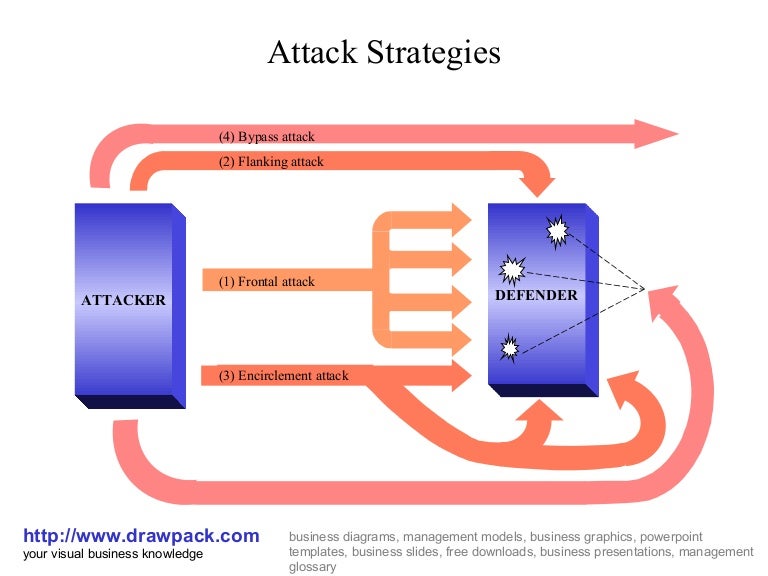
Bypass Attack Examples . Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware. A company following a bypass attack strategy simply outplays the competitor. The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier markets. That is, a firm doesn’t identify the weak areas of its competitor or launch. Itc and hul could be the best examples. The purpose of this strategy is to broaden the firm’s resources by capturing the market share of the competing firm. Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. A few examples of bypass attack strategy can be showcased as below. Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro quo, tailgating and diversion theft. For example, the beginning of the apple ipod.
from www.slideshare.net
That is, a firm doesn’t identify the weak areas of its competitor or launch. For example, the beginning of the apple ipod. The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier markets. A company following a bypass attack strategy simply outplays the competitor. A few examples of bypass attack strategy can be showcased as below. The purpose of this strategy is to broaden the firm’s resources by capturing the market share of the competing firm. Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro quo, tailgating and diversion theft. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware.
Attack strategies business diagram
Bypass Attack Examples Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware. Itc and hul could be the best examples. The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier markets. That is, a firm doesn’t identify the weak areas of its competitor or launch. For example, the beginning of the apple ipod. Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro quo, tailgating and diversion theft. Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware. A few examples of bypass attack strategy can be showcased as below. Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. The purpose of this strategy is to broaden the firm’s resources by capturing the market share of the competing firm. A company following a bypass attack strategy simply outplays the competitor.
From getlucidity.com
Bypass Attack Strategy Guide Lucidity Bypass Attack Examples Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro quo, tailgating and diversion theft. The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier markets. The bypass attack is the most indirect marketing strategy adopted by the challenging firm. Bypass Attack Examples.
From us.norton.com
Password attack 101 A definition + 10 types of password attacks Norton Bypass Attack Examples A company following a bypass attack strategy simply outplays the competitor. Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. A few examples of bypass attack strategy can be showcased as below. The purpose of this strategy is to broaden the firm’s resources by capturing the market share of. Bypass Attack Examples.
From secureb4.io
Different Types of Password Attacks An Overview Bypass Attack Examples A company following a bypass attack strategy simply outplays the competitor. The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier markets. Itc and hul could be the best examples. The bypass attack is the most indirect marketing strategy adopted by the challenging firm. Bypass Attack Examples.
From www.youtube.com
OTP BYPASS ATTACK ( HOW TO BYPASS OTP ON REAL WORLD DOMAIN) YouTube Bypass Attack Examples The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware. That is, a firm doesn’t identify the weak areas of its competitor or launch.. Bypass Attack Examples.
From www.automox.com
What is Authentication Bypass? Bypass Attack Examples A few examples of bypass attack strategy can be showcased as below. Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware. A company following a bypass attack strategy simply. Bypass Attack Examples.
From secureteam.co.uk
Phishing Attacks That Can Bypass MFA SecureTeam Bypass Attack Examples For example, the beginning of the apple ipod. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware. The bypass attack is the indirect. Bypass Attack Examples.
From www.vectra.ai
Attack Anatomy MFA Bypass Bypass Attack Examples Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware. Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro quo, tailgating and diversion theft. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor. Bypass Attack Examples.
From www.youtube.com
How MFA Bypass Attacks Work YouTube Bypass Attack Examples For example, the beginning of the apple ipod. The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier markets. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier. Bypass Attack Examples.
From ndupress.ndu.edu
Operational Graphics for Cyberspace > National Defense University Press > News Bypass Attack Examples For example, the beginning of the apple ipod. Itc and hul could be the best examples. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but. Bypass Attack Examples.
From www.slideserve.com
PPT A Security Analysis of the PHP language PowerPoint Presentation, free download ID9238462 Bypass Attack Examples The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier markets. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. Once they circumvent authentication, attackers can escalate. Bypass Attack Examples.
From www.slideserve.com
PPT Dealing with Competition PowerPoint Presentation, free download ID1782046 Bypass Attack Examples Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. That is, a firm doesn’t identify the weak areas of its competitor or launch. The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier. Bypass Attack Examples.
From www.vrogue.co
Bypass Or Steal Login Otp Using Phishing Attack vrogue.co Bypass Attack Examples A company following a bypass attack strategy simply outplays the competitor. Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware. Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. The bypass attack is the most indirect marketing strategy. Bypass Attack Examples.
From www.researchgate.net
(PDF) ControlFlow Integrity Attacks and Protections Bypass Attack Examples The purpose of this strategy is to broaden the firm’s resources by capturing the market share of the competing firm. A few examples of bypass attack strategy can be showcased as below. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. Itc and. Bypass Attack Examples.
From www.golinuxcloud.com
How to bypass CSRF Protection [5 Different Methods] GoLinuxCloud Bypass Attack Examples That is, a firm doesn’t identify the weak areas of its competitor or launch. Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro quo, tailgating and diversion theft. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. The. Bypass Attack Examples.
From www.netskope.com
MultiFactor Authentication (MFA) Bypass Through ManintheMiddle Phishing Attacks Netskope Bypass Attack Examples Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro quo, tailgating and diversion theft. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. The purpose of this strategy is to broaden the firm’s resources by capturing the market. Bypass Attack Examples.
From terralogic.com
MFA BYPASS TECHNIQUES A Threat Analysis from Microsoft Bypass Attack Examples Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. The bypass attack is the indirect attack, wherein the market challenger does not attack. Bypass Attack Examples.
From epoxywar.web.fc2.com
How To Bypass Restrictions Bypass Attack Examples A company following a bypass attack strategy simply outplays the competitor. A few examples of bypass attack strategy can be showcased as below. Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro quo, tailgating and diversion theft. Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication. Bypass Attack Examples.
From www.slideserve.com
PPT Bypass Windows Defender Attack Surface Reduction PowerPoint Presentation ID9081862 Bypass Attack Examples The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware. That is, a firm doesn’t identify the weak areas of its competitor or launch.. Bypass Attack Examples.
From www.youtube.com
Hacking Two Factor Authentication Four Methods for Bypassing 2FA and MFA YouTube Bypass Attack Examples The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. A company following a bypass attack strategy simply outplays the competitor. The purpose of. Bypass Attack Examples.
From integrationobjects.com
Windows Server Security Feature Bypass Integration Objects Bypass Attack Examples The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro. Bypass Attack Examples.
From mainnerve.com
3 Ways To Protect Your Applications From Authentication Bypass Attacks MainNerve Bypass Attack Examples The purpose of this strategy is to broaden the firm’s resources by capturing the market share of the competing firm. A company following a bypass attack strategy simply outplays the competitor. Itc and hul could be the best examples. For example, the beginning of the apple ipod. Authentication bypass attacks are unique in that the attacker does not steal credentials,. Bypass Attack Examples.
From www.techtarget.com
Cybercriminals launching more MFA bypass attacks TechTarget Bypass Attack Examples Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro quo, tailgating and diversion theft. Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware. The purpose of this strategy is to broaden the firm’s resources by capturing the market share of the competing firm. A. Bypass Attack Examples.
From www.slideshare.net
Attack strategies business diagram Bypass Attack Examples That is, a firm doesn’t identify the weak areas of its competitor or launch. Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro quo, tailgating and diversion theft. For example, the beginning of the apple ipod. Itc and hul could be the best examples. The bypass attack is the indirect attack, wherein the market challenger. Bypass Attack Examples.
From www.onespan.com
How Attackers Bypass Modern Twofactor Authentication and How to Protect Your Users OneSpan Bypass Attack Examples Itc and hul could be the best examples. A few examples of bypass attack strategy can be showcased as below. The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier markets. The purpose of this strategy is to broaden the firm’s resources by capturing. Bypass Attack Examples.
From www.azion.com
The recent WAF Bypass attack does not affect Azion's Application Firewall Azion Bypass Attack Examples Itc and hul could be the best examples. That is, a firm doesn’t identify the weak areas of its competitor or launch. The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier markets. A few examples of bypass attack strategy can be showcased as. Bypass Attack Examples.
From www.threatlocker.com
Understanding MFA Bypass ThreatLocker Bypass Attack Examples The purpose of this strategy is to broaden the firm’s resources by capturing the market share of the competing firm. Itc and hul could be the best examples. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. Six types of most common social. Bypass Attack Examples.
From www.slideshare.net
AMCA Lecture Three Competitive Marketing Strategy Bypass Attack Examples Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware. Itc and hul could be the best examples. For example, the beginning of the apple ipod. That is, a firm doesn’t identify the weak areas of its competitor or launch. A company following a bypass attack strategy simply outplays the. Bypass Attack Examples.
From kratikal.com
bypassfirewall_info Kratikal Blogs Bypass Attack Examples The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier markets. A few examples of bypass attack strategy can be showcased as below. Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. Itc. Bypass Attack Examples.
From www.intrust-it.com
How to Protect Against MFA Bypass Attacks Intrust IT Bypass Attack Examples That is, a firm doesn’t identify the weak areas of its competitor or launch. A few examples of bypass attack strategy can be showcased as below. Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro quo, tailgating and diversion theft. Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather. Bypass Attack Examples.
From www.researchgate.net
Miter circuit used for bypass attack and corresponding probabilities of... Download Scientific Bypass Attack Examples For example, the beginning of the apple ipod. That is, a firm doesn’t identify the weak areas of its competitor or launch. A company following a bypass attack strategy simply outplays the competitor. The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier markets.. Bypass Attack Examples.
From www.youtube.com
Understanding Bypass Attack YouTube Bypass Attack Examples The purpose of this strategy is to broaden the firm’s resources by capturing the market share of the competing firm. Itc and hul could be the best examples. Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. For example, the beginning of the apple ipod. Six types of most. Bypass Attack Examples.
From laptrinhx.com
5 Common Cyber Security Threats That Bypass Legacy AV LaptrinhX Bypass Attack Examples Authentication bypass attacks are unique in that the attacker does not steal credentials, but rather bypasses the authentication process entirely. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the competitor by attacking its easier markets. The bypass attack is the indirect attack, wherein the market challenger does not attack. Bypass Attack Examples.
From www.slideserve.com
PPT Competitive Strategy PowerPoint Presentation, free download ID1666567 Bypass Attack Examples A company following a bypass attack strategy simply outplays the competitor. A few examples of bypass attack strategy can be showcased as below. Six types of most common social engineering attacks are phishing, pretexting, baiting, quid pro quo, tailgating and diversion theft. Itc and hul could be the best examples. Authentication bypass attacks are unique in that the attacker does. Bypass Attack Examples.
From www.researchgate.net
Working principle of active shield and bypass attack on active shield [33]. Download Bypass Attack Examples That is, a firm doesn’t identify the weak areas of its competitor or launch. The bypass attack is the indirect attack, wherein the market challenger does not attack the leader directly, but broaden its market share by attacking the easier markets. A few examples of bypass attack strategy can be showcased as below. Six types of most common social engineering. Bypass Attack Examples.
From www.aon.com
Bypassing MFA A Forensic Look at Evilginx2 Phishing Kit Bypass Attack Examples The purpose of this strategy is to broaden the firm’s resources by capturing the market share of the competing firm. Once they circumvent authentication, attackers can escalate privileges, move to other pages, steal or alter data, or download malicious firmware. The bypass attack is the most indirect marketing strategy adopted by the challenging firm with a view to surpassing the. Bypass Attack Examples.