Vulnerable Devices List . You can search the cve list for a cve record if the cve id is known. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage. The mission of the cve® program is to identify, define, and catalog publicly disclosed. The cve list is available for download in the formats below, per the terms of use. Total count of cve records is currently unavailable. Please report the issue and try again later. To search by keyword, use a specific term or. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. New cve list download format is available now on cve.org. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.
from www.slideserve.com
Total count of cve records is currently unavailable. To search by keyword, use a specific term or. Please report the issue and try again later. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. New cve list download format is available now on cve.org. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage. The mission of the cve® program is to identify, define, and catalog publicly disclosed. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. You can search the cve list for a cve record if the cve id is known.
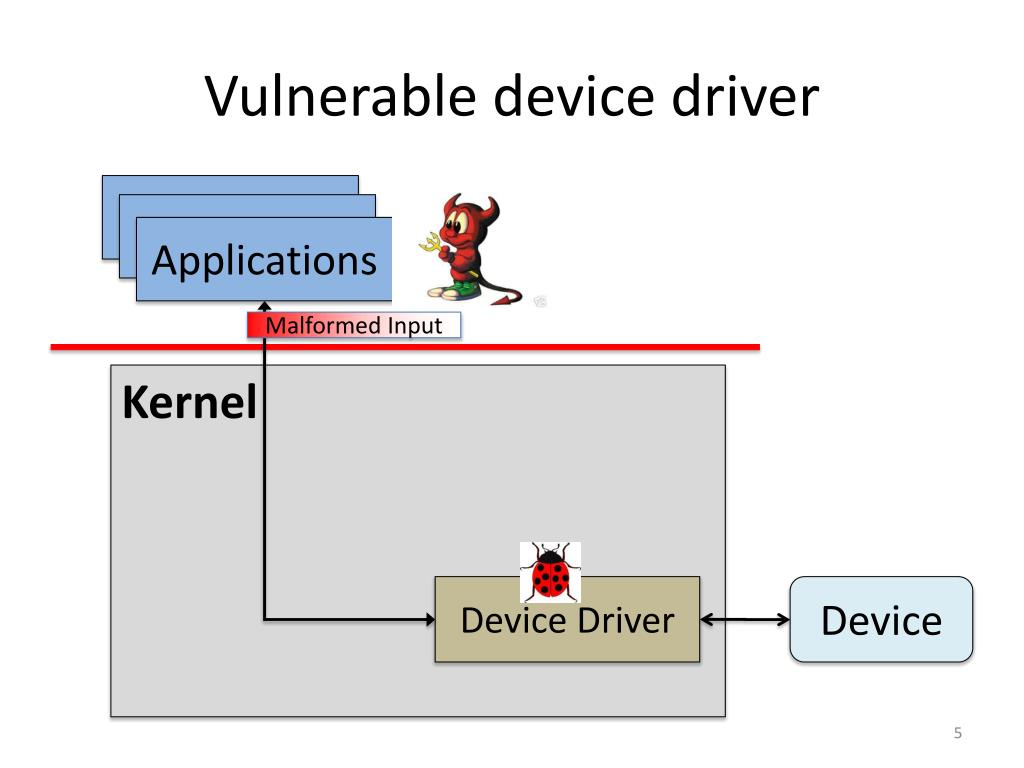
PPT Protecting Commodity Operating System Kernels from Vulnerable
Vulnerable Devices List Please report the issue and try again later. Total count of cve records is currently unavailable. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage. The cve list is available for download in the formats below, per the terms of use. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. The mission of the cve® program is to identify, define, and catalog publicly disclosed. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. Please report the issue and try again later. You can search the cve list for a cve record if the cve id is known. To search by keyword, use a specific term or. New cve list download format is available now on cve.org. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and.
From www.youtube.com
Fix Local Security Authority protection is off Your device may be Vulnerable Devices List Please report the issue and try again later. The mission of the cve® program is to identify, define, and catalog publicly disclosed. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can.. Vulnerable Devices List.
From www.researchgate.net
(PDF) Scanning for Vulnerable Devices in the of Things Vulnerable Devices List Total count of cve records is currently unavailable. New cve list download format is available now on cve.org. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. The cve list is available for. Vulnerable Devices List.
From www.scadafence.com
OT Security for Vulnerable Devices SCADAfence Vulnerable Devices List To search by keyword, use a specific term or. The mission of the cve® program is to identify, define, and catalog publicly disclosed. The cve list is available for download in the formats below, per the terms of use. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Please report the issue and try again later. New cve list download format. Vulnerable Devices List.
From www.yeahhub.com
List of Vulnerable /Mobile/OS Projects 2018 Update Yeah Hub Vulnerable Devices List Total count of cve records is currently unavailable. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. To search by keyword, use a specific term or. You can search the cve list for a cve record if the cve id is known. The. Vulnerable Devices List.
From support.langner.com
Using the vulnerability dashboard OTbase Help Center Langner, Inc. Vulnerable Devices List You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. New cve list download format is available now on cve.org. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage. Total count of cve records is currently unavailable. Please report the issue and try. Vulnerable Devices List.
From www.slideserve.com
PPT Protecting Commodity Operating System Kernels from Vulnerable Vulnerable Devices List The mission of the cve® program is to identify, define, and catalog publicly disclosed. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. New cve list download format is available now on cve.org. Please report the issue and try again later. To search by keyword, use a specific term or. The cve list is available for download in the formats below,. Vulnerable Devices List.
From mobilerecell.com
Vulnerable Devices & Data Threats Mobile reCell Vulnerable Devices List The mission of the cve® program is to identify, define, and catalog publicly disclosed. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. You can search the cve list for a cve record. Vulnerable Devices List.
From www.youtube.com
Search for Vulnerable Devices Around the World with Shodan [Tutorial Vulnerable Devices List The cve list is available for download in the formats below, per the terms of use. Total count of cve records is currently unavailable. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. You can view cve vulnerability details, exploits, references, metasploit modules,. Vulnerable Devices List.
From www.csoonline.com
Ripple20 Finding Vulnerable Devices and Detecting Attacks CSO Online Vulnerable Devices List New cve list download format is available now on cve.org. Total count of cve records is currently unavailable. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage. Please report the issue and try again later. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score. Vulnerable Devices List.
From www.thewindowsclub.com
Disable Microsoft Vulnerable Driver Blocklist in Windows 11 Vulnerable Devices List The mission of the cve® program is to identify, define, and catalog publicly disclosed. Total count of cve records is currently unavailable. You can search the cve list for a cve record if the cve id is known. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. You can view cve. Vulnerable Devices List.
From www.mdpi.com
Electronics Free FullText Analysis of Consumer IoT Device Vulnerable Devices List Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. You can search the cve list for a cve record if the cve id is known. Please report the issue and try again later. The cve list is available for download in the formats below, per the terms of use. The mission of the cve® program is to identify, define, and catalog. Vulnerable Devices List.
From www.bitdefender.co.uk
What’s the Most Vulnerable Device in Your Home? It’s Not What You Think Vulnerable Devices List The cve list is available for download in the formats below, per the terms of use. New cve list download format is available now on cve.org. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage.. Vulnerable Devices List.
From wiki.itarian.com
How to identify vulnerable devices and install security patches Vulnerable Devices List The cve list is available for download in the formats below, per the terms of use. Total count of cve records is currently unavailable. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. You can search the cve list for a cve record if the cve id is known. You can. Vulnerable Devices List.
From www.zimperium.com
Our Most Vulnerable Devices Are in Our Pockets Zimperium Vulnerable Devices List Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. Please report the issue and try again later. The mission of the cve® program is to identify, define, and catalog publicly disclosed. The cve list is available for download in the formats below, per the terms of use. New cve list download format is available now on cve.org. Nist maintains the national. Vulnerable Devices List.
From www.zimperium.com
Our Most Vulnerable Devices Are in Our Pockets Zimperium Vulnerable Devices List You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. Please report the issue and try again later. For the benefit of the cybersecurity community and network defenders—and to help every organization. Vulnerable Devices List.
From www.researchgate.net
Top 5 most vulnerable devices in 2021 Source Bitdefender, March 2021 Vulnerable Devices List Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. Please report the issue and try again later. New cve list download format is available now on cve.org. Total count of cve records is currently unavailable. The mission of the cve® program is to identify, define, and catalog publicly disclosed. The cve. Vulnerable Devices List.
From www.privateinternetaccess.com
Hacking the World Part 2 What's Being Hacked (And What Changed with Vulnerable Devices List New cve list download format is available now on cve.org. The cve list is available for download in the formats below, per the terms of use. The mission of the cve® program is to identify, define, and catalog publicly disclosed. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. For the benefit of the cybersecurity community and network defenders—and to help. Vulnerable Devices List.
From geekrewind.com
How to Turn On or Off Microsoft Vulnerable Driver Blocklist in Windows Vulnerable Devices List To search by keyword, use a specific term or. New cve list download format is available now on cve.org. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. The cve list is available for download in the formats below, per the terms of. Vulnerable Devices List.
From securitychallengesfacingtheinternet.blogspot.com
Smart but vulnerable devices Vulnerable Devices List The mission of the cve® program is to identify, define, and catalog publicly disclosed. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. To search by keyword, use a specific term or. Please report the issue and try again later. The cve list is available for download in the. Vulnerable Devices List.
From null-byte.wonderhowto.com
How to Detect BlueBorne Vulnerable Devices & What It Means « Null Byte Vulnerable Devices List The mission of the cve® program is to identify, define, and catalog publicly disclosed. To search by keyword, use a specific term or. Please report the issue and try again later. You can search the cve list for a cve record if the cve id is known. You can view cve vulnerability details, exploits, references, metasploit modules, full list of. Vulnerable Devices List.
From wiki.itarian.com
How to identify vulnerable devices and install security patches Vulnerable Devices List Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. You can search the cve list for a cve record if the cve id is known. The mission of the cve® program is to identify, define, and catalog publicly disclosed. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. To search. Vulnerable Devices List.
From shufflingbytes.com
UPnProxyChain a Tool to Exploit Devices Vulnerable to UPnProxy Vulnerable Devices List The cve list is available for download in the formats below, per the terms of use. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. New cve list download format is available now on cve.org. The mission of the cve® program is to identify, define, and catalog publicly disclosed.. Vulnerable Devices List.
From www.zimperium.com
Mobile Device Protection Mobile Devices are Vulnerable Vulnerable Devices List Total count of cve records is currently unavailable. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage. New cve list download format is available now on cve.org. The mission of the cve® program. Vulnerable Devices List.
From www.spiceworks.com
Top 10 Vulnerability Management Tools Spiceworks Vulnerable Devices List Total count of cve records is currently unavailable. The mission of the cve® program is to identify, define, and catalog publicly disclosed. The cve list is available for download in the formats below, per the terms of use. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. New cve list download format is available now on cve.org. Please report the issue. Vulnerable Devices List.
From blog.avast.com
How secure is your WiFi network at home? Avast Vulnerable Devices List The cve list is available for download in the formats below, per the terms of use. To search by keyword, use a specific term or. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. Total count of cve records is currently. Vulnerable Devices List.
From www.pinterest.com
How vulnerable are your devices to hackers?, Singapore News & Top Vulnerable Devices List The mission of the cve® program is to identify, define, and catalog publicly disclosed. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. The cve list is available for download in the formats below, per the terms of use. New cve list download format is available now on cve.org. Please report. Vulnerable Devices List.
From ordr.net
Ripple20 How to identify, protect vulnerable devices Ordr Vulnerable Devices List Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. The mission of the cve® program is to identify, define, and catalog publicly disclosed. Please report the issue and try again later. To search by keyword, use a specific term or. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. New. Vulnerable Devices List.
From thescottking.com
Infographic Vulnerable Mobile Devices Scott King Vulnerable Devices List Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. The cve list is available for download in the formats below, per the terms of use. The mission of the cve® program is to identify, define, and catalog publicly disclosed. New cve list download format is available now on cve.org. Total count. Vulnerable Devices List.
From www.youtube.com
How to hunt for vulnerable devices on the IoT and exploit them. YouTube Vulnerable Devices List To search by keyword, use a specific term or. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage. New cve list download format is available now on cve.org. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. Nist maintains the national vulnerability. Vulnerable Devices List.
From www.youtube.com
How to fix No active antivirus provider Your device is vulnerable Vulnerable Devices List Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage. Total count of cve records is currently unavailable. You can search the cve list for a cve record if the cve id is known. New cve. Vulnerable Devices List.
From www.fortinet.com
Zerobot New GoBased Campaign Targets Multiple Vulnerabilities Vulnerable Devices List Please report the issue and try again later. The cve list is available for download in the formats below, per the terms of use. Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. The mission of the cve® program is to identify, define, and catalog publicly disclosed. For the benefit of. Vulnerable Devices List.
From www.atstratus.com
OT/ICS Security from Armis Vulnerable Devices List Nist maintains the national vulnerability database (nvd), a repository of information on software and hardware flaws that can. To search by keyword, use a specific term or. Please report the issue and try again later. The cve list is available for download in the formats below, per the terms of use. Total count of cve records is currently unavailable. You. Vulnerable Devices List.
From www.kaspersky.co.in
Vulnerable Software Infographic Software Exploits Infographic Vulnerable Devices List Total count of cve records is currently unavailable. You can view cve vulnerability details, exploits, references, metasploit modules, full list of vulnerable products and cvss score reports and. The mission of the cve® program is to identify, define, and catalog publicly disclosed. Please report the issue and try again later. For the benefit of the cybersecurity community and network defenders—and. Vulnerable Devices List.
From gridinsoft.com
Critical LG TV Vulnerabilities Allow for Command Execution Gridinsoft Vulnerable Devices List To search by keyword, use a specific term or. For the benefit of the cybersecurity community and network defenders—and to help every organization better manage. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. The mission of the cve® program is to identify, define, and catalog publicly disclosed. New cve list download format is available now on cve.org. Total count of. Vulnerable Devices List.
From 4imag.com
How vulnerable are our devices when travelling abroad? 4imag Vulnerable Devices List The mission of the cve® program is to identify, define, and catalog publicly disclosed. You can search the cve list for a cve record if the cve id is known. To search by keyword, use a specific term or. Please report the issue and try again later. Identify, define, and catalog publicly disclosed cybersecurity vulnerabilities. You can view cve vulnerability. Vulnerable Devices List.