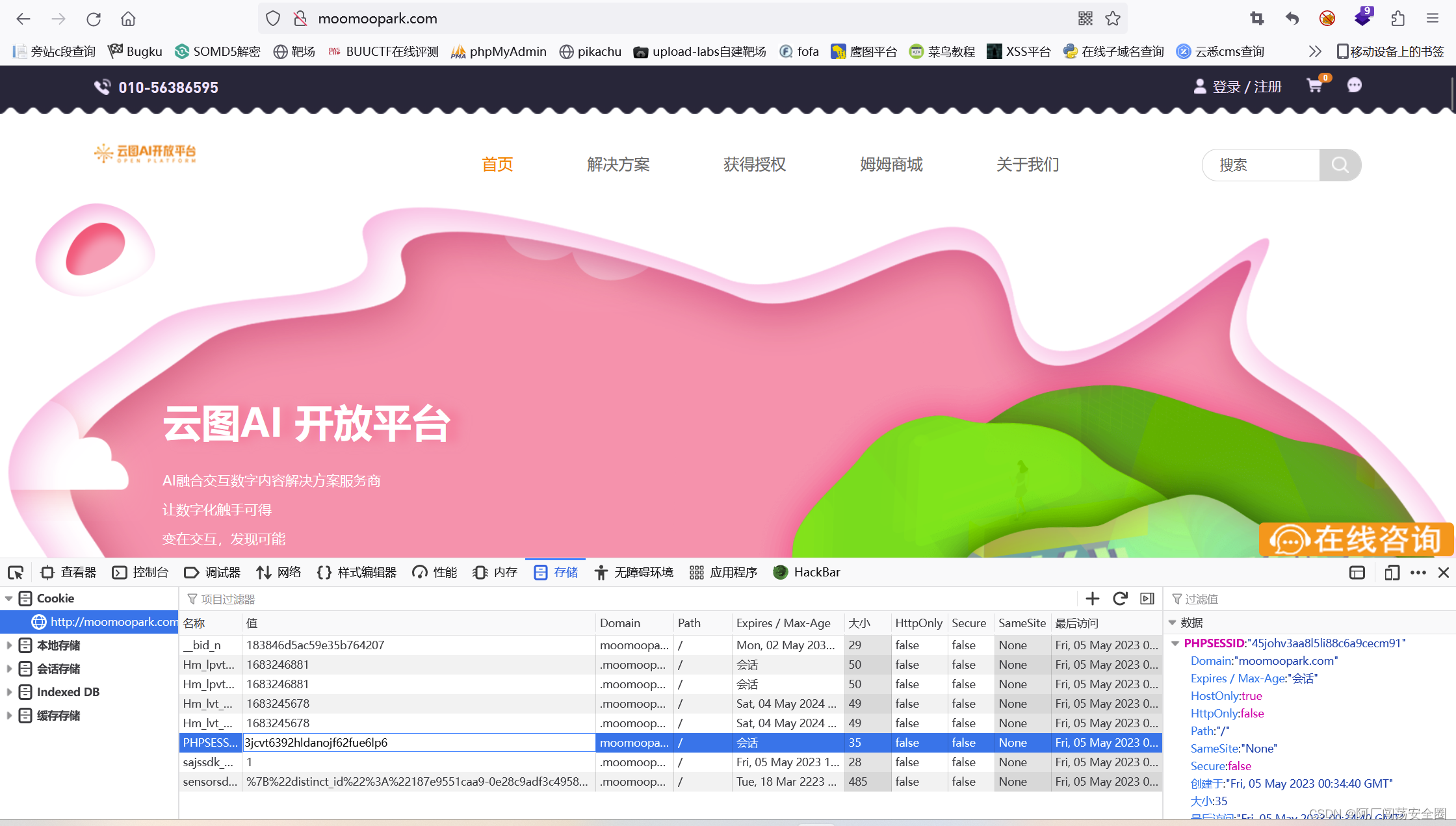
Xss In Cookie . one possible exploit path is using a xss vulnerability on a subdomain to leverage the following property of cookies:. I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. the answer is that depending on context, then cookie xss can often be exploited. stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. Follow the steps to create a burp collaborator. Some routes to achieve this are. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. learn how to prevent xss vulnerabilities by using output encoding, html sanitization, and framework security. upon accessing the default admin, i noticed that the device generates a user cookie. learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and impersonate them.
from blog.csdn.net
by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. upon accessing the default admin, i noticed that the device generates a user cookie. Follow the steps to create a burp collaborator. I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. the answer is that depending on context, then cookie xss can often be exploited. stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. Some routes to achieve this are. learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and impersonate them. one possible exploit path is using a xss vulnerability on a subdomain to leverage the following property of cookies:. learn how to prevent xss vulnerabilities by using output encoding, html sanitization, and framework security.
XSS平台打cookie实战_xss打印cookieCSDN博客
Xss In Cookie Follow the steps to create a burp collaborator. the answer is that depending on context, then cookie xss can often be exploited. I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. learn how to prevent xss vulnerabilities by using output encoding, html sanitization, and framework security. stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and impersonate them. Follow the steps to create a burp collaborator. Some routes to achieve this are. upon accessing the default admin, i noticed that the device generates a user cookie. one possible exploit path is using a xss vulnerability on a subdomain to leverage the following property of cookies:.
From blog.csdn.net
存储型XSS结合XSS平台获取cookie信息进后台——efucms_利用xss获取cookie再回到后台查看cookie信息,发现获取成功 Xss In Cookie by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. the answer is that depending on context, then cookie xss can often be exploited. upon accessing the default admin, i noticed that the device generates a user cookie. Some. Xss In Cookie.
From www.acunetix.com
The HttpOnly Flag Protecting Cookies against XSS Xss In Cookie I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. learn how to prevent xss vulnerabilities by using output encoding, html sanitization, and framework security. Follow the steps to create a burp collaborator. one possible exploit path is using a xss vulnerability on a subdomain to leverage the following property of cookies:. the answer. Xss In Cookie.
From bergee.it
Turning cookie based XSS into account takeover Bergee's Stories on Xss In Cookie the answer is that depending on context, then cookie xss can often be exploited. Some routes to achieve this are. stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies,. Xss In Cookie.
From www.youtube.com
How Hackers Use Stored Cross Site Scripting (XSS) to Steal Session Xss In Cookie upon accessing the default admin, i noticed that the device generates a user cookie. Follow the steps to create a burp collaborator. the answer is that depending on context, then cookie xss can often be exploited. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate. Xss In Cookie.
From www.youtube.com
XSS Cookie Stolen YouTube Xss In Cookie learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and impersonate them. one possible exploit path is using a xss vulnerability on a subdomain to leverage the following property of cookies:. Some routes to achieve this are. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session. Xss In Cookie.
From github.com
easyxsscookiestealer/cookiestealer.php at master · AXDOOMER/easyxss Xss In Cookie one possible exploit path is using a xss vulnerability on a subdomain to leverage the following property of cookies:. learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and impersonate them. upon accessing the default admin, i noticed that the device generates a user cookie. stored xss attack occurs when a. Xss In Cookie.
From blog.csdn.net
xss获取cookie登陆_xss拿到cookie怎么登陆CSDN博客 Xss In Cookie learn how to prevent xss vulnerabilities by using output encoding, html sanitization, and framework security. upon accessing the default admin, i noticed that the device generates a user cookie. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their.. Xss In Cookie.
From krourke.org
Gimme your cookies! XSS vulnerabilities and how to protect yourself Xss In Cookie Some routes to achieve this are. stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. upon accessing the default admin, i noticed that the device generates a user cookie. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies,. Xss In Cookie.
From www.aptive.co.uk
What is Crosssite Scripting (XSS)? Stored, DOM & Reflected Examples Xss In Cookie upon accessing the default admin, i noticed that the device generates a user cookie. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and. Xss In Cookie.
From careertechnologycybersecurityindia.blogspot.com
Stored XSS Vulnerability Xss In Cookie upon accessing the default admin, i noticed that the device generates a user cookie. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. stored xss attack occurs when a malicious script through user input is stored on the. Xss In Cookie.
From dxogtktrr.blob.core.windows.net
Xss Iframe Cookie at Michael Hodges blog Xss In Cookie I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. the answer is that depending on context, then cookie xss can often be exploited. one possible exploit path is using a xss vulnerability on a subdomain to leverage the following property of cookies:. upon accessing the default admin, i noticed that the device generates. Xss In Cookie.
From blog.csdn.net
使用xss来打cookie_xss打cookieCSDN博客 Xss In Cookie upon accessing the default admin, i noticed that the device generates a user cookie. Follow the steps to create a burp collaborator. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. learn how to use a stored xss. Xss In Cookie.
From blog.csdn.net
XSS平台打cookie实战_xss打印cookieCSDN博客 Xss In Cookie by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. upon accessing the default admin, i noticed that. Xss In Cookie.
From blog.csdn.net
XSS平台打cookie实战_xss打印cookieCSDN博客 Xss In Cookie stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. the answer is that depending on context, then cookie xss can often be exploited. learn how to prevent xss vulnerabilities by using output encoding, html sanitization, and framework security. one possible exploit path is using. Xss In Cookie.
From academind.com
XSS localStorage vs Cookies Xss In Cookie stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. Follow the steps to create a burp collaborator. learn how to prevent xss vulnerabilities by using output encoding, html sanitization, and framework security. the answer is that depending on context, then cookie xss can often be. Xss In Cookie.
From samsclass.info
Proj 11x Stealing Cookies with XSS (10 pts.) Xss In Cookie I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and impersonate them. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their.. Xss In Cookie.
From bergee.it
Turning cookie based XSS into account takeover Bergee's Stories on Xss In Cookie by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. one possible exploit path is using a xss vulnerability on a subdomain to leverage the following property of cookies:. I’m exploring whether there’s a method to intercept or obtain that. Xss In Cookie.
From medium.com
Pentesting basics Cookie Grabber (XSS) by Laur Telliskivi Medium Xss In Cookie Some routes to achieve this are. stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. one possible exploit path is using a xss vulnerability on a subdomain to leverage the following property of. Xss In Cookie.
From securityonline.info
Steal victim's cookie using Cross Site Scripting (XSS) Xss In Cookie stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and impersonate them. I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. learn how to prevent xss vulnerabilities. Xss In Cookie.
From www.youtube.com
How To Steal Cookies Using XSS Part 1 Tech Master YouTube Xss In Cookie upon accessing the default admin, i noticed that the device generates a user cookie. the answer is that depending on context, then cookie xss can often be exploited. I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. Some routes to achieve this are. Follow the steps to create a burp collaborator. learn how. Xss In Cookie.
From lizitong67.github.io
DVWA下利用XSS获取Cookie Alston's blog Xss In Cookie upon accessing the default admin, i noticed that the device generates a user cookie. Follow the steps to create a burp collaborator. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. one possible exploit path is using a. Xss In Cookie.
From www.youtube.com
XSS Cookie Stealing Example YouTube Xss In Cookie stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. Some routes to achieve this are. upon accessing the default admin, i noticed that the device generates a user cookie. Follow the steps to create a burp collaborator. the answer is that depending on context, then. Xss In Cookie.
From null-byte.wonderhowto.com
How to Write an XSS Cookie Stealer in JavaScript to Steal Passwords Xss In Cookie stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. Some routes to achieve this are. learn how to prevent xss vulnerabilities by using output encoding, html sanitization, and framework security. by leveraging. Xss In Cookie.
From www.cnblogs.com
如何使用xss带cookie blacksunny 博客园 Xss In Cookie upon accessing the default admin, i noticed that the device generates a user cookie. one possible exploit path is using a xss vulnerability on a subdomain to leverage the following property of cookies:. Follow the steps to create a burp collaborator. learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and impersonate. Xss In Cookie.
From www.youtube.com
How to XSS for Cookie xss cookie ethicalhacking YouTube Xss In Cookie I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. Some routes to achieve this are. learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and impersonate them. upon accessing the default admin, i noticed that the device generates a user cookie. the answer is that depending on context,. Xss In Cookie.
From tutorialboy24.blogspot.com
Turning cookie based XSS into account takeover Tutorial Boy Xss In Cookie stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. upon accessing the default admin, i noticed that the device generates a user cookie. the answer is that depending on context, then cookie xss can often be exploited. learn how to use a stored xss. Xss In Cookie.
From blog.csdn.net
使用xss来打cookie_xss打cookieCSDN博客 Xss In Cookie Some routes to achieve this are. stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and impersonate them. I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. . Xss In Cookie.
From www.scribd.com
Stealing Cookies With Xss Http Cookie Online Safety & Privacy Xss In Cookie learn how to prevent xss vulnerabilities by using output encoding, html sanitization, and framework security. Some routes to achieve this are. upon accessing the default admin, i noticed that the device generates a user cookie. learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and impersonate them. stored xss attack occurs. Xss In Cookie.
From studylib.net
Cookie Stealing and XSS Presentation (Click to Xss In Cookie learn how to prevent xss vulnerabilities by using output encoding, html sanitization, and framework security. by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. the. Xss In Cookie.
From terminalcoders.blogspot.com
XSS > Theft Session Cookies Full Tutorial Xss In Cookie learn how to use a stored xss vulnerability to exfiltrate a victim's session cookie and impersonate them. one possible exploit path is using a xss vulnerability on a subdomain to leverage the following property of cookies:. learn how to prevent xss vulnerabilities by using output encoding, html sanitization, and framework security. Some routes to achieve this are.. Xss In Cookie.
From www.nakanosec.com
Bypass Login Menggunakan Cookie dari XSS Xss In Cookie by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. learn how to prevent xss vulnerabilities by using. Xss In Cookie.
From mastomi.id
Exploiting Cookie Based XSS by Finding RCE mastomi.id Xss In Cookie one possible exploit path is using a xss vulnerability on a subdomain to leverage the following property of cookies:. I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. upon accessing the default. Xss In Cookie.
From github.com
GitHub Silme94/XSSCookieStealer Advanced XSS cookie stealer that Xss In Cookie learn how to prevent xss vulnerabilities by using output encoding, html sanitization, and framework security. stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. upon accessing the default admin, i noticed that the device generates a user cookie. by leveraging xss attacks, we learned. Xss In Cookie.
From palant.info
Universal XSS in Ninja Cookie extension Almost Secure Xss In Cookie upon accessing the default admin, i noticed that the device generates a user cookie. the answer is that depending on context, then cookie xss can often be exploited. I’m exploring whether there’s a method to intercept or obtain that cookie illicitly. Follow the steps to create a burp collaborator. learn how to use a stored xss vulnerability. Xss In Cookie.
From www.youtube.com
Stealing Cookie With XSS (Demo) YouTube Xss In Cookie by leveraging xss attacks, we learned to inject malicious scripts into web pages, exfiltrate session cookies, and use them to impersonate victims, thereby gaining unauthorized access to their. stored xss attack occurs when a malicious script through user input is stored on the target server, such as in a. learn how to use a stored xss vulnerability. Xss In Cookie.