Vpn Tunnel Hardware . Let’s compare vpn hardware and vpn software by looking at the key factors: Speed, locations, setup, maintenance, updates, remote access,. Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. To do this, you need to specify the type of vpn protocol you want to use (e.g. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the same abilities to connect to a. Vpn tunneling allows data to be transmitted privately and securely over the internet. We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. The last step is to configure vpn tunnels. It also allows you to securely.
from www.linksys.com
Vpn tunneling allows data to be transmitted privately and securely over the internet. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the same abilities to connect to a. The last step is to configure vpn tunnels. We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Speed, locations, setup, maintenance, updates, remote access,. Let’s compare vpn hardware and vpn software by looking at the key factors: To do this, you need to specify the type of vpn protocol you want to use (e.g. It also allows you to securely.
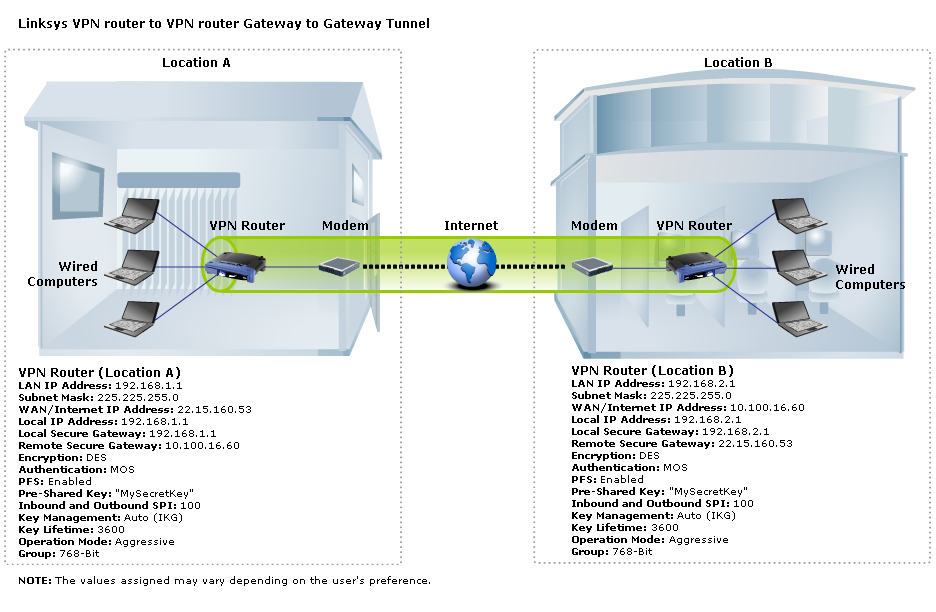
Linksys Official Support Setting up a VPN Tunnel on two (2) routers
Vpn Tunnel Hardware Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Vpn tunneling allows data to be transmitted privately and securely over the internet. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the same abilities to connect to a. We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. Let’s compare vpn hardware and vpn software by looking at the key factors: Speed, locations, setup, maintenance, updates, remote access,. To do this, you need to specify the type of vpn protocol you want to use (e.g. It also allows you to securely. The last step is to configure vpn tunnels.
From help.zscaler.com
IPSec VPN Configuration Guide for Cisco 881 ISR Zscaler Vpn Tunnel Hardware Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the same abilities to connect to a. It also allows you to securely. The last step is to configure vpn tunnels. Let’s compare vpn hardware and vpn software by looking at the key factors: To do. Vpn Tunnel Hardware.
From www.planet.com.tw
How to setup VPN tunnel with dual VRT402N? FAQ Technology Vpn Tunnel Hardware The last step is to configure vpn tunnels. Vpn tunneling allows data to be transmitted privately and securely over the internet. Speed, locations, setup, maintenance, updates, remote access,. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the same abilities to connect to a. Let’s. Vpn Tunnel Hardware.
From turingpoint.de
What makes a VPN Tunnel Secure? turingpoint Vpn Tunnel Hardware Let’s compare vpn hardware and vpn software by looking at the key factors: Vpn tunneling allows data to be transmitted privately and securely over the internet. To do this, you need to specify the type of vpn protocol you want to use (e.g. We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. The. Vpn Tunnel Hardware.
From help.ui.com
Intro to Networking Virtual Private Networks & Tunneling Ubiquiti Vpn Tunnel Hardware Speed, locations, setup, maintenance, updates, remote access,. It also allows you to securely. Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Vpn tunneling allows data to be transmitted privately and securely over the internet. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd. Vpn Tunnel Hardware.
From info-firewall-technology.laconicsecurity.com
Types Of Vpn And Vpn Protocols Explained Firewalls Software Vpn Tunnel Hardware Speed, locations, setup, maintenance, updates, remote access,. It also allows you to securely. Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the same abilities to connect to a.. Vpn Tunnel Hardware.
From info-firewalls.s4x18.com
What Is A Vpn? Firewalls Software & Hardware Solutions Vpn Tunnel Hardware Speed, locations, setup, maintenance, updates, remote access,. The last step is to configure vpn tunnels. Let’s compare vpn hardware and vpn software by looking at the key factors: Vpn tunneling allows data to be transmitted privately and securely over the internet. It also allows you to securely. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the. Vpn Tunnel Hardware.
From www.independent.co.uk
VPN tunnels Unbeatable data privacy and protection Vpn Tunnel Hardware Let’s compare vpn hardware and vpn software by looking at the key factors: Vpn tunneling allows data to be transmitted privately and securely over the internet. The last step is to configure vpn tunnels. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the same. Vpn Tunnel Hardware.
From www.youtube.com
How to Configure a SitetoSite VPN Tunnel using IPSec Custom mode Vpn Tunnel Hardware Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Vpn tunneling allows data to be transmitted privately and securely over the internet. To do this, you need to specify the type of vpn protocol you want to use (e.g. It also allows you to securely. Let’s compare vpn hardware and vpn software by. Vpn Tunnel Hardware.
From www.artofit.org
What is a vpn tunnel Artofit Vpn Tunnel Hardware It also allows you to securely. Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Speed, locations, setup, maintenance, updates, remote access,. Let’s compare vpn hardware and vpn software by looking at the key factors: Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd. Vpn Tunnel Hardware.
From www.pinterest.com
How to enable VPN split tunneling in Windows 10 Windows 10, Best vpn Vpn Tunnel Hardware It also allows you to securely. To do this, you need to specify the type of vpn protocol you want to use (e.g. We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. The last step is to configure vpn tunnels. Let’s compare vpn hardware and vpn software by looking at the key factors:. Vpn Tunnel Hardware.
From www.draytek.com.tw
Make specific host use VPN tunnel as the default gateway DrayTek Vpn Tunnel Hardware Let’s compare vpn hardware and vpn software by looking at the key factors: Vpn tunneling allows data to be transmitted privately and securely over the internet. We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. To do this, you need to specify the type of vpn protocol you want to use (e.g. The. Vpn Tunnel Hardware.
From www.comparitech.com
What is VPN Tunneling? A complete guide to VPN Tunneling Vpn Tunnel Hardware To do this, you need to specify the type of vpn protocol you want to use (e.g. It also allows you to securely. Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. Speed, locations, setup, maintenance, updates,. Vpn Tunnel Hardware.
From weibeld.net
How VPN Tunnelling Works Vpn Tunnel Hardware It also allows you to securely. Speed, locations, setup, maintenance, updates, remote access,. Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Vpn tunneling allows data to be transmitted privately and securely over the internet. To do this, you need to specify the type of vpn protocol you want to use (e.g. The. Vpn Tunnel Hardware.
From www.slideserve.com
PPT Virtual Private Networks (VPN’s) PowerPoint Presentation, free Vpn Tunnel Hardware It also allows you to securely. Vpn tunneling allows data to be transmitted privately and securely over the internet. Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the. Vpn Tunnel Hardware.
From www.slideteam.net
VPN Tunnel Connecting Different Servers Presentation Graphics Vpn Tunnel Hardware Let’s compare vpn hardware and vpn software by looking at the key factors: We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. Speed, locations, setup, maintenance, updates, remote access,. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all. Vpn Tunnel Hardware.
From www.slideteam.net
Client Connected To Various Application Through VPN Tunnel PowerPoint Vpn Tunnel Hardware It also allows you to securely. To do this, you need to specify the type of vpn protocol you want to use (e.g. We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. The last step is to configure vpn tunnels. Let’s compare vpn hardware and vpn software by looking at the key factors:. Vpn Tunnel Hardware.
From www.upwork.com
IPSec VPN Tunnel Setup Upwork Vpn Tunnel Hardware We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. To do this, you need to specify the type of vpn protocol you want to use (e.g. Let’s compare vpn hardware and vpn software by looking at the key factors: The last step is to configure vpn tunnels. Speed, locations, setup, maintenance, updates, remote. Vpn Tunnel Hardware.
From www.lifewire.com
VPN Tunnels Tutorial Types of VPNs, Protocols & More Vpn Tunnel Hardware We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Speed, locations, setup, maintenance, updates, remote access,. It also allows you to securely. The last step is to configure vpn tunnels. Essentially, choosing the right hardware vpn for. Vpn Tunnel Hardware.
From wethegeek.com
What Is A VPN Tunnel & How Does It Work Vpn Tunnel Hardware Vpn tunneling allows data to be transmitted privately and securely over the internet. To do this, you need to specify the type of vpn protocol you want to use (e.g. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the same abilities to connect to. Vpn Tunnel Hardware.
From www.configjon.com
Always On VPN Basic Deployment Guide Jon's Notes Vpn Tunnel Hardware To do this, you need to specify the type of vpn protocol you want to use (e.g. It also allows you to securely. We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. The last step is to configure vpn tunnels. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the. Vpn Tunnel Hardware.
From www.slideteam.net
VPN Tunnel Structure Showing Various Components Connected Through Cloud Vpn Tunnel Hardware The last step is to configure vpn tunnels. To do this, you need to specify the type of vpn protocol you want to use (e.g. Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Speed, locations, setup, maintenance, updates, remote access,. We reveal how vpn tunneling really works plus the most secure tunneling. Vpn Tunnel Hardware.
From instasafe.com
VPN Tunnels What They Are & How they Work Instasafe Vpn Tunnel Hardware Vpn tunneling allows data to be transmitted privately and securely over the internet. Let’s compare vpn hardware and vpn software by looking at the key factors: Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the same abilities to connect to a. We reveal how. Vpn Tunnel Hardware.
From top-firewall-hardware.myinformationsecuritypolicy.com
Traffic Protection Using Ipsec Tunneling Protocol Overview Firewalls Vpn Tunnel Hardware Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. To do this, you need to specify the type of vpn protocol you want to use (e.g. We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market. Essentially, choosing the right hardware vpn for your outer encryption tunnel. Vpn Tunnel Hardware.
From info.pivitglobal.com
Deep Dive into the SitetoSite VPN Tunnel Negotiation Process Vpn Tunnel Hardware Vpn tunneling allows data to be transmitted privately and securely over the internet. The last step is to configure vpn tunnels. It also allows you to securely. Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the same abilities to connect to a. Some hardware. Vpn Tunnel Hardware.
From www.canadavpns.com
The Top 5 Best VPN With Split Tunneling in 2022 Vpn Tunnel Hardware Let’s compare vpn hardware and vpn software by looking at the key factors: Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. The last step is to configure vpn tunnels. Speed, locations, setup, maintenance, updates, remote access,. We reveal how vpn tunneling really works plus the most secure tunneling vpns on the market.. Vpn Tunnel Hardware.
From best-firewall-software.s4x18.com
Introduction To The Tunneling Process Firewalls Software & Hardware Vpn Tunnel Hardware The last step is to configure vpn tunnels. Speed, locations, setup, maintenance, updates, remote access,. Let’s compare vpn hardware and vpn software by looking at the key factors: Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. It also allows you to securely. To do this, you need to specify the type of. Vpn Tunnel Hardware.
From vpncentral.com
VPN Tunnel Types — How They Work and Best Use Cases Vpn Tunnel Hardware It also allows you to securely. To do this, you need to specify the type of vpn protocol you want to use (e.g. Vpn tunneling allows data to be transmitted privately and securely over the internet. Let’s compare vpn hardware and vpn software by looking at the key factors: We reveal how vpn tunneling really works plus the most secure. Vpn Tunnel Hardware.
From bulkyvpn.com
What is a VPN tunnel and how does it work? Vpn Tunnel Hardware To do this, you need to specify the type of vpn protocol you want to use (e.g. Let’s compare vpn hardware and vpn software by looking at the key factors: Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. It also allows you to securely. Vpn tunneling allows data to be transmitted privately. Vpn Tunnel Hardware.
From nordvpn.com
VPN tunnel what is it and how does it work? NordVPN Vpn Tunnel Hardware To do this, you need to specify the type of vpn protocol you want to use (e.g. Let’s compare vpn hardware and vpn software by looking at the key factors: Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the same abilities to connect to. Vpn Tunnel Hardware.
From info-firewalls.s4x18.com
Vpn Tunnels Explained What Are They And How Can Firewalls Vpn Tunnel Hardware Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Speed, locations, setup, maintenance, updates, remote access,. It also allows you to securely. To do this, you need to specify the type of vpn protocol you want to use (e.g. Vpn tunneling allows data to be transmitted privately and securely over the internet. We. Vpn Tunnel Hardware.
From www.researchgate.net
VPN tunnel and multilayer IP security model. Download Scientific Diagram Vpn Tunnel Hardware Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Speed, locations, setup, maintenance, updates, remote access,. It also allows you to securely. Let’s compare vpn hardware and vpn software by looking at the key factors: Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd. Vpn Tunnel Hardware.
From www.lifewire.com
What Are VPN Tunnels? Vpn Tunnel Hardware Essentially, choosing the right hardware vpn for your outer encryption tunnel eliminates the need to have an rd in your architecture, but affords all the same abilities to connect to a. Speed, locations, setup, maintenance, updates, remote access,. It also allows you to securely. To do this, you need to specify the type of vpn protocol you want to use. Vpn Tunnel Hardware.
From cooltechzone.com
What is a VPN Tunnel Cooltechzone Vpn Tunnel Hardware To do this, you need to specify the type of vpn protocol you want to use (e.g. Speed, locations, setup, maintenance, updates, remote access,. Vpn tunneling allows data to be transmitted privately and securely over the internet. It also allows you to securely. Let’s compare vpn hardware and vpn software by looking at the key factors: The last step is. Vpn Tunnel Hardware.
From helpx.adobe.com
Create IPSec VPN connection between AWS VPC and customer network Vpn Tunnel Hardware Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Vpn tunneling allows data to be transmitted privately and securely over the internet. Speed, locations, setup, maintenance, updates, remote access,. Let’s compare vpn hardware and vpn software by looking at the key factors: The last step is to configure vpn tunnels. We reveal how. Vpn Tunnel Hardware.
From www.linksys.com
Linksys Official Support Setting up a VPN Tunnel on two (2) routers Vpn Tunnel Hardware Let’s compare vpn hardware and vpn software by looking at the key factors: The last step is to configure vpn tunnels. It also allows you to securely. Some hardware vpns, like the gosilent cube, can protect many devices simultaneously using reliable hardware vpn. Speed, locations, setup, maintenance, updates, remote access,. Essentially, choosing the right hardware vpn for your outer encryption. Vpn Tunnel Hardware.