.secjuice.com
bypassxssfiltersusingjavascriptglobalvariables Remove Xss Javascript All tags can harbour xss risks. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. This could steal personal data, redirect visitors. Ensure that all user inputs are validated and sanitized before processing or displaying them. Basically you should validate all input data using. Remove Xss Javascript.
From developer.chrome.com
How Chrome DevTools helps to defend against selfXSS attacks Blog Remove Xss Javascript This helps to remove any. Ensure that all user inputs are validated and sanitized before processing or displaying them. All tags can harbour xss risks. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. The owasp cheatsheet covers all possible scenarios for xss. Sanitizer libraries use the domparser(). Remove Xss Javascript.
From www.secjuice.com
bypassxssfiltersusingjavascriptglobalvariables Remove Xss Javascript All tags can harbour xss risks. Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. The owasp cheatsheet covers all possible scenarios for xss. Ensure that all user inputs are validated and sanitized before processing or displaying them. The purpose of output encoding (as it relates to cross site scripting) is to. Remove Xss Javascript.
From www.akto.io
Cross Site Scripting(XSS) XSS Example, XSS Attack Akto Security Remove Xss Javascript This could steal personal data, redirect visitors. This helps to remove any. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. All tags can harbour xss risks. Xss allows. Remove Xss Javascript.
From payatu.com
How DOMbased CrossSite Scripting (XSS) Attack Works Remove Xss Javascript Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? If you are not outputting data within tags' definitions (not. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each. Remove Xss Javascript.
From loeamhioe.blob.core.windows.net
How Xss Works Javascript at Charlie Jenkins blog Remove Xss Javascript How can remove all of xss tags (script, iframe, canvas.) except of other html tags? This helps to remove any. Ensure that all user inputs are validated and sanitized before processing or displaying them. If you are not outputting data within tags' definitions (not. The purpose of output encoding (as it relates to cross site scripting) is to convert untrusted. Remove Xss Javascript.
From siunam321.github.io
Reflected XSS in a JavaScript URL with some characters blocked Jan 1 Remove Xss Javascript The purpose of output encoding (as it relates to cross site scripting) is to convert untrusted input into a safe form where the input is displayed as. This could steal personal data, redirect visitors. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. How can remove all of. Remove Xss Javascript.
From www.tech-wonders.com
CrossSite Scripting (XSS) Attacks and Prevention Tips Remove Xss Javascript Ensure that all user inputs are validated and sanitized before processing or displaying them. All tags can harbour xss risks. The owasp cheatsheet covers all possible scenarios for xss. The purpose of output encoding (as it relates to cross site scripting) is to convert untrusted input into a safe form where the input is displayed as. Basically you should validate. Remove Xss Javascript.
From medium.com
How JavaScript works 5 types of XSS attacks + tips on preventing them Remove Xss Javascript Ensure that all user inputs are validated and sanitized before processing or displaying them. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and.. Remove Xss Javascript.
From www.youtube.com
Self XSS (Cross Site Scripting) PoC YouTube Remove Xss Javascript The purpose of output encoding (as it relates to cross site scripting) is to convert untrusted input into a safe form where the input is displayed as. Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. This could steal personal data, redirect visitors. Sanitizer libraries use the domparser() method to create html. Remove Xss Javascript.
From learnhacking.io
PortSwigger's "Reflected XSS into a JavaScript string with angle Remove Xss Javascript Ensure that all user inputs are validated and sanitized before processing or displaying them. This helps to remove any. If you are not outputting data within tags' definitions (not. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. How can remove all of xss tags (script, iframe, canvas.). Remove Xss Javascript.
From cloudmersive.medium.com
How to Remove XSS Attacks from Text Input in Node.JS by Cloudmersive Remove Xss Javascript Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any. Remove Xss Javascript.
From geekdaxue.co
XSS跨站脚本攻击 浅谈跨站脚本(XSS)攻击 《 安全数据验证不当》 极客文档 Remove Xss Javascript Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? If you are not outputting data within tags' definitions (not. Xss allows attackers to inject malicious codes or scripts into. Remove Xss Javascript.
From www.youtube.com
Reflected XSS in a JavaScript URL with some characters blocked Remove Xss Javascript This helps to remove any. This could steal personal data, redirect visitors. The owasp cheatsheet covers all possible scenarios for xss. Ensure that all user inputs are validated and sanitized before processing or displaying them. All tags can harbour xss risks. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? The purpose of output. Remove Xss Javascript.
From tcm-sec.com
What is CrossSite Scripting (XSS)? TCM Security Remove Xss Javascript Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. This helps to remove any. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? Ensure that all user inputs are validated and sanitized before processing or displaying them. This could steal personal data,. Remove Xss Javascript.
From academind.com
XSS What are CrossSite Scripting Attacks? Remove Xss Javascript Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. This helps to remove any. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. This could steal personal data, redirect visitors. Sanitizer libraries use the domparser() method to create html elements. Remove Xss Javascript.
From www.youtube.com
xss (cross site scripting ) filter evasion series stage 4 YouTube Remove Xss Javascript Ensure that all user inputs are validated and sanitized before processing or displaying them. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? This helps to remove any. All tags can harbour xss risks. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are. Remove Xss Javascript.
From nextvision.mx
¿Qué es el XSS o Cross Site Scripting? Remove Xss Javascript If you are not outputting data within tags' definitions (not. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. Ensure that all user. Remove Xss Javascript.
From loeamhioe.blob.core.windows.net
How Xss Works Javascript at Charlie Jenkins blog Remove Xss Javascript All tags can harbour xss risks. Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. This helps to remove any. The owasp cheatsheet covers all possible scenarios. Remove Xss Javascript.
From codegrazer.com
Codegrazer 7 Reflected Crosssite Scripting (XSS) Remove Xss Javascript Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. This helps to remove any. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. How can remove all of xss tags (script, iframe,. Remove Xss Javascript.
From 0727.site
JS trick in XSS Remove Xss Javascript Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. This could steal personal data, redirect visitors. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? Ensure that all user inputs are validated and sanitized before processing or displaying them. If you are. Remove Xss Javascript.
From www.makeuseof.com
How to Prevent CrossSite Scripting Using HTML, JavaScript, and DOM Remove Xss Javascript The owasp cheatsheet covers all possible scenarios for xss. How can remove all of xss tags (script, iframe, canvas.) except of other html tags? Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. Ensure that all user inputs are validated and sanitized before processing. Remove Xss Javascript.
From www.secjuice.com
bypassxssfiltersusingjavascriptglobalvariables Remove Xss Javascript Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. The owasp cheatsheet covers all possible scenarios for xss. Xss allows attackers to inject. Remove Xss Javascript.
From binary-studio.com
Crosssite scription (XSS) 101 What It Is, Why It’s So Dangeruous, and Remove Xss Javascript Xss allows attackers to inject malicious codes or scripts into webpages, targeting unsuspecting users visiting the site. All tags can harbour xss risks. If you are not outputting data within tags' definitions (not. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. How can. Remove Xss Javascript.
From www.akto.io
What is Crosssite scripting (XSS) and how to prevent as a developer? Remove Xss Javascript The owasp cheatsheet covers all possible scenarios for xss. Sanitizer libraries use the domparser() method to create html elements from your html string, then loop through each element and remove any attributes, properties, and. Basically you should validate all input data using white list approach (define valid patterns not invalid patterns as you are trying. Ensure that all user inputs. Remove Xss Javascript.