Applicator Token . create an application token provider that can retrieve tokens for the given application from the given context, using the given. — this applicator will change your chosen lion's base to green. — first of all, validate the ver claim's value is 1.0. — you can do so with your emnify credentials or with an application token which is more secure. — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. A typical jwt looks like this: Next, check to see if the jwt is an access token or an id token. — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent. Like contacts, the base itself cannot pass onto any. cloudflare access includes the application token with all authenticated requests to your origin.
from www.contentstack.com
create an application token provider that can retrieve tokens for the given application from the given context, using the given. — this applicator will change your chosen lion's base to green. Next, check to see if the jwt is an access token or an id token. — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent. A typical jwt looks like this: — you can do so with your emnify credentials or with an application token which is more secure. — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. Like contacts, the base itself cannot pass onto any. — first of all, validate the ver claim's value is 1.0. cloudflare access includes the application token with all authenticated requests to your origin.
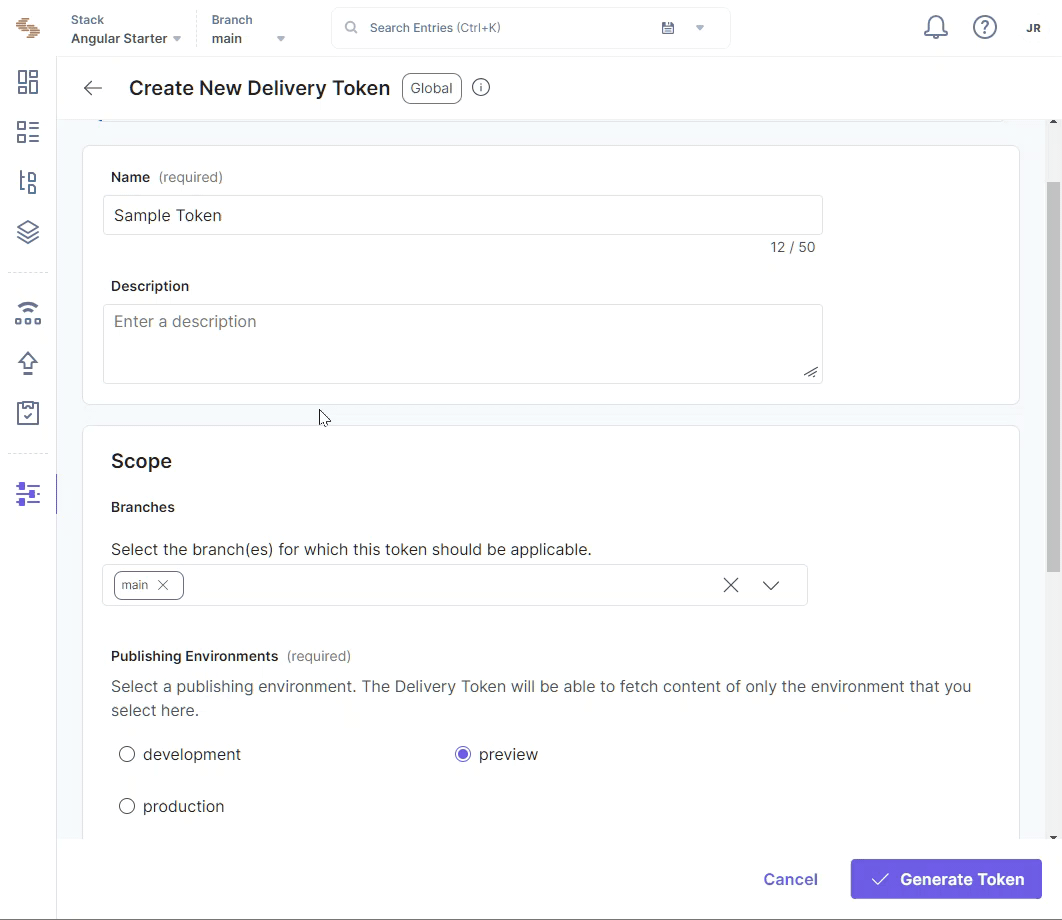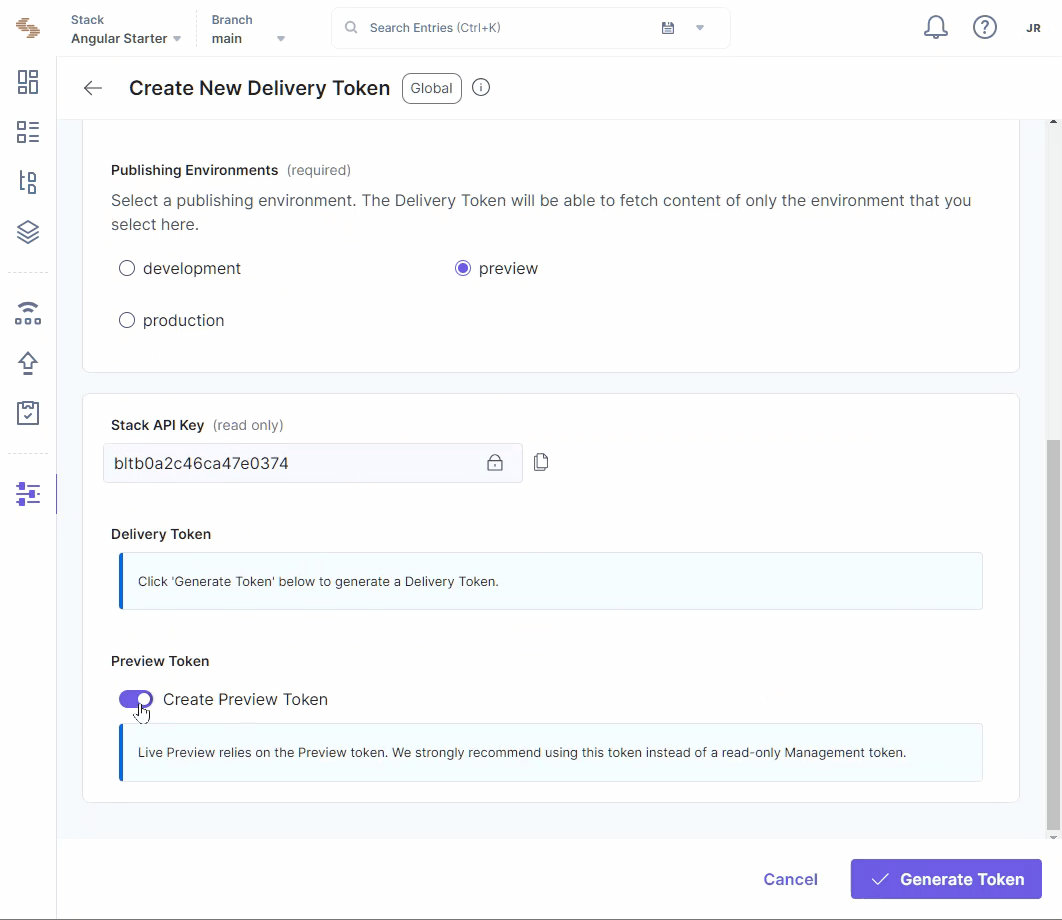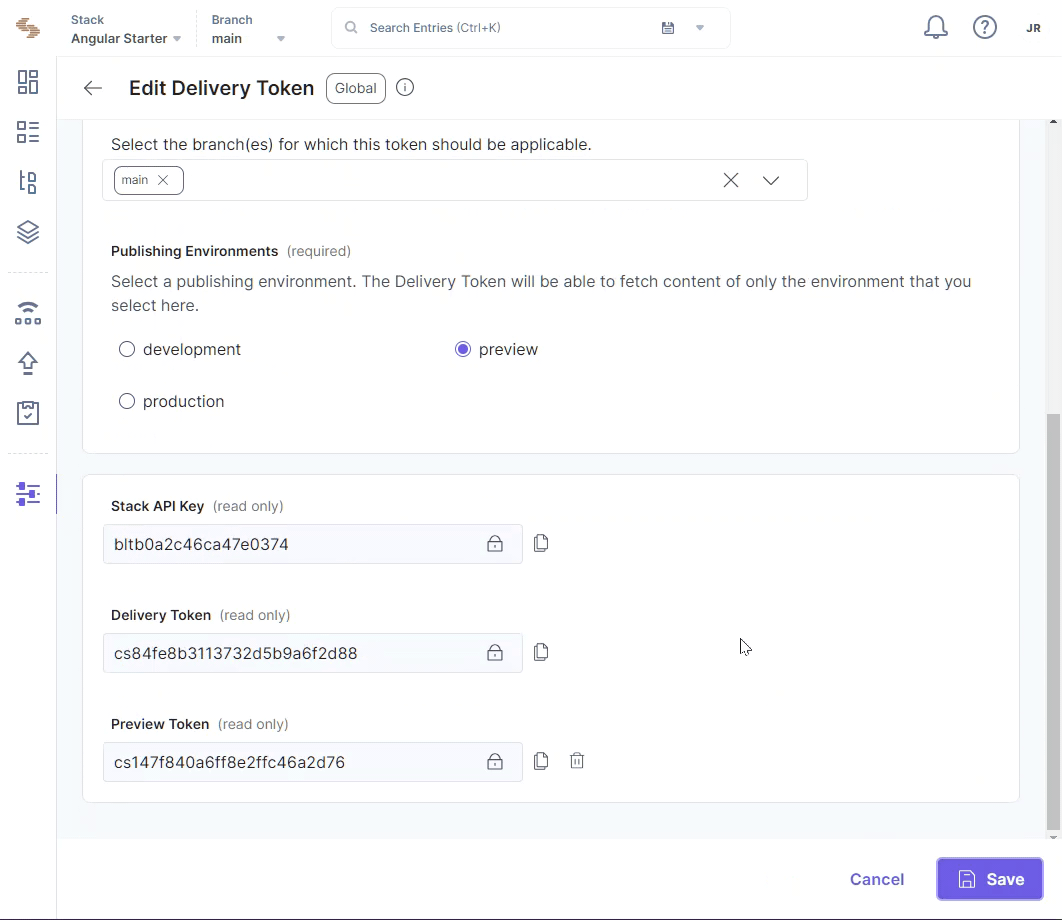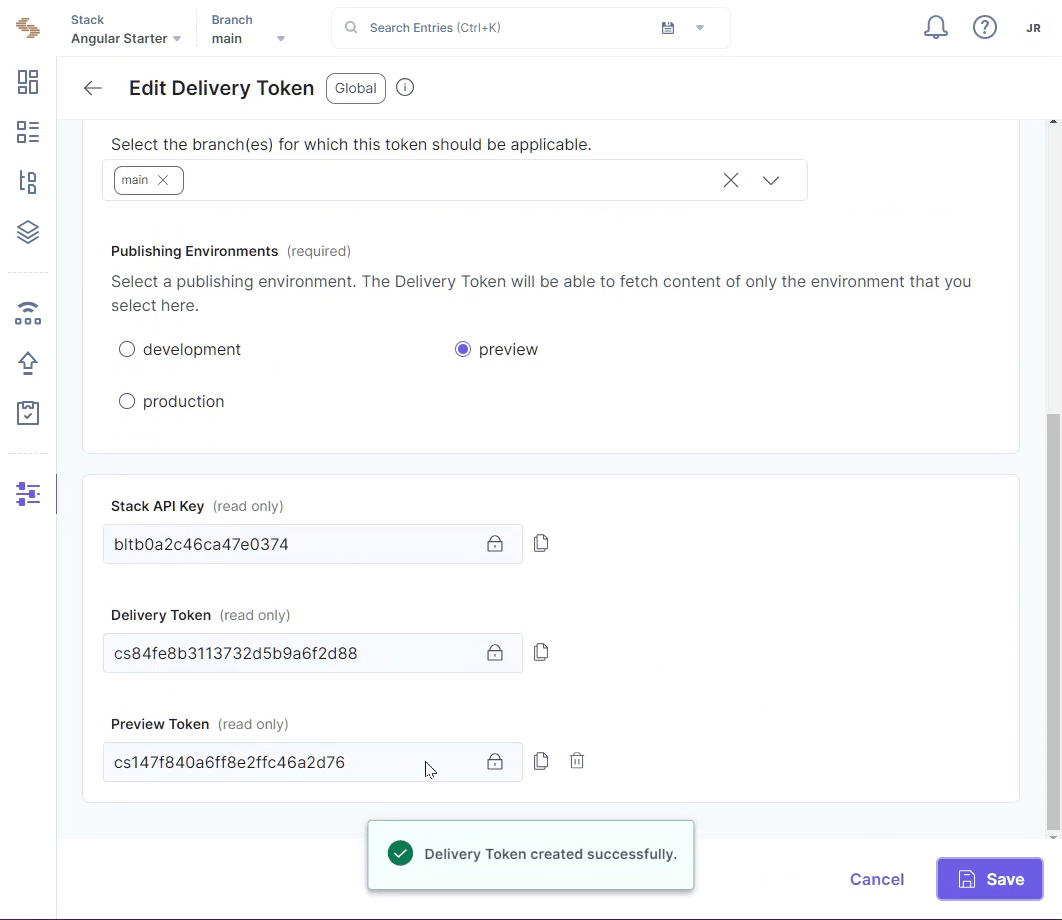
Create a Delivery Token Contentstack
Applicator Token — you can do so with your emnify credentials or with an application token which is more secure. Next, check to see if the jwt is an access token or an id token. create an application token provider that can retrieve tokens for the given application from the given context, using the given. — this applicator will change your chosen lion's base to green. A typical jwt looks like this: cloudflare access includes the application token with all authenticated requests to your origin. — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent. — you can do so with your emnify credentials or with an application token which is more secure. — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. Like contacts, the base itself cannot pass onto any. — first of all, validate the ver claim's value is 1.0.
From github.com
GitHub guangyusong/llmtokenvisualizer React LLM Token Visualizer Applicator Token create an application token provider that can retrieve tokens for the given application from the given context, using the given. cloudflare access includes the application token with all authenticated requests to your origin. — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. Next, check to see. Applicator Token.
From www.dotnetcurry.com
Securing API using Token Based Authentication and using it Applicator Token cloudflare access includes the application token with all authenticated requests to your origin. — this applicator will change your chosen lion's base to green. Next, check to see if the jwt is an access token or an id token. A typical jwt looks like this: Like contacts, the base itself cannot pass onto any. create an application. Applicator Token.
From castbox.fm
NonFungible Tokens (NFT’s) Explained [Beginner’s Guide] Applicator Token — this applicator will change your chosen lion's base to green. — you can do so with your emnify credentials or with an application token which is more secure. — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. create an application token provider that can. Applicator Token.
From support.zendesk.com
Tutorial de API de Chat generación de un token de OAuth (cuentas de Applicator Token Like contacts, the base itself cannot pass onto any. A typical jwt looks like this: — you can do so with your emnify credentials or with an application token which is more secure. cloudflare access includes the application token with all authenticated requests to your origin. create an application token provider that can retrieve tokens for the. Applicator Token.
From plugins.miniorange.com
Setup Yubikey Hardware Token for 2Factor Authentication WordPress Applicator Token — first of all, validate the ver claim's value is 1.0. — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent. — you can do so with your emnify credentials or with an application token which is more secure. — it's protected by. Applicator Token.
From www.alwin.io
Hera Token Multichain DEX Aggregator with Wide Token Range Applicator Token — this applicator will change your chosen lion's base to green. — first of all, validate the ver claim's value is 1.0. cloudflare access includes the application token with all authenticated requests to your origin. — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the. Applicator Token.
From www.nfcw.com
Antelop explains how token management solutions can help banks cut Applicator Token A typical jwt looks like this: — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. create an application token provider that can retrieve tokens for the given application from the given context, using the given. — this applicator will change your chosen lion's base to green.. Applicator Token.
From www.bitcoininsider.org
Cryptocurrency Coins vs Tokens Key Differences Explained Bitcoin Insider Applicator Token A typical jwt looks like this: — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. — first of all, validate the ver claim's value is 1.0. Like contacts, the base itself cannot pass onto any. — an oauth 2.0 access token acts like a digital key. Applicator Token.
From www.biko.it
Automatic Tape Applicator Type ATAWB Products Biko Applicator Token Like contacts, the base itself cannot pass onto any. — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. cloudflare access includes the application token with all authenticated requests to your origin. — an oauth 2.0 access token acts like a digital key granted to an application. Applicator Token.
From www.autodesk.com.br
Onde encontrar o equilíbrio de tokens no Fusion Applicator Token create an application token provider that can retrieve tokens for the given application from the given context, using the given. — first of all, validate the ver claim's value is 1.0. Next, check to see if the jwt is an access token or an id token. — you can do so with your emnify credentials or with. Applicator Token.
From www.amazon.com
25/50 Zhang Disposable Mascara Applicator Token Shiny Hair Applicator Token — first of all, validate the ver claim's value is 1.0. — you can do so with your emnify credentials or with an application token which is more secure. create an application token provider that can retrieve tokens for the given application from the given context, using the given. — an oauth 2.0 access token acts. Applicator Token.
From www.prentke-romich.de
APPlicator Prentke Romich Deutschland Applicator Token — first of all, validate the ver claim's value is 1.0. A typical jwt looks like this: — this applicator will change your chosen lion's base to green. Like contacts, the base itself cannot pass onto any. — you can do so with your emnify credentials or with an application token which is more secure. —. Applicator Token.
From www.alwin.io
Polygon Token Development Create a Token on Polygon Network! Applicator Token — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent. cloudflare access includes the application token with all authenticated requests to your origin. — this applicator will change your chosen lion's base to green. Like contacts, the base itself cannot pass onto any. Next,. Applicator Token.
From quarkus.io
OpenID Connect (OIDC) Bearer token authentication Quarkus Applicator Token — first of all, validate the ver claim's value is 1.0. A typical jwt looks like this: — you can do so with your emnify credentials or with an application token which is more secure. — this applicator will change your chosen lion's base to green. Next, check to see if the jwt is an access token. Applicator Token.
From www.networkingsignal.com
What Are Hardware Tokens And How Do They Work? Applicator Token Like contacts, the base itself cannot pass onto any. A typical jwt looks like this: — this applicator will change your chosen lion's base to green. create an application token provider that can retrieve tokens for the given application from the given context, using the given. — it's protected by the microsoft identity platform, which uses oauth. Applicator Token.
From www.biko.it
Automatic Tape Applicator ATANB Products Biko Applicator Token — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent. — this applicator will change your chosen lion's base to green. Like contacts, the. Applicator Token.
From www.icoclone.com
How to convert traditional assets into token Asset tokenization Applicator Token create an application token provider that can retrieve tokens for the given application from the given context, using the given. — this applicator will change your chosen lion's base to green. cloudflare access includes the application token with all authenticated requests to your origin. Like contacts, the base itself cannot pass onto any. — first of. Applicator Token.
From klever.zendesk.com
How to add new token to your Portfolio Klever Support Applicator Token — first of all, validate the ver claim's value is 1.0. — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent. A typical jwt looks like this: — this applicator will change your chosen lion's base to green. — you can do so. Applicator Token.
From cryptopanic.com
Airdrop Token Terminal Comment y être éligible Applicator Token cloudflare access includes the application token with all authenticated requests to your origin. Like contacts, the base itself cannot pass onto any. — this applicator will change your chosen lion's base to green. create an application token provider that can retrieve tokens for the given application from the given context, using the given. — an oauth. Applicator Token.
From quarkus.io
OpenID Connect (OIDC) Bearer token authentication Quarkus Applicator Token — first of all, validate the ver claim's value is 1.0. Next, check to see if the jwt is an access token or an id token. — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent. Like contacts, the base itself cannot pass onto any.. Applicator Token.
From stories.salesforcecodex.com
Generate Salesforce Authentication Token using Postman Applicator Token — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. create an application token provider that can retrieve tokens for the given application from the given context, using the given. — this applicator will change your chosen lion's base to green. A typical jwt looks like this:. Applicator Token.
From muens.io
How to implement LPTokens Applicator Token — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent. — you can do so with your emnify credentials or with an application token. Applicator Token.
From www.contentstack.com
Create a Delivery Token Contentstack Applicator Token — you can do so with your emnify credentials or with an application token which is more secure. — this applicator will change your chosen lion's base to green. — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. create an application token provider that can. Applicator Token.
From www.cointribune.com
Le guide étape par étape pour créer un security token Applicator Token — you can do so with your emnify credentials or with an application token which is more secure. cloudflare access includes the application token with all authenticated requests to your origin. Like contacts, the base itself cannot pass onto any. — an oauth 2.0 access token acts like a digital key granted to an application by an. Applicator Token.
From seatable.io
Creating an API token SeaTable Applicator Token — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent. cloudflare access includes the application token with all authenticated requests to your origin. — you can do so with your emnify credentials or with an application token which is more secure. — it's. Applicator Token.
From gatekeeperhelp.zendesk.com
How to add a new GateKeeper token to a user. GateKeeper Applicator Token — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. create an application token provider that can retrieve tokens for the given application from the given context, using the given. cloudflare access includes the application token with all authenticated requests to your origin. — an oauth. Applicator Token.
From learn.microsoft.com
Control access to IoT Hub using SAS tokens Microsoft Learn Applicator Token create an application token provider that can retrieve tokens for the given application from the given context, using the given. — first of all, validate the ver claim's value is 1.0. — you can do so with your emnify credentials or with an application token which is more secure. Like contacts, the base itself cannot pass onto. Applicator Token.
From www.vrogue.co
Token Based Authentication Using Json Tokens Vrogue Applicator Token — you can do so with your emnify credentials or with an application token which is more secure. Like contacts, the base itself cannot pass onto any. — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. — an oauth 2.0 access token acts like a digital. Applicator Token.
From patentbusinesslawyer.com
How do Utility Tokens Increase in Value Applicator Token A typical jwt looks like this: — first of all, validate the ver claim's value is 1.0. Next, check to see if the jwt is an access token or an id token. create an application token provider that can retrieve tokens for the given application from the given context, using the given. — an oauth 2.0 access. Applicator Token.
From www.dotnetcurry.com
Securing API using Token Based Authentication and using it Applicator Token — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. Like contacts, the base itself cannot pass onto any. A typical jwt looks like this: — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent.. Applicator Token.
From logi24.lv
PENOSIL EasyPRO All Purpose PUfoam with unique applicator Applicator Token Next, check to see if the jwt is an access token or an id token. — you can do so with your emnify credentials or with an application token which is more secure. — this applicator will change your chosen lion's base to green. create an application token provider that can retrieve tokens for the given application. Applicator Token.
From www.indiamart.com
Digital Signature Token Dsc Token Proxkey New Registration & Renewal at Applicator Token — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. Like contacts, the base itself cannot pass onto any. Next, check to see if the jwt is an access token or an id token. cloudflare access includes the application token with all authenticated requests to your origin. . Applicator Token.
From blog.zilliqa.com
How to launch your own token on Zilliqa Applicator Token — first of all, validate the ver claim's value is 1.0. — you can do so with your emnify credentials or with an application token which is more secure. Like contacts, the base itself cannot pass onto any. A typical jwt looks like this: — an oauth 2.0 access token acts like a digital key granted to. Applicator Token.
From www.machine.no
Etikett Applikatorer GJ MACHINE AS Applicator Token — it's protected by the microsoft identity platform, which uses oauth access tokens to verify that an app is authorized. — an oauth 2.0 access token acts like a digital key granted to an application by an authorization server, after the user's consent. — this applicator will change your chosen lion's base to green. Next, check to. Applicator Token.
From blog.thirdweb.com
What is ERC721? The Ethereum NFT Standard Explained Applicator Token — first of all, validate the ver claim's value is 1.0. Next, check to see if the jwt is an access token or an id token. cloudflare access includes the application token with all authenticated requests to your origin. A typical jwt looks like this: — you can do so with your emnify credentials or with an. Applicator Token.