What Is Access Control In Database . Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. Database access control is a method of allowing access to company’s sensitive data only to those people (database users) who are allowed to access such data and to restrict access to unauthorized. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. The security mechanism of dbms must include some provisions for restricting access to the data base by. At a high level, access control is a selective. Access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to company data. By controlling who or what has access to a resource, it ensures that only. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are allowed.
from form-content-updates-1901--budibase.netlify.app
Access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to company data. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. At a high level, access control is a selective. The security mechanism of dbms must include some provisions for restricting access to the data base by. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Database access control is a method of allowing access to company’s sensitive data only to those people (database users) who are allowed to access such data and to restrict access to unauthorized. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. By controlling who or what has access to a resource, it ensures that only. Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are allowed.
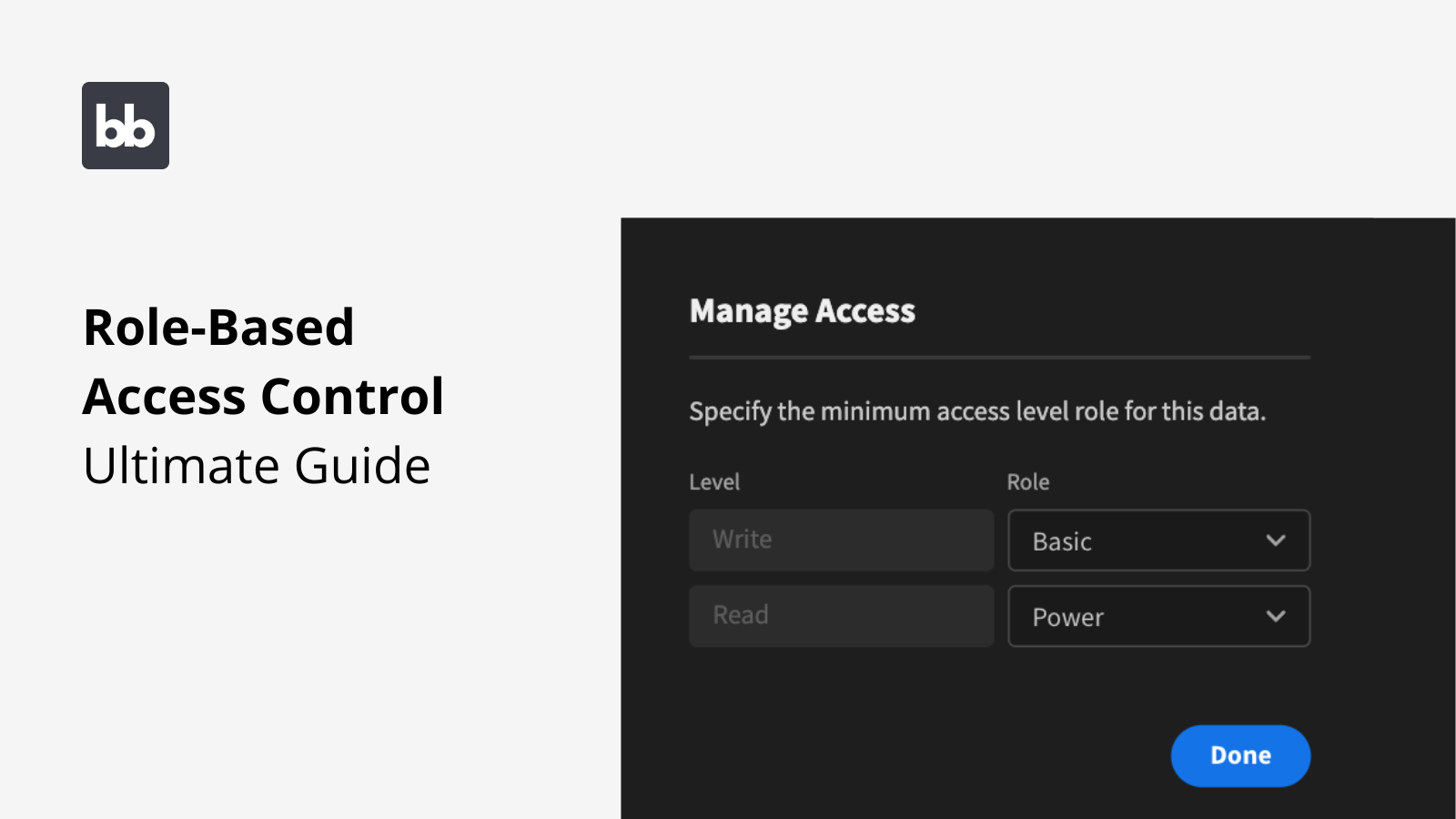
RoleBased Access Control Ultimate Guide
What Is Access Control In Database Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. Access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to company data. The security mechanism of dbms must include some provisions for restricting access to the data base by. Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are allowed. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Database access control is a method of allowing access to company’s sensitive data only to those people (database users) who are allowed to access such data and to restrict access to unauthorized. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. At a high level, access control is a selective. Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. By controlling who or what has access to a resource, it ensures that only.
From badamateur.weebly.com
Free Microsoft Access Stock Control Database Design badamateur What Is Access Control In Database Database access control is a method of allowing access to company’s sensitive data only to those people (database users) who are allowed to access such data and to restrict access to unauthorized. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is an essential element of security that determines who is allowed. What Is Access Control In Database.
From thecyphere.com
Access Control Security Types Of Access Control What Is Access Control In Database Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to company data. Database access control, or db access control, is a method of allowing access to. What Is Access Control In Database.
From www.cctvminneapolis.com
Benefits of Access Control What Is Access Control In Database Database access control is a method of allowing access to company’s sensitive data only to those people (database users) who are allowed to access such data and to restrict access to unauthorized. By controlling who or what has access to a resource, it ensures that only. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized. What Is Access Control In Database.
From www.networkeducator.com
What Is Access Control List (ACL) & How It Works Network Educator What Is Access Control In Database By controlling who or what has access to a resource, it ensures that only. At a high level, access control is a selective. Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are allowed. Key security principles, such as “least privilege” and “separation of privilege”, are. What Is Access Control In Database.
From www.youtube.com
Authentication, Authorization and Access Control in Database Management What Is Access Control In Database By controlling who or what has access to a resource, it ensures that only. Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are allowed. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,.. What Is Access Control In Database.
From www.stellarinfo.com
Compact and Repair a Corrupt MS Access Database Free Methods What Is Access Control In Database Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to company data. By controlling who or what has access to a resource, it ensures that only. Access control is an essential element. What Is Access Control In Database.
From hackersparadise01.com
What is Access Control? Important Networking Basics Part 25 What Is Access Control In Database Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. Access control is an essential element of security that determines who is allowed to access. What Is Access Control In Database.
From www.cdvi.co.uk
What is access control? Access control explained CDVI UK What Is Access Control In Database Database access control is a method of allowing access to company’s sensitive data only to those people (database users) who are allowed to access such data and to restrict access to unauthorized. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. The security mechanism of dbms must include some provisions for restricting access to. What Is Access Control In Database.
From www.slideteam.net
Access Control In Secured Database Management System PPT Template What Is Access Control In Database Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. The security mechanism of dbms must include some provisions for restricting access to the data base by. Access control is an. What Is Access Control In Database.
From www.slideserve.com
PPT Chapter 9 Database Security PowerPoint Presentation, free What Is Access Control In Database The security mechanism of dbms must include some provisions for restricting access to the data base by. Access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to company data. Database access control is a method of allowing access to company’s sensitive data only to those people (database. What Is Access Control In Database.
From eskills.academy
Mastering Access Control in Data Security Eskills Academy What Is Access Control In Database Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. At a high level, access control is a selective. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Database access control, or db access. What Is Access Control In Database.
From www.techxio.com
Extended Access List Control configuration with example What Is Access Control In Database The security mechanism of dbms must include some provisions for restricting access to the data base by. At a high level, access control is a selective. Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are allowed. Key security principles, such as “least privilege” and “separation. What Is Access Control In Database.
From www.conceptdraw.com
Network Security What Is Access Control In Database Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are allowed. At a high level, access control is a selective. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control is a proactive. What Is Access Control In Database.
From www.slideshare.net
Database Security What Is Access Control In Database Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. By controlling who or what has access to a resource, it ensures that only. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is a method of guaranteeing that users. What Is Access Control In Database.
From liquidvideotechnologies.com
What is Access Control Liquid Video Technologies What Is Access Control In Database By controlling who or what has access to a resource, it ensures that only. Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. At a high level, access control is a selective. Access control is a proactive security measure that helps deter, detect, and prevent. What Is Access Control In Database.
From amplication.com
The Right Type of Access Control RBAC, PBAC or PBAC Amplication What Is Access Control In Database By controlling who or what has access to a resource, it ensures that only. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. At a high level, access control is a selective. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Key. What Is Access Control In Database.
From www.ekransystem.com
Mandatory (MAC) vs Discretionary Access Control (DAC) Differences What Is Access Control In Database Database access control is a method of allowing access to company’s sensitive data only to those people (database users) who are allowed to access such data and to restrict access to unauthorized. The security mechanism of dbms must include some provisions for restricting access to the data base by. Key security principles, such as “least privilege” and “separation of privilege”,. What Is Access Control In Database.
From www.touchstar-atc.com
Access Control Systems, Turnstiles & Biometric Devices TouchStar What Is Access Control In Database The security mechanism of dbms must include some provisions for restricting access to the data base by. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what.. What Is Access Control In Database.
From blog.nortechcontrol.com
What Is Access Control? (Simple Guide) What Is Access Control In Database At a high level, access control is a selective. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to company data. Access control is a. What Is Access Control In Database.
From nepcodex.com
Access control mechanisms in software — Programming What Is Access Control In Database Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are. What Is Access Control In Database.
From www.upguard.com
What is Access Control? The Essential Cybersecurity Practice UpGuard What Is Access Control In Database Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are allowed. By controlling who or what has access to a resource, it ensures that only. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in. What Is Access Control In Database.
From www.slideserve.com
PPT Access Control Matrix PowerPoint Presentation, free download ID What Is Access Control In Database Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are allowed. Access control is a proactive security measure that helps deter, detect,. What Is Access Control In Database.
From www.360connect.com
5 Things You Need to Know About Access Control Software 360Connect What Is Access Control In Database Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. The security mechanism of dbms must include some provisions for restricting access to the data base by. At a high level,. What Is Access Control In Database.
From www.youtube.com
Flexible Database Access Control YouTube What Is Access Control In Database The security mechanism of dbms must include some provisions for restricting access to the data base by. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups. What Is Access Control In Database.
From www.csoonline.com
What is access control? A key component of data security CSO Online What Is Access Control In Database Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are allowed. Access control is an essential element of security that determines who is allowed to access certain data, apps, and resources—and in what. Key security principles, such as “least privilege” and “separation of privilege”, are employed. What Is Access Control In Database.
From www.springboard.com
How To an Information Security Analyst [9 Step Guide] What Is Access Control In Database Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are allowed. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized. What Is Access Control In Database.
From merkez-ihayat.blogspot.ca
Access Database Management With Excel Userform Hints And Tips About What Is Access Control In Database Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Database access control is a method of allowing access to company’s sensitive data only to. What Is Access Control In Database.
From dicsan.com
Access control server Dicsan Technology What Is Access Control In Database Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. Access control is a method of guaranteeing that users are who they say they are and that they have the appropriate. What Is Access Control In Database.
From brownholo.weebly.com
Microsoft Access Database Examples brownholo What Is Access Control In Database Database access control is a method of allowing access to company’s sensitive data only to those people (database users) who are allowed to access such data and to restrict access to unauthorized. The security mechanism of dbms must include some provisions for restricting access to the data base by. At a high level, access control is a selective. Access control. What Is Access Control In Database.
From frontegg.com
What is RoleBased Access Control RBAC vs ABAC What Is Access Control In Database Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. The security mechanism of dbms must include some provisions for restricting access to the data base by. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Access control is an. What Is Access Control In Database.
From form-content-updates-1901--budibase.netlify.app
RoleBased Access Control Ultimate Guide What Is Access Control In Database Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. By controlling who or what has access to a resource, it ensures that only. Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. Access. What Is Access Control In Database.
From www.techtarget.com
Secure data in the cloud with encryption and access controls TechTarget What Is Access Control In Database The security mechanism of dbms must include some provisions for restricting access to the data base by. Database access control is a method of allowing access to company’s sensitive data only to those people (database users) who are allowed to access such data and to restrict access to unauthorized. Access control is an essential element of security that determines who. What Is Access Control In Database.
From manuals.xtuple.com
1. The Access Database What Is Access Control In Database By controlling who or what has access to a resource, it ensures that only. At a high level, access control is a selective. Access control is a proactive security measure that helps deter, detect, and prevent unauthorized access. Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups. What Is Access Control In Database.
From evbn.org
Top 9 access control in network security in 2022 EUVietnam Business What Is Access Control In Database Key security principles, such as “least privilege” and “separation of privilege”, are employed to give users the minimum level of access required to perform. At a high level, access control is a selective. Database access control, or db access control, is a method of allowing access to a company’s sensitive information only to user groups who are allowed. Database access. What Is Access Control In Database.
From cyral.com
Attribute Based Access Control in Databases ABAC Security What Is Access Control In Database Access control is a comprehensive data security mechanism that determines who is permitted to access specific digital resources, such as data,. At a high level, access control is a selective. Database access control is a method of allowing access to company’s sensitive data only to those people (database users) who are allowed to access such data and to restrict access. What Is Access Control In Database.